- Defend & Conquer
- Posts
- Adapting to new U.S. DoD cybersecurity rules (effective November 2025) and contract risk
Adapting to new U.S. DoD cybersecurity rules (effective November 2025) and contract risk
CybersecurityHQ Report - Pro Members
Welcome reader to a 🔒 pro subscriber-only deep dive 🔒.
Brought to you by:
👣 Smallstep – Secures Wi-Fi, VPNs, ZTNA, SaaS and APIs with hardware-bound credentials powered by ACME Device Attestation
📊 LockThreat – AI-powered GRC that replaces legacy tools and unifies compliance, risk, audit and vendor management in one platform
Forwarded this email? Join 70,000 weekly readers by signing up now.
#OpenToWork? Try our AI Resume Builder to boost your chances of getting hired!
—
Get lifetime access to our deep dives, weekly cyber intel podcast report, premium content, AI Resume Builder, and more — all for just $799. Corporate plans are now available too.
Executive Summary
On November 10, 2025, the U.S. Department of Defense implemented the most consequential cybersecurity regulatory change in defense contracting history. The Cybersecurity Maturity Model Certification (CMMC) 2.0 framework, now embedded in Defense Federal Acquisition Regulation Supplement (DFARS) clauses 252.204-7021 and 252.204-7025, transforms cybersecurity from a self-attestation exercise into a contractual prerequisite. For the estimated 338,000 contractors comprising the defense industrial base, certification is no longer optional - it is the price of market entry.
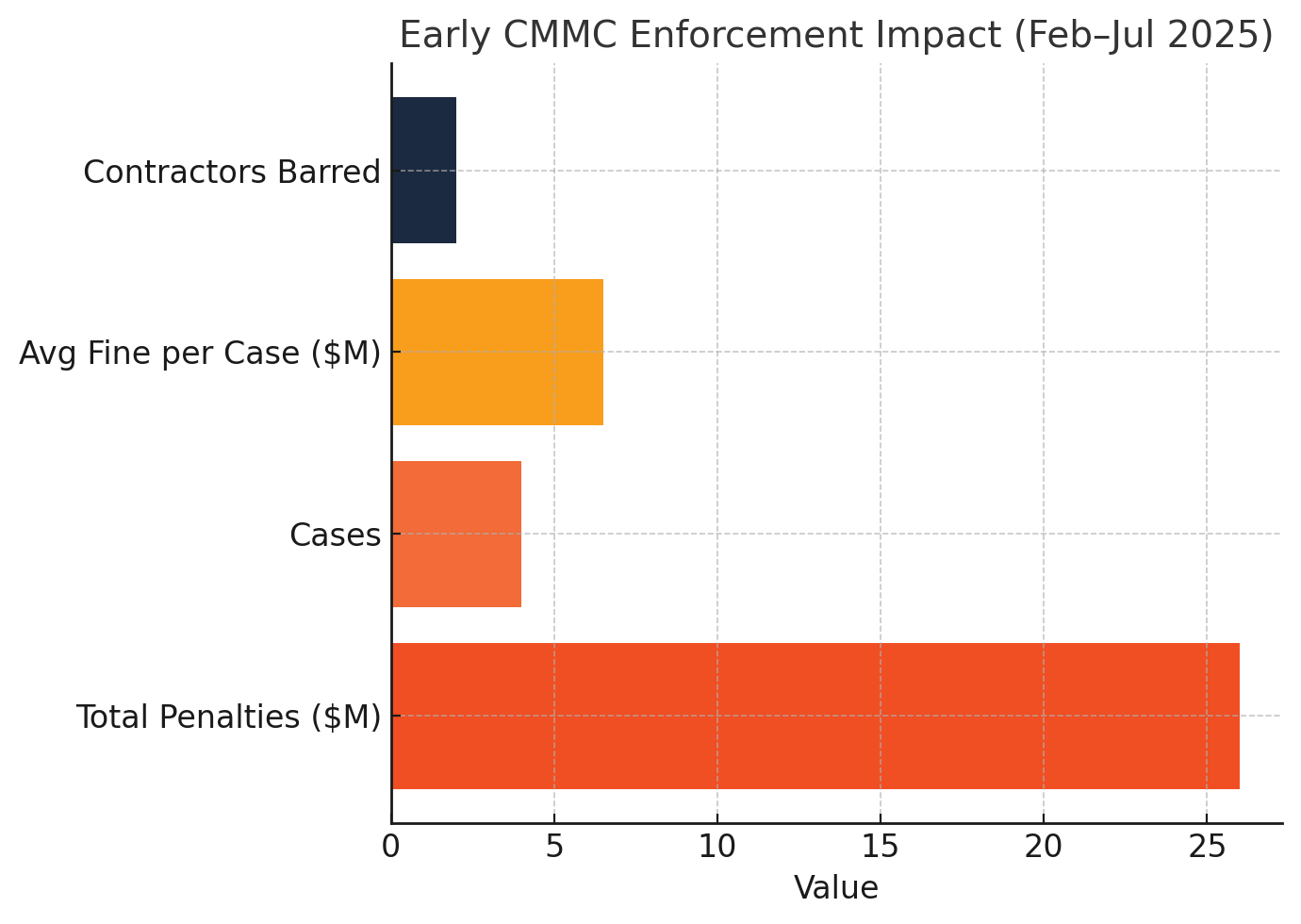
The regulatory shift carries material business consequences. Analysis of early enforcement actions reveals significant financial exposure: between February and July 2025, the Department of Justice secured $26 million in False Claims Act settlements from contractors who misrepresented cybersecurity compliance, with penalties including multi-year contracting bans. Contract eligibility now depends on verifiable security posture, with contracting officers mandated to confirm certification status before award. Non-compliance eliminates bid eligibility regardless of technical qualifications or past performance.
The CMMC framework establishes three maturity levels aligned with NIST SP 800-171 and 800-172 standards. Level 1 requires 15 foundational practices for Federal Contract Information through annual self-assessment. Level 2 mandates 110 controls for Controlled Unclassified Information, verified by independent third-party assessors every three years. Level 3, affecting fewer than 1% of contracts involving critical national security programs, requires government-led Defense Industrial Base Cybersecurity Assessment Center evaluation plus enhanced threat protections from NIST SP 800-172.
Implementation follows a phased 36-month rollout. Phase 1 (November 2025) introduces self-assessment requirements in select solicitations, affecting approximately 1,104 entities. Phase 2 (November 2026) scales third-party certification requirements to 18,554 contractors. Phase 3 (November 2027) incorporates Level 3 assessments for high-sensitivity programs. Phase 4 (November 2028) achieves full implementation across an estimated 229,818 entities, 68% of which are small businesses.
Chief Information Security Officers face a compressed timeline for organizational transformation. Survey data from 1,491 global executives indicates that only 21% of organizations have fundamentally redesigned workflows for new technology adoption, and fewer than 28% report CEO oversight of governance frameworks - the two factors most correlated with bottom-line impact. Defense contractors must close this execution gap while managing technical remediation, supply chain verification, and continuous compliance obligations.
This whitepaper provides a comprehensive implementation roadmap for CISOs navigating CMMC requirements, synthesizing regulatory analysis, technical architecture guidance, risk mitigation strategies, and board-level action frameworks to enable both compliance and competitive differentiation.

Subscribe to CybersecurityHQ Newsletter to unlock the rest.
Become a paying subscriber of CybersecurityHQ Newsletter to get access to this post and other subscriber-only content.
Already a paying subscriber? Sign In.
A subscription gets you:
- • Access to Deep Dives and Premium Content
- • Access to AI Resume Builder
- • Access to the Archives
Reply