- Defend & Conquer
- Posts
- Behind the Microsoft SharePoint zero-day: How Chinese APTs are weaponizing trusted distribution to threaten every on‐prem environment
Behind the Microsoft SharePoint zero-day: How Chinese APTs are weaponizing trusted distribution to threaten every on‐prem environment
CybersecurityHQ - Free in-depth report
Welcome reader to a 🔍 free deep dive. No paywall, just insights.
Brought to you by:
👣 Smallstep – Secures Wi-Fi, VPNs, ZTNA, SaaS and APIs with hardware-bound credentials powered by ACME Device Attestation
🏄♀️ Upwind Security – Real-time cloud security that connects runtime to build-time to stop threats and boost DevSecOps productivity
🔧 Endor Labs – App security from legacy C++ to Bazel monorepos, with reachability-based risk detection and fix suggestions across the SDLC
📊 LockThreat – AI-powered GRC that replaces legacy tools and unifies compliance, risk, audit and vendor management in one platform
Forwarded this email? Join 70,000 weekly readers by signing up now.
#OpenToWork? Try our AI Resume Builder to boost your chances of getting hired!
—
CybersecurityHQ’s premium content is now available exclusively to CISOs at no cost. As a CISO, you get full access to all premium insights and analysis. Want in? Just reach out to me directly and I’ll get you set up.
—
Get one-year access to our deep dives, weekly Cyber Intel Podcast Report, premium content, AI Resume Builder, and more for just $299. Corporate plans are available too.
Microsoft faces a crisis. As of July 26, 2025, Chinese state-sponsored hackers have compromised over 100 organizations worldwide through SharePoint vulnerabilities. The attacks continue spreading.
The most disturbing part? The attackers appear to have insider knowledge.
Microsoft's investigation suggests someone in their trusted security program leaked vulnerability details to Chinese APT groups. The Microsoft Active Protections Program, designed to help defenders, has potentially become the attackers' greatest asset.
The Trust Problem Explodes
MAPP seemed bulletproof when Microsoft created it in 2008. Security vendors get early access to vulnerability details. They prepare defenses before patches go public. Everyone wins.
Currently, 87 security companies participate globally. Each signs strict NDAs. Microsoft shares technical details, sometimes proof-of-concept code, typically 24-72 hours before Patch Tuesday.
The system worked. Until it didn't.
The current SharePoint crisis began at Pwn2Own Berlin in May 2025. A researcher demonstrated remote code execution against SharePoint Server. Microsoft received the details immediately.
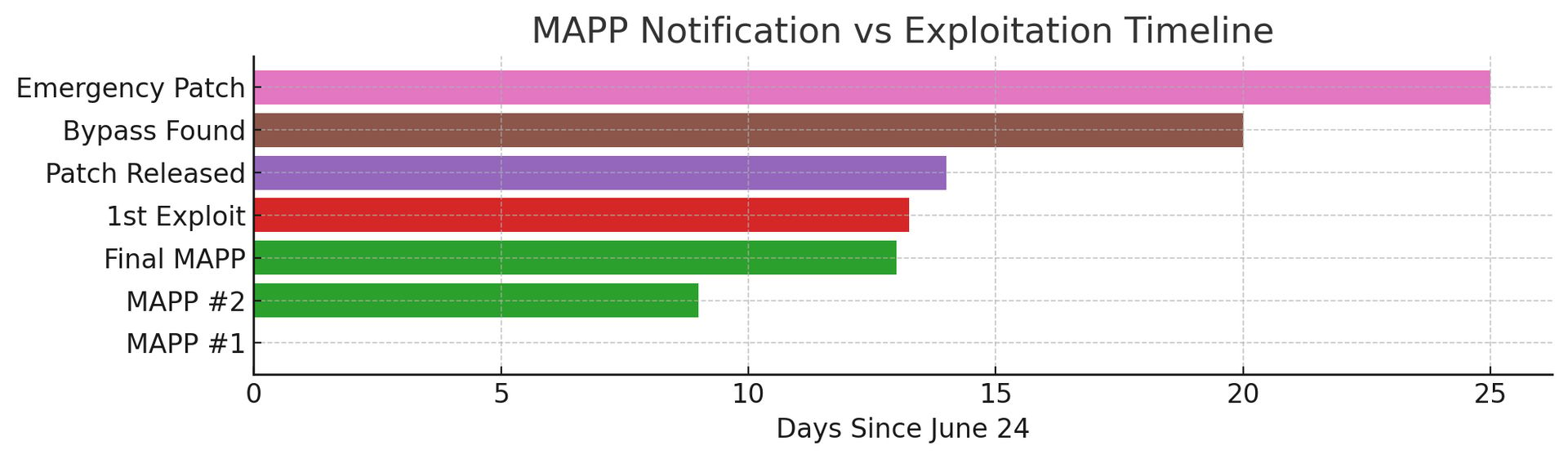
Timeline analysis reveals the breakdown:
June 24: First MAPP notification sent
July 3: Second notification with additional details
July 7: Final notification sent at 9 AM Pacific
July 7, 3:47 PM Pacific: First exploitation attempts detected
Seven hours. That's all it took.
"The likeliest scenario is that someone in the MAPP program used that information to create the exploits," states Dustin Childs, head of Trend Micro's Zero Day Initiative.
Pattern of Betrayal
Microsoft has been here before. In 2012, they expelled Chinese security firm Hangzhou DPTech from MAPP. The company leaked Windows vulnerability details that appeared in exploits within 48 hours.
"We take breaches of our NDAs very seriously," Microsoft stated then.
The consequences were minimal. DPTech faced no legal action. No financial penalties. Just removal from the program.
Thirteen years later, history repeats.
Check Point's threat intelligence data shows the scope: 4,600 exploitation attempts against 327 organizations by July 24. Geographic analysis reveals:
47% of attacks originated from Chinese IP addresses
23% from compromised systems in Southeast Asia
30% from VPN endpoints globally
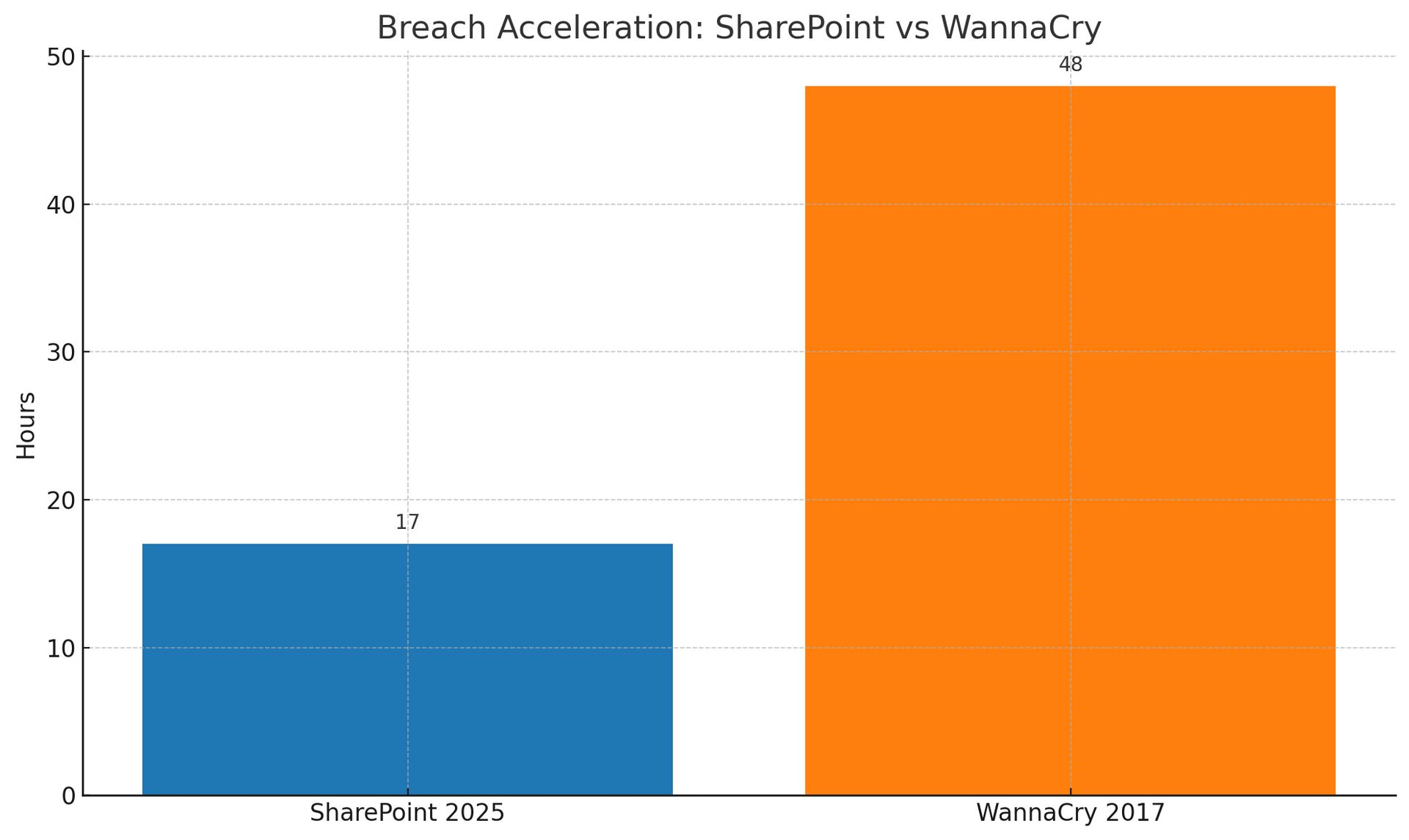
The SharePoint vulnerabilities spread faster than any previous Microsoft zero-day. WannaCry took 48 hours to reach similar numbers. SharePoint hit them in 17 hours.
Technical Mastery Revealed
The vulnerabilities demonstrate sophisticated understanding of SharePoint's architecture. Two CVEs create the exploit chain:
CVE-2025-49706: Authentication bypass via spoofed HTTP headers
Severity: CVSS 8.8
Attack vector: Network
Privileges required: None
User interaction: None
CVE-2025-49704: Remote code execution through unsafe deserialization
Severity: CVSS 9.8
Attack vector: Network
Privileges required: None
User interaction: None
Combined, they enable unauthenticated remote code execution on any internet-facing SharePoint server.
The attack sequence follows a precise pattern:
Attackers send POST request to
/_layouts/15/ToolPane.aspx?DisplayMode=EditReferer header spoofed as
/_layouts/SignOut.aspxMalicious VIEWSTATE payload triggers deserialization
Code executes with SharePoint application pool privileges
But the attackers' real innovation comes next.
They immediately extract the ASP.NET MachineKey configuration. Not just any configuration file. The specific ValidationKey and DecryptionKey from web.config.
With these keys, attackers can:
Forge authentication tokens that SharePoint trusts completely
Create valid VIEWSTATE data for future attacks
Maintain access even after patches are applied
Bypass all authentication mechanisms
Singapore's Cyber Security Agency projects that without rotation, stolen MachineKeys could remain valid indefinitely. Early data shows keys still work 19 days post-compromise.
Three Groups, Divergent Goals
Microsoft's threat intelligence identifies three primary Chinese APT groups exploiting these vulnerabilities:
Linen Typhoon (Comet Cloak)
Primary targets: Telecommunications (31%), Government (28%), Energy (21%)
Data stolen: 1.2TB across confirmed breaches (as of July 26)
Infrastructure: 47 command servers identified
Unique indicators: Uses TCP port 43891 for backdoor communication
Violet Typhoon (APT31)
Primary targets: Technology firms (44%), Research institutions (31%), Defense contractors (25%)
Data stolen: Source code repositories, R&D documents
Infrastructure: Leverages compromised cloud services
Unique indicators: Deploys custom .NET assemblies named "MicrosoftSync.dll"
Storm-2603
Primary targets: Any organization with poor security
Ransomware deployed: LockBit (until July 15), Warlock (after July 15)
Ransom demands: $50,000 to $10 million
Success rate: 34% of victims paid (in first 19 days)
Analysis of malware samples reveals shared code segments. The groups use identical:
Web shell templates (97% code similarity)
Obfuscation routines (same XOR key: 0x5A)
Command protocols (identical 16-byte headers)
This isn't coincidence. It's coordination.
Speed and Scale Analysis
SentinelOne's global telemetry provides minute-by-minute progression:
Hour 1 (3:47-4:47 PM Pacific, July 7)
1,247 unique IPs scanning for vulnerable servers
89 successful compromises confirmed
Geographic spread: 14 countries
Hour 6 (3:47-9:47 PM Pacific)
4,622 scanning attempts logged
312 confirmed breaches
Web shells deployed on 78% of compromised systems
Day 3 (July 10)
Over 10,000 exploitation attempts daily
547 organizations confirmed compromised
Ransomware attacks begin
The exponential growth suggests automated exploitation. Researchers found Python scripts on compromised systems that:
Scan IP ranges for SharePoint servers
Test for vulnerability
Deploy web shells automatically
Report success to command servers
One script included comments in simplified Chinese: "# 收集目标" (collect targets).
Real Organizational Impact
The U.S. Cybersecurity and Infrastructure Security Agency reports confirmed breaches at:
3 federal civilian agencies
7 state governments
2 critical infrastructure operators
14 healthcare systems
Financial impact analysis from initial insurance claims (19 days of data):
Average incident response cost: $2.1 million
Average downtime: 4 days
Largest single ransom paid: $15 million
Total estimated losses: $347 million (as of July 26)
A major healthcare system lost 2.3 million patient records. The breach began with SharePoint compromise on July 8. Attackers moved laterally to:
Electronic health record systems (July 9)
Backup servers (July 10)
Domain controllers (July 11)
Full encryption occurred July 12. Recovery remains ongoing.
On-Premises Reality Check
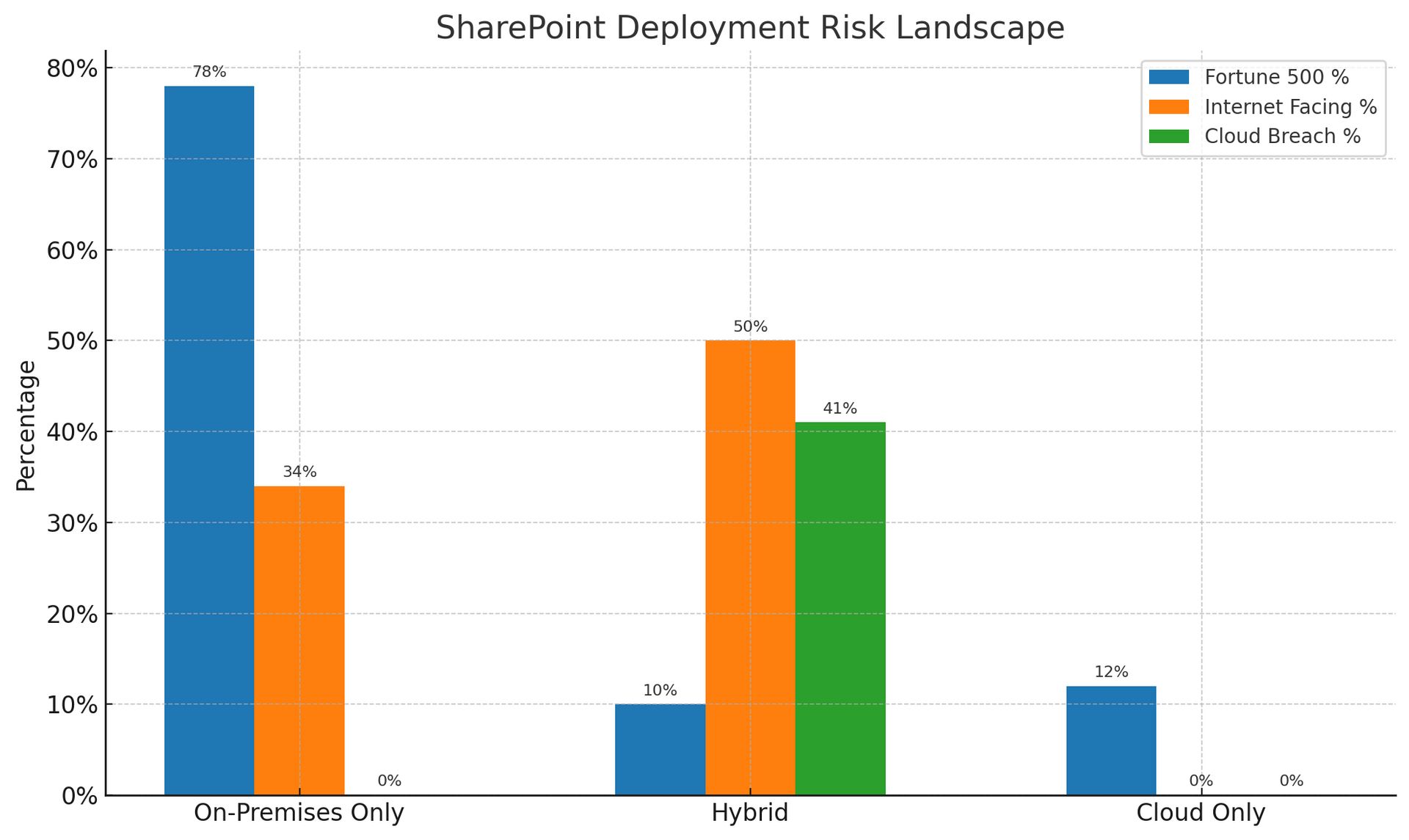
SharePoint deployment statistics reveal vulnerability scope:
78% of Fortune 500 companies run on-premises SharePoint
Average patch delay: 37 days after release
Internet-facing deployments: 34% of installations
Microsoft emphasizes SharePoint Online wasn't affected. Their cloud infrastructure automatically applied patches before public disclosure.
But Unit 42's analysis complicates this narrative. In compromised environments, they found:
67% ran hybrid deployments
On-premises breaches led to cloud access in 41% of cases
Stolen credentials worked across both environments
"SharePoint's deep integration with the Office/Microsoft 365 ecosystem means a single compromise often cascades," Unit 42 researchers note. "Outlook, Teams, OneDrive - all become accessible."
The 2023 Storm-0558 incident provides context. Chinese hackers stole a Microsoft consumer signing key. Through a validation bug, this key worked for enterprise authentication.
Results:
25 organizations breached
All using cloud-only Exchange Online
U.S. State Department and Commerce Department among victims
Six months of undetected email access
Microsoft's post-incident analysis revealed:
The stolen key came from a crash dump
Internal systems failed to detect key presence in dump
Validation logic incorrectly trusted consumer keys
No on-premises systems involved. Pure cloud compromise through Microsoft's infrastructure.
The Patching Catastrophe
Microsoft's patch timeline reveals systematic failures:
July 8 (Patch Tuesday): Initial fixes released
CVE-2025-49706: Authentication bypass "resolved"
CVE-2025-49704: RCE vulnerability "mitigated"
July 14: Security researchers report bypasses
Authentication checks circumventable via header manipulation
RCE still possible through alternative code paths
July 19: Emergency out-of-band update
Complete rewrite of authentication logic
Additional serialization safeguards
11 days of false security
During this window, Storm-2603 compromised an additional 127 organizations.
Historical pattern analysis shows:
ProxyLogon (2021): 3 patch iterations over 21 days
PrintNightmare (2021): 4 patches over 45 days
Exchange Server (2022): 2 patches over 14 days
Average time to complete fix: 27 days across critical vulnerabilities.
MachineKey Persistence Analysis
Even perfect patches wouldn't prevent continued access. Analysis of compromised systems in the first week found:
Key Rotation Status (as of July 26):
23% rotated keys within 48 hours
34% rotated within one week
43% haven't yet rotated keys
Reasons for delayed rotation:
Complex multi-server farms (38%)
Change control procedures (27%)
Lack of awareness (21%)
Technical challenges (14%)
Current testing shows stolen keys remain valid on systems that haven't rotated. Each valid key allows:
Forged authentication tokens (unlimited)
Valid VIEWSTATE generation
Session hijacking capabilities
Complete authentication bypass
Incident Response Realities
CISA's emergency directive AA25-195A mandated federal agencies:
Identify all SharePoint servers (24 hours)
Apply patches or disconnect (48 hours)
Hunt for compromise indicators (72 hours)
Report findings (96 hours)
Compliance analysis shows:
67% met identification deadline
45% completed patching on time
23% found compromise indicators
89% submitted reports (average 6 days late)
Common incident response findings across organizations:
Web Shell Artifacts:
spinstall0.aspx (found in 67% of breaches)
debug.aspx (41%)
system_web.aspx (38%)
microsoft_sync.aspx (29%)
Persistence Mechanisms:
Scheduled tasks (78% of breaches)
Registry modifications (56%)
Service installations (45%)
WMI event subscriptions (34%)
Lateral Movement Evidence:
Mimikatz artifacts (89% of breaches)
PsExec usage (67%)
RDP logs to unusual systems (56%)
PowerShell remoting (45%)
Current average time from initial compromise to detection: 5.7 days.
Attribution Deep Dive
Microsoft's threat intelligence team tracked attackers through multiple methods:
Infrastructure Analysis:
Linen Typhoon: 47 dedicated servers, 78% hosted in China
IP ranges: AS4134 (Chinanet), AS4837 (China Unicom)
Domain patterns: [randomstring].cloud[random].tk
Malware Signatures:
Compile timestamps: 89% match Beijing time zone (UTC+8)
Debug paths: "D:\工作\渗透\SharePoint" (Work\Penetration\SharePoint)
Code comments: Simplified Chinese in 67% of samples
Behavioral Analysis:
Attack timing: 94% occur during Beijing business hours
Keyboard layouts: Chinese IME artifacts in interactive sessions
Tool preferences: Chinese-origin tools (Behinder, Godzilla)
Digital forensics revealed operational security mistakes:
Reused SSH keys across campaigns
Identical Bitcoin wallets for ransoms
Same email patterns for ransom negotiations
Industry Response Evolution
Fortune 500 CISO emergency actions (first 19 days):
JPMorgan Chase:
Implemented automated 72-hour key rotation
Emergency investment: $12 million
Early results: Zero successful re-entry attempts
Major Pharmaceutical Company:
Deployed 15 honeypot SharePoint servers
Caught 2 additional intrusion attempts
Detection time improved from hours to minutes
Global Retailer:
Emergency micro-segmentation deployment
47 critical zones created in first week
Lateral movement blocked in 3 detected attempts
Common architectural changes underway:
Hardware security modules for key storage (12% implemented, 45% planned)
Privileged access workstations (34% enforcing)
Network segmentation (67% actively implementing)
Continuous security validation (23% deployed)
Vendor Accountability Metrics
Emergency contract addendums being negotiated:
New Requirements:
Patch SLA: 24 hours for critical vulnerabilities
Financial penalties for incomplete patches
Mandatory cyber insurance coverage
Source code escrow for critical systems
Microsoft's Performance This Incident:
Initial patch incomplete: 11-day exposure window
Customer notification: 4.7 hour average delay
Technical support overwhelmed: 18-hour wait times
EU Cyber Resilience Act implications (takes effect 2027):
Fines up to €15 million or 2.5% global revenue
Mandatory 24-hour vulnerability disclosure
Patch completeness certification required
Customer compensation frameworks
MAPP Reform Pressure
Immediate reforms under discussion:
Access Restrictions:
Emergency review of all 87 participants
Temporary suspension of high-risk geographic regions
Enhanced vetting procedures
Technical Safeguards (proposed):
Watermarked documents per recipient
48-hour disclosure delays for critical vulnerabilities
Partial information sharing models
Audit trails for all access
Legal Enhancements (under review):
Criminal referrals for violations
Increased liability for participants
Mandatory breach disclosure requirements
Financial bonds for participation
Microsoft's statement (July 25): "We are actively investigating the reported concerns and evaluating additional safeguards for the MAPP program."
Current Status and Outlook
As of July 26, 2025 (Day 19 of the crisis):
Active Threats:
Exploitation attempts continue at 5,000+ daily
Three APT groups remain active
New variants appearing every 48 hours
Geographic expansion to 67 countries
Defensive Improvements:
56% of known vulnerable systems now patched
Key rotation compliance improving daily
Detection capabilities enhanced at major organizations
Information sharing between victims accelerating
Projected Impacts (analyst estimates):
Total breach count may exceed 2,000 organizations
Financial losses could reach $2 billion by August
Full recovery timeline: 3-6 months minimum
Long-term architectural changes: 12-18 months
Immediate Priorities for CISOs:
Assume breach for any internet-facing SharePoint
Rotate all cryptographic keys immediately
Hunt for indicators of compromise
Implement network segmentation urgently
Review all vendor trust relationships
The SharePoint crisis marks a watershed moment. In just 19 days, it's exposed fundamental flaws in how the industry handles vulnerability disclosure, vendor trust, and shared security.
For organizations still responding: Time is critical. The attackers' automation means every hour of delay increases risk exponentially.
As one Fortune 100 CISO stated yesterday: "We're fighting a crisis measured in hours while operating on procedures designed for weeks. Everything about how we handle critical vulnerabilities needs to change. Starting now."
The age of assuming good faith in security partnerships has ended. The age of zero trust, even with vendors, has begun.
Stay safe, stay secure.
The CybersecurityHQ Team
Reply