- Defend & Conquer
- Posts
- Bridging the technical skills gap: Outsourcing vs insourcing security operations in 2025
Bridging the technical skills gap: Outsourcing vs insourcing security operations in 2025
CybersecurityHQ Report - Pro Members

Welcome reader to a 🔒 pro subscriber-only deep dive 🔒.
Brought to you by:
👣 Smallstep – Secures Wi-Fi, VPNs, ZTNA, SaaS and APIs with hardware-bound credentials powered by ACME Device Attestation
📊 LockThreat – AI-powered GRC that replaces legacy tools and unifies compliance, risk, audit and vendor management in one platform
Forwarded this email? Join 70,000 weekly readers by signing up now.
#OpenToWork? Try our AI Resume Builder to boost your chances of getting hired!
—
Get lifetime access to our deep dives, weekly cyber intel podcast report, premium content, AI Resume Builder, and more — all for just $799. Corporate plans are now available too.
Executive Summary
The cybersecurity workforce crisis has reached unprecedented severity in 2025, with an estimated 4.8 million unfilled security positions globally—a 19% year-over-year increase that represents a 47% shortage across the profession. This talent deficit directly impacts organizational resilience: 87% of enterprises experienced at least one breach in 2024, with 56% incurring losses exceeding $1 million, and recovery averaging 2.5 months. The correlation between inadequate staffing and preventable incidents is undeniable—analysts predict that by 2025, lack of skilled personnel will be a root cause in over 50% of significant cyber incidents.
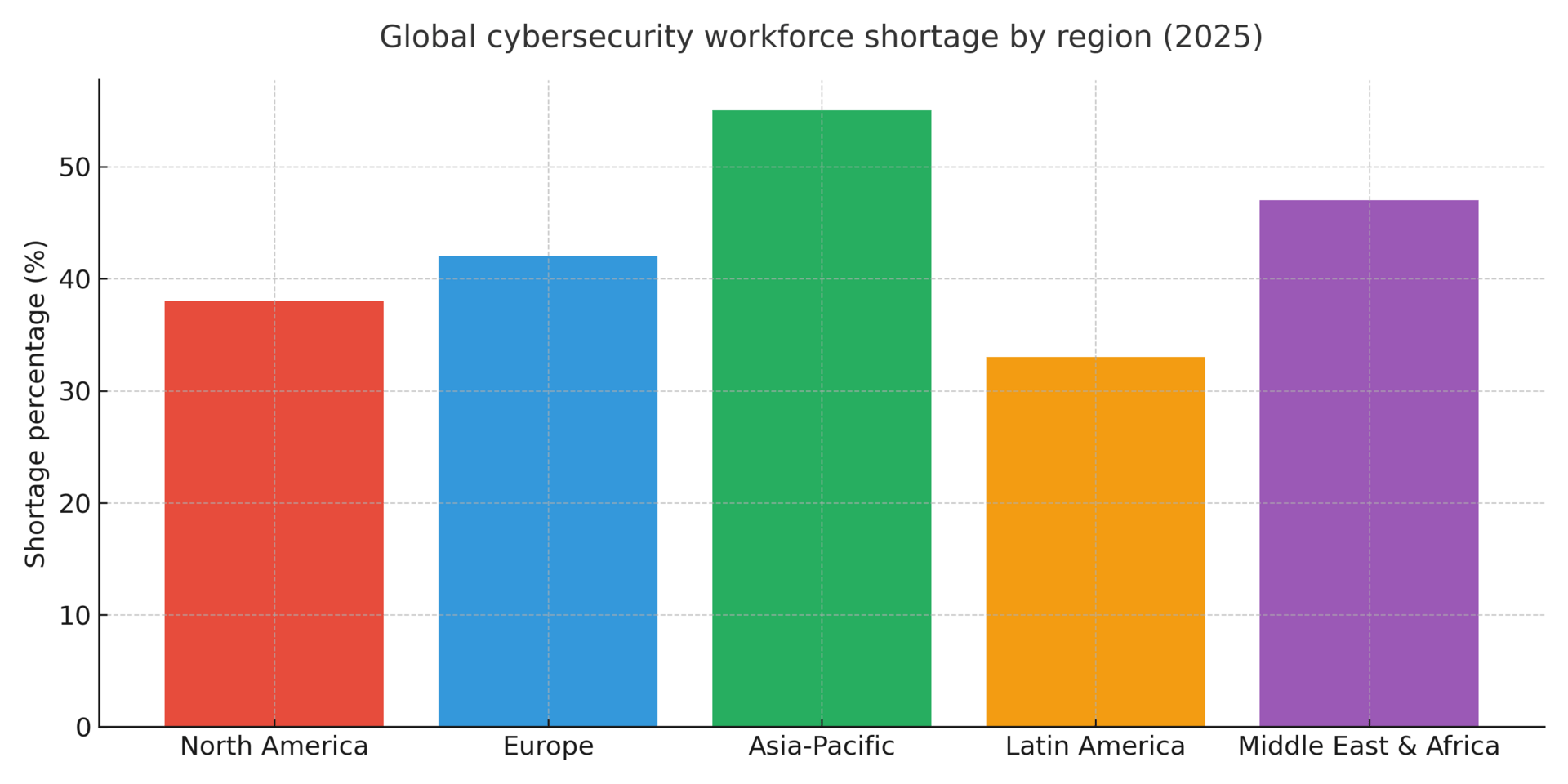
Against this backdrop, Chief Information Security Officers face a strategic inflection point: how to deliver enterprise-grade security operations when traditional hiring models have failed. The answer increasingly lies not in binary choices between insourcing and outsourcing, but in sophisticated hybrid models that leverage artificial intelligence, managed service providers (MSSPs), and strategic capability mapping.
Three critical trends are reshaping the security operations landscape in 2025. First, AI-enabled Security Operations Center (AI-SOC) platforms have fundamentally inverted the traditional cost calculus. AI-SOC platforms starting at approximately $30,000 annually now deliver 24/7 automated triage, correlation, and enrichment—capabilities that previously required multi-million dollar investments in staffing and infrastructure. Second, 82% of organizations now plan to outsource at least some security functions within the next 12 months, with threat detection, SOC monitoring, and vulnerability management leading adoption. Third, large enterprises with revenues exceeding $500 million are implementing co-managed security models at significantly higher rates than smaller organizations, recognizing that control and scale need not be mutually exclusive.
The financial imperative is compelling. Traditional insourced SOCs require 5-7 analysts for basic 24/7 coverage, with fully-loaded costs (salaries, benefits, tools, training) typically 3-4x the cost of equivalent managed services. Specialized roles command premium compensation—Security Architects with 21+ years of experience earn $205,500-$241,500 annually, while cloud security and threat intelligence specialists face similar wage pressures. Compounding these costs, 21% of security team members leave annually, with specialized AI security recruitment averaging 99 days per hire. Organizations lacking sufficient staff suffered cloud security incidents at dramatically higher rates—65% experienced breaches in 2024, yet only 6% remediated within the critical first hour.
However, outsourcing introduces distinct trade-offs that demand executive-level governance. Regulatory liability remains non-transferable—if a Managed Detection and Response (MDR) vendor mishandles data, the contracting organization bears full compliance exposure under GDPR, HIPAA, and SEC disclosure requirements. Third-party dependencies create supply chain vulnerabilities, while shared-attention models may result in slower mean time to contain (MTTC) compared to dedicated internal teams. The optimal model thus requires function-by-function analysis, mapping each security capability against criticality, required control levels, and AI augmentation potential.
This whitepaper provides CISOs with a comprehensive framework for navigating sourcing decisions in 2025. Drawing on the latest workforce studies, regulatory guidance, and organizational research, we analyze when to insource (governance, compliance, security architecture, incident response strategy), when to outsource (Tier 1 alert triage, specialized penetration testing, 24/7 commodity monitoring), and how to implement hybrid models that maximize coverage while maintaining strategic control. The analysis integrates specific guidance on NIST SP 800-53 Rev. 6 alignment, NIS2 Directive compliance, and SEC cybersecurity disclosure requirements—all critical considerations for regulated industries navigating third-party risk.
The strategic imperative for 2025 is clear: CISOs must pivot from managing expensive headcount to governing sophisticated technology platforms and rigorously managing third-party dependencies. Organizations that successfully execute this transition—combining lean internal teams focused on strategy and governance with AI-augmented platforms and selective MSSP partnerships—will achieve both superior security outcomes and sustainable cost structures in an environment where talent scarcity shows no signs of abating.

Subscribe to CybersecurityHQ Newsletter to unlock the rest.
Become a paying subscriber of CybersecurityHQ Newsletter to get access to this post and other subscriber-only content.
Already a paying subscriber? Sign In.
A subscription gets you:
- • Access to Deep Dives and Premium Content
- • Access to AI Resume Builder
- • Access to the Archives
Reply