- Defend & Conquer
- Posts
- Building analytics systems to detect anomalous high-velocity API usage – a CISO’s guide
Building analytics systems to detect anomalous high-velocity API usage – a CISO’s guide
CybersecurityHQ Report - Pro Members

Welcome reader to a 🔒 pro subscriber-only deep dive 🔒.
Brought to you by:
👣 Smallstep – Secures Wi-Fi, VPNs, ZTNA, SaaS and APIs with hardware-bound credentials powered by ACME Device Attestation
📊 LockThreat – AI-powered GRC that replaces legacy tools and unifies compliance, risk, audit and vendor management in one platform
Forwarded this email? Join 70,000 weekly readers by signing up now.
#OpenToWork? Try our AI Resume Builder to boost your chances of getting hired!
—
Get lifetime access to our deep dives, weekly cyber intel podcast report, premium content, AI Resume Builder, and more — all for just $799. Corporate plans are now available too.
Executive Summary
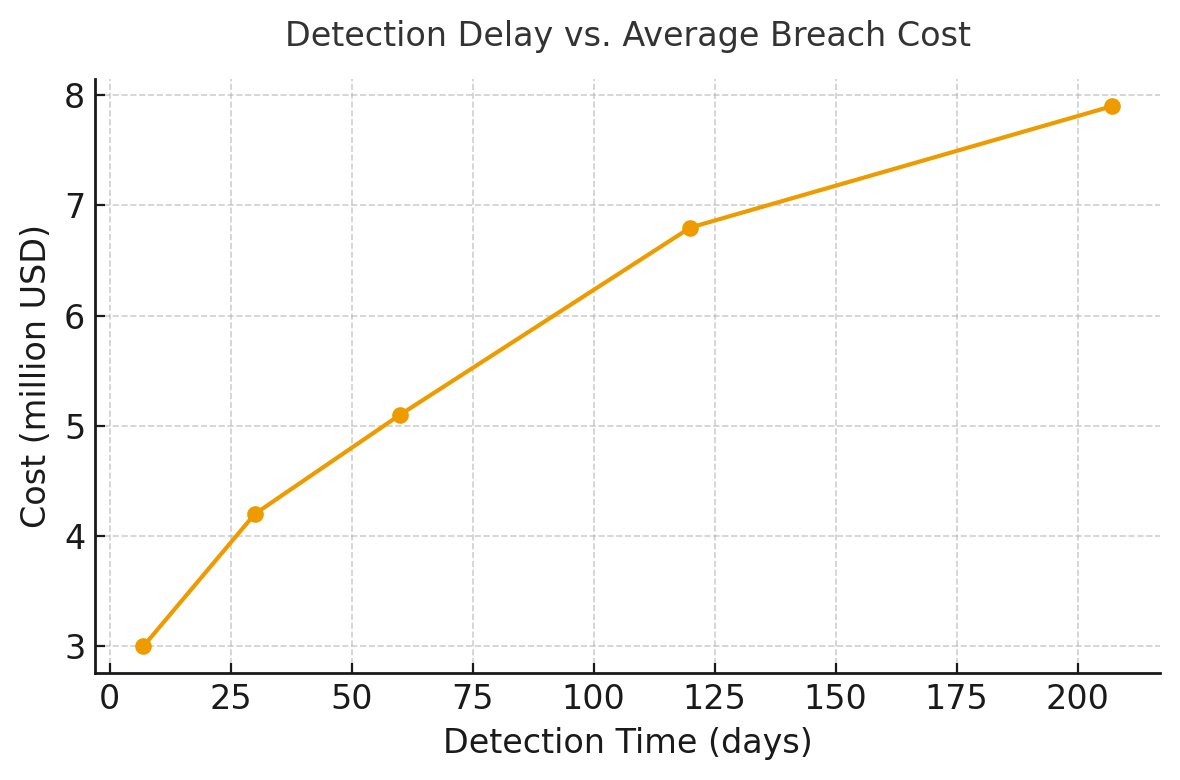
APIs have become the primary attack vector in modern enterprise security. In 2025, API-related breaches account for 42% of web application security incidents, a 30% increase from 2023. The T-Mobile API breach—where attackers exfiltrated 37 million customer records over six weeks before detection—exemplifies the cost of delayed response. Organizations that detect and contain API breaches within 30 days save an average of $1.2 million in incident costs compared to slower responders.

Traditional security approaches are insufficient. Ninety-one percent of API attacks use valid credentials and legitimate access patterns, evading signature-based defenses. The new imperative is sub-second behavioral analytics—real-time systems that establish baselines, detect anomalies, and trigger automated responses before damage scales.
This whitepaper provides a comprehensive framework for CISOs to build analytics systems that detect anomalous high-velocity API usage. Drawing on 2025 threat intelligence, regulatory requirements, and technical best practices, we outline a maturity-based implementation roadmap aligned with OWASP API Security Top 10, NIST SP 800-228, and ISO 27001:2022 standards.
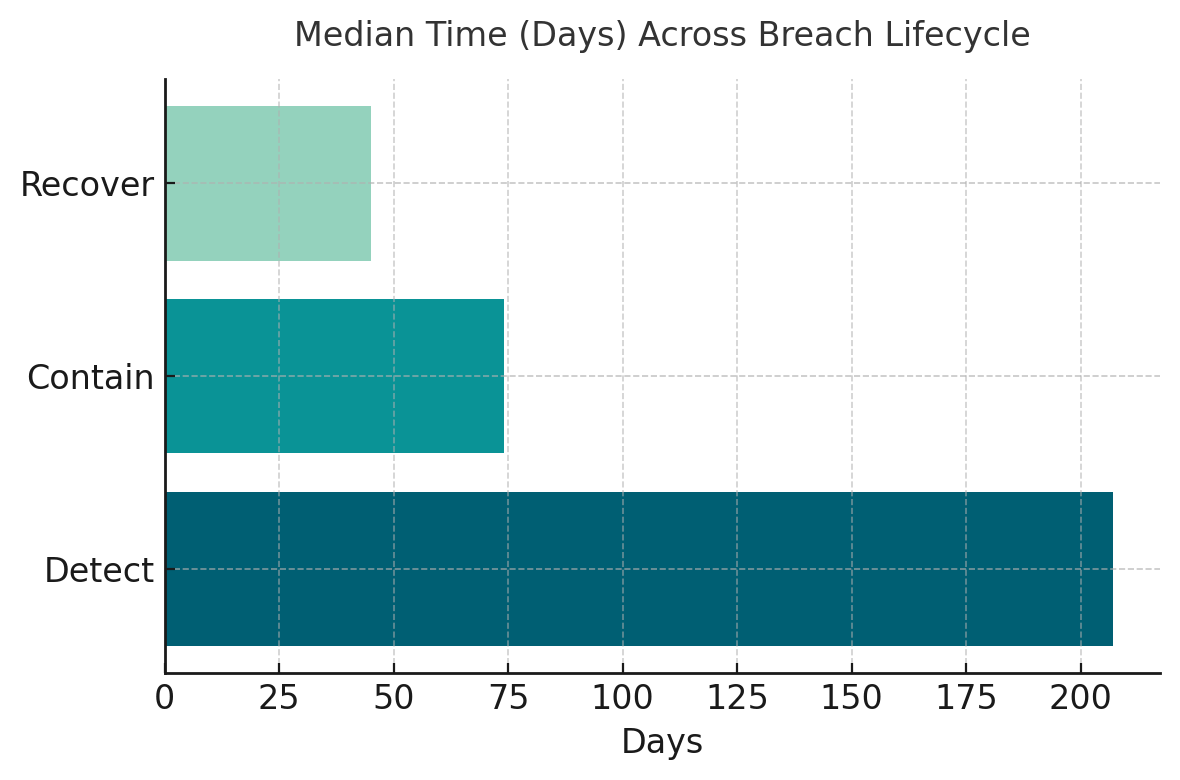
Key findings:
Organizations implementing AI-driven anomaly detection achieve 95-97% accuracy in identifying API abuse, reducing false positives by 30% compared to static thresholds
CEO oversight of AI governance correlates most strongly with bottom-line impact from AI deployment—critical as APIs become AI-enabled
Twenty-one percent of organizations have fundamentally redesigned workflows to embed gen AI and analytics—workflow redesign shows the highest correlation with EBIT impact
Real-time stream processing (Apache Kafka, Tinybird) combined with hybrid ML models (isolation forests, Markov chains) enables detection within seconds versus the industry average of 207 days
Multi-layer controls—adaptive rate limiting, behavioral baselining per user/API, and automated blocking—reduce incident response times by 40-60%
Strategic imperatives: Shift from reactive logging to proactive behavioral monitoring. Integrate API telemetry into SIEM/SOC workflows. Establish senior-level governance (28% of AI-using organizations report CEO oversight of AI governance). Deploy layered defenses that account for seasonality, entity-specific baselines, and zero-trust principles. The organizations capturing value from AI and API security are those "rewiring" processes, not merely deploying new tools.

Subscribe to CybersecurityHQ Newsletter to unlock the rest.
Become a paying subscriber of CybersecurityHQ Newsletter to get access to this post and other subscriber-only content.
Already a paying subscriber? Sign In.
A subscription gets you:
- • Access to Deep Dives and Premium Content
- • Access to AI Resume Builder
- • Access to the Archives
Reply