- Defend & Conquer
- Posts
- Centralizing DLP policy enforcement for remote users: Evaluating effectiveness and enterprise challenges
Centralizing DLP policy enforcement for remote users: Evaluating effectiveness and enterprise challenges
CybersecurityHQ Report - Pro Members
Welcome reader to a 🔒 pro subscriber-only deep dive 🔒.
Brought to you by:
👣 Smallstep – Secures Wi-Fi, VPNs, ZTNA, SaaS and APIs with hardware-bound credentials powered by ACME Device Attestation
🏄♀️ Upwind Security – Real-time cloud security that connects runtime to build-time to stop threats and boost DevSecOps productivity
🔧 Endor Labs – App security from legacy C++ to Bazel monorepos, with reachability-based risk detection and fix suggestions across the SDLC
📊 LockThreat – AI-powered GRC that replaces legacy tools and unifies compliance, risk, audit and vendor management in one platform
Forwarded this email? Join 70,000 weekly readers by signing up now.
#OpenToWork? Try our AI Resume Builder to boost your chances of getting hired!
—
Get lifetime access to our deep dives, weekly cyber intel podcast report, premium content, AI Resume Builder, and more — all for just $799. Corporate plans are now available too.
Executive Summary
The rapid expansion of remote work has fundamentally altered the enterprise security landscape, creating unprecedented challenges for data loss prevention (DLP) strategies. As of 2025, with remote work comprising over 50% of global knowledge-based roles, organizations face a critical imperative to centralize their DLP policy enforcement across distributed workforces. This whitepaper examines the effectiveness and challenges of centralizing DLP for remote users in enterprise network environments, drawing on recent academic research, industry implementations, and real-world case studies.
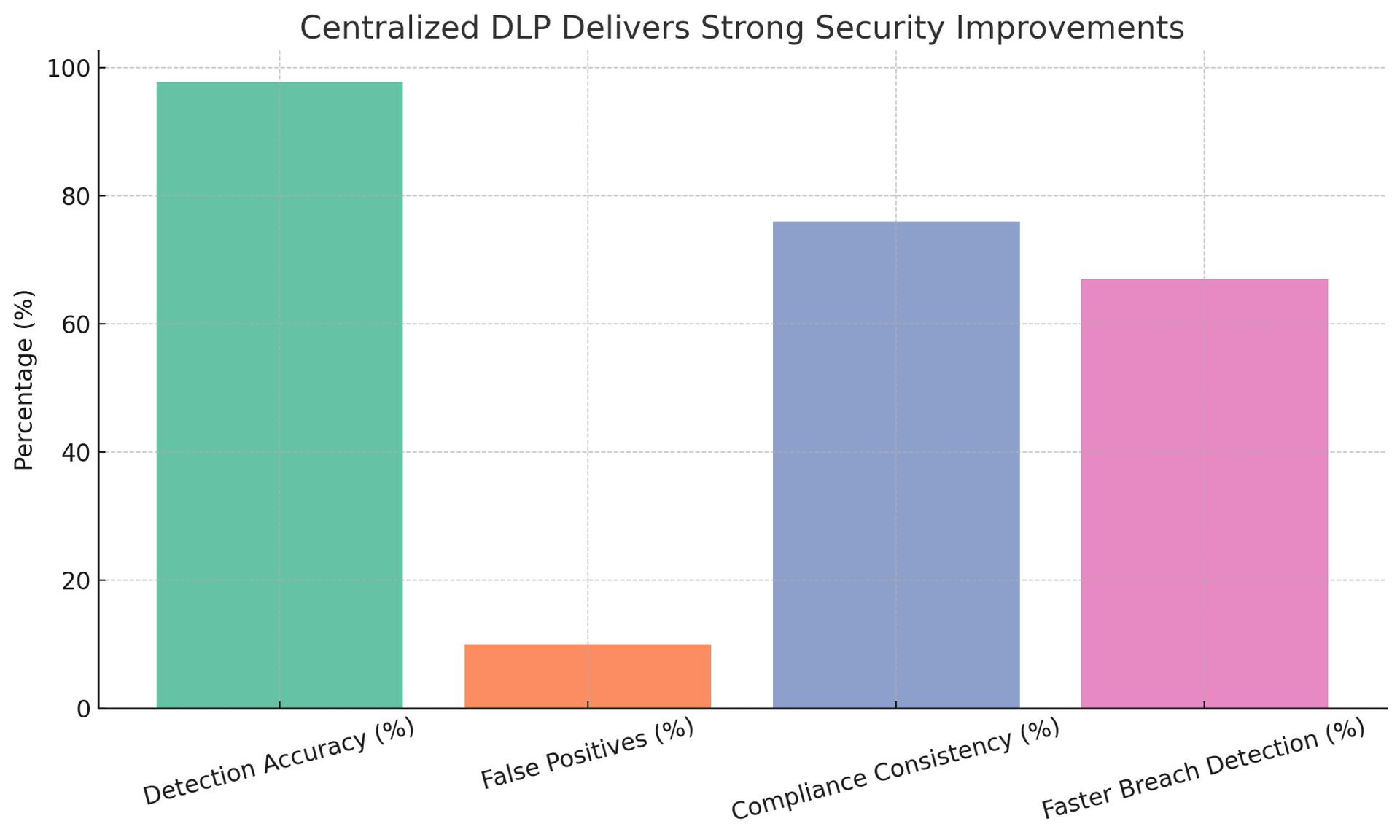
Our analysis reveals that centralized DLP enforcement delivers significant security improvements, with organizations reporting detection accuracies up to 97.8% and false positive rates below 10% when properly implemented. However, technical challenges persist, including device heterogeneity, encrypted traffic inspection, and performance overhead that can range from negligible to over 120% depending on implementation approach. The research indicates that organizations successfully centralizing DLP see measurable benefits including 76% improved compliance consistency, 67% faster breach detection, and substantial reductions in administrative overhead.
Key findings include the critical importance of CEO-level oversight for DLP governance, with organizations having executive involvement showing significantly higher bottom-line impact from their security investments. Workflow redesign emerges as the single most impactful factor for capturing value from centralized DLP, yet only 21% of organizations have fundamentally redesigned workflows to accommodate new security requirements. Large enterprises with revenues exceeding $500 million are leading adoption, implementing more comprehensive risk mitigation strategies and achieving better outcomes than smaller organizations.
This whitepaper provides actionable recommendations for CISOs including adopting Security Service Edge (SSE) architectures, implementing AI-driven detection capabilities, conducting regular business impact analyses, and integrating DLP with Zero Trust frameworks. By following these evidence-based strategies, security leaders can build resilient, scalable DLP programs that protect sensitive data while enabling productive remote work.

Subscribe to CybersecurityHQ Newsletter to unlock the rest.
Become a paying subscriber of CybersecurityHQ Newsletter to get access to this post and other subscriber-only content.
Already a paying subscriber? Sign In.
A subscription gets you:
- • Access to Deep Dives and Premium Content
- • Access to AI Resume Builder
- • Access to the Archives
Reply