- Defend & Conquer
- Posts
- CISO market intelligence: Oct 16-22, 2025
CISO market intelligence: Oct 16-22, 2025
CybersecurityHQ weekly analysis

Welcome reader to your CybersecurityHQ report
Brought to you by:
👣 Smallstep – Secures Wi-Fi, VPNs, ZTNA, SaaS and APIs with hardware-bound credentials powered by ACME Device Attestation
📊 LockThreat – AI-powered GRC that replaces legacy tools and unifies compliance, risk, audit and vendor management in one platform
Forwarded this email? Join 70,000 weekly readers by signing up now.
—
Get annual access to our deep dives, weekly cyber intel podcast report, premium content, AI Resume Builder, and more — all for just $299. Corporate plans are now available too.
Introducing the CISO Access Plan Unlock premium CybersecurityHQ insights at no cost, exclusively for CISOs. Reach out to me to claim your access.
Top Targeted Sectors & Attack Trends

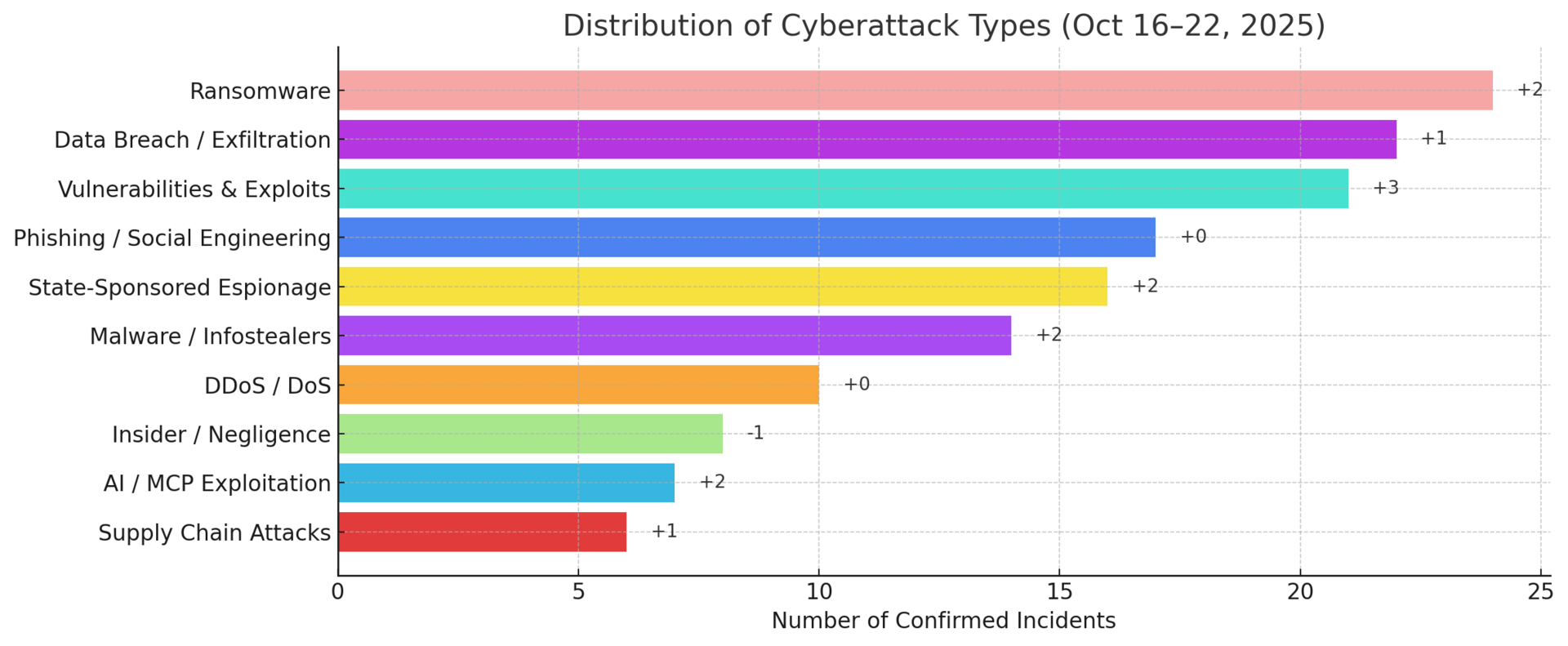
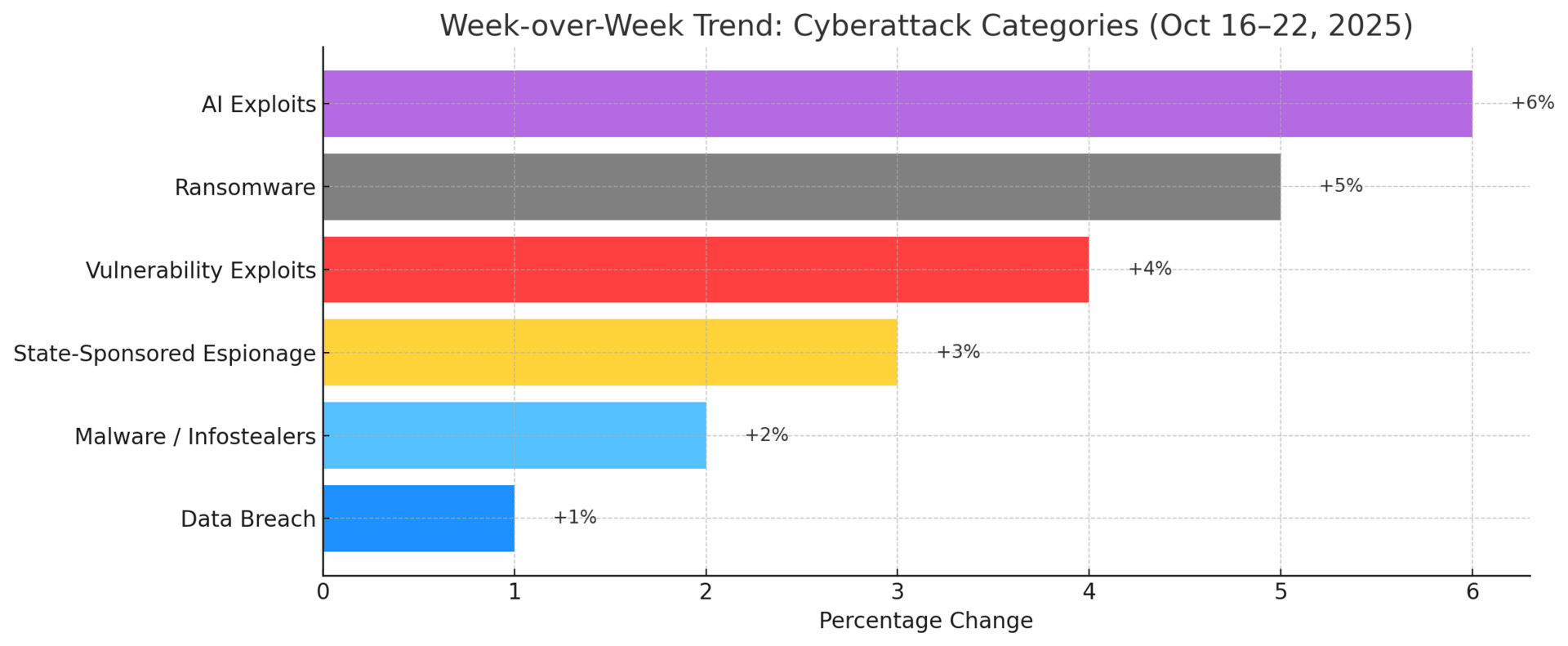
Threat Highlights:
Government / Public: Sustained spike in incidents linked to F5 BIG-IP and Cisco SNMP exploitation; multiple APT campaigns attributed to China-based groups targeted federal and defense infrastructure. The AWS outage further highlighted systemic cloud dependency risk within public sector workloads.
Healthcare: Continued activity from Rhysida and 8Base ransomware targeting hospitals and medical suppliers. A U.S. health network reported data exfiltration involving 2.5M records. Despite no new mega-breaches, healthcare remains a prime ransomware target due to slow patching cycles.
Financial Services: Stable week with low volume of direct ransomware, but VM memory leak (VMScape) and BitLocker bypass exploits gained traction. Financial SOC teams warned of increased credential replay attacks via infostealer kits on dark markets.
Technology & Cloud: Most active sector again — AWS, F5, and Adobe AEM vulnerabilities dominated headlines. CISA added CVE-2025-61884 to its KEV catalog. AI-phishing rose 1,200% YoY (Palo Alto Networks) as attackers automate credential harvesting. Cloud API exploitation and NuGet package supply-chain compromise underline growing dependency-chain risks.
Industrial / Manufacturing: Elevated activity tied to Jaguar Land Rover (£1.9B impact) — the costliest cyber incident in UK history. Multiple OT vendors targeted via Zero Disco Linux rootkit and Mirai variants exploiting IoT/PLC controllers. Analysts warn of tightening convergence between cyber and physical disruption.
Energy & Utilities: Incremental rise in Sandworm reconnaissance across Eastern Europe. ICS-CERT issued advisories for new vulnerabilities in water management systems. North American utilities saw minor phishing surges aimed at energy brokers.
Telecom: One confirmed breach in European telecom traced to Citrix flaw (SnappyBee malware). Continued exploitation of legacy routers (Cisco, ASUS, QNAP, Synology) by PolarEdge botnet. Nation-state attribution under review.
Education: Moderate ransomware exposure persisted, especially in U.S. school districts renewing cyber contracts post-attack. Campaigns by Vice Society and Play continue exploiting outdated Windows servers.
Ransomware: Still the dominant threat vector. LockBit, ALPHV/BlackCat, and Medusa remained active. Analysts report growing use of data-extortion-only operations without encryption to accelerate monetization.
Exploits: This week’s primary intrusion vector — Async-Tar RCE (Rust), TP-Link Omada flaws, and Adobe AEM exploitations widespread. Over 34 new zero-days were successfully demonstrated in global Pwn2Own-style contests, many already repurposed in the wild.
Phishing: Stable volume but higher sophistication through AI-assisted deep-phish, agentic lure crafting, and blockchain-based malware delivery (EtherHiding). Targets shifted toward telecom, retail, and enterprise VPN users.
AI / MCP Exploitation: Rapidly expanding threat surface (+6% WoW). Adversaries now automate malware obfuscation, generate polymorphic phishing text, and craft fake job postings leveraging LLMs to bypass detection — notably by Lazarus Group and emerging agentic AI crews.
CybersecurityHQ: This Week’s Reports Based on Technical Research and Academic Papers
→ Free
The rise of source code warfare: how nation-states are turning vendor blueprints into precision cyberweapons 👉 Read the report
→ Pro subscriber-only
Shifting left in risk: Applying security earlier in design systems 👉 Read the report
Securing the data supply chain in outsourced AI/data services 👉 Read the report
Bridging gaps in the NIST SSDF 800‐218 modernization and what modern organizations should prepare for 👉 Read the report
Automated containment vs human discretion — where to draw the line 👉 Read the report
And more inside - check out the full list here.
Cybersecurity Stocks

Market Intelligence
The cybersecurity sector dipped again this week, averaging roughly –2.6%, as investors took profits from a third-quarter rally and recalibrated around near-term execution risks and valuation discipline. The underlying tone shifted: while enthusiasm for AI-driven security remains, caution around budget seasonality, vendor differentiation and geostrategic tailwinds is growing.
AI continues to be the core narrative, but the market is now distinguishing between vendors that embed intelligence natively versus those simply layering AI features on legacy stacks. Firms demonstrating real workflow automation—such as credential risk scoring, autonomous certificate rotation or zero-touch anomaly remediation—are receiving stronger marks for customer stickiness and margin durability.
Investor focus has also turned back to operating discipline. Names such as ZS (Zscaler), CRWD (CrowdStrike) and CYBR (CyberArk) that balance growth with margin expansion continue to hold favor, while smaller unprofitable vendors are facing sharper scrutiny. The bar for premium valuations has clearly risen – the question is no longer just ARR velocity, but visibility into cash flow and margin uplift.
A wave of public-sector and infrastructure-centric cybersecurity concerns added complexity. Reports of a nation-state breach at vendors like F5 Networks and fresh scrutiny around federal cyber-budgets underscore the macro risk shifting from consumer-facing exposures to infrastructure and supply-chain resilience. This has subtly boosted demand expectations for platform players with federal-grade certifications or proven resilience credentials.
From a demand vantage point, enterprise buyers remain cautious but engaged. Effective spend is being skewed toward renewals and expansion within existing platforms rather than new vendor adoption. This environment benefits vendors with broad product suites and high dollar-based net retention. Those with strong cross-sell mechanics and renewal-centric growth are better insulated from macro drag.
Overall, the market appears to be consolidating around a few durable themes: AI-native automation is outperforming marketing-driven AI; margin strength is being rewarded more than raw growth speed; and resilience in the face of regulatory and budget turbulence is becoming a core investor filter.
Earnings Watch
Zscaler (ZS): Analysts expect Q4 revenue growth of ~19% to about $707 million while EPS is forecast to dip to ~$0.80/share, reflecting higher spending.
While the top line is solid, the EPS decline highlights the margin pressure question. Surveyed firms also highlight margin expansion and free cash-flow leverage (rather than just growth) as key to sustaining valuation.
CrowdStrike (CRWD): The company recently reported Q2 revenue of $1.17 billion (up ~21% YoY) and beat EBITDA expectations, but guidance remains cautious – valuation sensitivity is visibly higher.
Analysts note that CrowdStrike is well positioned in the consolidation wave of endpoint & workload security but expect margins and cash-flow to drive the next leg of upside.
Analyst Sentiment: The consensus tilt for the broader cybersecurity group remains Neutral → Cautious Positive: many brokers maintain Buy or Outperform ratings on the top tier vendors, but valuation discipline and execution clarity are increasingly gating factors (rather than features or narrative alone).
Tactical View
Maintain overweight on Zscaler, CyberArk and Palo Alto Networks for their combination of automation leverage and improving profitability visibility. Keep a close watch on Varonis and CrowdStrike for potential rebounds if risk-appetite returns and cost disciplines show traction. In the meantime, avoid mid-cap consulting and endpoint-only vendors until clear signs of cost stabilisation and backlog recovery emerge.
M&A and Funding Summary
Cybersecurity Activity
This week saw significant consolidation in the cybersecurity sector, with three notable acquisitions totaling over $2 billion. The largest deal came from cloud data protection company Veeam, which agreed to acquire AI-focused security firm Securiti AI for $1.73 billion. Meanwhile, data intelligence company Dataminr announced its acquisition of Arlington-based ThreatConnect for $290 million, strengthening its threat intelligence capabilities. Additionally, MTX Group Inc. acquired VerifyID.ai to enhance its AI-powered digital identity verification offerings.
Quantum Computing Activity
The quantum computing sector experienced a wave of funding and merger activity this week. SuperQ Quantum Computing Inc. completed a $3.45 million CAD LIFE offering through Hampton Securities Limited. Several merger announcements also emerged, including CCCX's spotlight-generating plans to merge with Infleqtion, and Horizon Quantum Computing's merger with dMY Squared. The week's activity reflects broader market momentum, with reports indicating the post-quantum cryptography (PQC) market is experiencing explosive growth, driven by an urgent $2.84 billion investment surge as organizations race to address quantum computing threats to current encryption standards.
CISO Intelligence Report: Leadership Lessons from the Field
This is what you missed in this week’s Cyber Intel Report sourced from top cybersecurity podcasts and webinars, if you haven’t upgraded your membership:
The Transferability Problem that fundamentally breaks the "security through obscurity" model for AI systems—with implications spanning 7B to trillion-parameter deployments that most organizations haven't grasped yet
The 1-2 Year AI Agent Blocker threatening enterprise deployment timelines as one critical vulnerability type proves resistant to all current architectural solutions while financially-motivated adversaries sharpen their tools
10,000:1 Crisis Ratio exposing catastrophic global security staffing reality as Shadow AI emerges to replace Shadow IT—with only 37% of organizations prepared despite 66% expecting significant impact
Life-Threatening vs. Data-Threatening security paradigm requiring fundamentally different approaches for critical infrastructure as 250,000+ connected devices create attack surfaces traditional IT security frameworks cannot address
Perfect Protection's Fatal Flaw forcing impossible choices between provable security guarantees and model performance—leaving organizations with uncomfortable truth about treating deployed systems
And more insights in this week’s full CISO briefing.
Interesting Read
Quantum-Ready Now: The “Harvest Now, Decrypt Later” Threat Has Begun
While large-scale quantum computers aren’t yet operational, security researchers and threat intelligence teams are warning that the race for “harvest now, decrypt later” data has already started. Adversaries are quietly exfiltrating and stockpiling encrypted information—financial data, state secrets, health records—so that once quantum decryption becomes viable, these archives can be instantly unlocked.
This marks a paradigm shift: the quantum threat is no longer theoretical. Attackers are weaponizing time itself, betting that stolen ciphertext will one day yield cleartext. Enterprises relying on RSA and ECC remain especially exposed, as Shor’s algorithm could render both obsolete within the decade.
What’s changing fast is the interplay between AI and quantum risk. Advanced AI systems are automating reconnaissance, scanning for unpatched encryption endpoints, and optimizing data exfiltration pipelines for long-term retention. This convergence of AI and quantum capabilities could accelerate the erosion of current cryptographic confidence much faster than anticipated.
The takeaway for CISOs is clear: quantum migration isn’t an R&D exercise anymore—it’s an operational mandate. The first wave of post-quantum cryptography (PQC) standards from NIST is here, and cryptographic agility—how easily an organization can swap algorithms—will soon define resilience itself.
→ Read more at Palo Alto Networks
Fresh From the Field: Security Resources You Can Use
Title | Domain | Authors / Vendor | Key Insight | Source |
|---|---|---|---|---|
Cyber Security of Government Networks and Systems (Report to Parliament — Canada, Oct 2025) | Government Networks / Systems Security | Office of the Auditor General of Canada | Finds that while security tools exist across departments, Canada’s federal government still lacks a unified approach to network monitoring, incident management, and asset visibility — exposing critical service continuity risks. | |
Microsoft Digital Defense Report 2025 (Oct 2025) | Global Cyber Threat Landscape / AI Security | Microsoft Corporation | Highlights how AI has become both a cyber-defense amplifier and a new attack vector. Explains shifts in ransomware economies, influence operations, and the convergence of identity, IoT, and cloud attack surfaces. | |
ENISA Threat Landscape 2025 (ETL 2025) (Oct 2025) | European Cyber Threat Landscape / Resilience | European Union Agency for Cybersecurity (ENISA) | Analyzes 4,900 incidents (Jul 2024 – Jun 2025) showing ransomware’s continued dominance, rise of AI-assisted phishing, and increasing difficulty in attribution as threat actors use generative content to evade tracking. | |
2025 Kyndryl Readiness Report (Oct 2025) | IT Readiness / Resilience / Cyber Risk | Kyndryl (with Edelman DXI) | Survey of 3,700 senior leaders across 8 markets: only 31% feel ready for external risks. Cyberattacks remain the top concern; organizations struggle to modernize infrastructure and embed resilience into security operations. | |
Annual Cyber Threat Report 2024–25 (Oct 2025) | National Threat Landscape / Resilience | Australian Signals Directorate – Australian Cyber Security Centre (ASD/ACSC) | Reports an 11% YoY rise in incidents (>1,200), DDoS attacks up ~280%, ransomware most disruptive; average self-reported loss up 50% to ≈ $80,850. Emphasizes basic resilience and rapid patching for internet-facing systems. |
Northern Trust
Chicago, IL, US
Member of Technical Staff II - Architecture
Illumio
Sunnyvale, CA, US
Ecclesiastes Inc
Edgewater, NJ, US
Nissan Motor Corporation
Franklin, TN, US
Deloitte Cyber Data Protection and Encryption Sr. Consultant
Deloitte
Hartford, CT, US
Palo Alto Networks
Remote (California, United States, US)
Procore Technologies
Austin, TX, US
Mountain America Credit Union
Sandy, UT, US
Technology Risk and Controls Lead - Identity & Access Management
JPMorganChase
Plano, TX, US
Stay safe, stay secure.
The CybersecurityHQ Team


Reply