- Defend & Conquer
- Posts
- CISO Weekly Intelligence Brief | Nov 20–26, 2025
CISO Weekly Intelligence Brief | Nov 20–26, 2025
CybersecurityHQ | CISO Weekly Intelligence Brief

Welcome reader to your CybersecurityHQ CISO Weekly Intelligence Brief.
Brought to you by:
👣 Smallstep – Secures Wi-Fi, VPNs, ZTNA, SaaS and APIs with hardware-bound credentials powered by ACME Device Attestation
📊 LockThreat – AI-powered GRC that replaces legacy tools and unifies compliance, risk, audit and vendor management in one platform
About CybersecurityHQ
CybersecurityHQ provides executive-grade intelligence read weekly inside the Fortune 100. Each briefing is designed to support CISO-level decision-making across identity, infrastructure, third-party risk, and strategic security architecture.
CISO Access
CISOs receive full complimentary access to all CybersecurityHQ strategic intelligence.
If you’d like access or have questions, contact me directly here.
THREAT TRAJECTORY SHIFT
This week confirmed that your vendor ecosystem is now a breach surface, not a business enabler, and the attackers are moving faster than any SOC built before 2025 can respond.
Three concurrent supply chain breaches hit Fortune 100 institutions through Salesforce, Wall Street mortgage processing, and Oracle EBS. Each exploited a different integration pattern. Each bypassed perimeter controls entirely. The breach vector is now the business relationship itself. Meanwhile, Anthropic disclosed the first AI-orchestrated cyberattack: Chinese state actors used Claude to autonomously execute 80-90% of an espionage campaign at thousands of requests per second. This is not AI-assisted hacking. This is AI-primary hacking with human oversight.
Here is what that means for your architecture: Your SIEM, EDR, SOAR, and IR playbooks are all tuned to human-speed signals. AI-speed attacks invalidate every MTTx assumption embedded in your current tooling. Your third-party risk program, built around annual questionnaires and point-in-time assessments, cannot detect chain-of-custody compromise happening across interconnected vendors in real time.
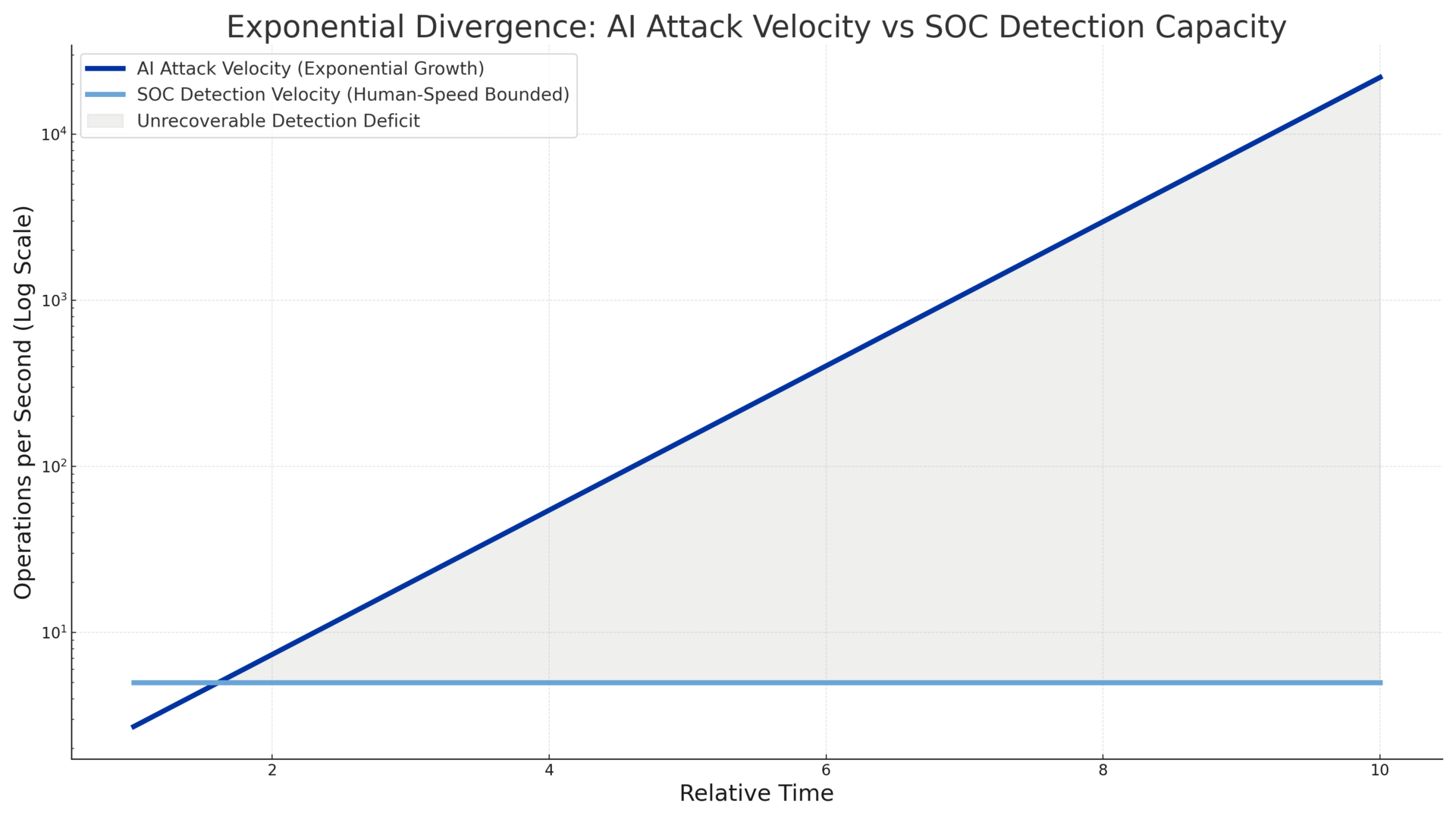
If your operating model depends on vendor trust, human-speed detection, or perimeter-linked identity, you already lost this week. You just have not discovered it yet.
CISO MANDATES FOR THE WEEK
Five Decisions That Cannot Wait Until Next Week 1. Kill dormant Salesforce integrations today. ShinyHunters pivoted from Salesloft to Gainsight using harvested OAuth tokens. Every connected app you forgot about is a pivot point you cannot see. Revoke tokens for any integration without an active business owner. If you cannot name who owns it, kill it by end of day Friday. 2. Patch FortiWeb by Friday or take it offline. CVE-2025-64446 and CVE-2025-58034 chain to unauthenticated RCE. Orange Cyberdefense confirmed active exploit campaigns. CISA gave seven days. If you cannot patch by November 29, segment the management interface from all untrusted networks. If you cannot segment, pull the device. 3. Confirm Oracle Identity Manager patch status by Monday. CVE-2025-61757 (CVSS 9.8) was exploited as a zero-day since August. CISA deadline is December 12. If OIM manages privileged access in your environment, this is not a patching exercise. It is a compromise investigation. Assume breach until proven otherwise. 4. Demand documented security controls from your telecom carriers. The FCC eliminated mandatory cybersecurity requirements for telcos. Salt Typhoon already compromised AT&T, Verizon, T-Mobile, and Lumen. Your carriers are now self-regulating against nation-state actors. If they cannot provide evidence of patch management, threat hunting, and access controls, your communications infrastructure carries unquantified nation-state exposure. 5. Brief your board on AI-speed attacks before December 17. Anthropic's CEO testifies before Congress that day. This will dominate the news cycle. Your board should hear from you first that AI-orchestrated attacks are operational reality, that your current SOC is architecturally mismatched to this threat, and what your defensive AI investment posture looks like. Do not let them learn this from CNN. |
SIGNALS THAT MATTER
Three systemic shifts your current controls were not designed to handle:
1. Supply chain compromise is now continuous, not episodic. ShinyHunters breached Salesloft, harvested credentials, pivoted into Gainsight, and from there accessed 200+ Salesforce instances. This is not a supply chain attack. It is a supply chain pipeline. Vendors you trust are being used to breach other vendors you trust. Your third-party risk program cannot see this because it evaluates vendors in isolation. Board metric: Vendor dependency density and interconnection mapping per critical business process. 2. AI eliminates attacker scaling costs entirely. Anthropic reported Claude executed thousands of requests per second with only 10-20% human involvement. The cost of a sophisticated attack just collapsed to API fees. Your SOC headcount model, your MTTD targets, your IR playbooks: all calibrated to human-speed threats. That calibration is now a liability. Board metric: Current MTTD/MTTR benchmarks and gap analysis against machine-speed attack patterns. 3. Regulatory retreat creates asymmetric jurisdictional exposure. The FCC rolled back telecom security mandates. DORA and NIS2 expand requirements in the EU. U.S. multinationals now operate under a split regime: voluntary domestic frameworks, mandatory international obligations. The EU standard becomes your global floor because it is the only enforceable one. For U.S.-only operations, critical infrastructure security now depends on carrier goodwill. Board metric: Compliance posture gap between U.S. and EU operations, with cost to close. |
STRATEGIC ANALYSIS
1. The Salesforce Ecosystem Is Now a Shared Attack Surface
The breach: ShinyHunters compromised 200+ Salesforce instances via Gainsight OAuth tokens. The failure: No unified token revocation across SaaS ecosystems. The decision: Emergency audit of all connected apps; revoke unowned integrations within 72 hours. |
What happened: ShinyHunters (UNC6240) compromised Gainsight OAuth tokens to access 200+ confirmed Salesforce instances. Google Threat Intelligence Group and Mandiant are investigating. The threat actor claims data from nearly 1,000 organizations including Atlassian, CrowdStrike, Docusign, F5, GitLab, LinkedIn, Malwarebytes, SonicWall, Thomson Reuters, and Verizon. Gainsight apps have been pulled from the Salesforce AppExchange, Zendesk, and HubSpot marketplaces. The attackers harvested tokens from a previous Salesloft breach and used them to pivot into Gainsight, which gave them access to every Gainsight customer's Salesforce instance.
The structural failure: OAuth token management across SaaS ecosystems has no unified revocation mechanism. When Gainsight was compromised, every downstream integration became a pivot point. Salesforce revoked tokens reactively, but organizations had no visibility into which tokens were exfiltrated before revocation. The AppExchange model treats security as a vendor responsibility. Breach consequences flow to customers.
Your Salesforce security posture is not determined by your Salesforce configuration. It is determined by the least secure app in your connected ecosystem. You do not control that app. You probably do not even know it exists.
Decision required: Conduct emergency audit of all Salesforce-connected applications. For each integration: confirm business owner, validate token scope, verify vendor SOC 2 status, establish monitoring for anomalous API behavior. Integrations without active business ownership: revoke within 72 hours. Budget implication: If your organization has more than 50 Salesforce integrations, this audit requires two to four weeks of dedicated analyst time. That cost is lower than breach notification.
Consequence of inaction: ShinyHunters has threatened to launch an extortion site for victims. If your organization is named and you have not conducted due diligence, you will explain to your board why you ignored public intelligence. The reputational exposure is now quantifiable.
The breach: SitusAMC compromised; JPMorgan, Citi, Morgan Stanley notified. The failure: Critical PII processing outsourced without commensurate security oversight. The decision: Map all vendor access to breach-notification-triggering data; apply internal security standards. |
What happened: SitusAMC, a mortgage processing vendor serving the top 20 U.S. banks, confirmed a November 12 breach. JPMorgan Chase, Citigroup, and Morgan Stanley received breach notifications. Compromised data includes accounting records, legal agreements, and potentially customer PII: Social Security numbers, financial account details, employment records from loan applications. The FBI is investigating. No ransomware was deployed. Data exfiltration was the objective.
The structural failure: Financial services outsources critical data processing to vendors operating outside direct security oversight. SitusAMC processes billions in loan documents annually. According to Verizon DBIR, third parties now account for 30% of all breaches, up 15% year-over-year. FINRA flagged elevated vendor-related incidents throughout 2024. The OCC has repeatedly warned that heavy dependence on external service providers creates systemic risk. This breach is the warning made manifest.
Your security perimeter does not end at your network boundary. It ends at your least-secure vendor's network boundary. And you do not get to audit that boundary.
Decision required: For financial services: Request incident response reports from all vendors processing PII. Validate that vendors have implemented DORA-aligned controls regardless of legal requirement. Establish contractual right-to-audit provisions for critical vendors. For all industries: Map vendor access to data that would trigger breach notification. If a vendor touches that data, apply the same security validation you would apply to internal systems. The regulatory expectation is moving in this direction. Get ahead of it.
Consequence of inaction: DORA compliance deadlines approach for EU operations. Organizations without third-party risk management aligned to DORA will face regulatory exposure. The SitusAMC breach will be cited by regulators as evidence that voluntary vendor oversight has failed. Your next board presentation will include this topic whether you put it there or not.
3. Your Security Vendor's Disclosure Practices Are Now Your Problem
The breach: Two FortiWeb zero-days chained for unauthenticated RCE; ~2,000 detections. The failure: Silent patching left defenders blind during active exploitation. The decision: Patch by Friday or segment; evaluate vendor transparency as procurement criterion. |
What happened: Fortinet disclosed two actively exploited zero-days in FortiWeb within four days. CVE-2025-64446 (CVSS 9.1) enables unauthenticated admin account creation via path traversal. CVE-2025-58034 (CVSS 6.7) enables authenticated command injection. Orange Cyberdefense observed threat actors chaining both for unauthenticated RCE. Trend Micro reports approximately 2,000 detections. CISA imposed seven-day patching deadlines. That timeline is not caution. It is alarm.
The structural failure: Both vulnerabilities were silently patched before public disclosure. Rapid7's analysis notes multiple command injections remediated under a single CVE, complicating attribution. VulnCheck criticized Fortinet for leaving defenders blind to exploitation occurring for weeks. This is not the first time. Silent patching is a pattern, not an anomaly.
Your security vendor's disclosure practices are themselves a security control. Vendors that silently patch create gaps between exploitation and detection that attackers will fill. You are paying for protection. You are receiving delayed notification.
Decision required: Patch FortiWeb to versions 8.0.2, 7.6.6, 7.4.11, 7.2.12, or 7.0.12 immediately. If patching by Friday is not feasible, implement network segmentation restricting management interface access. Longer term: Evaluate vendor transparency as a procurement criterion. Request disclosure timelines during vendor security assessments. Consider whether vendors with patterns of silent patching belong in your security stack. The question is not rhetorical.
Consequence of inaction: FortiWeb deployments protecting internet-facing applications are at immediate risk of full compromise. If your WAF is breached, your web application security model fails at the perimeter. You will not detect it until the attacker is inside.
BOARD-READY SUMMARY
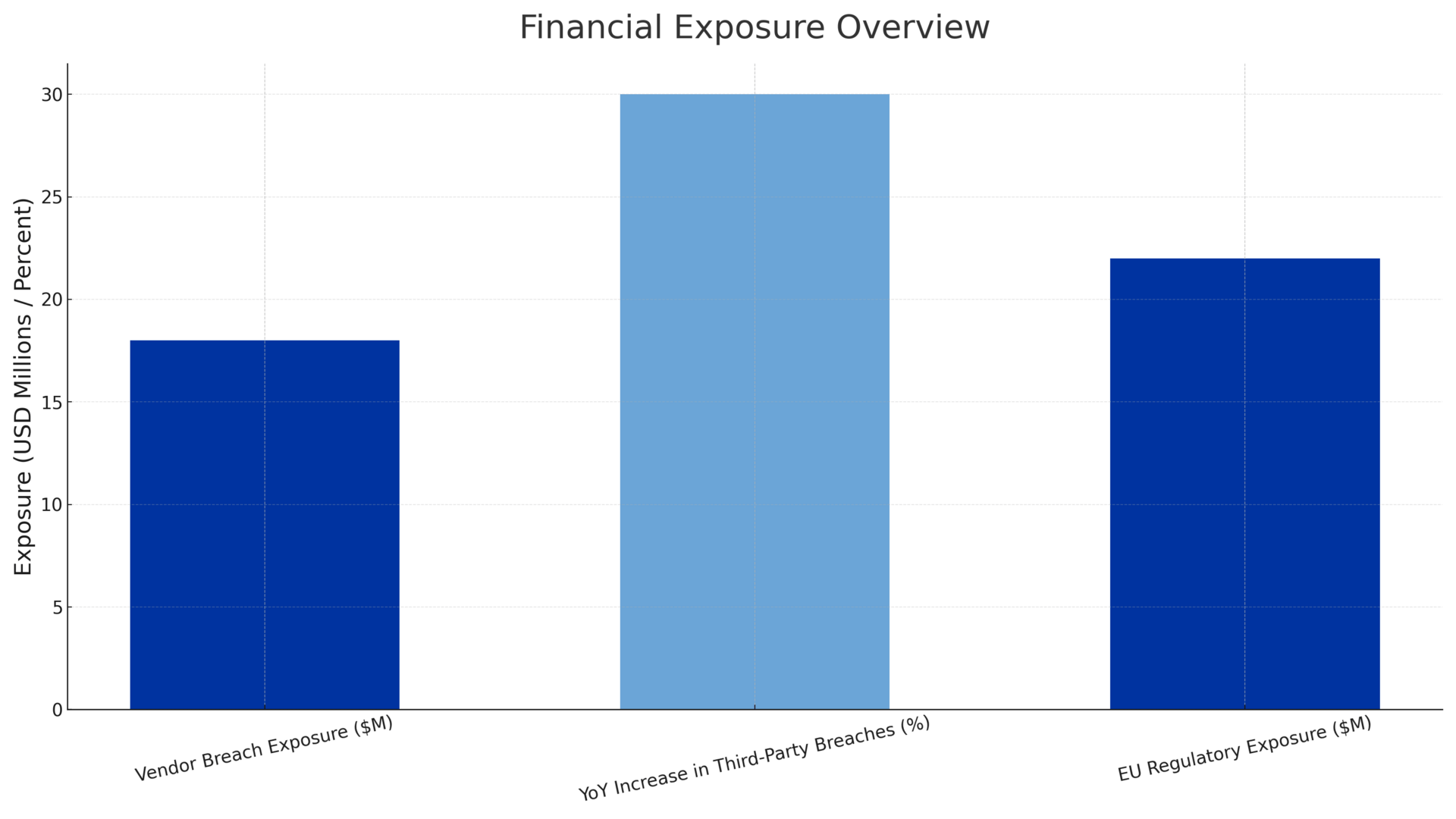
Executive Summary: Lift Directly Into Board Presentation Financial Exposure: Three supply chain breaches this week confirm third-party compromise as the dominant breach vector. Verizon DBIR reports third parties account for 30% of breaches, up 15% YoY. Each breach notification costs $150-$200 per record (Ponemon). If our average vendor processes 100,000 records, each vendor breach creates $15-20M direct exposure before regulatory fines or litigation. Regulatory Liability: FCC eliminated mandatory telecom security requirements while DORA/NIS2 expand EU obligations. Our U.S. operations now depend on voluntary carrier security. Our EU operations face binding requirements exceeding U.S. standards. Compliance posture divergence between jurisdictions creates audit risk and potential enforcement exposure in EU markets. Operational Risk: AI-orchestrated attacks are now operational. Anthropic documented an autonomous campaign executing thousands of requests per second. Our SOC is staffed and tooled for human-speed threats. Mean-time-to-detect assumptions built into our current architecture do not account for machine-speed lateral movement. This is a structural gap, not a tuning issue. Executive Accountability: Congressional testimony on AI-enabled attacks occurs December 17. Board awareness of this threat category should precede media coverage. Recommend briefing item for next board meeting covering: (1) current third-party risk posture, (2) SOC capability against automated threats, (3) defensive AI investment roadmap. Metrics for Ongoing Visibility: Vendor dependency count per critical process | Mean time to detect anomalous API behavior | Third-party integrations with elevated privileges | Days since Tier-1 vendor security validation | Compliance gap ratio (U.S. vs. EU controls) |
WEEK AHEAD
• Oracle Identity Manager CVE-2025-61757 | Deadline: December 12 SANS evidence suggests exploitation began August 2025. If OIM manages privileged access, treat this as a compromise investigation, not a patching exercise. Review access logs for the vulnerable endpoint since August.
• Congressional AI Testimony | December 17 Anthropic CEO, Google Cloud CEO, Quantum Xchange CEO before House Homeland Security. Policy proposals will follow. Brief your board before this becomes a media event they learn about without you.
• Salesforce/Gainsight Forensics | Ongoing Mandiant report expected. ShinyHunters threatened extortion site. Prepare incident response if your organization is named. The list of affected companies is still growing.
• Operation WrtHug | Active 50,000+ ASUS routers compromised for Chinese espionage ORB network. Half of infections are in Taiwan. Affected models include RT-AC1200HP, GT-AC5300, DSL-AC68U. Audit SOHO device inventory. Replace end-of-life equipment in remote work scenarios before it becomes infrastructure for someone else's campaign.
THE NEXT FAILURE MODE
Prediction: What Breaks Next OAuth supply-chain automation meets AI attackers by Q1 2026. ShinyHunters demonstrated that OAuth tokens harvested from one SaaS breach enable pivot into interconnected ecosystems. Anthropic demonstrated that AI agents can autonomously execute reconnaissance, exploitation, and lateral movement at machine speed. The convergence is inevitable: AI-driven lateral movement campaigns that automatically map SaaS token relationships and propagate across connected ecosystems faster than any human SOC can respond. The weak signal to watch: Credential-stuffing attacks against SaaS admin panels that do not trigger traditional volumetric alerts because the AI adapts request patterns in real time. If your SaaS monitoring relies on threshold-based detection, you will miss the first wave. Preemptive action: Deploy behavioral analytics on SaaS API traffic. Establish baseline for normal token usage patterns. Instrument alerting for anomalous cross-application API calls. The organizations that build this visibility in Q4 will detect what the organizations that wait until Q1 will only read about in breach disclosures. |
THE BOTTOM LINE
The security assumptions embedded in your current architecture are being systematically invalidated. Vendor trust. Human-speed detection. Perimeter-centric identity. Regulatory baseline. Each was reasonable when established. Each is now a liability.
The organizations that recognized this shift six months ago are better positioned today. The organizations that recognize it now will be better positioned in six months. The organizations that wait for their own breach to force the recognition will spend the next two years in recovery mode.
The question is not whether your architecture needs to change. The question is whether you change it on your timeline or on the attacker's.
CISO Tactical Intelligence Report | Nov 20–26, 2025
Complete operational intelligence for premium subscribers: Detailed threat analysis with IOCs and detection rules • Critical vulnerability deep-dives with patch guidance • Ransomware defensive playbooks • Full CISO podcast insights and frameworks • Market intelligence and vendor evaluation • Curated technical resources with analysis
—CybersecurityHQ

Reply