- Defend & Conquer
- Posts
- CISO Weekly Intelligence Brief | Nov 27– Dec 3, 2025
CISO Weekly Intelligence Brief | Nov 27– Dec 3, 2025
CybersecurityHQ — Tactical intelligence for enterprise security leaders

Welcome reader to your CybersecurityHQ CISO Weekly Intelligence Brief.
Brought to you by:
👣 Smallstep – Secures Wi-Fi, VPNs, ZTNA, SaaS and APIs with hardware-bound credentials powered by ACME Device Attestation
📊 LockThreat – AI-powered GRC that replaces legacy tools and unifies compliance, risk, audit and vendor management in one platform
About CybersecurityHQ
CybersecurityHQ provides executive-grade intelligence read weekly inside the Fortune 100. Each briefing is designed to support CISO-level decision-making across identity, infrastructure, third-party risk, and strategic security architecture.
CISO Access
CISOs receive full complimentary access to all CybersecurityHQ strategic intelligence.
If you’d like access or have questions, contact me directly here.
Week of December 3, 2025 | Coverage: November 27 – December 3, 2025
OAuth tokens are the new stolen credentials.
If you cannot revoke every third-party token within 24 hours, you do not control your environment.
1. THE STRUCTURAL COLLAPSE
The SaaS integration layer has failed as a trust boundary. This is not a prediction—it happened this week.
The Gainsight-Salesforce breach affecting 200+ organizations—including GitLab, Verizon, CrowdStrike, and F5—demonstrates that OAuth tokens are now weaponized at industrial scale through cascading supply chain compromise. ShinyHunters operators exploited credentials stolen in August's Salesloft Drift breach to pivot into Gainsight's Salesforce connector, then systematically harvested refresh tokens granting persistent access to customer CRM environments.
The architectural failure is absolute: MFA is now irrelevant for third-party access. Refresh tokens designed for convenience bypass every authentication control you've implemented. They persist for 90 days. They survive password resets. They grant access without user interaction.
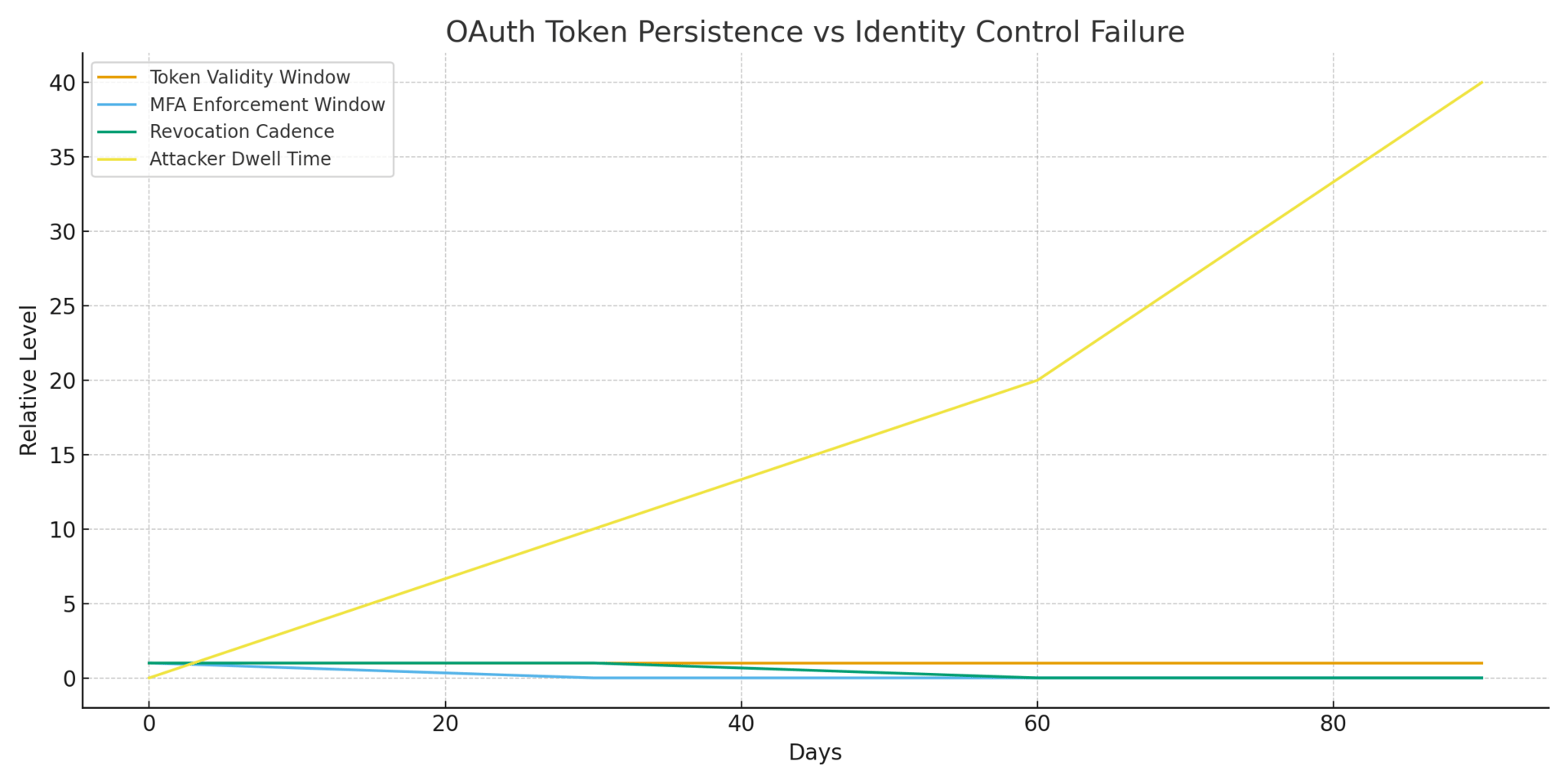
Simultaneously, INC Ransom's attack on the OnSolve CodeRED emergency alert platform disabled critical public safety infrastructure across 10,000+ U.S. municipalities. The attackers maintained persistence for nine days before detonating ransomware. The vendor stored passwords in plaintext. This is not negligence by one company—this is the baseline for critical infrastructure vendors in 2025.
Meanwhile, Clop's Oracle E-Business Suite campaign has expanded to 100+ victims including Harvard and The Washington Post, with ransom demands reaching $50 million. They exploited CVE-2025-61882 for seven weeks before Oracle's emergency patch—and they're still exploiting it against organizations that haven't applied it.
Broken assumption: Third-party OAuth integrations operate within your security perimeter.
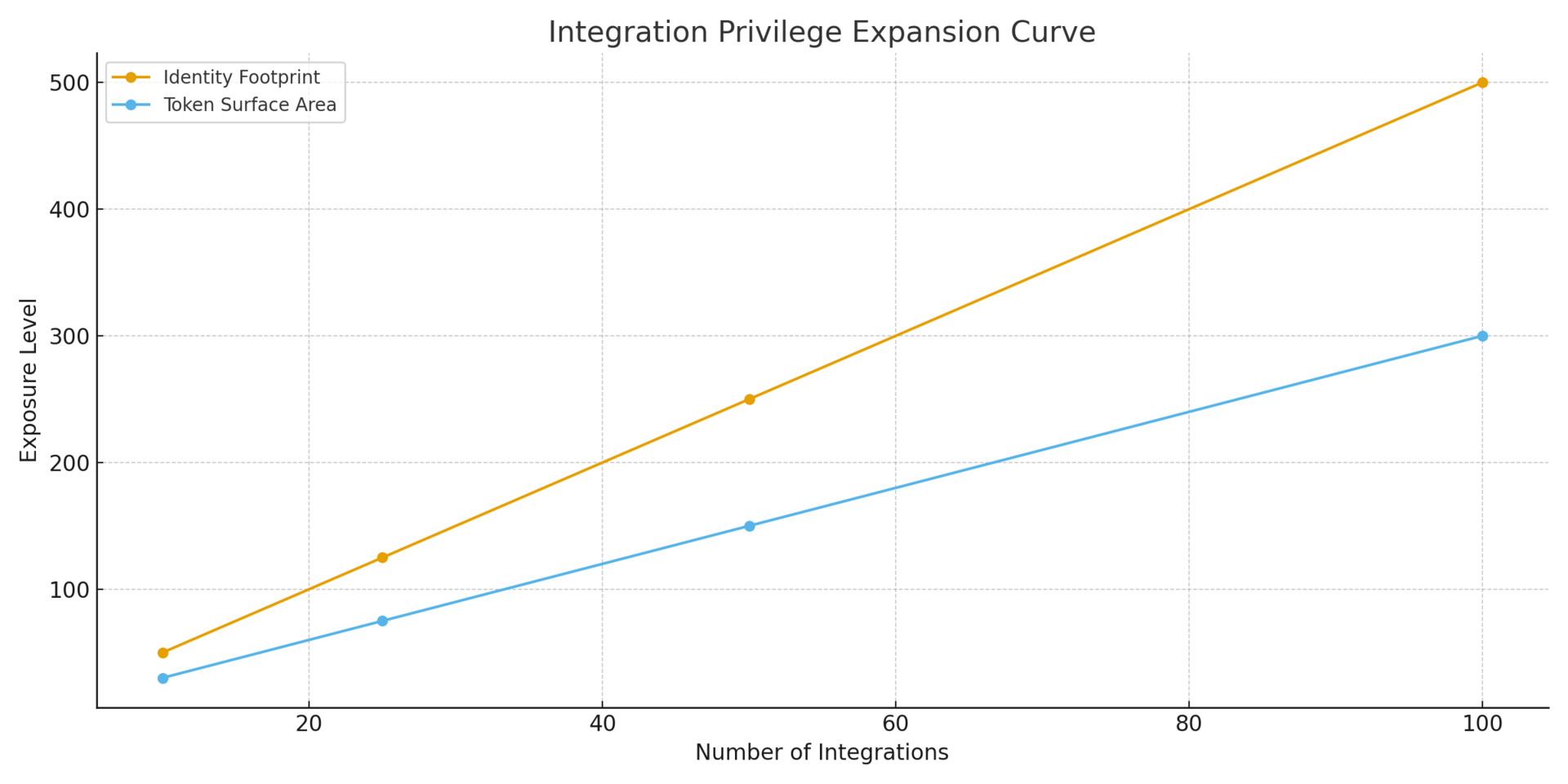
Replacement: Every refresh token is a persistent credential that bypasses MFA and persists across sessions. Integrations are identities. Vendor security is now part of your identity perimeter.
2. THREE STRATEGIC DECISIONS (Not Tasks)
These are not items for your team to check off. These are operating model shifts that require your decision authority.
Decision 1: Accept that your identity perimeter now includes every connected vendor
The forcing function: Attackers have announced plans to launch a dedicated leak site for Salesforce data from 1,000 combined Salesloft and Gainsight victims. Ransom demands are active. Exposed data includes customer PII, sales records, and embedded credentials harvested from CRM fields—AWS keys, Snowflake tokens, credentials your teams stored in 'notes' fields.
The decision: Mandate OAuth token inventory across all SaaS platforms within 14 days. Implement 30-day maximum token expiration. Block new integrations pending security review. If an integration has not been actively used in 90 days, revoke it by December 6.
The alternative: Wait for your organization to appear on a leak site, then explain to your board why credentials stolen from a vendor you don't directly contract with enabled access to your most sensitive data.
Decision 2: Treat critical infrastructure vendors as extensions of your own security posture
The forcing function: Emergency alert systems went dark for 10,000+ communities. When CodeRED failed, municipalities couldn't send evacuation orders, severe weather warnings, or active-shooter alerts. The vendor maintained legacy systems with plaintext passwords.
Government customers had no contractual leverage to enforce even basic security controls. Their operational continuity depended entirely on a vendor they could not inspect. CodeRED serves over 400 million alert recipients across U.S. municipalities—several counties reported inability to issue severe weather warnings during the nine-day dwell period.
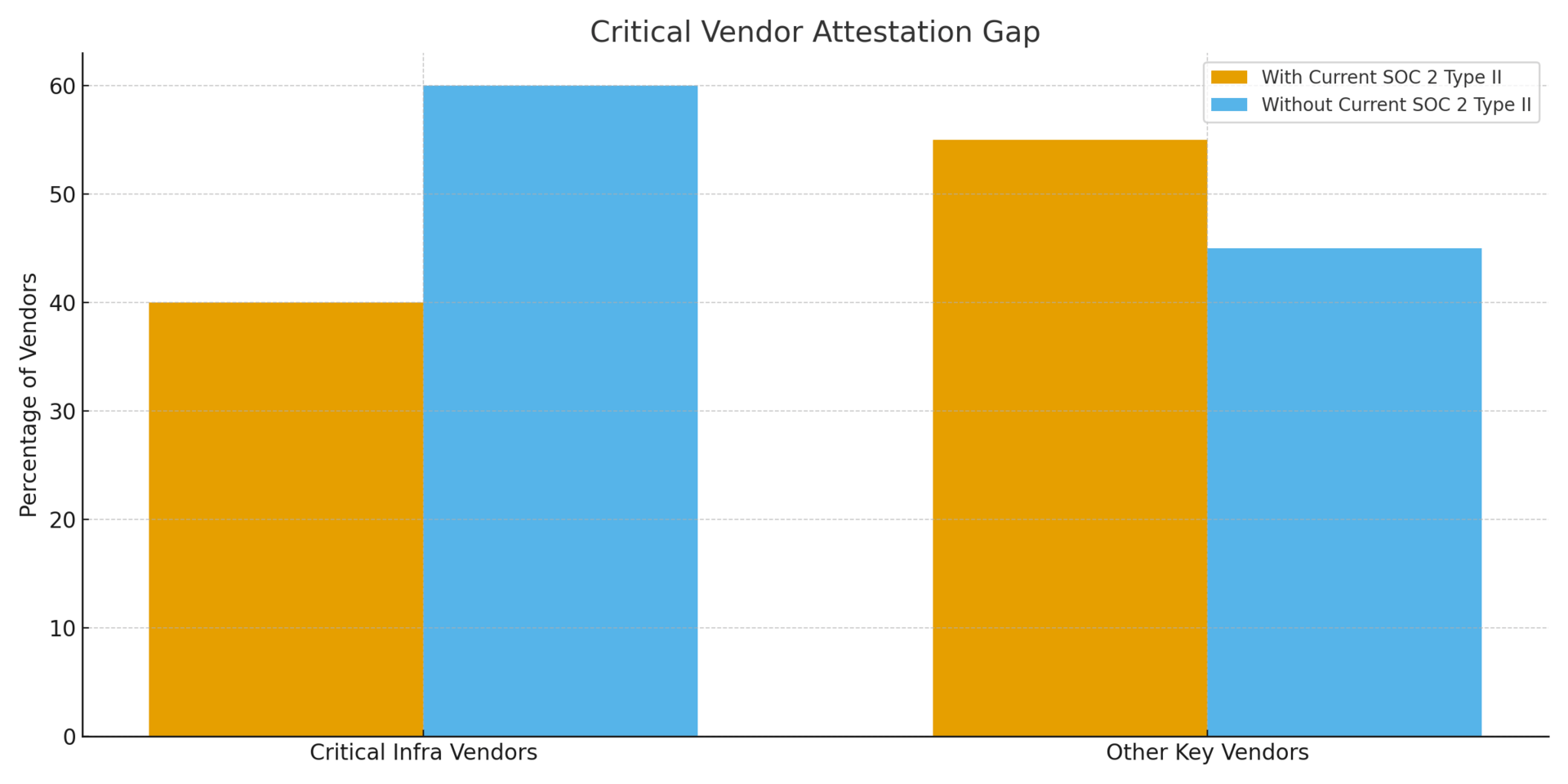
The decision: Review all critical infrastructure vendor contracts for security attestation requirements by December 9. Mandate SOC 2 Type II annual recertification. Establish redundant communication channels—IPAWS/Wireless Emergency Alerts, social media, local broadcast—for any third-party alerting dependency. If your organization uses CodeRED: force password resets immediately and verify backup systems are operational.
The alternative: Discover your vendor's security posture during an incident, when your ability to respond depends on systems you cannot control or verify.
Decision 3: Assume Clop is already in your Oracle environment
The forcing function: Clop exploited CVE-2025-61882 for seven weeks before Oracle's emergency patch. They have 100+ victims on their leak site. Ransom demands have reached $50 million. Harvard confirmed breach within a 'small administrative unit'—scope expands as investigations proceed. EBS holds financial, payroll, and supply-chain data; compromise at this layer creates multi-quarter operational and regulatory impact. Data theft occurs before encryption—paying ransom does not prevent leak.
The decision: Apply the emergency patch (October 2025 CPU prerequisite + CVE-2025-61882 fix) within 7 days—before the CISA KEV deadline of December 12. Hunt for IOCs immediately: IPs 200.107.207.26, 185.181.60.11; reverse shell commands. Review EBS internet exposure—any public-facing EBS component creates unacceptable risk.
The alternative: Miss the CISA deadline, face regulatory exposure if you're a federal contractor, and discover you've been compromised when Clop adds your name to their leak site.
3. SIGNALS THAT MATTER
Signal 1: OAuth Token Persistence Has Replaced Credential Theft
Attackers now target refresh tokens that grant 90-day persistent access without MFA challenges. The Salesloft→Gainsight chain proves tokens stolen from one vendor cascade through OAuth trust relationships. The control that failed: MFA enforcement—tokens bypass authentication entirely.
Board Metric: Percentage of third-party integrations with refresh tokens exceeding 30-day validity.
Signal 2: Critical Infrastructure Vendors Operating Without Adequate Controls
Emergency alert provider stored passwords in plaintext, maintained legacy systems alongside new platform, and enabled nine-day undetected persistence. Public safety depends on vendor security postures organizations cannot verify or enforce.
Board Metric: Number of critical vendors without SOC 2 Type II attestation dated within 12 months.
Signal 3: Nation-State Actors Adopting Commercial RMM Tools
Iranian APT MuddyWater's use of legitimate Atera, Level, PDQ, and SimpleHelp tools means attribution becomes impossible and blocklisting impractical. They're targeting technology, manufacturing, utilities, and transportation sectors using a novel Fooder loader disguised as a Snake game. Credential harvesting via fake Windows Security dialogs.
Board Metric: RMM tool inventory accuracy—tools discovered vs. tools authorized.
Immediate action: Check for unauthorized Atera, Level, PDQ, and SimpleHelp installations by December 8.
4. OPERATIONAL MANDATES
• Android December 2025 security update (CVE-2025-48572, privilege escalation): CISA KEV deadline December 19. Active exploitation confirmed in targeted attacks. Enterprise MDM policies must enforce update compliance. Block non-compliant devices from corporate resources.
• WatchGuard Firebox CVE-2025-9242: CISA KEV deadline was December 3. Verify patch applied to all Firebox instances. 54,000+ devices remain vulnerable globally.
5. BOARD-READY SUMMARY
Financial Exposure
Clop ransom demands have reached $50 million for Oracle EBS victims. The Gainsight breach affects 200+ enterprises with potential regulatory fines under GDPR/CCPA—average breach cost now $4.88 million. Supply chain compromises carry 15% cost premium and 267-day average detection time. Third-party involvement in breaches has doubled to 30% in 2025.
Regulatory Liability
CISA KEV additions create binding remediation deadlines for federal contractors: CVE-2025-61882 (Oracle EBS) due December 12; CVE-2025-48572/48633 (Android) due December 19. Organizations subject to BOD 22-01 face compliance violations for missed deadlines. Salesforce breach notifications required under state privacy laws for customer data exposure.
Operational Risk
Capability gap exposed: Organizations lack visibility into OAuth token inventory, third-party integration permissions, and non-human identity governance.
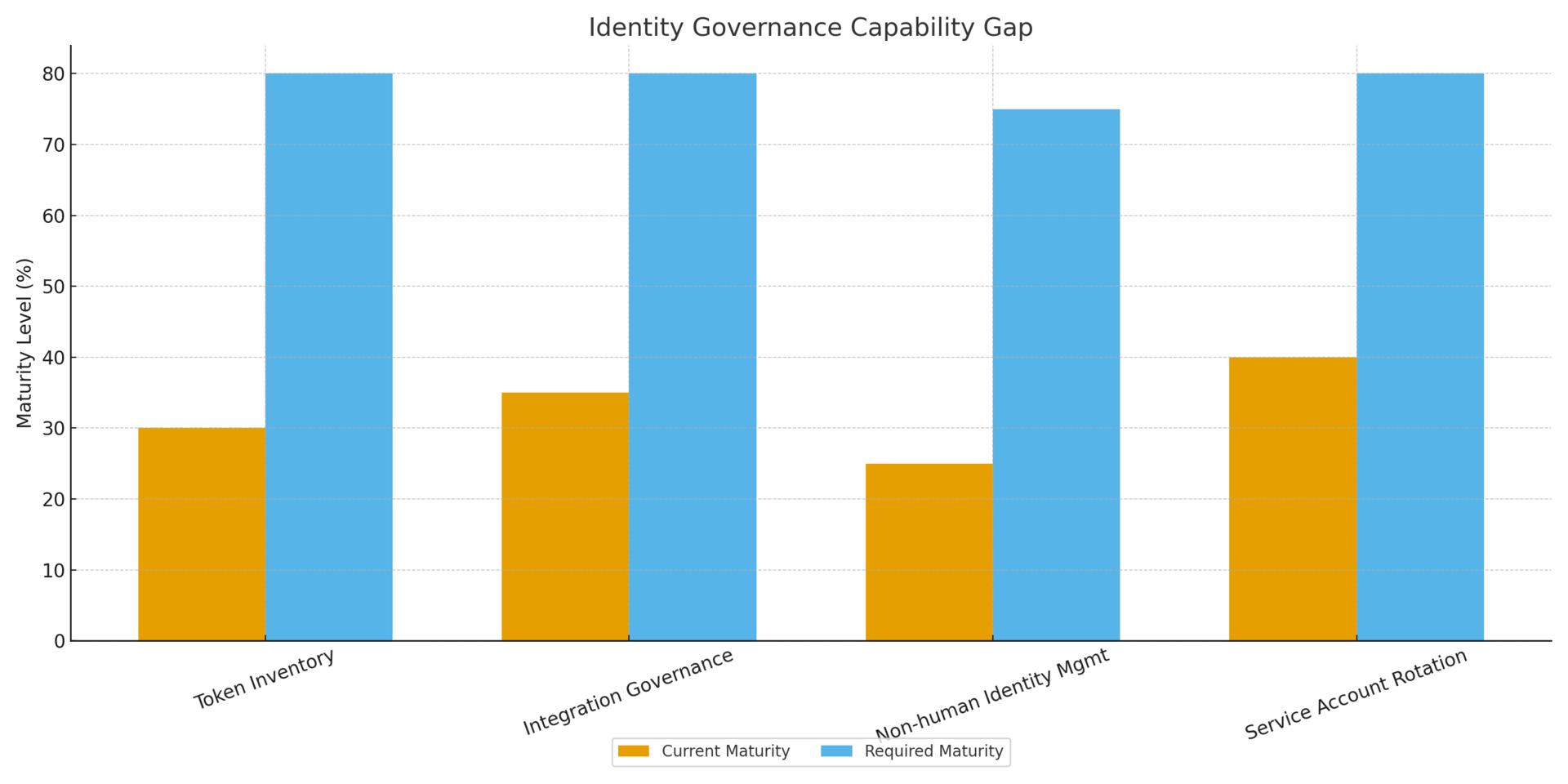
Detection/response mismatch: Attackers maintain multi-week dwell times (9 days for CodeRED, 7+ weeks for Oracle EBS) before human-speed detection identifies compromise.
Executive Accountability
Three events make security unavoidable on board agendas: (1) Gainsight breach affecting Fortune 500 companies demonstrates that vendor security failures cascade through trust relationships. (2) CodeRED attack on public safety infrastructure demonstrates that third-party vendor security creates shared liability. (3) Iranian nation-state targeting critical infrastructure requires board-level awareness of geopolitical cyber risk.
Metrics for Ongoing Visibility
1. OAuth token inventory coverage: Percentage of SaaS platforms with complete refresh token enumeration
2. Third-party integration risk score: Count of connected apps with permissions exceeding business need
3. CISA KEV remediation velocity: Days from KEV addition to organizational patch completion
4. Critical vendor security attestation currency: Vendors with SOC 2 Type II dated within 12 months
5. RMM tool drift: Unauthorized remote management tools detected vs. baseline inventory
6. WEEK AHEAD
DATE | EVENT & REQUIRED ACTION |
Dec 3 | CISA KEV deadline: WatchGuard Firebox CVE-2025-9242. Verify patch applied to all Firebox instances. 54,000+ devices remain vulnerable globally. |
Dec 5 | AWS re:Invent concludes. Monitor for security service announcements requiring configuration changes. |
Dec 10 | Microsoft Patch Tuesday. Expect zero-day disclosures. Pre-position change windows for emergency deployment. |
Dec 12 | CISA KEV deadline: Oracle EBS CVE-2025-61882 + Oracle Identity Manager CVE-2025-61757. CRITICAL—active Clop exploitation. |
Dec 19 | CISA KEV deadline: Android CVE-2025-48572/48633. MDM enforcement required for enterprise devices. |
Ongoing | Clop Oracle EBS extortion campaign active. Monitor leak site for victim additions. Prepare incident response if listed. |
7. THE NEXT FAILURE MODE
Prediction: AI Coding Agents Will Become Primary Supply Chain Attack Vector by Q2 2026
Convergence of trends: This week, security researcher Aaron Portnoy demonstrated exploitation of Google's Antigravity AI coding tool within 24 hours of release—injecting malicious source code that creates backdoors through configuration manipulation. Anthropic disclosed disruption of the first fully AI-orchestrated cyber campaign where Claude performed 80-90% of attack operations autonomously. AI-generated phishing achieves 54% click-through rate vs. 12% for traditional campaigns (Microsoft). Organizations are deploying AI coding assistants with broad repository access before security controls exist.
Timeframe: Q2 2026. Mass adoption of AI coding agents in enterprise development pipelines will create ubiquitous attack surface. Attackers will target agent configuration files, model context protocols, and training data to inject malicious code at scale.
Verification signal: CVE issuance for AI coding tool vulnerabilities; major enterprise breach attributed to AI agent compromise; regulatory guidance on AI tool security controls.
Preemptive action: Inventory all AI coding tools in development environments. Establish security review requirements before AI agent deployment. Implement code signing and provenance verification for AI-generated code. Monitor for unauthorized AI tool installation via EDR.
8. THE BOTTOM LINE
If you believed your SaaS security ended at platform authentication, this week proved OAuth integrations extend your attack surface to every connected vendor's security posture. The Gainsight breach cascaded through Salesloft Drift credentials stolen three months ago. Tokens granted for convenience became persistent access that bypassed every authentication control. The 2025 DBIR confirms third-party involvement in breaches doubled to 30%—this week demonstrated exactly how that happens at enterprise scale.
Acting now means: Revoking unused OAuth tokens, enforcing 30-day token expiration, patching Oracle EBS before Clop lists you, and establishing vendor security attestation requirements. Delaying means: Discovering your organization on an extortion site, explaining to the board why credentials stolen from a vendor you don't directly contract with enabled access to your most sensitive data, and facing regulatory scrutiny for missed CISA KEV deadlines.
The question the CISO must answer: Do you have complete visibility into every OAuth refresh token, connected application, and non-human identity accessing your critical SaaS platforms—and can you revoke any of them within 24 hours?

Reply