- Defend & Conquer
- Posts
- Comparing the effectiveness of security frameworks in reducing infrastructure-as-code risks with minimal developer burden
Comparing the effectiveness of security frameworks in reducing infrastructure-as-code risks with minimal developer burden
CybersecurityHQ Report - Pro Members
Welcome reader to a 🔒 pro subscriber-only deep dive 🔒.
Brought to you by:
👣 Smallstep – Secures Wi-Fi, VPNs, ZTNA, SaaS and APIs with hardware-bound credentials powered by ACME Device Attestation
🏄♀️ Upwind Security – Real-time cloud security that connects runtime to build-time to stop threats and boost DevSecOps productivity
🔧 Endor Labs – App security from legacy C++ to Bazel monorepos, with reachability-based risk detection and fix suggestions across the SDLC
📊 LockThreat – AI-powered GRC that replaces legacy tools and unifies compliance, risk, audit and vendor management in one platform
Forwarded this email? Join 70,000 weekly readers by signing up now.
#OpenToWork? Try our AI Resume Builder to boost your chances of getting hired!
—
Get lifetime access to our deep dives, weekly cyber intel podcast report, premium content, AI Resume Builder, and more — all for just $799. Corporate plans are now available too.
Executive Summary
Infrastructure-as-Code (IaC) has revolutionized how organizations provision and manage cloud infrastructure, enabling unprecedented speed and scalability. However, this transformation introduces significant security risks that demand sophisticated frameworks capable of detecting and preventing vulnerabilities without hampering developer productivity. This whitepaper examines the comparative effectiveness of different security frameworks for securing IaC, based on a comprehensive analysis of 24 studies covering various approaches from static analysis to AI-driven solutions.
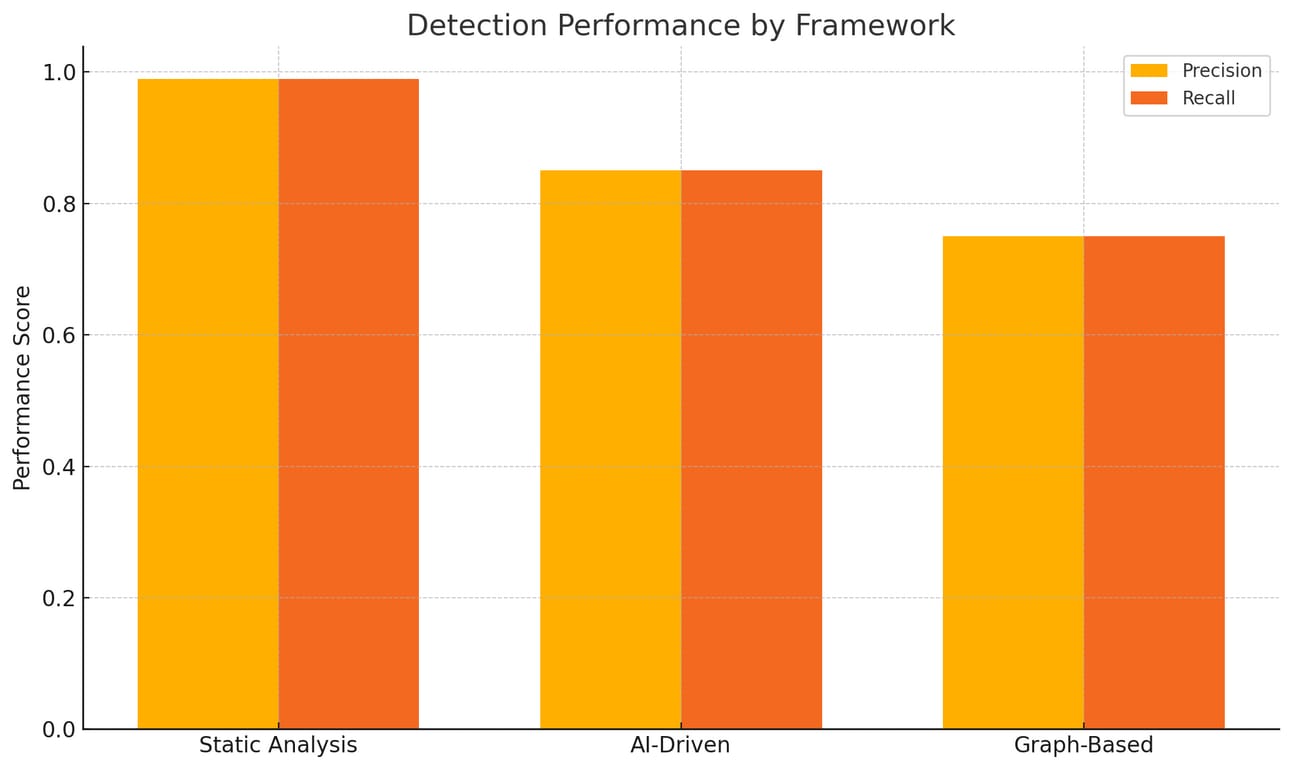
Our analysis reveals that static analysis tools achieve near-perfect detection rates (0.99 precision and recall) for IaC vulnerabilities, while AI-driven approaches reach 85% accuracy but require more developer oversight due to false positives. The research demonstrates that organizations can achieve up to 78% reduction in misconfigurations through proper framework implementation. Most importantly, the integration complexity remains manageable, with most frameworks requiring only moderate effort to implement into existing development workflows.
For Chief Information Security Officers (CISOs) and security leaders, the key finding is clear: securing IaC effectively requires selecting frameworks that balance high detection rates with minimal developer friction. The most successful approaches embed security directly into development workflows through automation, policy-as-code, and intelligent tooling that provides immediate feedback without blocking productivity.

Subscribe to CybersecurityHQ Newsletter to unlock the rest.
Become a paying subscriber of CybersecurityHQ Newsletter to get access to this post and other subscriber-only content.
Already a paying subscriber? Sign In.
A subscription gets you:
- • Access to Deep Dives and Premium Content
- • Access to AI Resume Builder
- • Access to the Archives
Reply