- Defend & Conquer
- Posts
- De‐risking digital transformation: Security as an enabler of cloud migration
De‐risking digital transformation: Security as an enabler of cloud migration
CybersecurityHQ Report - Pro Members

Welcome reader to a 🔒 pro subscriber-only deep dive 🔒.
Brought to you by:
👣 Smallstep – Secures Wi-Fi, VPNs, ZTNA, SaaS and APIs with hardware-bound credentials powered by ACME Device Attestation
📊 LockThreat – AI-powered GRC that replaces legacy tools and unifies compliance, risk, audit and vendor management in one platform
Forwarded this email? Join 70,000 weekly readers by signing up now.
#OpenToWork? Try our AI Resume Builder to boost your chances of getting hired!
—
Get lifetime access to our deep dives, weekly cyber intel podcast report, premium content, AI Resume Builder, and more — all for just $799. Corporate plans are now available too.
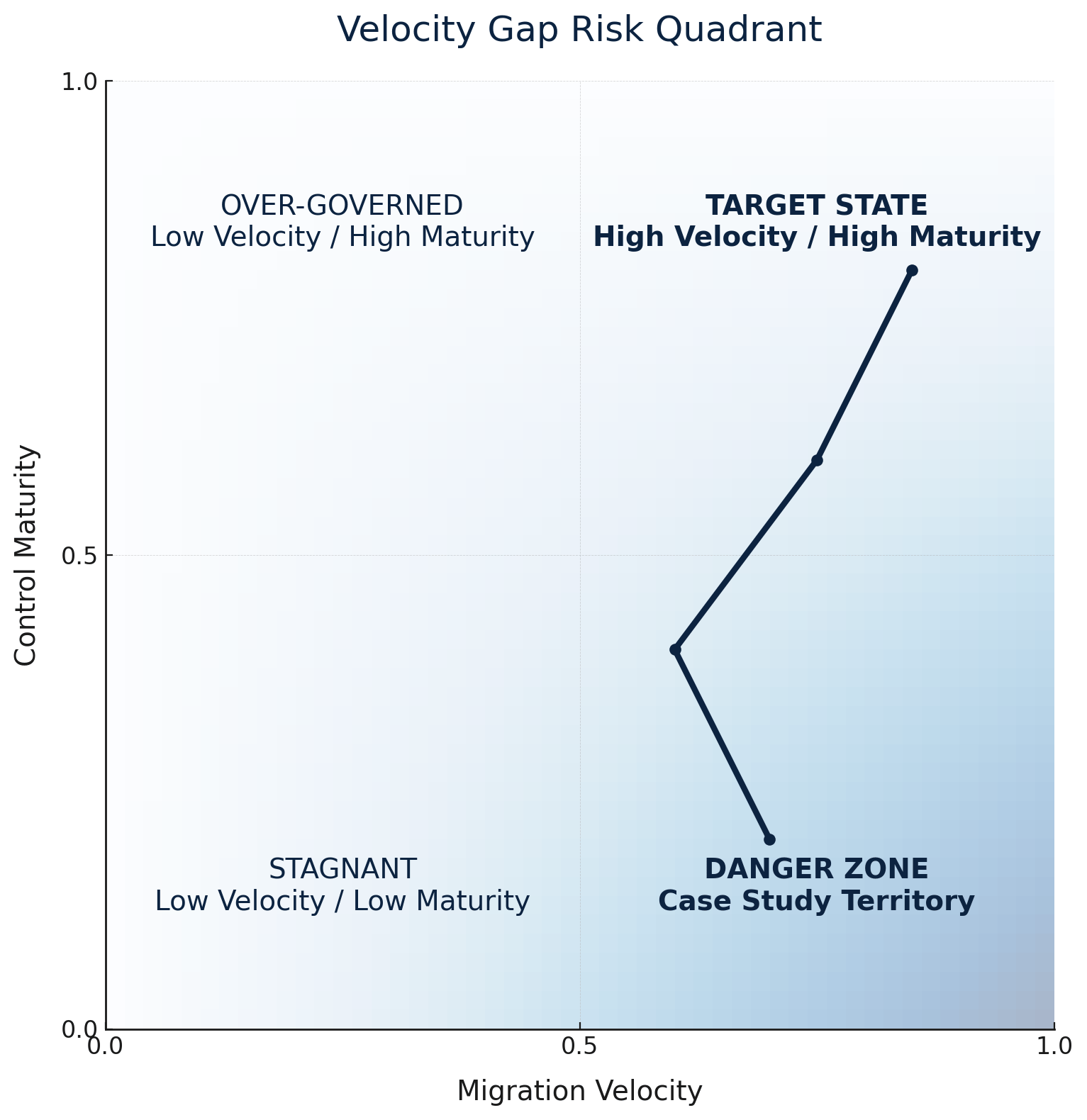
THE CORE THESIS: Enterprises fail at secure cloud migration not because threats are sophisticated, but because they migrate faster than they can govern. The resulting 12-18 month velocity gap concentrates 70% of cloud breach exposure. Organizations that do not close this gap do not recover. They become case studies.
Executive Summary
Cloud migration has become the central nervous system of digital transformation. Yet most enterprises approach it backward: optimizing for migration velocity while treating security as friction to be minimized. This fundamental inversion explains why 45% of breaches now occur in cloud environments, and why organizations with aggressive transformation timelines experience breach rates 2.3x higher than measured adopters.¹
The problem is not technology. It is sequencing. Organizations migrate faster than they can govern, creating systematic exposure windows that sophisticated attackers have learned to exploit with precision. The velocity gap between migration speed and control maturity has become the defining vulnerability of modern enterprise security.
This analysis introduces the Cloud Risk Velocity Model (CRVM), a diagnostic framework that reframes cloud security from compliance burden to velocity enabler. For CFOs, it provides a quantified financial exposure formula that translates security risk into capital allocation language. For COOs, it delivers operational resilience metrics aligned to regulatory requirements. For CISOs, it offers a board-ready resource allocation model that positions security investment as transformation acceleration rather than cost.
The core insight is counterintuitive: the enterprises that migrate most securely are not those that migrate most slowly. They are those that close the velocity gap between migration speed and control maturity. Speed without governance creates exposure. Governance without speed creates competitive disadvantage. The CRVM framework enables both simultaneously by focusing investment on the three controls that reduce 70% of migration-phase risk while enabling rather than inhibiting transformation velocity.

Subscribe to CybersecurityHQ Newsletter to unlock the rest.
Become a paying subscriber of CybersecurityHQ Newsletter to get access to this post and other subscriber-only content.
Already a paying subscriber? Sign In.
A subscription gets you:
- • Access to Deep Dives and Premium Content
- • Access to AI Resume Builder
- • Access to the Archives
Reply