- Defend & Conquer
- Posts
- Effective strategies for preventing and mitigating destructive malware in enterprise networks
Effective strategies for preventing and mitigating destructive malware in enterprise networks
CybersecurityHQ Report - Pro Members

Welcome reader to a 🔒 pro subscriber-only deep dive 🔒.
Brought to you by:
👣 Smallstep – Secures Wi-Fi, VPNs, ZTNA, SaaS and APIs with hardware-bound credentials powered by ACME Device Attestation
🏄♀️ Upwind Security – Real-time cloud security that connects runtime to build-time to stop threats and boost DevSecOps productivity
🔧 Endor Labs – App security from legacy C++ to Bazel monorepos, with reachability-based risk detection and fix suggestions across the SDLC
📊 LockThreat – AI-powered GRC that replaces legacy tools and unifies compliance, risk, audit and vendor management in one platform
🧠 Ridge Security – The AI-powered offensive security validation platform
Forwarded this email? Join 70,000 weekly readers by signing up now.
#OpenToWork? Try our AI Resume Builder to boost your chances of getting hired!
—
Get lifetime access to our deep dives, weekly cyber intel podcast report, premium content, AI Resume Builder, and more — all for just $799. Corporate plans are now available too.
Executive Summary
Destructive malware represents one of the most severe cybersecurity threats facing enterprises in 2025. Unlike traditional malware focused on data theft or financial gain, destructive variants aim to permanently destroy data, cripple operations, and inflict maximum damage. Recent attacks demonstrate the evolving sophistication of these threats, with state-sponsored actors and cybercriminal groups deploying wiper malware, ransomware without decryption capabilities, and hybrid attacks that blend multiple destructive techniques.
This whitepaper examines the current destructive malware landscape and provides enterprise security leaders with actionable strategies for prevention and mitigation. Based on analysis of recent incidents, emerging attack patterns, and proven defensive approaches, we present a comprehensive framework that addresses technical controls, organizational readiness, and recovery capabilities.
Key findings indicate that enterprises achieving the highest resilience against destructive malware share several characteristics: they implement network segmentation with zero-trust principles, maintain immutable offline backups, deploy advanced endpoint detection capabilities, and have well-rehearsed incident response procedures. Organizations following these practices report containing 95% of destructive malware incidents with recovery times under 72 hours, compared to weeks or months for unprepared enterprises.
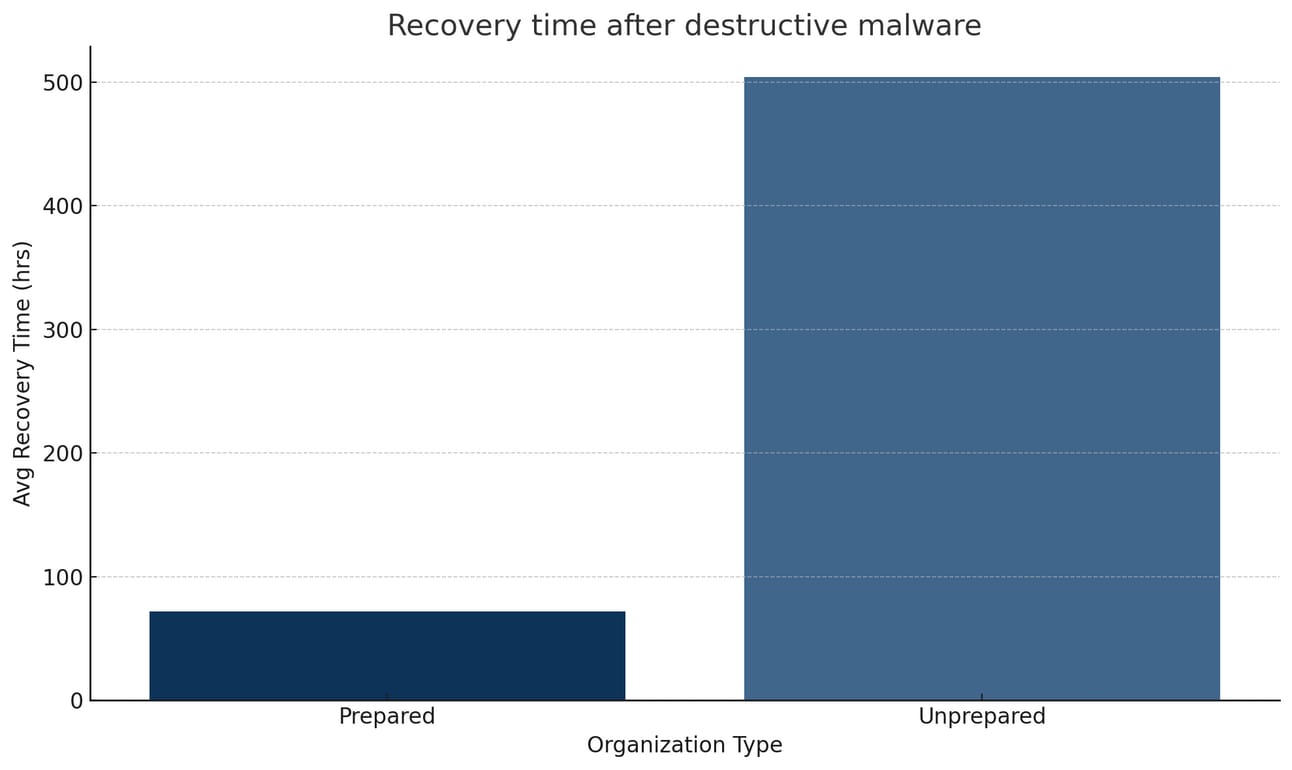
The strategic recommendations focus on three pillars: prevention through architecture hardening and access controls, detection via behavioral analytics and threat intelligence, and recovery through robust backup strategies and tested disaster recovery procedures. Success requires executive leadership engagement, cross-functional coordination, and sustained investment in both technology and human capabilities.

Subscribe to CybersecurityHQ Newsletter to unlock the rest.
Become a paying subscriber of CybersecurityHQ Newsletter to get access to this post and other subscriber-only content.
Already a paying subscriber? Sign In.
A subscription gets you:
- • Access to Deep Dives and Premium Content
- • Access to AI Resume Builder
- • Access to the Archives
Reply