- Defend & Conquer
- Posts
- Effective zero trust migration strategies for CISOs in OT and ICS environments
Effective zero trust migration strategies for CISOs in OT and ICS environments
CybersecurityHQ Report - Pro Members
Welcome reader to a 🔒 pro subscriber-only deep dive 🔒.
Brought to you by:
👣 Smallstep – Secures Wi-Fi, VPNs, ZTNA, SaaS and APIs with hardware-bound credentials powered by ACME Device Attestation
🏄♀️ Upwind Security – Real-time cloud security that connects runtime to build-time to stop threats and boost DevSecOps productivity
🔧 Endor Labs – App security from legacy C++ to Bazel monorepos, with reachability-based risk detection and fix suggestions across the SDLC
📊 LockThreat – AI-powered GRC that replaces legacy tools and unifies compliance, risk, audit and vendor management in one platform
Forwarded this email? Join 70,000 weekly readers by signing up now.
#OpenToWork? Try our AI Resume Builder to boost your chances of getting hired!
—
Get lifetime access to our deep dives, weekly cyber intel podcast report, premium content, AI Resume Builder, and more — all for just $799. Corporate plans are now available too.
Executive Summary
Operational Technology (OT) and Industrial Control Systems (ICS) networks face unprecedented cybersecurity challenges in 2025 as digital transformation accelerates convergence with IT systems. Traditional perimeter-based security models prove inadequate against sophisticated threats targeting critical infrastructure. Zero Trust architecture emerges as the essential framework for securing industrial environments, yet implementation remains complex due to legacy constraints, operational requirements, and cultural barriers.
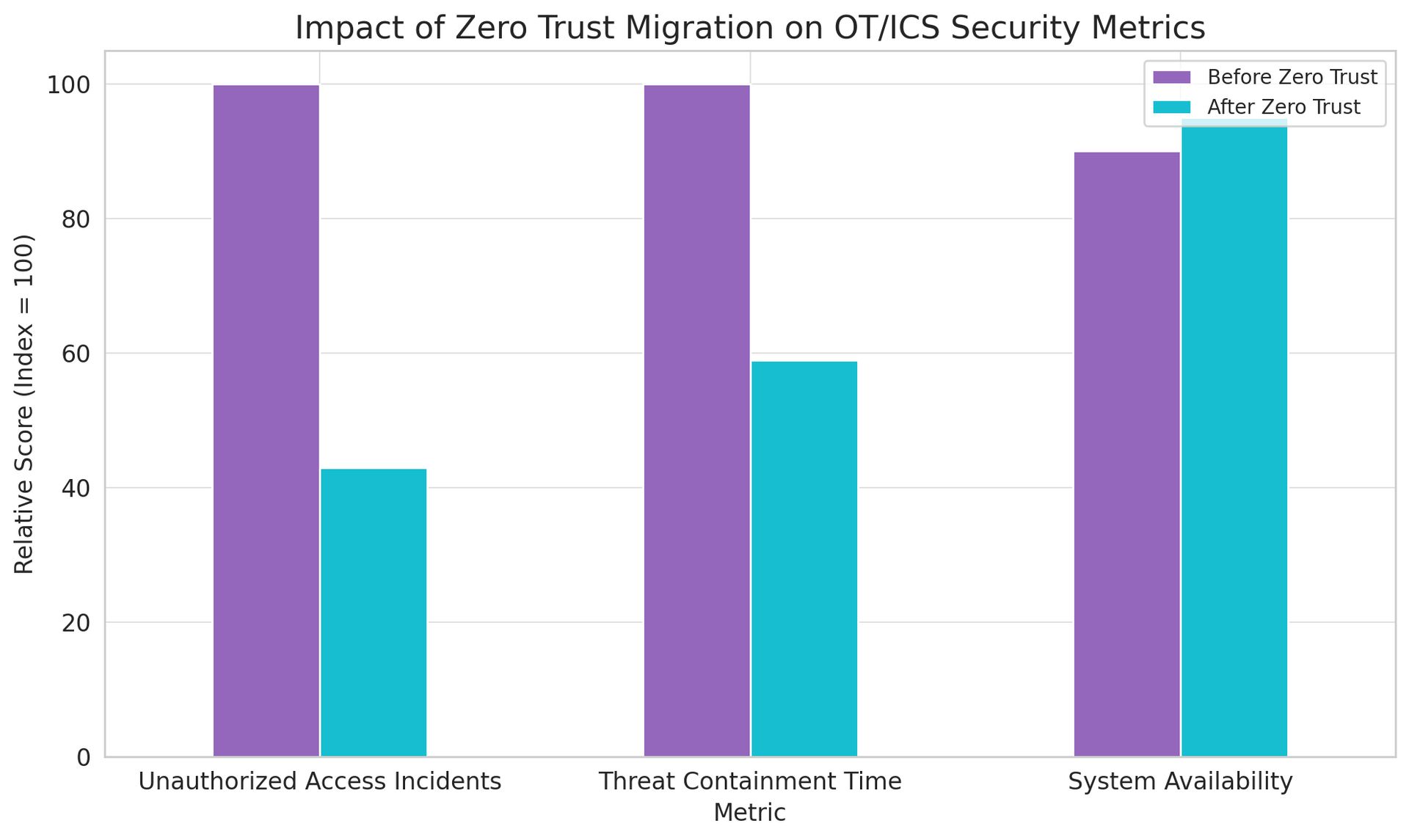
This whitepaper provides Chief Information Security Officers (CISOs) with actionable strategies for migrating OT/ICS networks to Zero Trust architectures. Based on recent industry research and real-world implementations, we outline practical approaches that balance security enhancement with operational continuity. Key findings indicate that organizations implementing phased Zero Trust migrations report 57% fewer unauthorized access incidents and 41% faster threat containment, while maintaining critical system availability above 95%.
The analysis covers fundamental challenges unique to OT environments, proven migration frameworks, technological solutions, and organizational transformation requirements. We present evidence-based recommendations for CISOs to lead successful Zero Trust initiatives that protect critical infrastructure without compromising industrial operations.

Subscribe to CybersecurityHQ Newsletter to unlock the rest.
Become a paying subscriber of CybersecurityHQ Newsletter to get access to this post and other subscriber-only content.
Already a paying subscriber? Sign In.
A subscription gets you:
- • Access to Deep Dives and Premium Content
- • Access to AI Resume Builder
- • Access to the Archives
Reply