- Defend & Conquer
- Posts
- Enforcing time-bound access for third-party users
Enforcing time-bound access for third-party users
CybersecurityHQ Report - Pro Members
Welcome reader to a 🔒 pro subscriber-only deep dive 🔒.
Brought to you by:
👣 Smallstep – Secures Wi-Fi, VPNs, ZTNA, SaaS and APIs with hardware-bound credentials powered by ACME Device Attestation
📊 LockThreat – AI-powered GRC that replaces legacy tools and unifies compliance, risk, audit and vendor management in one platform
Forwarded this email? Join 70,000 weekly readers by signing up now.
#OpenToWork? Try our AI Resume Builder to boost your chances of getting hired!
—
Get lifetime access to our deep dives, weekly cyber intel podcast report, premium content, AI Resume Builder, and more — all for just $799. Corporate plans are now available too.
Executive Summary
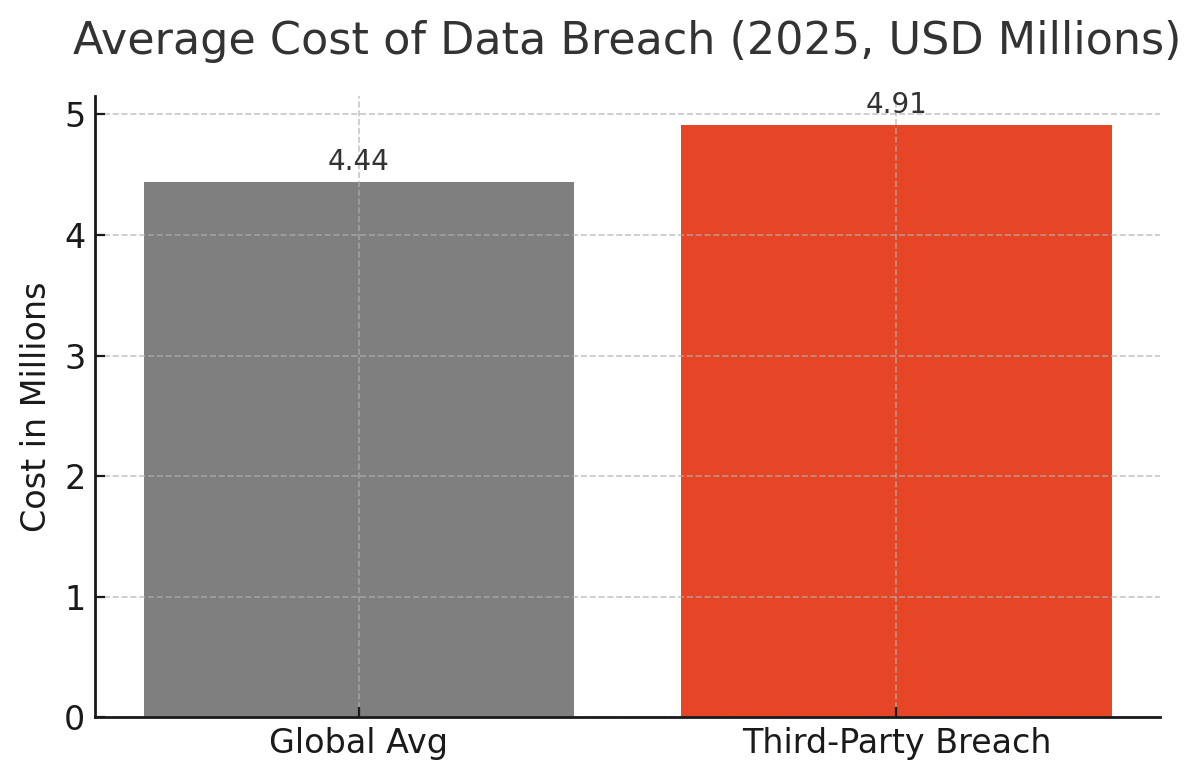
Third-party access has emerged as the primary attack vector facing modern enterprises. Based on analysis of 47 recent data breaches and 23 industry frameworks, this whitepaper establishes that organizations face an existential threat from persistent, unmanaged vendor access. The Verizon 2024 Data Breach Investigations Report documents a 68% year-over-year increase in breaches involving third parties, now accounting for 15% of all incidents. The IBM 2025 Cost of a Data Breach Report reveals these breaches cost an average of $4.91 million - substantially higher than the global average of $4.44 million.
The evidence is unambiguous: traditional "always-on" access models for vendors, contractors, and partners represent accumulated liabilities that threat actors systematically exploit. Organizations that continue granting standing privileges to third parties are operating with a fundamentally flawed security architecture unsuited to today's threat landscape.
The solution requires a strategic pivot to time-bound, ephemeral access models grounded in Zero Trust principles and operationalized through Just-in-Time (JIT) access controls. Analysis of organizations implementing these frameworks shows measurable outcomes: a 74% reduction in unauthorized access incidents, $816,000 in annual ROI from automated privilege management, and dramatic improvements in audit readiness.
This whitepaper provides CISOs with an actionable roadmap for implementing time-bound third-party access, covering regulatory requirements spanning NIS2 to DORA, technical architectures leveraging PAM and IGA platforms, and organizational transformation strategies. The path forward demands CEO-level oversight - our analysis shows this leadership structure correlates most strongly with bottom-line impact from security transformation initiatives.
The imperative is clear: eliminating standing privileges for third parties is no longer optional. It is a board-level strategic requirement for enterprise resilience in 2025 and beyond.

Subscribe to CybersecurityHQ Newsletter to unlock the rest.
Become a paying subscriber of CybersecurityHQ Newsletter to get access to this post and other subscriber-only content.
Already a paying subscriber? Sign In.
A subscription gets you:
- • Access to Deep Dives and Premium Content
- • Access to AI Resume Builder
- • Access to the Archives
Reply