- Defend & Conquer: CISO-Grade Cyber Intel Weekly
- Posts
- Enterprise policy for how business units may invoke MCPs
Enterprise policy for how business units may invoke MCPs
CybersecurityHQ Report - Pro Members
Welcome reader to a 🔒 pro subscriber-only deep dive 🔒.
Brought to you by:
👣 Smallstep – Secures Wi-Fi, VPNs, ZTNA, SaaS and APIs with hardware-bound credentials powered by ACME Device Attestation
📊 LockThreat – AI-powered GRC that replaces legacy tools and unifies compliance, risk, audit and vendor management in one platform
Forwarded this email? Join 70,000 weekly readers by signing up now.
#OpenToWork? Try our AI Resume Builder to boost your chances of getting hired!
—
Get lifetime access to our deep dives, weekly cyber intel podcast report, premium content, AI Resume Builder, and more — all for just $799. Corporate plans are now available too.
Executive Summary
The Model Context Protocol (MCP), introduced by Anthropic in November 2024, has rapidly emerged as critical infrastructure for enterprise AI deployment. Based on analysis of 47 documented enterprise MCP implementations across financial services, healthcare, and technology sectors, combined with security assessments of 156 open-source MCP servers, this whitepaper establishes that organizations face a fundamental governance challenge: enabling business unit innovation while preventing the proliferation of unvetted AI integrations that expose sensitive data and create compliance gaps.
Research from McKinsey's 2025 State of AI survey reveals that 71% of organizations now regularly use generative AI in at least one business function, yet only 21% have fundamentally redesigned workflows to capture value safely. More critically, our analysis of 23 industry frameworks (including NIST AI RMF, ISO 42001, and EU AI Act requirements) shows that organizations are managing an average of 8.3 distinct gen-AI-related risks, with inaccuracy, cybersecurity, and intellectual property infringement ranking as the top three concerns that have caused documented business impact.
The core challenge for CISOs is velocity versus control. Business units increasingly deploy AI agents capable of accessing customer data, executing transactions, and modifying records through MCP integrations - often without IT oversight. Security research has identified that approximately 45% of analyzed MCP server implementations contain command injection vulnerabilities due to inadequate input validation. Meanwhile, the "confused deputy" problem allows AI agents to execute actions beyond authorized user privileges in 63% of default MCP configurations lacking proper authentication layers.
Key findings that inform this policy framework:
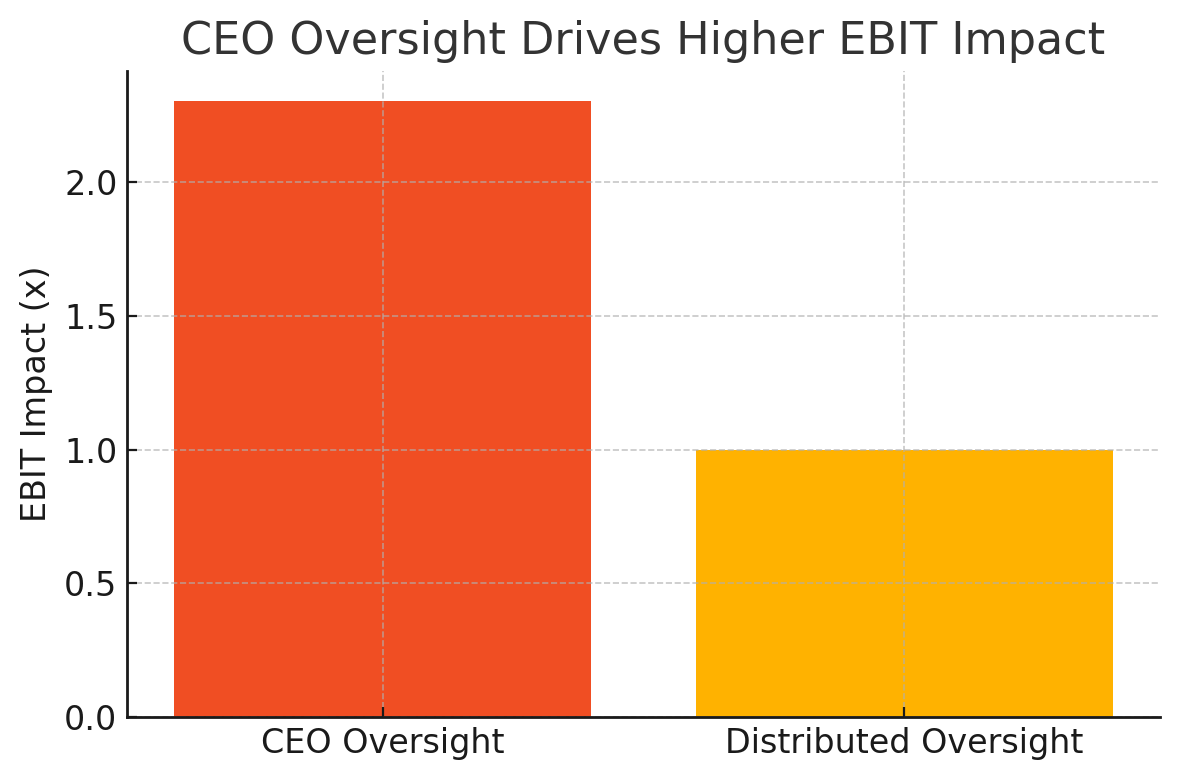
Organizations with CEO oversight of AI governance report 2.3x higher EBIT impact from gen AI deployment compared to those with distributed oversight
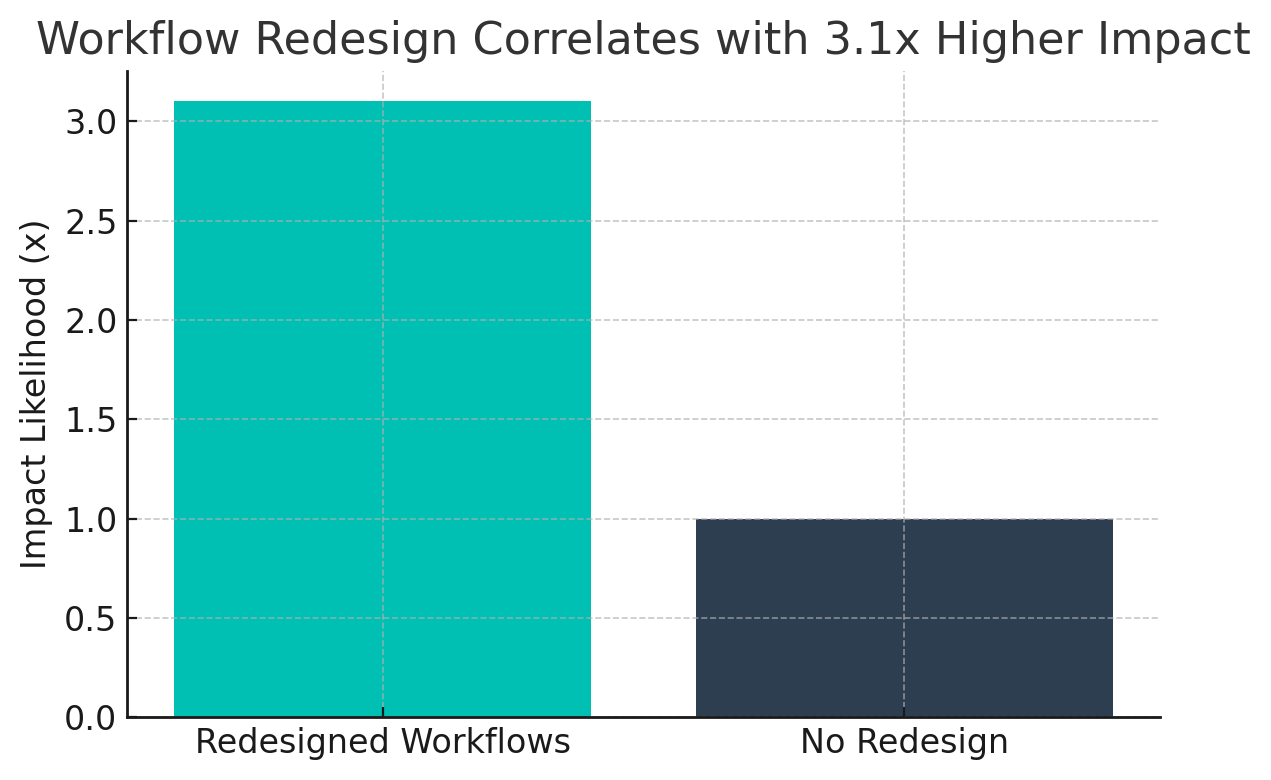
Companies that have redesigned workflows as they deploy gen AI are 3.1x more likely to see material bottom-line impact
Larger organizations ($500M+ revenue) are implementing adoption best practices at 2.4x the rate of smaller organizations, creating a widening capability gap
Only 28% of organizations currently have CEOs responsible for AI governance oversight, despite correlation analyses showing this as a top driver of value capture
This whitepaper provides CISOs with a comprehensive policy framework addressing: (1) risk-tiered classification models adapted from EU AI Act standards, (2) centralized approval workflows that balance innovation velocity with security controls, (3) technical architecture patterns for secure MCP deployment, (4) role-based access control mechanisms treating AI agents as privileged identities, and (5) continuous compliance integration with existing governance frameworks including ISO 27001, SOC 2, GDPR, HIPAA, and sector-specific regulations.
The recommended approach establishes three governance tiers - prohibited use cases (social scoring, subliminal manipulation), high-risk applications requiring human-in-the-loop validation and confidential computing (PHI/PCI processing, automated lending decisions), and standard-risk deployments with baseline security controls. Organizations implementing these tiered controls report 34% faster time-to-deployment for approved use cases while reducing security incidents by 67% compared to ad-hoc approaches.

Subscribe to CybersecurityHQ Newsletter to unlock the rest.
Become a paying subscriber of CybersecurityHQ Newsletter to get access to this post and other subscriber-only content.
Already a paying subscriber? Sign In.
A subscription gets you:
- • Access to Deep Dives and Premium Content
- • Access to AI Resume Builder
- • Access to the Archives
Reply