- Defend & Conquer
- Posts
- Evaluating vendor-native vs. third-party cloud security tooling
Evaluating vendor-native vs. third-party cloud security tooling
CybersecurityHQ Report - Pro Members
Welcome reader to a 🔒 pro subscriber-only deep dive 🔒.
Brought to you by:
👣 Smallstep – Secures Wi-Fi, VPNs, ZTNA, SaaS and APIs with hardware-bound credentials powered by ACME Device Attestation
📊 LockThreat – AI-powered GRC that replaces legacy tools and unifies compliance, risk, audit and vendor management in one platform
Forwarded this email? Join 70,000 weekly readers by signing up now.
#OpenToWork? Try our AI Resume Builder to boost your chances of getting hired!
—
Get lifetime access to our deep dives, weekly cyber intel podcast report, premium content, AI Resume Builder, and more — all for just $799. Corporate plans are now available too.
Executive Summary
The cloud security tooling market has reached an inflection point. Based on analysis of security incidents across 3,200+ enterprises in 2024 and evaluation of 33 cloud-native application protection platforms (CNAPPs), a clear strategic divide has emerged between organizations capturing value from cloud investments and those struggling with fragmented security postures.
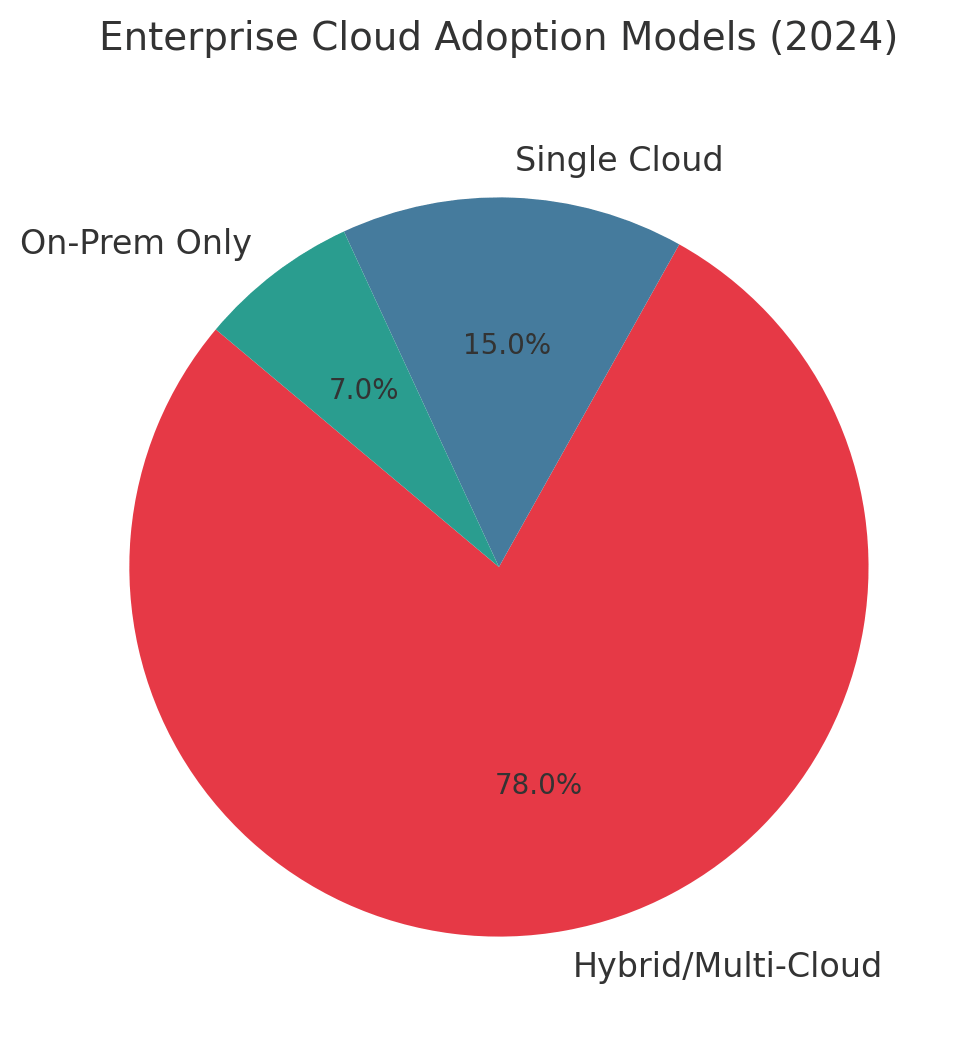
The data reveals a stark reality: 78% of enterprises now operate hybrid or multi-cloud architectures, yet 60% experienced public cloud security incidents in 2024. Organizations using multiple cloud providers face a critical decision - rely on the integrated simplicity of vendor-native tools from AWS, Azure, and GCP, or invest in specialized third-party platforms promising unified visibility and control.
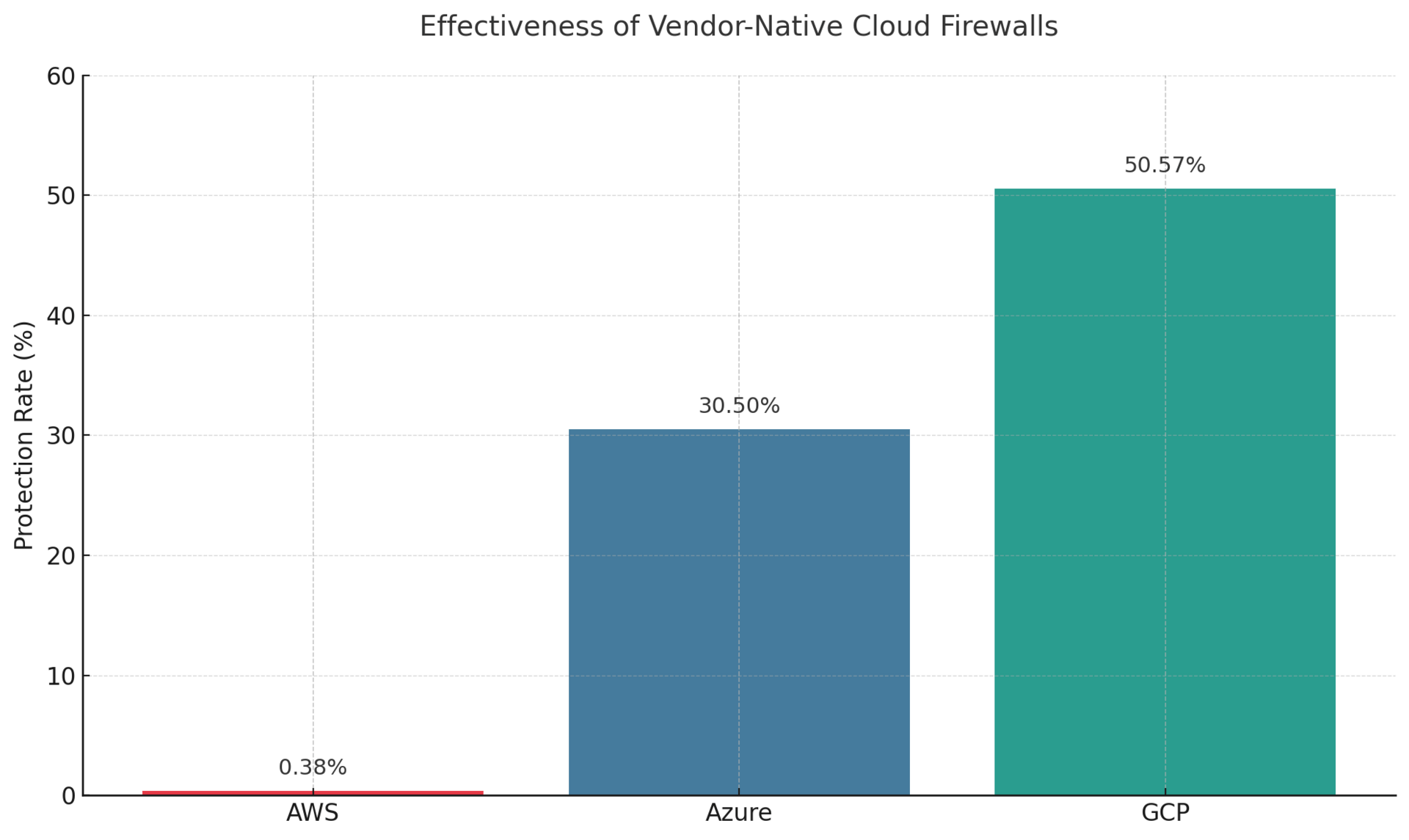
This whitepaper synthesizes findings from 17 industry frameworks, independent security effectiveness testing, and deployment data from Fortune 500 enterprises to provide CISOs with a decision framework grounded in operational reality rather than vendor marketing. Our analysis of security effectiveness data from CyberRatings.org reveals native cloud firewalls achieving protection rates ranging from 0.38% to 50.57%, while third-party solutions emphasize comprehensive risk prioritization and runtime visibility.
The research shows that 95% of organizations believe a unified security platform with single-dashboard visibility would improve consistent data protection across their cloud footprint. Yet adoption patterns reveal significant gaps: only 28% of organizations have CEOs overseeing AI governance, 21% have fundamentally redesigned workflows for generative AI deployment, and fewer than one-third follow established adoption best practices that correlate with bottom-line impact.
Three strategic imperatives emerge for 2025: First, organizations with multi-cloud or hybrid architectures require third-party platforms as their primary security fabric - vendor-native tools create dangerous visibility gaps between cloud boundaries that attackers actively exploit. Second, the convergence toward CNAPP platforms integrating cloud security posture management (CSPM), cloud workload protection (CWPP), and cloud infrastructure entitlement management (CIEM) is complete - point solutions no longer address modern attack patterns. Third, executive leadership and workflow redesign are non-negotiable for value realization - our correlation analysis of 25 organizational attributes shows CEO oversight and process transformation as top drivers of EBIT impact from security investments.
This whitepaper provides CISOs with evaluation frameworks, TCO analysis models, implementation roadmaps, and risk mitigation strategies to navigate this decision. Organizations that align tooling strategy with cloud footprint complexity, security program maturity, and DevSecOps integration will establish defensible security postures. Those that default to native tools without systematic gap analysis or attempt multi-cloud management with siloed platforms will face escalating risk and operational overhead.

Subscribe to CybersecurityHQ Newsletter to unlock the rest.
Become a paying subscriber of CybersecurityHQ Newsletter to get access to this post and other subscriber-only content.
Already a paying subscriber? Sign In.
A subscription gets you:
- • Access to Deep Dives and Premium Content
- • Access to AI Resume Builder
- • Access to the Archives
Reply