- Defend & Conquer
- Posts
- Evolution of Chinese state-affiliated hacking operations in 2025
Evolution of Chinese state-affiliated hacking operations in 2025
CybersecurityHQ Report - Pro Members

Welcome reader to a 🔒 pro subscriber-only deep dive 🔒.
Brought to you by:
👣 Smallstep – Secures Wi-Fi, VPNs, ZTNA, SaaS and APIs with hardware-bound credentials powered by ACME Device Attestation
📊 LockThreat – AI-powered GRC that replaces legacy tools and unifies compliance, risk, audit and vendor management in one platform
Forwarded this email? Join 70,000 weekly readers by signing up now.
#OpenToWork? Try our AI Resume Builder to boost your chances of getting hired!
—
Get lifetime access to our deep dives, weekly cyber intel podcast report, premium content, AI Resume Builder, and more — all for just $799. Corporate plans are now available too.
Executive Summary
Chinese state-affiliated cyber operations have undergone a fundamental transformation in 2025, shifting from opportunistic intellectual property theft to coordinated strategic disruption campaigns targeting critical infrastructure across 80+ nations. This whitepaper provides Chief Information Security Officers and senior security leadership with an evidence-based analysis of current threat vectors, regulatory imperatives, and actionable defense frameworks.
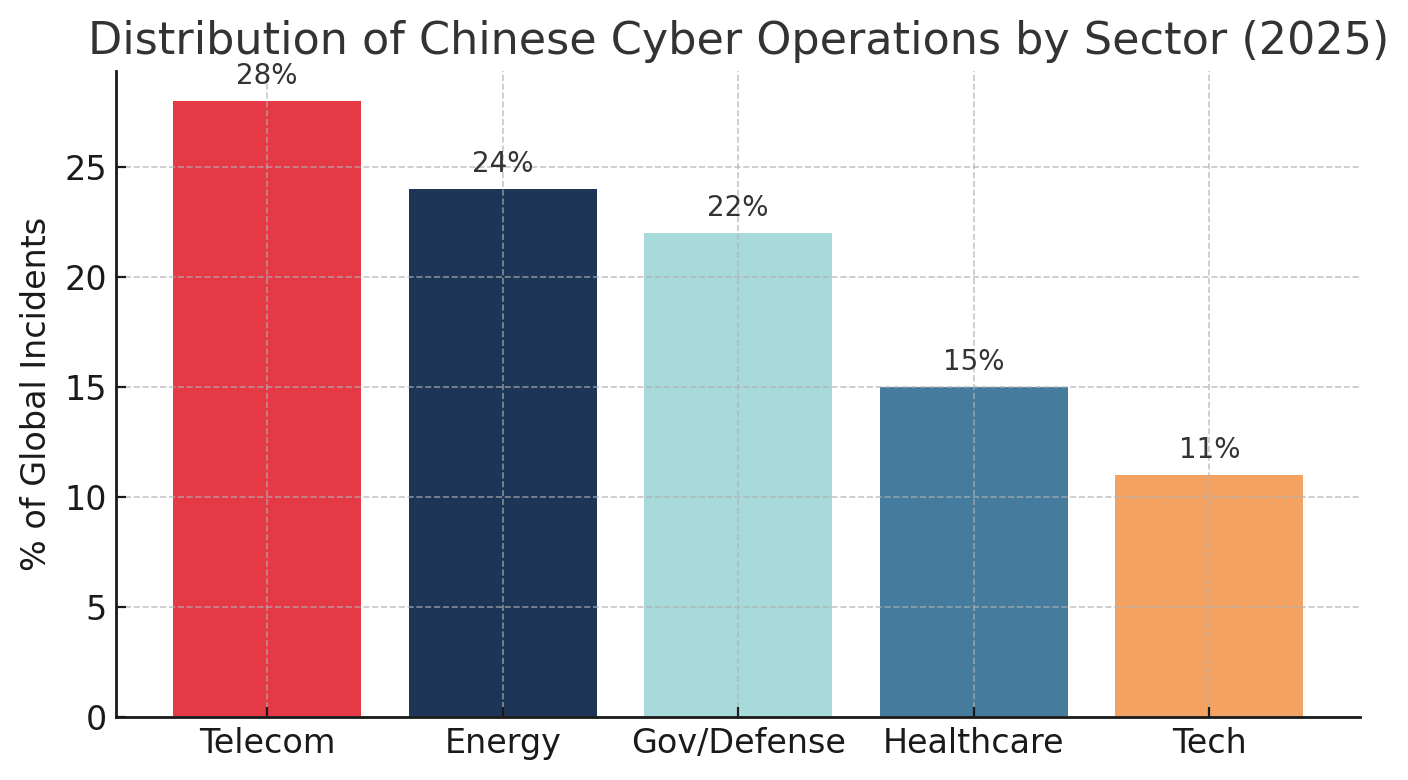
Scale and Sophistication: Research indicates a 150% escalation in Chinese state-sponsored cyber activities compared to 2024 baselines. Groups including Salt Typhoon, Volt Typhoon, and APT41 have compromised over 200 U.S. organizations and penetrated telecommunications networks globally, enabling persistent surveillance and pre-positioning for potential sabotage operations. The breadth of this campaign - spanning government, defense, energy, healthcare, and technology sectors - represents one of the largest coordinated cyber-espionage efforts in modern history.
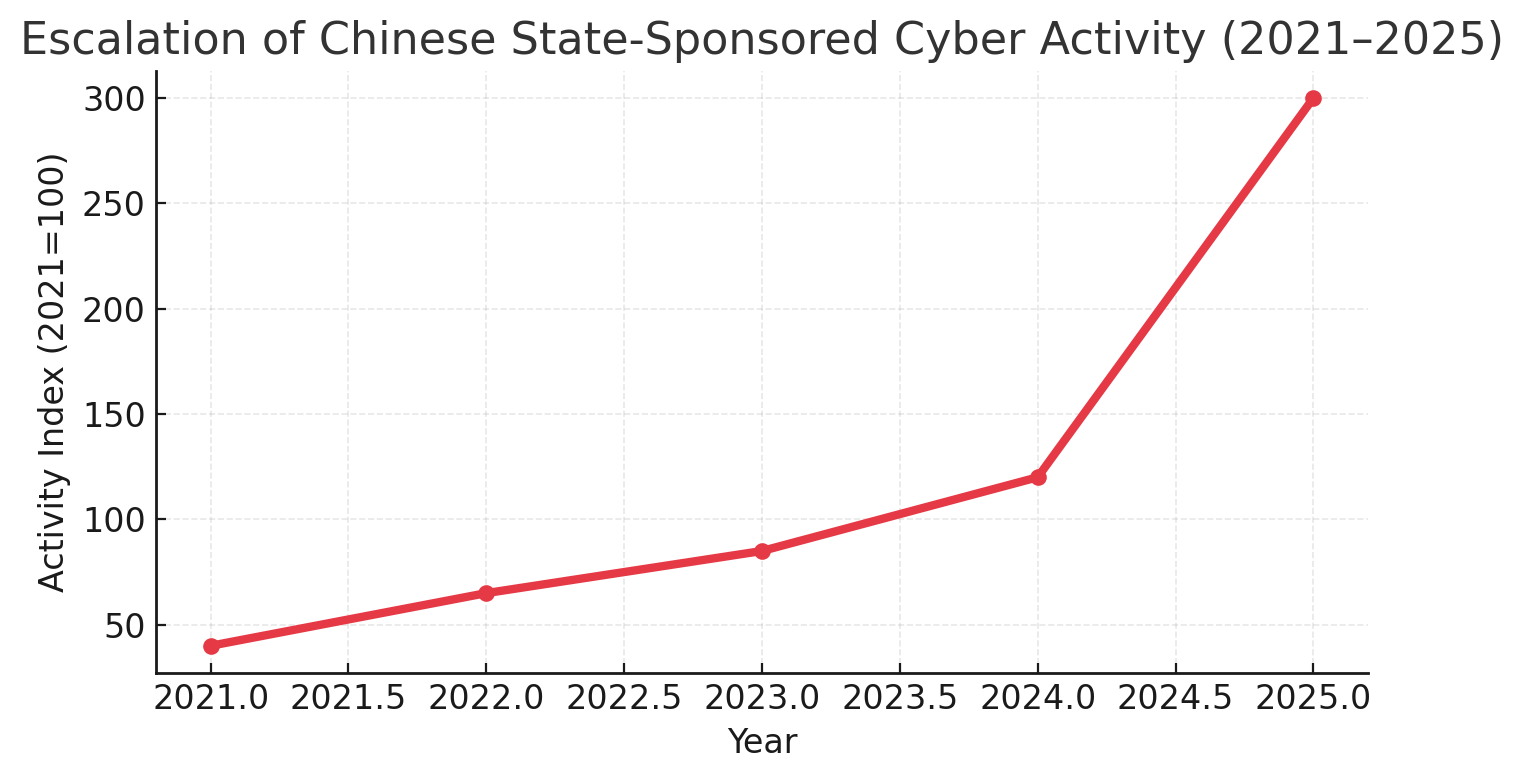
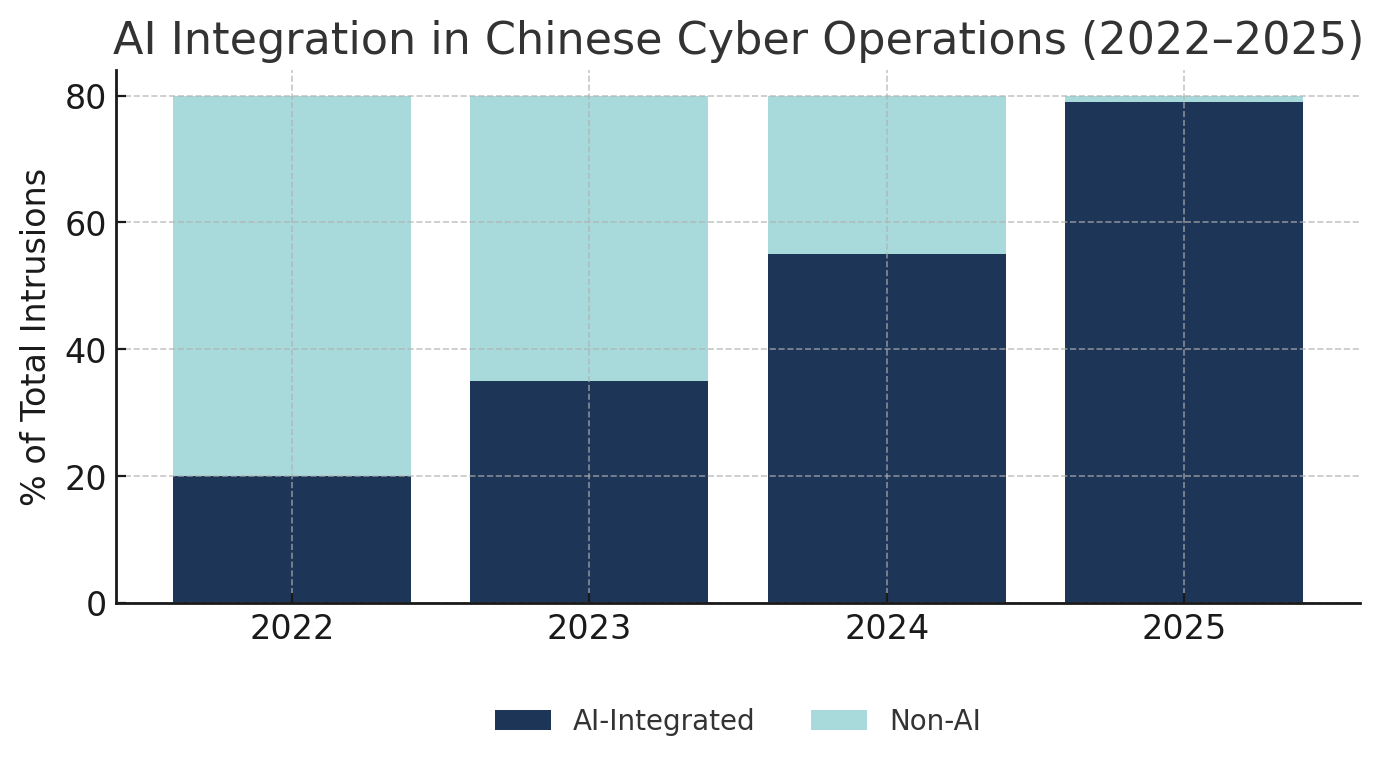
Tactical Evolution: Three critical shifts define 2025 operations. First, artificial intelligence integration has compressed exploit development cycles from weeks to hours, with 79% of intrusions now achieving initial access through malware-free techniques. Second, collaborative "Premier Pass-as-a-Service" models among APT groups enable shared access and complicate attribution. Third, supply chain and edge device exploitation - targeting routers, VPNs, and industrial systems - provides persistent footholds in critical infrastructure with minimal detection signatures.
Economic and Strategic Impact: The Salt Typhoon telecommunications campaign alone has generated costs exceeding $15 billion across remediation, legal liability, and lost competitive advantage. Taiwan faces 2.8 million daily intrusion attempts (a 17% year-over-year increase), while U.S. critical infrastructure sectors report the embedding of "digital landmines" - dormant capabilities designed for crisis-time activation. These operations reflect China's "active defense" doctrine, positioning cyber capabilities as a fifth domain for strategic leverage in potential conflicts, particularly scenarios involving Taiwan.
Regulatory Response: The 2025 landscape features heightened compliance requirements across jurisdictions. The EU's NIS2 Directive mandates incident reporting within 24 hours for essential services operators. The U.S. Cybersecurity and Infrastructure Security Agency (CISA) has designated 47 new Known Exploited Vulnerabilities (KEVs) linked to Chinese actors, requiring federal agencies to patch within 14 days. Southeast Asian nations, serving as testing grounds for tactics before global deployment, have implemented Active Cyber Defence laws enabling pre-emptive countermeasures.
Defense Imperative: Organizations must transition from perimeter-focused security to assumption-of-breach architectures. Analysis of 25 organizational attributes shows that CEO oversight of AI governance, fundamental workflow redesign during generative AI deployment, and implementation of zero trust principles correlate most strongly with resilience against advanced persistent threats. CISOs should prioritize edge device hardening, prompt patching of CVEs exploited in the wild (including CVE-2024-21887 in Ivanti and CVE-2023-20198 in Cisco), and deployment of anomaly-based detection systems calibrated for AI-enhanced reconnaissance patterns.
This whitepaper synthesizes intelligence from CISA advisories, CrowdStrike's 2025 Global Threat Report, NSA guidance, and real-time campaign tracking to provide senior leadership with a strategic roadmap for 2025-2027. The recommendations balance immediate tactical hardening with long-term organizational transformation, recognizing that effective defense against nation-state adversaries requires integration across technology, process, and governance domains.

Subscribe to CybersecurityHQ Newsletter to unlock the rest.
Become a paying subscriber of CybersecurityHQ Newsletter to get access to this post and other subscriber-only content.
Already a paying subscriber? Sign In.
A subscription gets you:
- • Access to Deep Dives and Premium Content
- • Access to AI Resume Builder
- • Access to the Archives
Reply