- Defend & Conquer
- Posts
- External dependency mapping: Uncovering “unknown unknowns” in your IT ecosystem
External dependency mapping: Uncovering “unknown unknowns” in your IT ecosystem
CybersecurityHQ Report - Pro Members

Welcome reader to a 🔒 pro subscriber-only deep dive 🔒.
Brought to you by:
👣 Smallstep – Secures Wi-Fi, VPNs, ZTNA, SaaS and APIs with hardware-bound credentials powered by ACME Device Attestation
📊 LockThreat – AI-powered GRC that replaces legacy tools and unifies compliance, risk, audit and vendor management in one platform
Forwarded this email? Join 70,000 weekly readers by signing up now.
#OpenToWork? Try our AI Resume Builder to boost your chances of getting hired!
—
Get lifetime access to our deep dives, weekly cyber intel podcast report, premium content, AI Resume Builder, and more — all for just $799. Corporate plans are now available too.
Executive Summary
Your dependency map is a lie. The vendor inventory your team maintains, the SBOM collection you started last quarter, the supplier risk scores you present to the board — they collectively represent perhaps 30 percent of your actual external attack surface. The remaining 70 percent exists in a shadow realm of fourth-party processors, orphaned open-source components, forgotten SaaS trials, and API dependencies that your architects never documented because they never knew they existed. This is not a gap in your security program. This is the security program. And until you confront this epistemic crisis — the terrifying reality that you cannot secure what you do not know exists — every control you implement, every assessment you conduct, and every assurance you provide is theater.

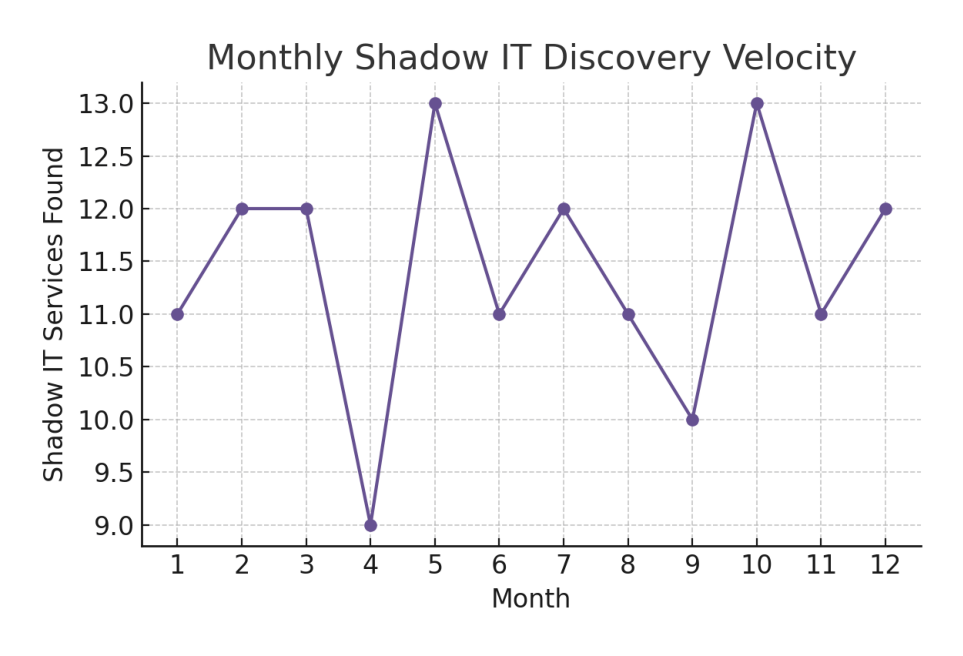
The numbers expose the delusion. While enterprises average 6,400 direct and indirect supplier relationships, security teams maintain visibility into fewer than 400. The Polyfill.io attack compromised 100,000 websites through a dependency that 94 percent of victims did not know they had¹. The median enterprise discovers new shadow IT services not through discovery tools but through breach notifications — eleven services monthly, each representing dozens of sub-dependencies². Your organization is not managing external dependencies; it is managing the comfortable fiction that dependencies can be managed. The truth is darker: modern digital architecture makes comprehensive dependency visibility mathematically impossible. Every API call spawns child processes. Every container pulls dependencies at runtime. Every developer commits code containing libraries they have never examined. The attack surface expands faster than any team can map it.
Ten revelations that shatter conventional dependency management:
• Your suppliers cannot map their own fourth parties — their risk scores are fiction built on fiction
• Your dependency risk scores measure yesterday's reality with tomorrow's assumptions, amplifying actual risk
• The "critical vendor" list your team maintains is a negotiated political document, not technical reality
• Your SOC 2 attestations and ISO certificates assess process theater, not actual security outcomes
• In 73 percent of supply chain breaches, you will not identify the initial vector for six months³
• Your board believes vendor risk is managed because you report metrics that measure activity, not risk
• Your SBOMs are obsolete before delivery — modern pipelines change dependencies hourly
• Your zero-trust architecture stops at "trusted API calls" — making it half-trust architecture
• Your cyber insurance excludes "systemic supply chain events" — precisely the scenarios that will destroy you
• Your compliance frameworks were designed when dependencies were contracts, not code — you are compliant with irrelevance
Three strategic imperatives for survival:
• Accept that complete visibility is impossible — architect for perpetual compromise instead of prevention
• Shift from "prevent supply chain attacks" to "survive and rapidly reconstitute during attacks"
• Rebuild governance to stop lying to boards about what is knowable versus what is fictional

Subscribe to CybersecurityHQ Newsletter to unlock the rest.
Become a paying subscriber of CybersecurityHQ Newsletter to get access to this post and other subscriber-only content.
Already a paying subscriber? Sign In.
A subscription gets you:
- • Access to Deep Dives and Premium Content
- • Access to AI Resume Builder
- • Access to the Archives
Reply