- Defend & Conquer
- Posts
- Improving threat detection for unmanaged network assets
Improving threat detection for unmanaged network assets
CybersecurityHQ Report - Pro Members
Welcome reader to a 🔒 pro subscriber-only deep dive 🔒.
Brought to you by:
👣 Smallstep – Secures Wi-Fi, VPNs, ZTNA, SaaS and APIs with hardware-bound credentials powered by ACME Device Attestation
🏄♀️ Upwind Security – Real-time cloud security that connects runtime to build-time to stop threats and boost DevSecOps productivity
🔧 Endor Labs – App security from legacy C++ to Bazel monorepos, with reachability-based risk detection and fix suggestions across the SDLC
📊 LockThreat – AI-powered GRC that replaces legacy tools and unifies compliance, risk, audit and vendor management in one platform
🧠 Ridge Security – The AI-powered offensive security validation platform
Forwarded this email? Join 70,000 weekly readers by signing up now.
#OpenToWork? Try our AI Resume Builder to boost your chances of getting hired!
—
Get lifetime access to our deep dives, weekly cyber intel podcast report, premium content, AI Resume Builder, and more — all for just $799. Corporate plans are now available too.
Executive Summary
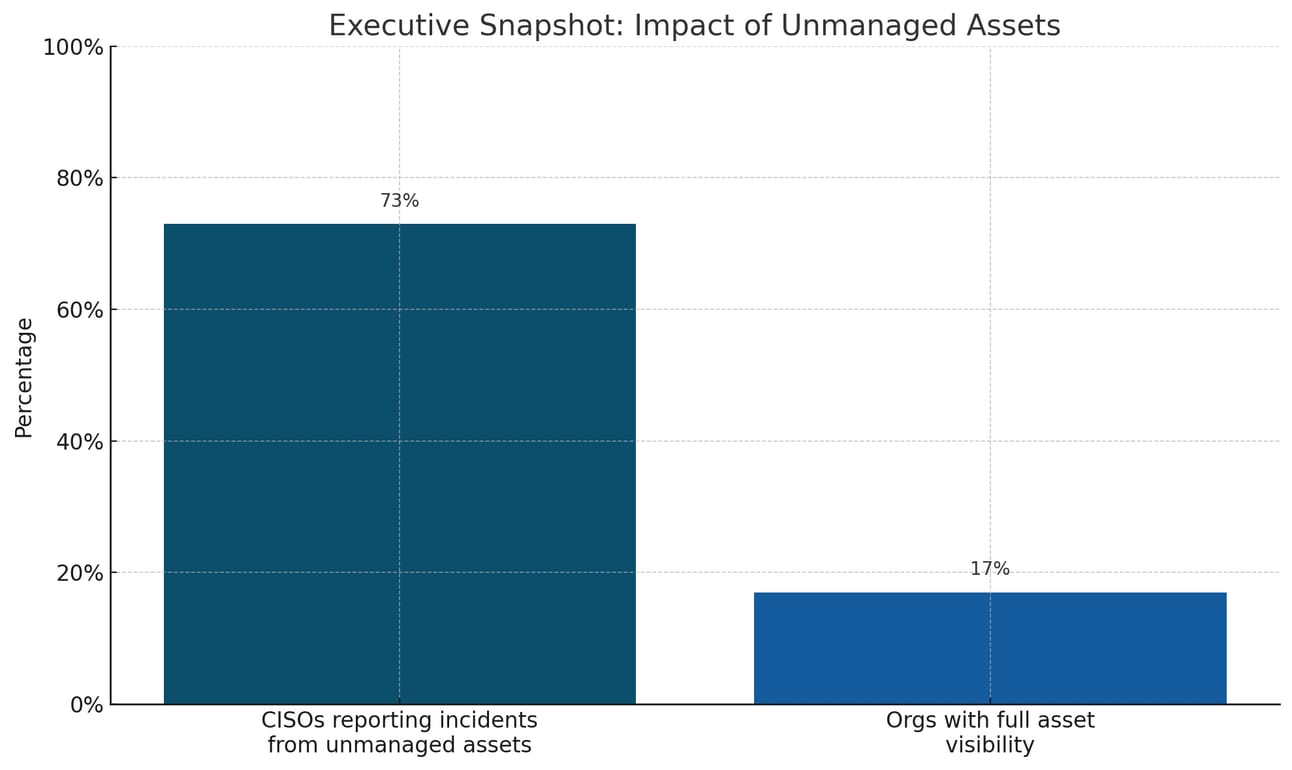
Enterprise networks face an expanding threat landscape where unmanaged assets create significant security blind spots. With 73% of CISOs reporting security incidents from unmanaged assets and only 17% of organizations maintaining comprehensive asset visibility, detecting indicators of compromise (IOCs) across these ungoverned endpoints has become critical for cybersecurity resilience.
This whitepaper examines the most effective methods for identifying IOCs across unmanaged network assets, drawing from recent research, industry best practices, and emerging technologies. Key findings include:
Hybrid detection approaches combining multiple data sources achieve detection rates of 62-100% with false positive rates as low as 0.000034%
Network Detection and Response (NDR) solutions provide critical visibility for assets that cannot host traditional security agents
Extended Detection and Response (XDR) platforms correlate signals across managed and unmanaged systems to surface hidden IOCs
Zero Trust architectures and network segmentation contain potential breaches from unmanaged assets
Organizations implementing comprehensive detection strategies see significant reductions in dwell time and breach impact
The research emphasizes that technical solutions alone are insufficient. Success requires organizational changes including continuous asset discovery, third-party risk management, security-aware culture development, and executive-level governance. As enterprises continue adopting IoT, BYOD, and cloud services throughout 2025, implementing robust IOC detection for unmanaged assets will determine which organizations thrive versus those that become breach statistics.

Subscribe to CybersecurityHQ Newsletter to unlock the rest.
Become a paying subscriber of CybersecurityHQ Newsletter to get access to this post and other subscriber-only content.
Already a paying subscriber? Sign In.
A subscription gets you:
- • Access to Deep Dives and Premium Content
- • Access to AI Resume Builder
- • Access to the Archives
Reply