- Defend & Conquer: CISO-Grade Cyber Intel Weekly
- Posts
- Mapping and mitigating interdependent cybersecurity risks in complex technology ecosystems
Mapping and mitigating interdependent cybersecurity risks in complex technology ecosystems
CybersecurityHQ Report - Pro Members
Welcome reader to a 🔒 pro subscriber-only deep dive 🔒.
Brought to you by:
🏄♀️ Upwind Security – Real-time cloud security that connects runtime to build-time to stop threats and boost DevSecOps productivity
🔧 Endor Labs – Application security for the software development revolution, from ancient C++ code to bazel monorepos, and everything in between
🧠 Ridge Security – The AI-powered offensive security validation platform
Forwarded this email? Join 70,000 weekly readers by signing up now.
#OpenToWork? Try our AI Resume Builder to boost your chances of getting hired!
—
Get lifetime access to our deep dives, weekly cyber intel podcast report, premium content, AI Resume Builder, and more — all for just $799. Corporate plans are now available too.
Executive Summary
Organizations today operate within increasingly complex technology ecosystems where cybersecurity risks are deeply interconnected. A single vulnerability in one component can cascade through multiple systems, creating widespread impacts across supply chains, cloud services, and partner networks. This whitepaper presents comprehensive methodological approaches for mapping and mitigating these interdependent risks, drawing from recent research, industry best practices, and real-world case studies.
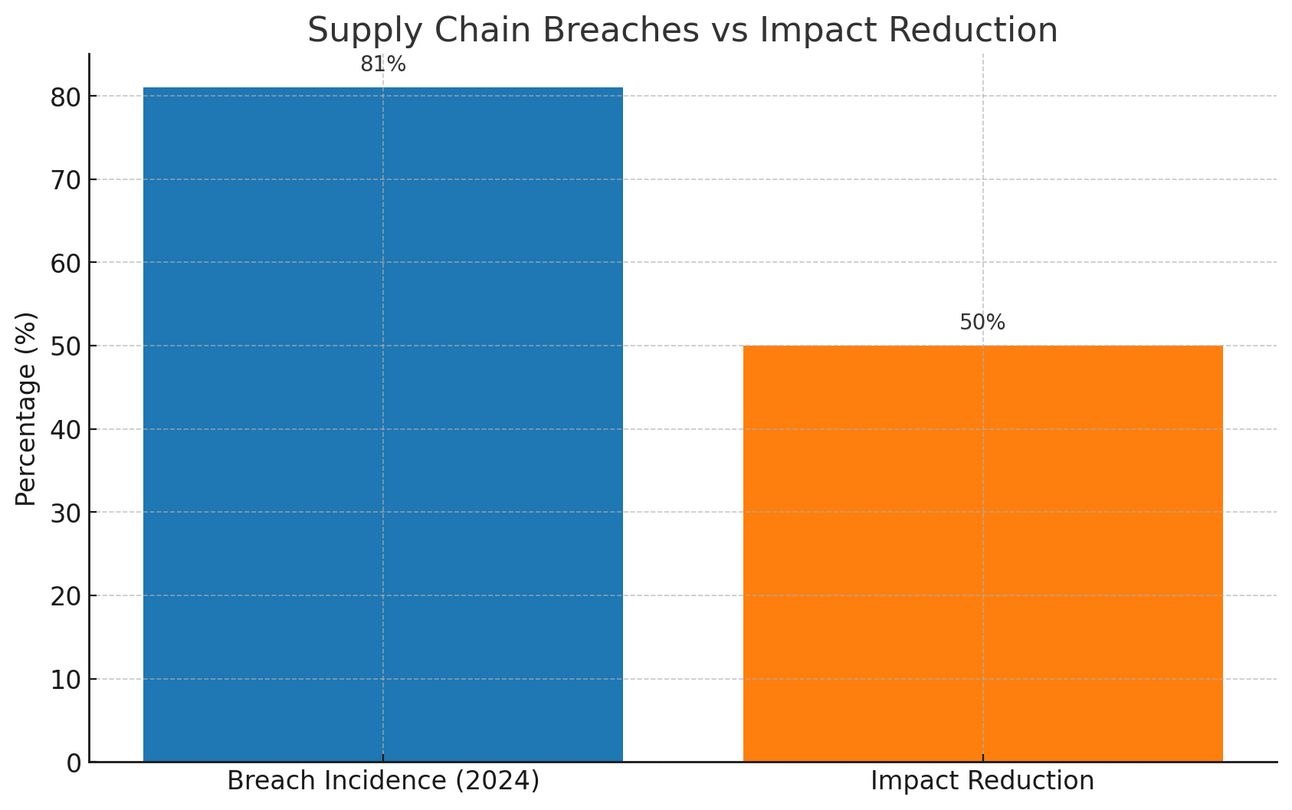
Key findings include:
81% of organizations experienced supply chain-related breaches in 2024, with impacts often extending through multiple tiers of dependencies
Organizations using comprehensive risk mapping frameworks reduced incident impacts by up to 50%
Effective mitigation requires combining technical tools (dependency graphs, simulation models) with organizational frameworks (NIST, ISO standards)
Success depends on executive leadership, cross-functional collaboration, and continuous monitoring of evolving risks
The paper provides actionable methodologies including graph-based dependency mapping, quantitative risk assessment techniques, resilience-by-design principles, and governance frameworks that organizations can implement to strengthen their cybersecurity posture in interconnected environments.

Subscribe to CybersecurityHQ Newsletter to unlock the rest.
Become a paying subscriber of CybersecurityHQ Newsletter to get access to this post and other subscriber-only content.
Already a paying subscriber? Sign In.
A subscription gets you:
- • Access to Deep Dives and Premium Content
- • Access to AI Resume Builder
- • Access to the Archives
Reply