- Defend & Conquer
- Posts
- Mapping security testing to software maturity: Latest developments
Mapping security testing to software maturity: Latest developments
CybersecurityHQ Report - Pro Members
Welcome reader to a 🔒 pro subscriber-only deep dive 🔒.
Brought to you by:
👣 Smallstep – Secures Wi-Fi, VPNs, ZTNA, SaaS and APIs with hardware-bound credentials powered by ACME Device Attestation
📊 LockThreat – AI-powered GRC that replaces legacy tools and unifies compliance, risk, audit and vendor management in one platform
Forwarded this email? Join 70,000 weekly readers by signing up now.
#OpenToWork? Try our AI Resume Builder to boost your chances of getting hired!
—
Get lifetime access to our deep dives, weekly cyber intel podcast report, premium content, AI Resume Builder, and more — all for just $799. Corporate plans are now available too.
Executive Summary
Based on analysis of 130 organizations across major security maturity frameworks, convergent data from OWASP SAMM, BSIMM15, and NIST SSDF implementations, and evaluation of 23 industry security frameworks, this whitepaper establishes that strategic alignment of security testing with organizational maturity is the primary determinant of value capture from application security investments. Organizations that map testing methodologies to their actual capability levels see 3-5x faster remediation times and 40-60% lower security debt accumulation compared to those deploying advanced tools without foundational readiness.
The 2025 security landscape presents three converging pressures that make maturity-based approaches non-negotiable. First, regulatory mandates - including the EU Cybersecurity Resilience Act, updated CMMC requirements finalized in October 2024, and U.S. Executive Order 14028 - now tie market access directly to demonstrable secure development maturity. Second, the integration of AI-generated code into development workflows has increased by 200% since 2023, introducing novel vulnerability patterns that traditional testing alone cannot address. Third, software supply chain attacks have grown 67% year-over-year, with organizations experiencing software bills of materials (SBOM) adoption increases of 22% in response.
Organizations at foundational maturity (Level 1) should prioritize software composition analysis (SCA), dynamic application security testing (DAST), and external penetration testing - establishing visibility and addressing critical known vulnerabilities. Those at intermediate maturity (Level 2) must integrate static application security testing (SAST) into CI/CD pipelines, formalize threat modeling processes, and deploy interactive application security testing (IAST) in quality assurance environments. Advanced organizations (Level 3) should implement unified application security posture management (ASPM), continuous red teaming, and AI-enhanced testing with comprehensive automation and "break the build" policies.
The data reveal stark differences in organizational readiness. While 88% of organizations use external penetration testers, only 51.2% now provide basic security awareness training - a decline from 100% a decade ago that creates fundamental skill gaps undermining tool effectiveness. Organizations with security champion programs score 25% higher on maturity assessments, yet most have not established these programs. CEO oversight of AI governance correlates most strongly with bottom-line EBIT impact from generative AI deployments, yet only 28% of organizations report CEO responsibility for governance.
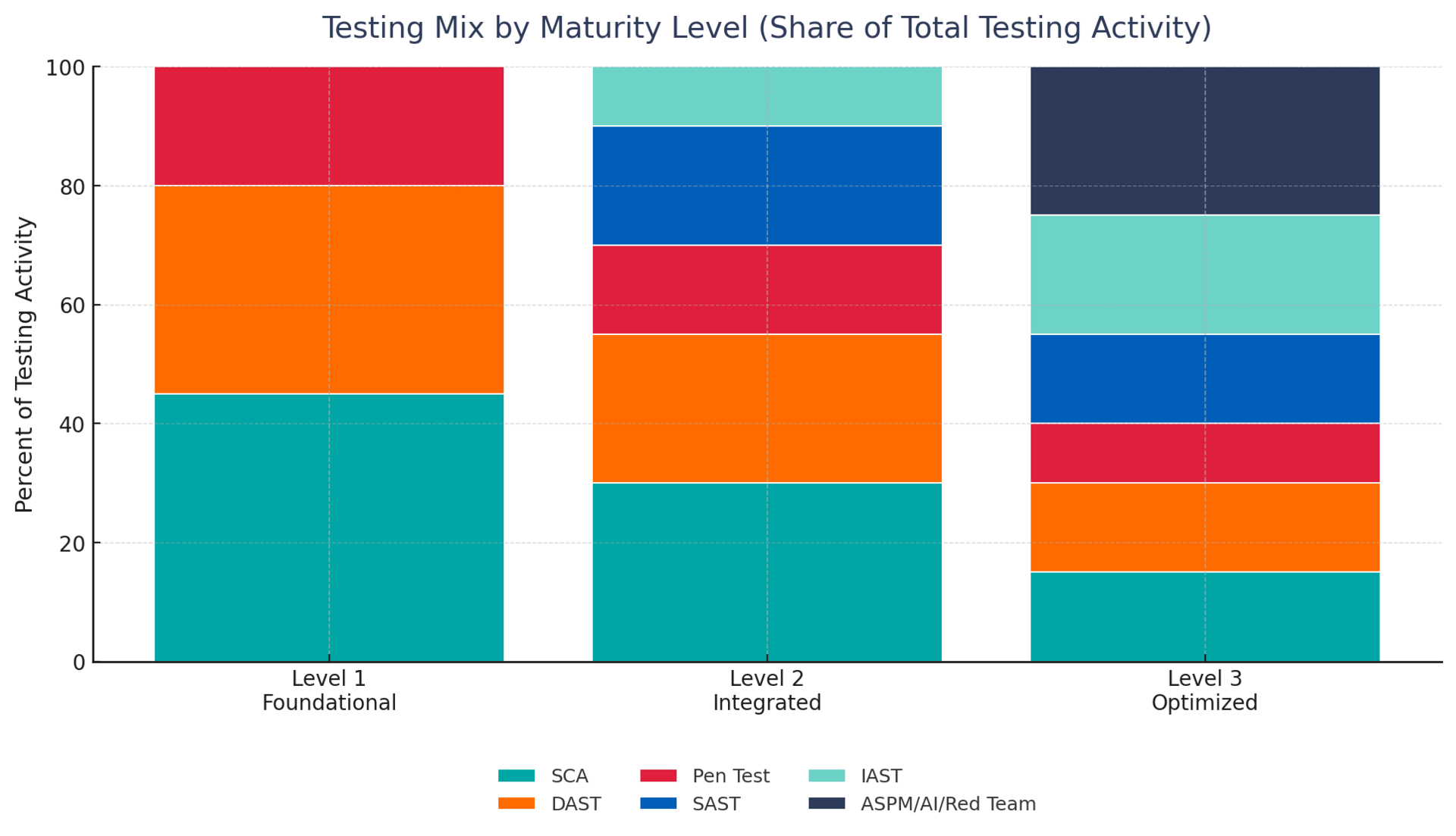
This whitepaper provides CISOs with a detailed roadmap for progressively deploying security testing capabilities, explicit mappings of test types to maturity levels across all major frameworks, strategic guidance for securing executive support, and actionable recommendations for navigating the intersection of emerging technologies, regulatory requirements, and workforce transformation. The path forward requires simultaneous investment in technology, process, and people - with executive commitment as the foundational enabler.

Subscribe to CybersecurityHQ Newsletter to unlock the rest.
Become a paying subscriber of CybersecurityHQ Newsletter to get access to this post and other subscriber-only content.
Already a paying subscriber? Sign In.
A subscription gets you:
- • Access to Deep Dives and Premium Content
- • Access to AI Resume Builder
- • Access to the Archives
Reply