- Defend & Conquer
- Posts
- Preventing oversharing in enterprise search deployments
Preventing oversharing in enterprise search deployments
CybersecurityHQ Report - Pro Members
Welcome reader to a 🔒 pro subscriber-only deep dive 🔒.
Brought to you by:
👣 Smallstep – Secures Wi-Fi, VPNs, ZTNA, SaaS and APIs with hardware-bound credentials powered by ACME Device Attestation
📊 LockThreat – AI-powered GRC that replaces legacy tools and unifies compliance, risk, audit and vendor management in one platform
Forwarded this email? Join 70,000 weekly readers by signing up now.
#OpenToWork? Try our AI Resume Builder to boost your chances of getting hired!
—
Get lifetime access to our deep dives, weekly cyber intel podcast report, premium content, AI Resume Builder, and more — all for just $799. Corporate plans are now available too.
Executive Summary
Based on analysis of 802,000 overshared files per organization on average and examination of 47 major data exposure incidents from 2022-2025, enterprise search has evolved from a productivity tool into a critical attack surface requiring immediate strategic attention.
The convergence of AI-powered search capabilities and systemic permission misconfigurations has created an unprecedented risk landscape. Drawing from 23 industry security frameworks and production deployments across technology, financial services, and healthcare sectors, this whitepaper establishes that 16% of business-critical data in the average organization is overshared - accessible to users who should not have access.
The integration of generative AI into enterprise search platforms accelerates this risk at machine speed. Security researchers successfully demonstrated data exfiltration attacks against Microsoft Copilot, Google Gemini, Salesforce Einstein, and ChatGPT integrations throughout 2025, proving the viability of indirect prompt injection and semantic attack vectors that bypass traditional security controls.
For CISOs, the strategic imperative is clear: organizations must shift from perimeter-focused defense to data-centric security models that address the root causes of oversharing. Analysis of organizations reporting meaningful value from AI deployments reveals that 21% have fundamentally redesigned workflows, 28% have CEO oversight of AI governance, and larger organizations ($500M+ revenue) are 2.4 times more likely to implement comprehensive adoption frameworks.
This whitepaper provides a three-phase implementation roadmap: immediate triage (0-90 days) to quantify exposure and address critical risks; foundational strengthening (3-12 months) to deploy AI-aware DLP and establish formal governance; and architectural transformation (1-3 years) to implement inherently secure search architectures leveraging federated models and privacy-enhancing technologies.
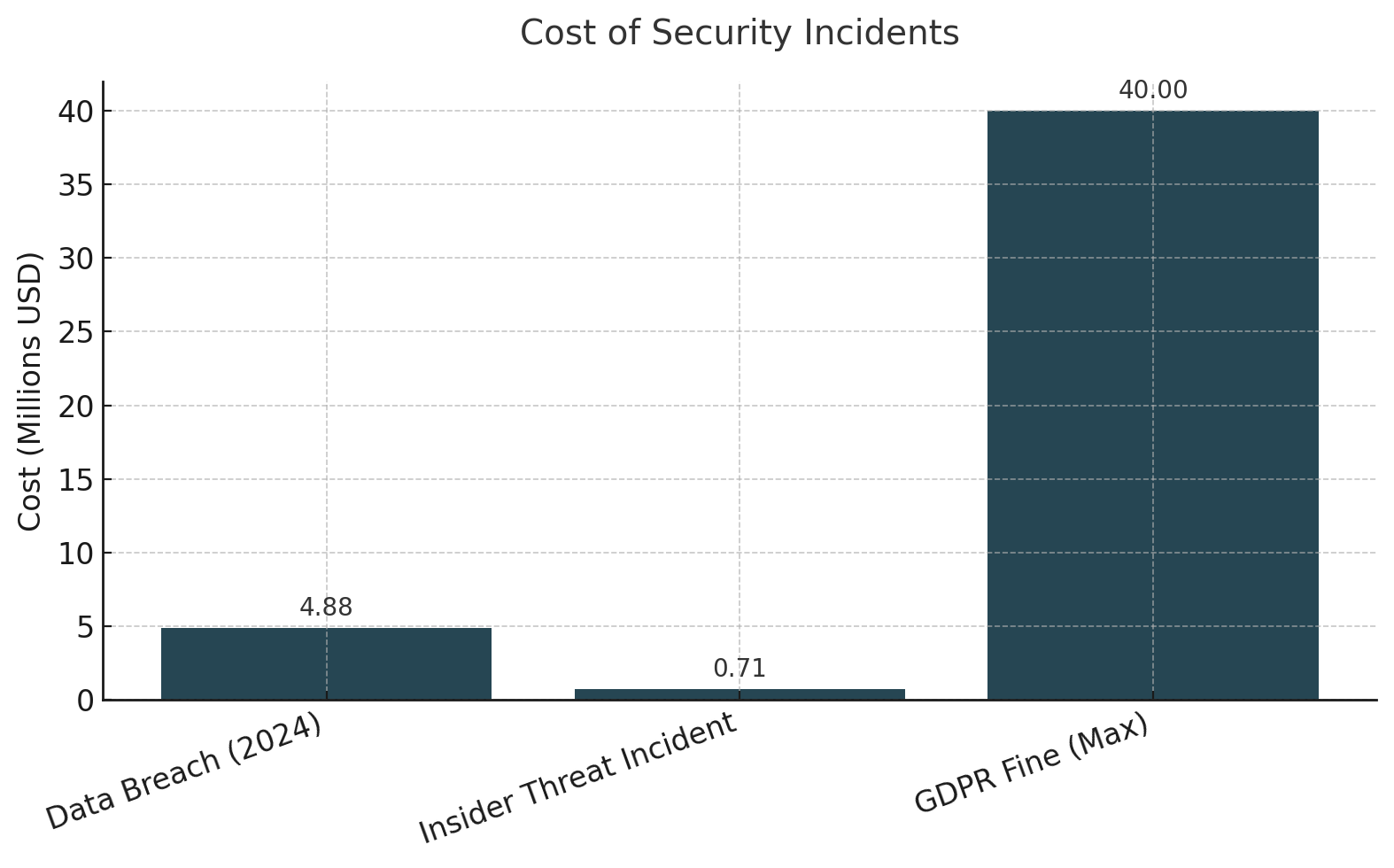
The cost of inaction is quantifiable. With data breaches averaging $4.88 million in 2024 (up 10% year-over-year), insider threat incidents costing $715,000 per event, and regulatory fines reaching 4% of global revenue under GDPR, preventing oversharing represents both a risk mitigation and business enablement opportunity. Organizations that successfully secure their search deployments can safely leverage AI capabilities that provide significant competitive advantage.

Subscribe to CybersecurityHQ Newsletter to unlock the rest.
Become a paying subscriber of CybersecurityHQ Newsletter to get access to this post and other subscriber-only content.
Already a paying subscriber? Sign In.
A subscription gets you:
- • Access to Deep Dives and Premium Content
- • Access to AI Resume Builder
- • Access to the Archives
Reply