- Defend & Conquer: CISO-Grade Cyber Intel Weekly
- Posts
- Risks from emerging technologies: IoT/5G/edge at scale and their security implications.
Risks from emerging technologies: IoT/5G/edge at scale and their security implications.
CybersecurityHQ Report - Pro Members
Welcome reader to a 🔒 pro subscriber-only deep dive 🔒.
Brought to you by:
👣 Smallstep – Secures Wi-Fi, VPNs, ZTNA, SaaS and APIs with hardware-bound credentials powered by ACME Device Attestation
📊 LockThreat – AI-powered GRC that replaces legacy tools and unifies compliance, risk, audit and vendor management in one platform
Forwarded this email? Join 70,000 weekly readers by signing up now.
#OpenToWork? Try our AI Resume Builder to boost your chances of getting hired!
—
Get lifetime access to our deep dives, weekly cyber intel podcast report, premium content, AI Resume Builder, and more — all for just $799. Corporate plans are now available too.
Executive Summary: The New Reality
IoT/5G/edge has become your third-largest attack surface. You're already compromised — you just don't know where yet.
Five Strategic Truths
1. The perimeter is dead. 33% of enterprise breaches now originate through IoT endpoints¹. Your 18,000 connected devices are 18,000 open doors.
2. You're blind to 40-60% of your IoT assets. Shadow deployments by well-meaning employees create unmanaged attack paths into crown jewel systems daily.
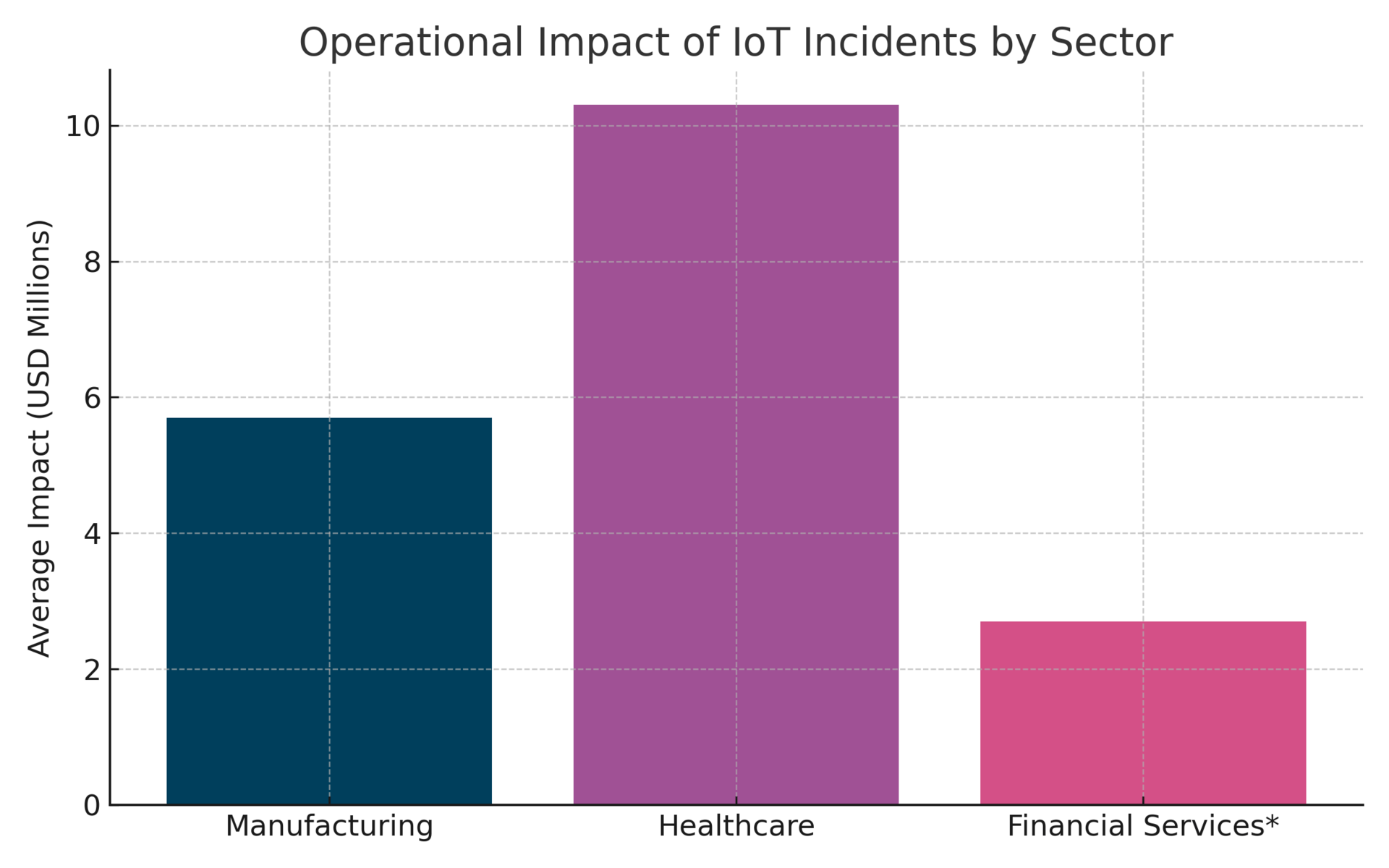
3. Operational impact now exceeds data breach costs. Manufacturing: $5.7M per incident. Healthcare: $10.3M². Financial services: $2.7M per hour of downtime.
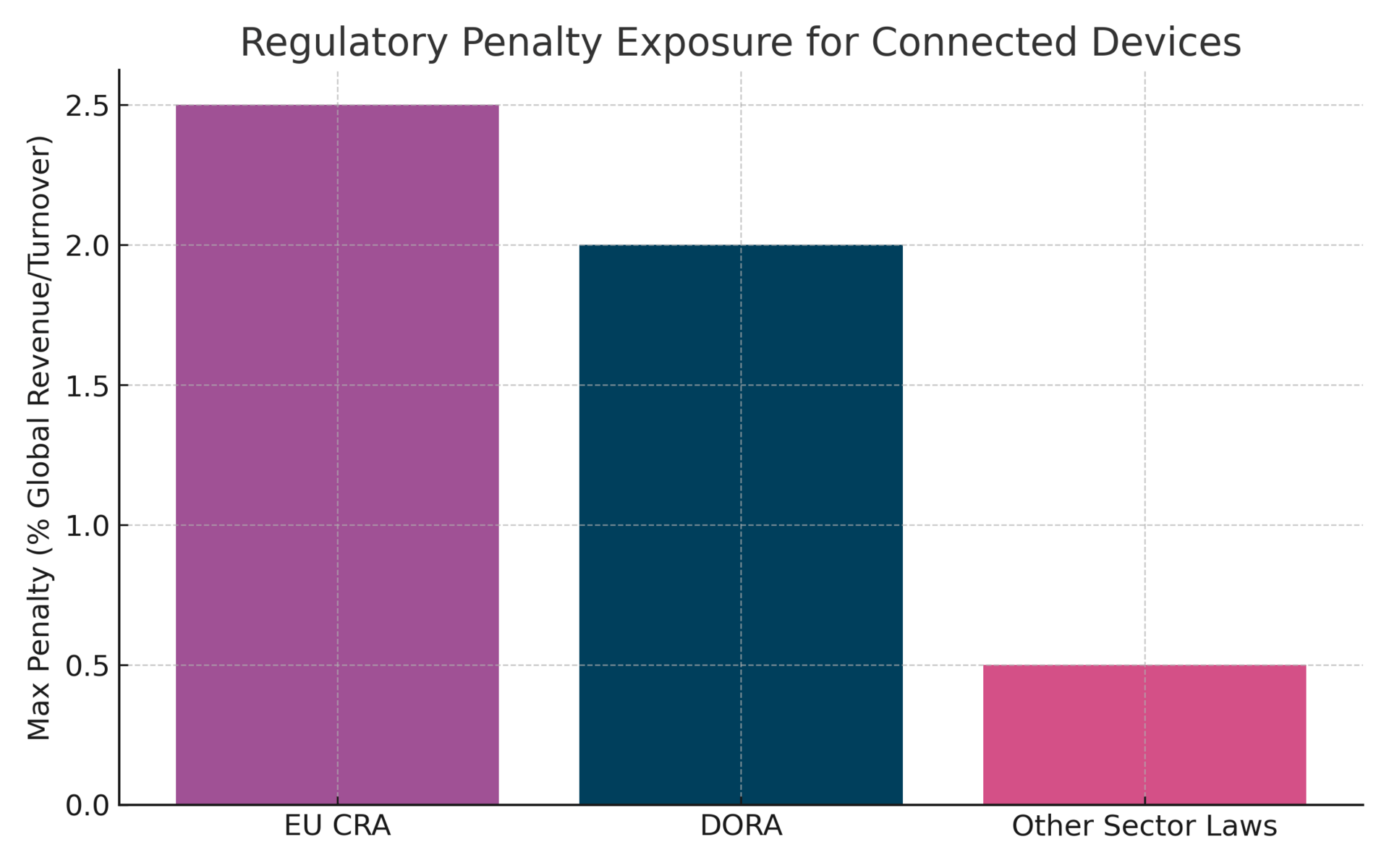
4. Regulation is now existential. EU CRA (2026): €15M fines or 2.5% global revenue. DORA: 4-hour recovery mandate. FDA: Criminal liability for medical device failures. Miss these deadlines and lose market access.
5. Your vendors are your biggest vulnerability. February 2025: Single IoT platform compromise cascaded to 100+ enterprises. Your security is only as strong as your weakest supplier.
The Cost of Inaction
Year 1: 67% probability of Tier 3 device enabling Tier 1 breach
Year 2: Regulatory non-compliance bars you from EU markets
Year 3: Insurance carriers exclude IoT incidents from coverage
Seven Non-Negotiables (Next 90 Days)
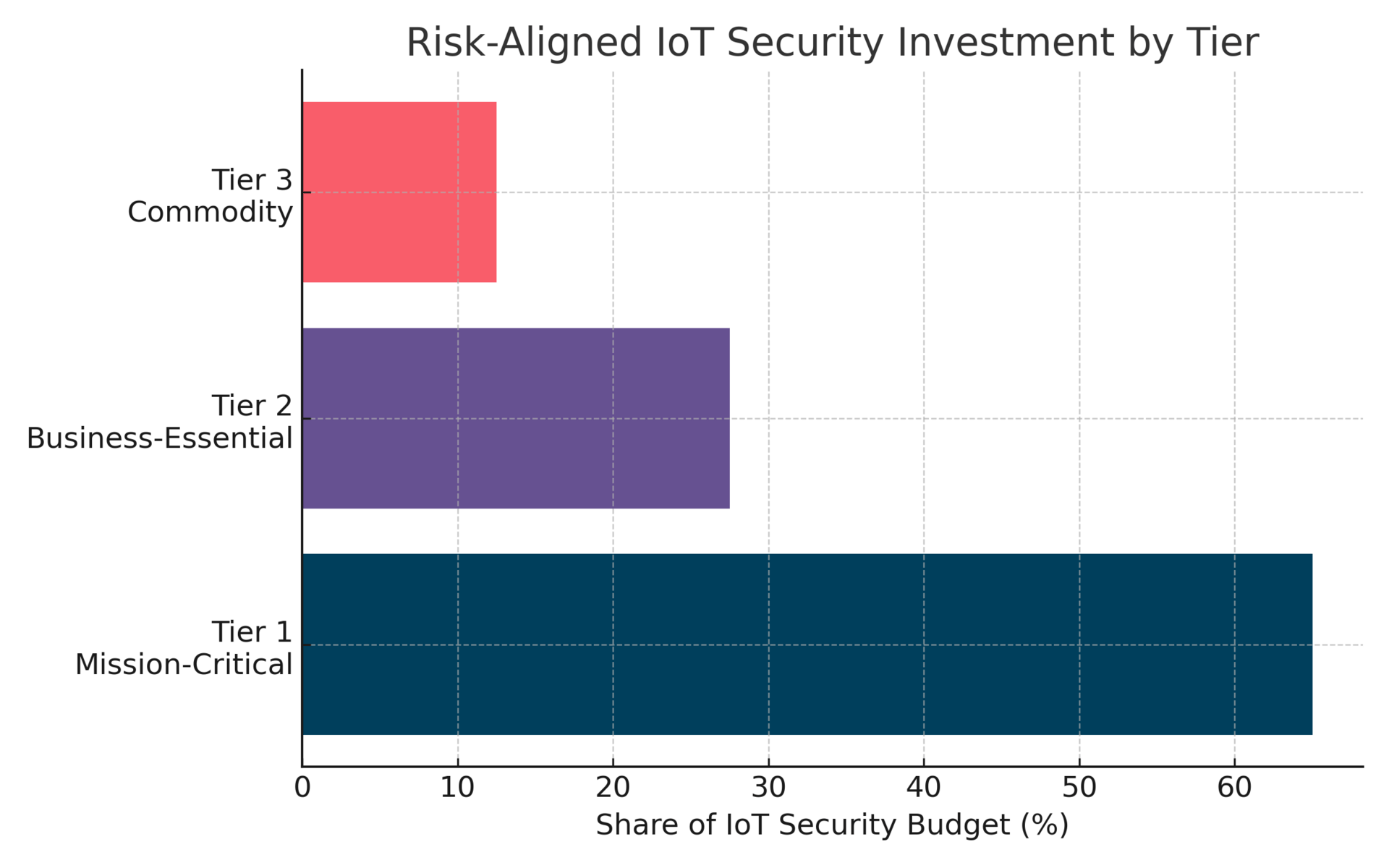
Stratify everything: Map all devices to three risk tiers. Tier 1 (mission-critical) gets 60% of security spend.
Implement Zero Trust for devices: PKI certificates, not passwords. Micro-segmentation, not VLANs.
Automate or drown: 18 billion events daily require ML-driven detection. Human SOCs can't scale.
Fix your blind spots: Deploy continuous discovery. Unknown device = immediate isolation.
Integrate IoT into enterprise risk: Board needs quarterly IoT KRIs. Make it visible or it won't get funded.
Build OT incident response: IT playbooks fail for industrial systems. Train dedicated OT response team.
Lock down supply chain: Vendor security assessments before contracts. SBOMs mandatory. Kill switches for vendor compromise.
Bottom Line: IoT/5G/edge security is no longer optional. It's the difference between operational resilience and existential failure. Act now or explain to your board why you didn't.
Investment required: 3-7% of IT security budget ROI: Avoiding one incident pays for five years of the program Timeline: 180 days to baseline security, 12 months to maturity

Subscribe to CybersecurityHQ Newsletter to unlock the rest.
Become a paying subscriber of CybersecurityHQ Newsletter to get access to this post and other subscriber-only content.
Already a paying subscriber? Sign In.
A subscription gets you:
- • Access to Deep Dives and Premium Content
- • Access to AI Resume Builder
- • Access to the Archives
Reply