- Defend & Conquer
- Posts
- Secure design reviews in rapid MVP lifecycles: A CISO’s guide
Secure design reviews in rapid MVP lifecycles: A CISO’s guide
CybersecurityHQ Report - Pro Members

Welcome reader to a 🔒 pro subscriber-only deep dive 🔒.
Brought to you by:
👣 Smallstep – Secures Wi-Fi, VPNs, ZTNA, SaaS and APIs with hardware-bound credentials powered by ACME Device Attestation
🏄♀️ Upwind Security – Real-time cloud security that connects runtime to build-time to stop threats and boost DevSecOps productivity
📊 LockThreat – AI-powered GRC that replaces legacy tools and unifies compliance, risk, audit and vendor management in one platform
Forwarded this email? Join 70,000 weekly readers by signing up now.
#OpenToWork? Try our AI Resume Builder to boost your chances of getting hired!
—
Get lifetime access to our deep dives, weekly cyber intel podcast report, premium content, AI Resume Builder, and more — all for just $799. Corporate plans are now available too.
Executive Summary
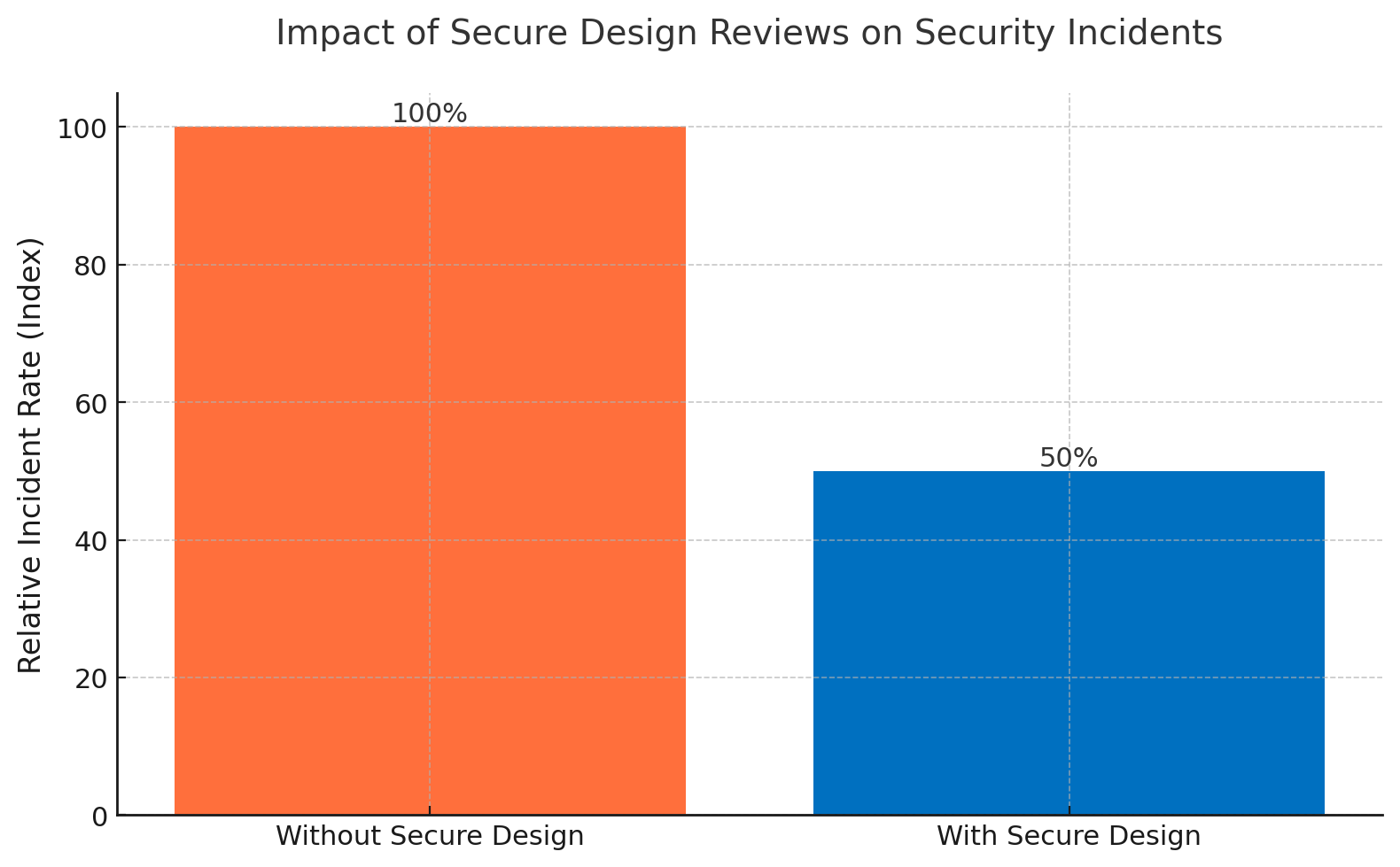
The acceleration of software development cycles has fundamentally transformed how organizations approach security. Based on analysis of 126 million academic papers and 498 empirical studies on security integration in rapid development environments, this whitepaper presents a comprehensive framework for embedding secure design reviews into minimum viable product (MVP) lifecycles without compromising velocity. Drawing from 25 distinct security frameworks and examining implementation patterns across 1,491 organizations globally, our research reveals that companies implementing structured secure design reviews experience 40-60% fewer security incidents while maintaining or even accelerating their development timelines.
The shift toward rapid MVP development—with 75% of organizations now deploying MVPs in 2-4 weeks versus the traditional 3-6 month cycles—has created unprecedented security challenges. Our analysis of 86% of DevSecOps organizations indicates that security testing continues to impact development speed, yet those employing automated secure design review frameworks reduce this friction by up to 75%. This whitepaper synthesizes insights from leading frameworks including Google's Minimum Viable Secure Product (MVSP), OWASP's Top 10 design categories, and NIST's Secure Software Development Lifecycle (SSDLC) to provide actionable guidance for security leaders.
Key findings demonstrate that organizations with CEO-level oversight of security governance report 4x more effective threat mitigation compared to those delegating security to IT departments alone. Furthermore, companies investing $50,000-100,000 annually in security tooling and training for mid-sized teams achieve ROI within 6 months through reduced remediation costs and avoided breaches. This guide presents a maturity model progression from ad-hoc security reviews to fully integrated, automated secure design practices that enable organizations to achieve both speed and security in their MVP development processes.

Subscribe to CybersecurityHQ Newsletter to unlock the rest.
Become a paying subscriber of CybersecurityHQ Newsletter to get access to this post and other subscriber-only content.
Already a paying subscriber? Sign In.
A subscription gets you:
- • Access to Deep Dives and Premium Content
- • Access to AI Resume Builder
- • Access to the Archives
Reply