- Defend & Conquer
- Posts
- Securing downstream data flows from SaaS to internal systems
Securing downstream data flows from SaaS to internal systems
CybersecurityHQ Report - Pro Members
Welcome reader to a 🔒 pro subscriber-only deep dive 🔒.
Brought to you by:
👣 Smallstep – Secures Wi-Fi, VPNs, ZTNA, SaaS and APIs with hardware-bound credentials powered by ACME Device Attestation
📊 LockThreat – AI-powered GRC that replaces legacy tools and unifies compliance, risk, audit and vendor management in one platform
Forwarded this email? Join 70,000 weekly readers by signing up now.
#OpenToWork? Try our AI Resume Builder to boost your chances of getting hired!
—
Get lifetime access to our deep dives, weekly cyber intel podcast report, premium content, AI Resume Builder, and more — all for just $799. Corporate plans are now available too.
Executive Summary
SaaS breaches surged 300% in 2024¹, with attackers exfiltrating data within nine minutes of initial access¹. Traditional perimeter defenses fail against these integration pathways—the connective tissue between cloud applications and internal systems that organizations depend on for business operations.
Global breach costs fell to $4.44 million in 2025 (down 9%)², driven by AI-powered detection and faster response capabilities. Yet U.S. costs hit $10.22 million³, and multi-environment breaches cost $5.05 million with 276-day containment cycles⁴. Organizations detect faster but face expanding attack surfaces from hybrid architectures that span on-premises infrastructure, multiple clouds, and hundreds of SaaS applications.
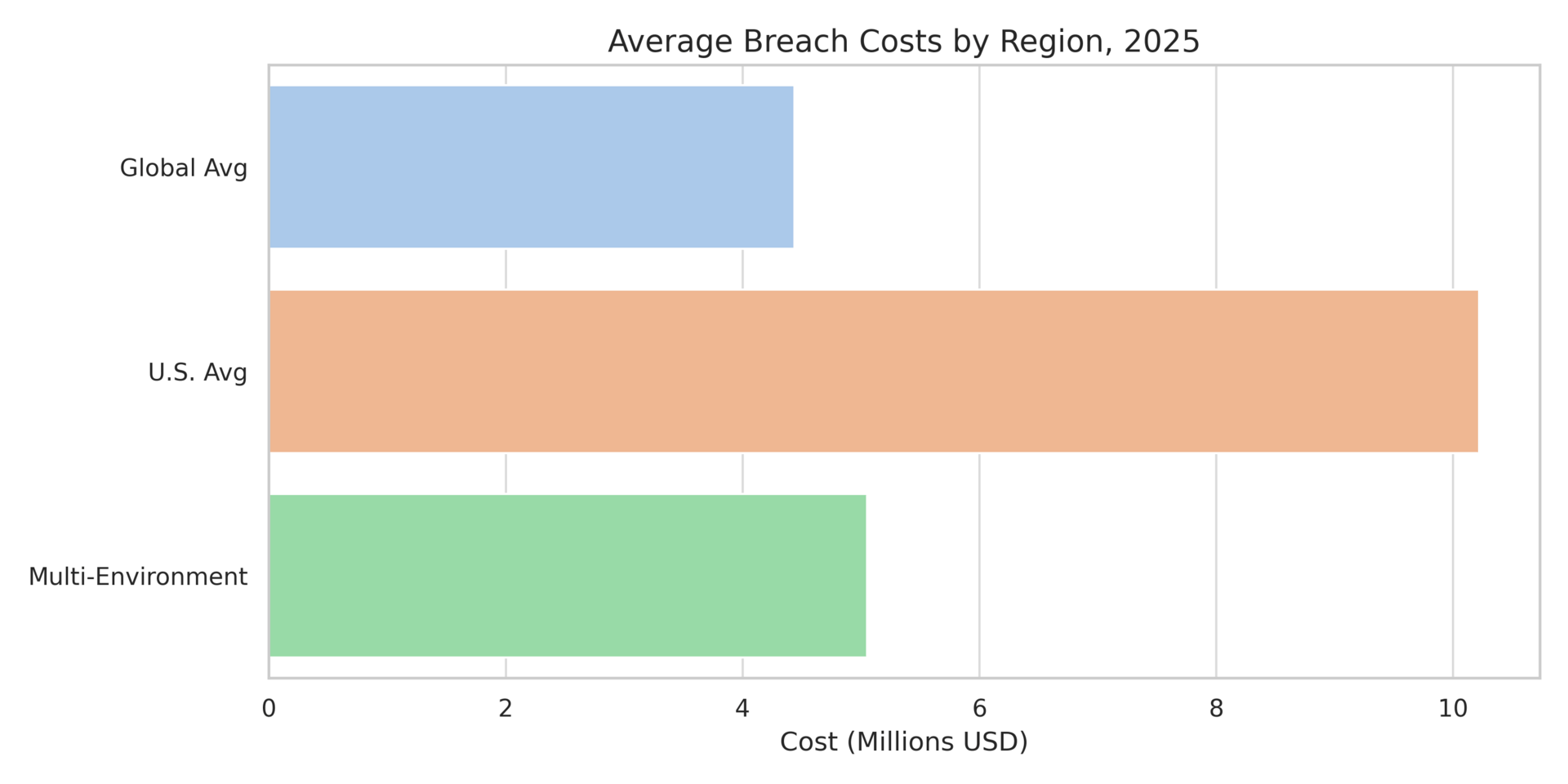
Identity failures drive breaches. 97% of AI-incident organizations lacked adequate access controls². Shadow AI added $670,000 to breach costs in 20% of cases⁵. The Snowflake breaches hitting AT&T, Santander, and Ticketmaster traced to missing multi-factor authentication on customer accounts⁶.
CISOs must implement Zero Trust architectures aligned with DORA (effective January 17, 2025)⁷ and NIST SP 800-53⁸. This requires strengthening both human and non-human identity controls, implementing continuous verification for data flows, and cutting mean detection time from the current 241-day average⁹.

Subscribe to CybersecurityHQ Newsletter to unlock the rest.
Become a paying subscriber of CybersecurityHQ Newsletter to get access to this post and other subscriber-only content.
Already a paying subscriber? Sign In.
A subscription gets you:
- • Access to Deep Dives and Premium Content
- • Access to AI Resume Builder
- • Access to the Archives
Reply