- Defend & Conquer
- Posts
- Tactical use of deception and honeypots in volatile threat climates
Tactical use of deception and honeypots in volatile threat climates
CybersecurityHQ Report - Pro Members

Welcome reader to a 🔒 pro subscriber-only deep dive 🔒.
Brought to you by:
👣 Smallstep – Secures Wi-Fi, VPNs, ZTNA, SaaS and APIs with hardware-bound credentials powered by ACME Device Attestation
📊 LockThreat – AI-powered GRC that replaces legacy tools and unifies compliance, risk, audit and vendor management in one platform
Forwarded this email? Join 70,000 weekly readers by signing up now.
#OpenToWork? Try our AI Resume Builder to boost your chances of getting hired!
—
Get lifetime access to our deep dives, weekly cyber intel podcast report, premium content, AI Resume Builder, and more — all for just $799. Corporate plans are now available too.
Executive Summary
The modern threat landscape demands a fundamental shift from reactive to proactive defense. With the median attacker dwell time at eight days while adversaries achieve Active Directory access within 16 hours¹, organizations face a critical detection gap that traditional perimeter defenses cannot address. Deception technologies and honeypots represent the most effective mechanism for closing this gap, delivering near-zero false-positive threat detection while imposing significant operational costs on attackers.
The strategic imperative is clear. The global deception technology market is projected to reach $7.20 billion by 2032, reflecting a compound annual growth rate of 13.6 percent from 2025². This growth correlates directly with escalating cybercrime damages, expected to reach $10.5 trillion annually by 2025³. Organizations deploying enterprise-grade deception platforms report average annual cost avoidance of $17.4 million, with containment time decreasing from 86 days to 81 days in the financial services sector⁴.
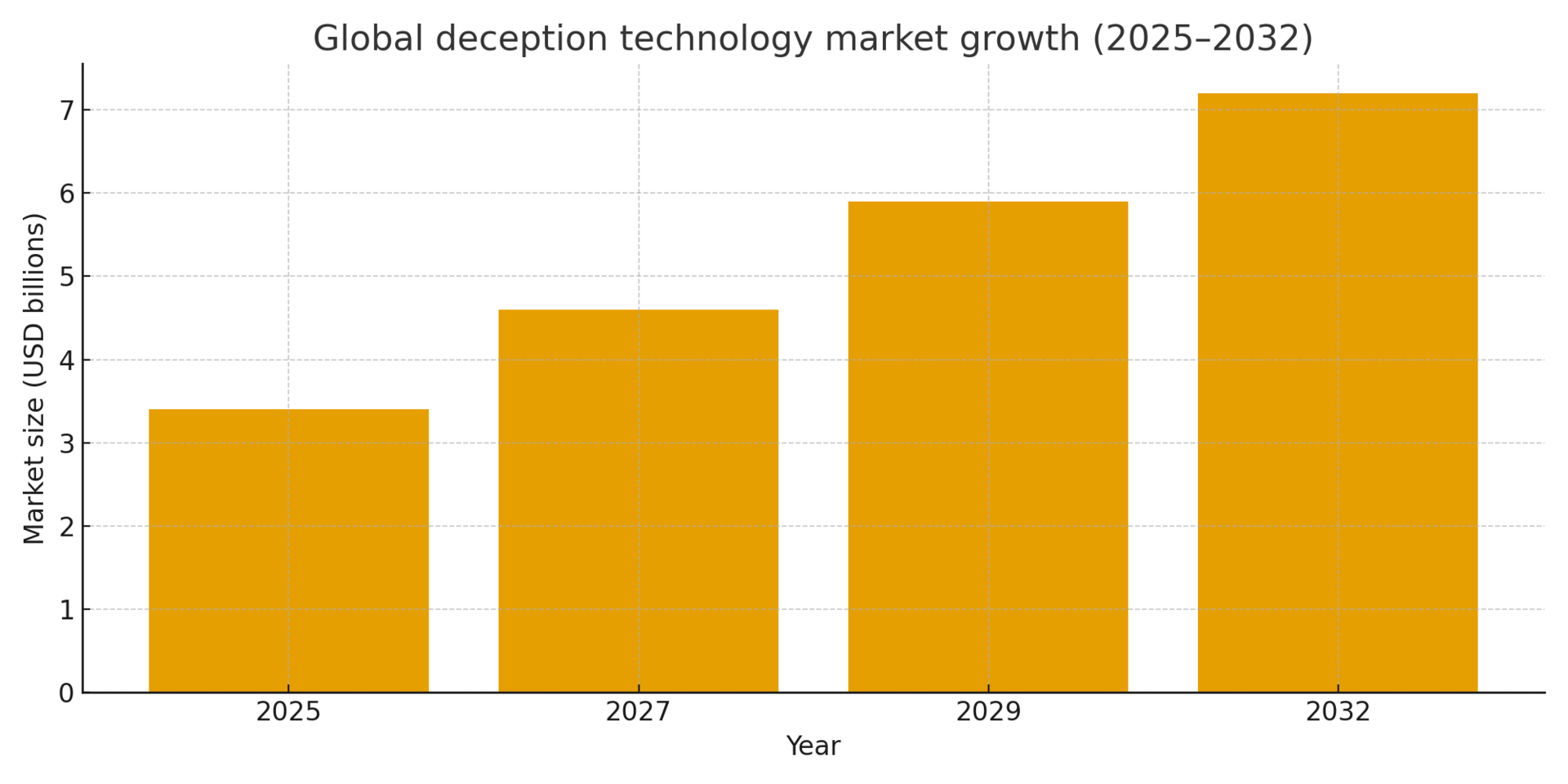
Chief Information Security Officers face three converging pressures: accelerating threat velocity, expanding attack surfaces driven by digital transformation, and persistent talent shortages. Fifty-two percent of organizations report that threat detection and response operations are more difficult than two years ago⁵. Deception technologies address these challenges by creating high-fidelity alerts that require minimal analyst expertise to triage, functioning as force multipliers for understaffed security operations centers.
This whitepaper provides a comprehensive framework for CISOs to evaluate, implement, and scale deception capabilities. Key findings include the criticality of CEO oversight of AI governance as the element most correlated with bottom-line impact⁶, the necessity of fundamentally redesigning workflows to capture value from security investments, and the requirement for hybrid deployment models that balance centralized governance with distributed execution. Organizations that successfully deploy deception report 60 percent reductions in false positives and 47 percent improvements in incident response time⁷.
The board-level imperative is to transition from prevention-focused security models to active defense architectures that assume breach and prioritize post-compromise detection. This strategic shift, enabled by deception technology, represents the primary defense against nation-state actors, ransomware syndicates, and AI-enhanced threats that increasingly characterize the 2025 threat landscape.

Subscribe to CybersecurityHQ Newsletter to unlock the rest.
Become a paying subscriber of CybersecurityHQ Newsletter to get access to this post and other subscriber-only content.
Already a paying subscriber? Sign In.
A subscription gets you:
- • Access to Deep Dives and Premium Content
- • Access to AI Resume Builder
- • Access to the Archives
Reply