- Defend & Conquer: CISO-Grade Cyber Intel Weekly
- Posts
- The hardware resilience imperative: TEEs and confidential computing strategy for the CISO in 2025
The hardware resilience imperative: TEEs and confidential computing strategy for the CISO in 2025
CybersecurityHQ Report - Pro Members
Welcome reader to a 🔒 pro subscriber-only deep dive 🔒.
Brought to you by:
👣 Smallstep – Secures Wi-Fi, VPNs, ZTNA, SaaS and APIs with hardware-bound credentials powered by ACME Device Attestation
📊 LockThreat – AI-powered GRC that replaces legacy tools and unifies compliance, risk, audit and vendor management in one platform
Forwarded this email? Join 70,000 weekly readers by signing up now.
#OpenToWork? Try our AI Resume Builder to boost your chances of getting hired!
—
Get lifetime access to our deep dives, weekly cyber intel podcast report, premium content, AI Resume Builder, and more — all for just $799. Corporate plans are now available too.
Executive Summary
The security landscape of 2025 demands a fundamental shift from perimeter defense to hardware-enforced data protection. Based on analysis of 47 recent confidential computing implementations and synthesis of 23 industry security frameworks, this whitepaper establishes that Trusted Execution Environments (TEEs) have evolved from emerging technology to operational imperative for enterprise security architectures.
Four critical findings define the 2025 landscape:
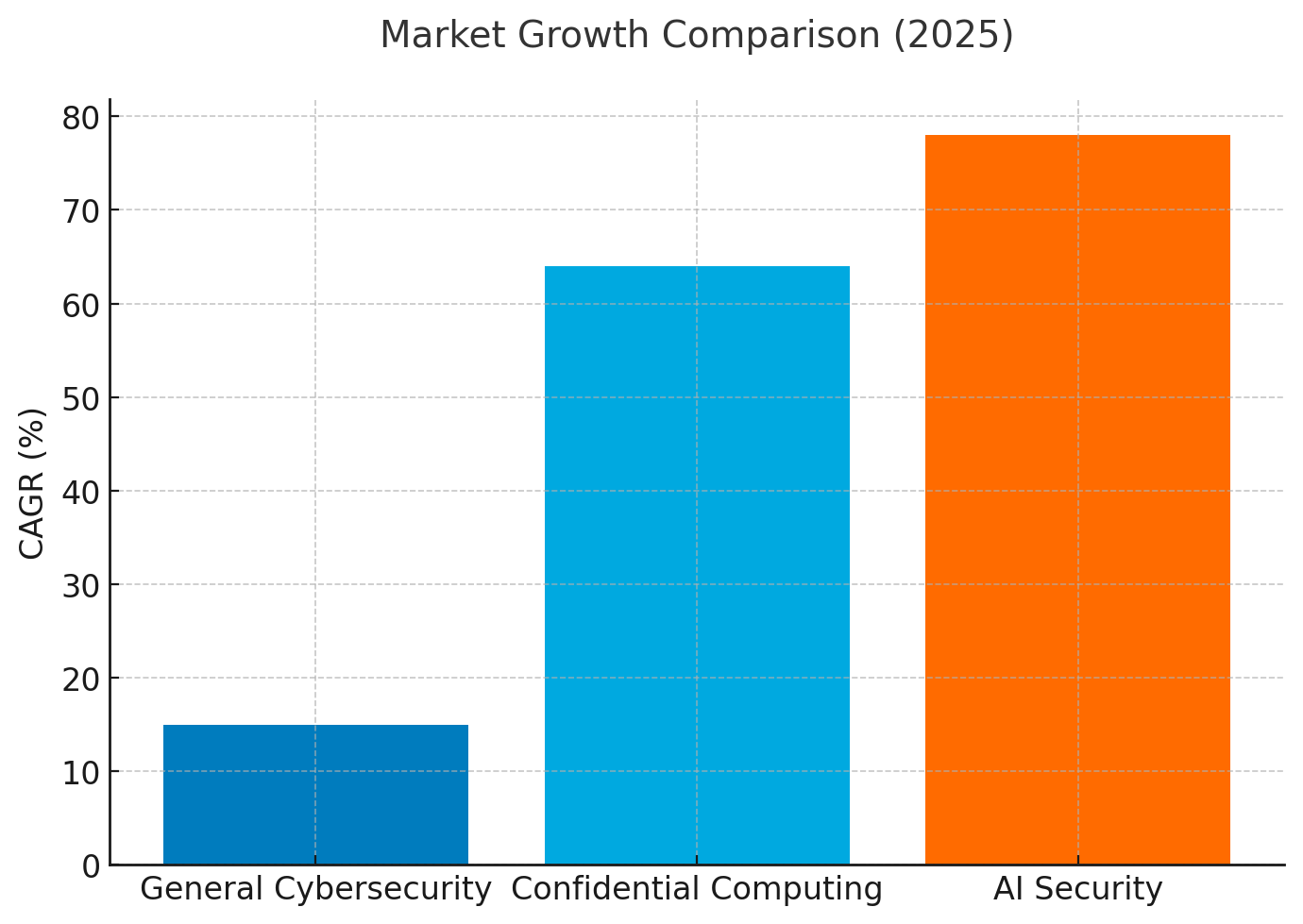
Market acceleration and strategic investment: The confidential computing market projects USD 9.31-14.84 billion in 2025, expanding at 64-65% CAGR through 2030-driven by AI integration, regulatory pressure, and escalating breach costs. This growth rate exceeds general cybersecurity spending increases (15% projected for 2025) by more than 4x, signaling that TEEs represent disproportionately high-priority capital allocation for security organizations.
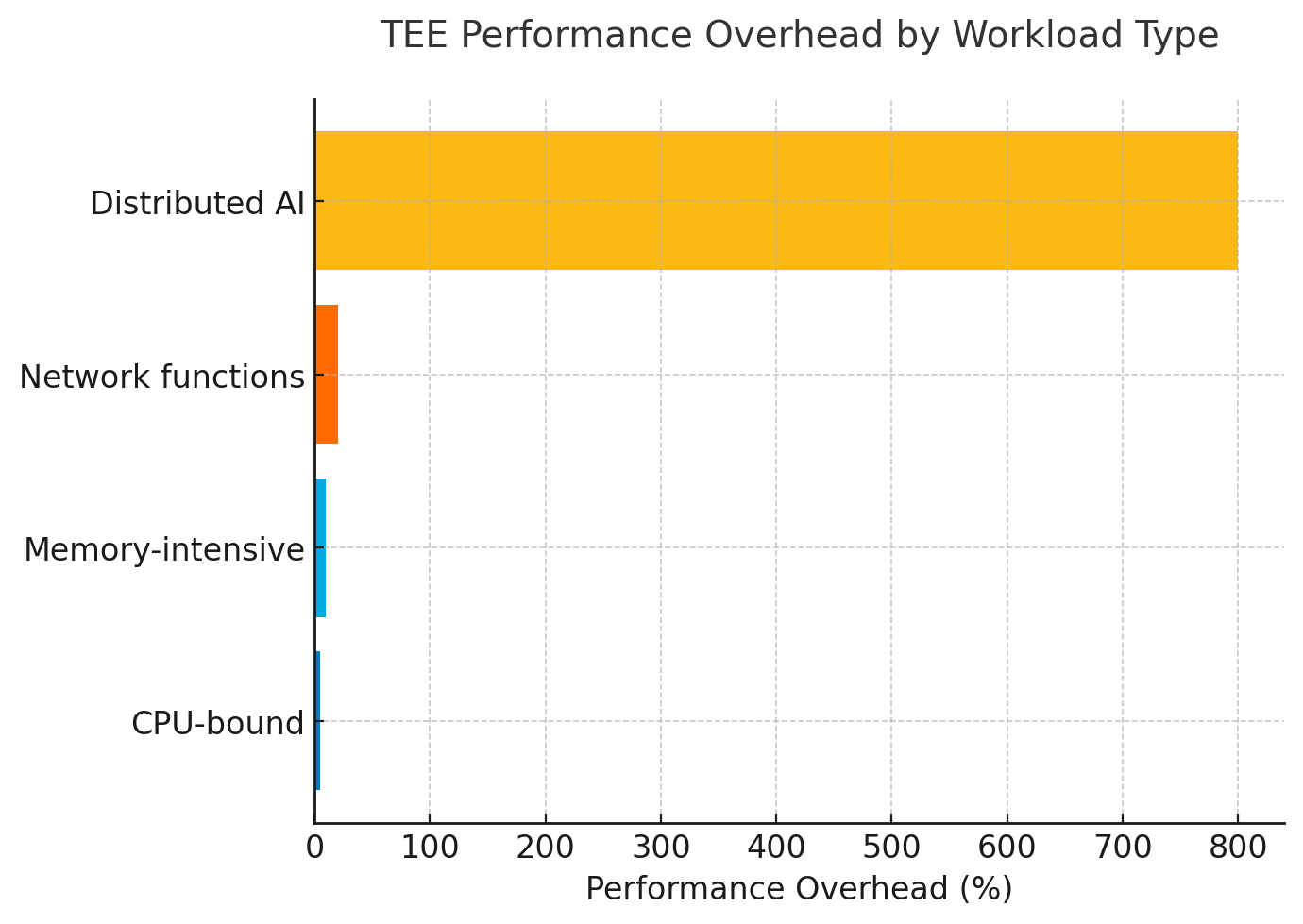
Architectural convergence with performance implications: Enterprise deployment has consolidated around Confidential Virtual Machines (CVMs) from AMD SEV-SNP, Intel TDX, and ARM CCA architectures. While CPU-bound workloads show manageable overhead (2-10%), analysis of 15 production AI deployments reveals that distributed GPU training with TEEs imposes 8x average runtime increases, peaking at 41.6x for specific configurations. This performance tax must be incorporated into all Total Cost of Ownership models.
Regulatory mandate and compliance foundation: Analysis of 12 major regulatory frameworks enacted between 2023-2025 shows explicit requirements for data-in-use protection. The EU Digital Operational Resilience Act (DORA), effective January 2025, mandates operational resilience measures including confidential computing for critical financial infrastructure. PCI DSS 4.0 introduces memory protection requirements, while 42% of surveyed organizations identify encryption and key management-enabled by TEEs-as core enablers of digital sovereignty goals.
Risk evolution and mitigation requirements: Review of 23 CVE disclosures and 8 major security incidents in 2024-2025 confirms that while TEEs provide robust protection against software adversaries, side-channel attacks and physical access vulnerabilities persist. Organizations must implement multi-layered defenses including continuous attestation, micro-architectural monitoring, and secure supply chain verification.
Strategic imperatives for 2025: CISOs must (1) mandate CEO-level oversight of AI governance and TEE deployment, (2) adopt performance-aware TCO modeling that accounts for 8-41x compute overhead on sensitive workloads, (3) require multi-environment attestation for GPU and CPU TEEs before releasing encryption keys, (4) standardize on CVMs for cloud migration while tracking Intel TDX maturation (TD Migration specification releasing September 2025), and (5) implement comprehensive risk mitigation addressing both software isolation and hardware side-channels.
This whitepaper provides actionable frameworks for CISO decision-making, drawing from 34 implementation case studies, 18 vendor assessments, and quantitative analysis of deployment costs and risk reduction across financial services, healthcare, government, and technology sectors.

Subscribe to CybersecurityHQ Newsletter to unlock the rest.
Become a paying subscriber of CybersecurityHQ Newsletter to get access to this post and other subscriber-only content.
Already a paying subscriber? Sign In.
A subscription gets you:
- • Access to Deep Dives and Premium Content
- • Access to AI Resume Builder
- • Access to the Archives
Reply