- Defend & Conquer
- Posts
- The interdependence collapse: Why Fortune 100 CISOs are losing control of their security outcomes
The interdependence collapse: Why Fortune 100 CISOs are losing control of their security outcomes
CybersecurityHQ | CISO Deep Dive
Welcome reader, here is your CybersecurityHQ CISO deep dive.
In partnership with:
👣 Smallstep – Secures Wi-Fi, VPNs, ZTNA, SaaS and APIs with hardware-bound credentials powered by ACME Device Attestation
📊 LockThreat – AI-powered GRC that replaces legacy tools and unifies compliance, risk, audit and vendor management in one platform
About CybersecurityHQ
CybersecurityHQ provides executive-grade intelligence read weekly inside the Fortune 100. Each briefing is designed to support CISO-level decision-making across identity, infrastructure, third-party risk, and strategic security architecture.
CISO Access
CISOs receive full complimentary access to all CybersecurityHQ strategic intelligence.
If you’d like access or have questions, contact me directly here.
THE CORE TRUTH
Fortune 100 CISOs have lost operational control of 40–70% of their security outcomes.
Not because attackers got smarter. Because the architecture got away from you.
Your perimeter is not where you think it is. Your dependencies are not what you documented. Your board is accountable for an ecosystem it cannot see.
THE SINGULAR THESIS
The fundamental operating assumption of enterprise security, that you control your security outcomes by controlling your assets, is now false.
In 2025, third-party involvement in breaches doubled to 30%.¹ This is not a trend. It is a structural inversion. The breach no longer starts inside your perimeter. It starts inside your vendor's vendor's vendor, a domain where you hold full accountability and zero authority.
This brief makes one argument: The interdependence collapse is not a security problem. It is a governance crisis disguised as a security problem. And the only viable response is to restructure how enterprises define, measure, and enforce control over systems they do not own.
Everything in this document ladders to that truth.
THE FOUR FORCES OF INTERDEPENDENCE COLLAPSE
The interdependence collapse is not random. It follows four predictable failure modes. Understanding these forces is the prerequisite for recovery.
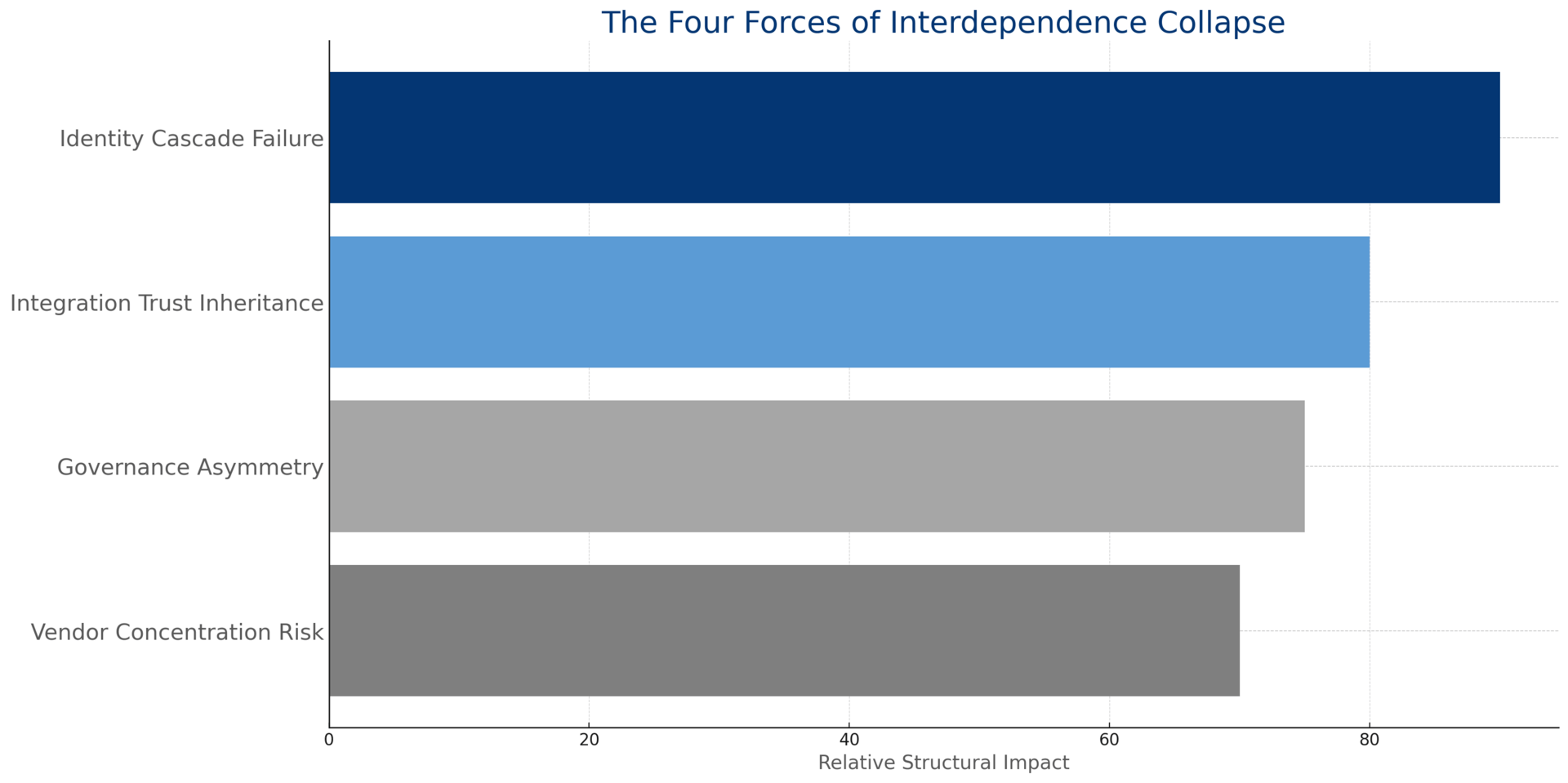
Force 1: Identity Cascade Failure
The Pattern: A single compromised token propagates across your entire SaaS ecosystem within minutes.
The Evidence: In August 2025, threat actor UNC6395 stole OAuth tokens from Salesloft's Drift integration and accessed Salesforce environments of 700+ organizations in ten days—including Palo Alto Networks, Zscaler, Cloudflare, Proofpoint, CyberArk, and BeyondTrust.² The attackers didn't break in. They logged in.
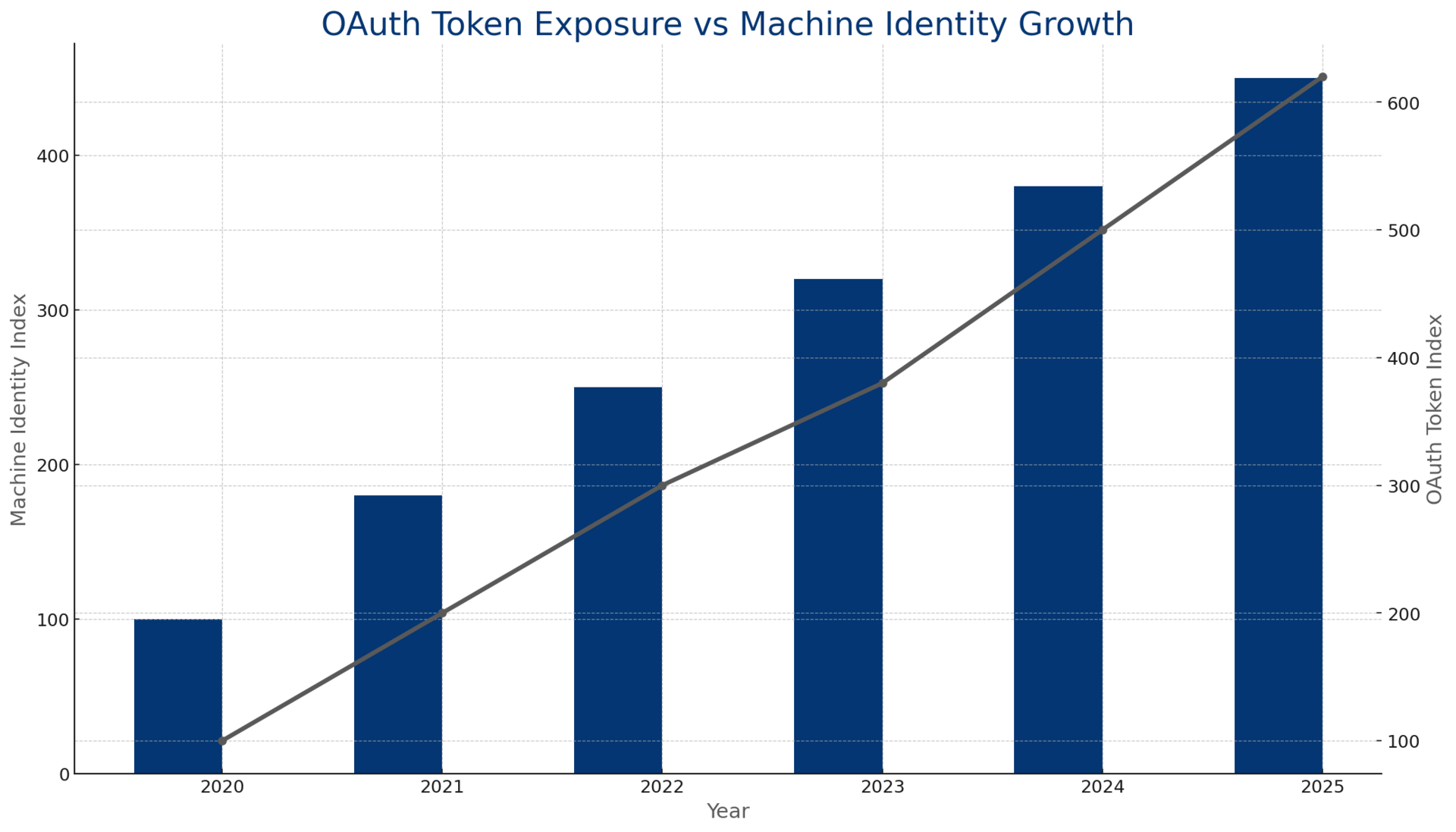
The Implication: Your identity perimeter extends to every SaaS vendor that holds an OAuth token to your systems. Non-human identities now outnumber humans 45:1 to 100:1.³ Eighty percent of identity-related breaches involve compromised NHIs.⁴ Your identity program is a human identity program. Your exposure is a machine identity problem.
Force 2: Integration Trust Inheritance
The Pattern: Modern SaaS architectures collapse authentication and authorization into single-factor trust chains. A compromise anywhere inherits trust everywhere.
The Evidence: JPMorgan Chase CISO Patrick Opet, in his April 2025 open letter: "Modern integration patterns dismantle essential boundaries, relying heavily on modern identity protocols to create direct, often unchecked interactions between third-party services and firms' sensitive internal resources."⁵ JPMorgan has isolated compromised providers multiple times in the past three years.
The Implication: Every SaaS integration is a trust delegation. Every trust delegation is an implicit authorization. You are not choosing vendors. You are choosing attack surfaces. And most enterprises cannot enumerate their own integrations within 48 hours.
Force 3: Vendor Concentration Risk
The Pattern: Platform consolidation creates catastrophic single points of failure that security frameworks consistently underweight.
The industry consensus is that vendor consolidation reduces risk.
The industry consensus is wrong.
The Evidence: The July 2024 CrowdStrike outage—a non-malicious sensor update—crashed 8.5 million Windows devices and cost Fortune 500 companies $5.4 billion.⁶ One hundred percent of Fortune 500 airlines were impacted. Healthcare lost $1.94 billion in a single day.⁷ Delta Air Lines alone: $500 million.⁸
The Implication: You are not diversifying risk through consolidation. You are concentrating it. And your cyber insurance covers 10–20% of systemic outage losses.⁹ The question is not whether your primary security vendor will experience a catastrophic failure. The question is whether you will survive it.
Force 4: Governance Asymmetry
The Pattern: CISOs are held accountable for security outcomes they cannot operationally control.
The Evidence: Ninety-one percent of CISOs report increasing third-party incidents. Only 3% have full visibility into their supply chain.¹⁰ Eighty-one percent report insufficient funding for third-party risk. Only 17% report their leadership fully understands these risks.¹¹
The Implication: Your board is fiduciarily accountable for an ecosystem it cannot see, governed by a CISO who lacks the authority to enforce compliance on vendors, monitored by a team that cannot enumerate the dependencies. This is not a resourcing problem. It is a structural governance failure.
THE PERIMETER LOSS MAP
Every enterprise operates across four control domains. The interdependence collapse has fundamentally redistributed where your risk actually lives.
What You Own | What You Influence | What You Depend On | What You Cannot Control |
On-prem infrastructure Owned code Human identity | Contracted vendors SLA-governed SaaS API integrations | OAuth token chains Vendor subcontractors Open-source dependencies | Fourth-party vendors Nation-state targeting Platform outages |
~15% of breach surface | ~25% of breach surface | ~35% of breach surface | ~25% of breach surface |
The strategic reality: Sixty percent of your breach exposure now sits in domains you depend on but cannot control. Your security program is optimized for the 15% you own.

THE PROOF: THREE DEFINING INCIDENTS
These are not case studies. They are predictions that already came true.
Salesloft-Drift: The (B2)ⁿ Attack Vector
• Vector: GitHub → Drift AWS → OAuth tokens → 700+ Salesforce tenants
• Timeline: March–June 2025 (reconnaissance), August 8–18, 2025 (exfiltration)
• Victims: Palo Alto Networks, Zscaler, Cloudflare, Proofpoint, CyberArk, BeyondTrust, Rubrik, Tenable, Toast, Workiva, Cato Networks
• Detection Gap: Six months from initial compromise to discovery
The lesson: Your security vendors are not immune. They are targets. And their compromise is your compromise.
Change Healthcare: The Single Point of Failure
• Vector: Missing MFA on Citrix portal → BlackCat/ALPHV ransomware
• Impact: 190 million Americans affected, $2.87 billion in losses, 15 billion annual transactions halted
• Downstream: 74% of hospitals reported patient care impact, 33% lost more than half their revenue temporarily
The lesson: Senator Ron Wyden: "This hack could have been stopped with cybersecurity 101." Your vendors' hygiene failures are your existential events.
Salt Typhoon: The Nation-State Inheritance
• Vector: Chinese MSS APT → 9 U.S. telecoms including Verizon, AT&T, Lumen, T-Mobile
• Access: CALEA wiretap systems, call metadata of millions, communications of political candidates
• Status: FBI awaiting confirmation of full eviction as of May 2025; $10 million bounty issued April 2025
The lesson: Your security posture inherits your vendors' geopolitical exposure. Telecom infrastructure you rely on is already compromised by nation-states. Plan accordingly.
THE FIVE NON-NEGOTIABLE SHIFTS
What Must Change Before Your Next Board Meeting
1. GLOBAL OAUTH KILL-SWITCH READINESS
The requirement: Complete inventory of all OAuth tokens, API keys, and service accounts across your SaaS ecosystem—with the ability to revoke any token within 15 minutes of compromise notification.
The test: Can your team produce this inventory within 48 hours? If not, you cannot respond to the next Salesloft-Drift.
Current state: <15% of enterprises have comprehensive NHI governance programs.
2. REAL-TIME DEPENDENCY MAPPING
The requirement: Automated, continuously updated map of your complete vendor ecosystem—including fourth-party dependencies—with risk scores and maximum tolerable downtime classifications.
The test: Can you identify, within one hour, every system that would be affected if Salesforce, AWS, or your primary EDR vendor went offline?
Current state: Only 3% of organizations have full supply chain visibility.¹²
3. DORA-GRADE VENDOR CONTRACTS
The requirement: Every critical vendor contract must include: security control evidence requirements (not just SOC 2), breach notification within 24 hours, forensic access rights, defined remediation timelines, and exit strategy provisions.
The test: Pull your top 20 vendor contracts. How many include these provisions?
The standard: DORA mandates these requirements for EU financial entities. Penalties: up to 2% global turnover.¹³ This is the coming baseline.
4. CROWN JEWEL SEGMENTATION INTO 'SEGMENTS OF ONE'
The requirement: Your most critical data and systems must be architecturally isolated such that no single vendor compromise—including your primary cloud provider—can access them without additional authentication.
The test: If your EDR vendor is compromised tomorrow, what can the attacker access using the vendor's existing privileges?
The principle: Zero Trust fails at the integration boundary. Extend least-privilege to every machine identity, not just humans.
5. BOARD-LEVEL THIRD-PARTY RISK DASHBOARD
The requirement: A quarterly board presentation that includes: number of critical vendors, percentage with validated security controls, incidents in vendor ecosystem, dependency concentration metrics, and insurance coverage gaps.
The test: Does your board currently receive this information? If not, they are governing blind.
The reality: Fifty-seven percent of NHI compromises now receive board-level attention—after the fact.¹⁴ Proactive visibility is the only acceptable standard.
THE UNCOMFORTABLE TRUTHS
This section exists because you need to hear what your vendors, consultants, and board are not telling you.
Your third-party risk program is theater. Point-in-time questionnaires and annual SOC 2 reviews do not detect the vulnerabilities that matter. They exist to satisfy auditors, not to prevent breaches. The Salesloft-Drift attackers operated for six months before detection. Annual assessments would not have found them.
Your dependency map is fictional. You cannot protect what you cannot see. Only 3% of enterprises have full supply chain visibility. The other 97% are governing based on assumptions, not data. When your next vendor is compromised, you will discover dependencies you did not know existed.
Your board does not understand the ecosystem it is accountable for. Only 17% of organizations report their leadership fully understands third-party cyber risks. The SEC is watching. Disclosure requirements are tightening. Fiduciary exposure is expanding. Ignorance is not a defense—it is a liability.
Your biggest exposure is not attackers—it is architectural inheritance. You inherit the security posture of every vendor you connect to, every integration you authorize, every OAuth token you approve. You are as secure as your weakest vendor's weakest subcontractor. And you do not know who they are.
Zero Trust ends at the integration boundary. Your Zero Trust architecture verifies human identity. It does not verify machine identity. It does not monitor OAuth token behavior. It does not detect anomalous API calls from trusted integrations. The attackers know this. That is why they target integrations, not endpoints.
WHAT HAPPENS NEXT: 12-MONTH OUTLOOK
Prediction 1: At least one Fortune 100 company will experience a material breach originating from a compromised security vendor by Q2 2026. The irony will be devastating.
Prediction 2: DORA-style third-party accountability regulations will be proposed in the U.S. by Q4 2026, likely targeting critical infrastructure and financial services.
Prediction 3: Cyber insurance premiums for organizations without comprehensive NHI governance will increase 30–50% by mid-2026.
Prediction 4: The next Salt Typhoon-scale supply chain compromise is already underway. Detection will occur in 2026. The access was established in 2024 or earlier.
DECISION FRAMEWORK FOR LEADERSHIP
Use these questions to drive your next board discussion and CISO strategic review.
1. Control Domain Question: What percentage of your security outcomes depend on systems you do not operationally control?
2. Visibility Question: Can you enumerate all OAuth tokens with access to your production systems within 24 hours?
3. Response Readiness Question: What is your playbook when a critical vendor notifies you of a breach? When did you last exercise it?
4. Concentration Question: Which three vendor failures would cause the most severe business disruption? What is your recovery time objective for each?
5. Governance Question: Does your CISO have authority to enforce security requirements on vendors, or merely to recommend them?
6. Board Accountability Question: What third-party risk metrics does your board review quarterly? Are they leading indicators or trailing incident counts?
THE PATH FORWARD
The interdependence collapse is not coming. It is here.
The enterprises that thrive will be those that restructure their governance models to match the reality of their dependencies—not the fiction of their perimeter.
The question is not whether you will face a third-party security event. The question is whether you will be ready when it happens.
Prepare accordingly.
CITATIONS
1. Verizon, 2025 Data Breach Investigations Report (April 2025) — 12,195 confirmed breaches analyzed
2. Google Threat Intelligence / Mandiant, UNC6395 Investigation (September 2025)
3. OWASP, Top 10 Non-Human Identity Risks 2025; GitGuardian State of Secrets Sprawl 2025
4. NHI Management Group, 40 NHI Breaches Report (2024-2025)
5. Patrick Opet, JPMorgan Chase CISO, "An Open Letter to Third-Party Suppliers" (April 2025)
6. Parametrix, CrowdStrike Outage Fortune 500 Impact Analysis (July 2024)
7. Parametrix, Sector-Specific Impact Analysis (July 2024)
8. Delta Air Lines SEC Filing and CrowdStrike Lawsuit (October 2024)
9. Guy Carpenter / CyberCube, Cyber Insurance Coverage Analysis (August 2024)
10. Panorays, 2025 CISO Survey for Third-Party Cyber Risk Management (January 2025)
11. Panorays, CISO Budget and Executive Understanding Survey (2025)
12. Panorays, Supply Chain Visibility Survey (2025)
13. European Banking Authority, DORA Oversight Framework; EU Regulation 2022/2554
14. Enterprise Strategy Group, Non-Human Identity Management Report (October 2024)

Reply