- Defend & Conquer
- Posts
- The rise of ‘stealth supply chain attacks’: From npm to AI dependencies
The rise of ‘stealth supply chain attacks’: From npm to AI dependencies
CybersecurityHQ - Free in-depth report

Welcome reader to a 🔍 free deep dive. No paywall, just insights.
Brought to you by:
👣 Smallstep – Secures Wi-Fi, VPNs, ZTNA, SaaS and APIs with hardware-bound credentials powered by ACME Device Attestation
🏄♀️ Upwind Security – Real-time cloud security that connects runtime to build-time to stop threats and boost DevSecOps productivity
🔧 Endor Labs – App security from legacy C++ to Bazel monorepos, with reachability-based risk detection and fix suggestions across the SDLC
📊 LockThreat – AI-powered GRC that replaces legacy tools and unifies compliance, risk, audit and vendor management in one platform
Forwarded this email? Join 70,000 weekly readers by signing up now.
#OpenToWork? Try our AI Resume Builder to boost your chances of getting hired!
—
CybersecurityHQ’s premium content is now available exclusively to CISOs at no cost. As a CISO, you get full access to all premium insights and analysis. Want in? Just reach out to me directly and I’ll get you set up.
—
Get one-year access to our deep dives, weekly Cyber Intel Podcast Report, premium content, AI Resume Builder, and more for just $299. Corporate plans are available too.
Software supply chain attacks have evolved from crude package impersonation schemes to sophisticated, multi-phase operations that exploit the trust inherent in modern development ecosystems. What began as isolated incidents in package registries has transformed into a systematic threat landscape where attackers leverage everything from typosquatting to AI model poisoning. The numbers tell a stark story: malicious package discoveries increased 188% year-over-year in 2025, with over 16,000 new threats identified in a single quarter. For CISOs navigating this landscape, understanding the evolution from npm vulnerabilities to AI dependency risks has become critical to organizational survival.
The Early Days: When Trust Became a Vulnerability
The modern software supply chain attack traces its origins to 2018, when the Event-Stream incident shocked the JavaScript community. A popular npm package with over 2 million weekly downloads was hijacked when its maintainer transferred ownership to an unknown developer. The new maintainer injected code that targeted Bitcoin wallets, specifically those used by the Copay application. The attack went undetected for months, demonstrating how a single compromised package could cascade through thousands of applications.
This incident revealed fundamental weaknesses in the npm ecosystem. With over 2 million packages and minimal vetting, npm had become a vast attack surface. Early attacks relied on simple tactics: typosquatting (creating packages with names similar to popular libraries), dependency confusion (exploiting naming conflicts between public and private packages), and maintainer account compromises. Between 2018 and 2023, security researchers documented over 5,000 malicious packages across npm, PyPI, and RubyGems.
The economics favored attackers. Publishing a malicious package cost nothing. Detection often took weeks or months. A single successful attack could yield cryptocurrency theft, credential harvesting, or backdoor access to thousands of systems. Meanwhile, the JavaScript ecosystem's culture of micro-dependencies meant that applications often included hundreds or thousands of third-party packages, multiplying exposure.
The Sophistication Surge: 2024-2025
By 2024, supply chain attacks had evolved beyond recognition. Simple typosquatting gave way to multi-phase attacks with sophisticated evasion techniques. The numbers reflect this escalation: CVE reports for npm packages increased 27% year-over-year in 2024, reaching over 33,000. But raw vulnerability counts only tell part of the story.

Modern attacks employ multiple layers of obfuscation. Packages now use time-delayed payloads that activate days or weeks after installation, evading initial security scans. Malware is encrypted and fragmented across multiple files. Some packages check for analysis environments and remain dormant when detected. Others use legitimate functionality as cover, adding malicious code to otherwise useful libraries.
The 2025 attacks demonstrate this evolution. In March, researchers discovered npm packages that appeared benign during installation but downloaded second-stage payloads from compromised WordPress sites weeks later. These payloads established reverse shells, exfiltrated environment variables, and could wipe entire codebases on command. One package, masquerading as a JSON parsing utility, contained a logic bomb triggered by the French phrase "remise à zéro" sent from a command server. Upon activation, it deleted all project files, configurations, and then itself, leaving no forensic evidence.
State-sponsored actors entered the ecosystem in force. North Korean operatives published 67 malicious npm packages in July 2025 as part of their "Contagious Interview" campaign. These packages, disguised as coding challenge solutions, deployed the BeaverTail stealer and InvisibleFerret backdoor. Over 17,000 downloads occurred before discovery. The campaign targeted cryptocurrency developers and companies, aligning with North Korea's broader cyber-enabled theft operations.
The Credential Theft Revolution
Phishing emerged as a primary vector for supply chain attacks in 2025. The Prettier tooling incident in July exemplified this trend. Attackers sent sophisticated phishing emails to maintainers of popular development tools, stealing credentials for packages like eslint-config-prettier and synckit. Within hours of compromise, attackers published malicious versions containing backdoors.
This shift to credential theft reflects operational maturity. Rather than creating new malicious packages that might be detected, attackers hijack trusted packages with established user bases. A ReversingLabs report found a 12% increase in leaked developer secrets in packages during 2025, providing attackers with ammunition for future compromises.
The React Native Aria ecosystem compromise in June 2025 showed the devastating potential. Sixteen packages in the Gluestack UI framework were hijacked simultaneously, affecting over 1 million weekly downloads. The malicious code included a Remote Access Trojan capable of taking screenshots, executing shell commands, and exfiltrating data. The attack remained active for six days before detection.
The Cryptocurrency Connection
Financial motivation drives many supply chain attacks. In 2025, researchers identified multiple npm packages specifically targeting cryptocurrency infrastructure. Packages with names like "pancakeswap-oracle-prediction" and "ethereum-smart-contract" stole 80-85% of funds from users' wallets. One campaign, attributed to user "@crypto-exploit," accumulated over 2,100 downloads across multiple packages.
The sophistication of crypto-targeting attacks increased dramatically. A PyPI package called "semantic-types" demonstrated the "sleeper" pattern: initially published as a legitimate utility in late 2024, it turned malicious in January 2025. The updated version monkey-patched Solana wallet generation functions to capture private keys. Rather than immediately stealing funds, it encrypted the keys and embedded them in dummy blockchain transactions, allowing attackers to retrieve them later while avoiding detection.
The AI Supply Chain: A New Frontier
As organizations rushed to adopt AI capabilities, attackers followed. The AI supply chain introduced entirely new attack vectors: poisoned models, compromised training data, and malicious ML frameworks. Unlike traditional code packages, AI components blur the line between data and executable code.
The first major AI supply chain attack came in February 2024 when JFrog researchers discovered a trojanized machine learning model on Hugging Face. The model, distributed as a Pickle file, executed arbitrary code when loaded. This wasn't a theoretical risk: the backdoor provided full system access to attackers. The incident highlighted a critical vulnerability: many ML model formats inherently allow code execution.
By March 2024, attackers had industrialized AI supply chain attacks. Campaigns emerged where adversaries created fake Hugging Face accounts impersonating major companies like Facebook, Visa, and SpaceX. These accounts uploaded models containing malware that exfiltrated environment variables, including API keys and credentials. One fake "Meta AI" repository included code that phoned home whenever loaded with the trust_remote_code=True flag.

The Slopsquatting Revolution
Perhaps the most innovative attack vector emerged from AI itself. Researchers coined the term "slopsquatting" to describe attacks exploiting large language model hallucinations. When coding assistants like GitHub Copilot or ChatGPT suggest importing non-existent packages, attackers quickly register these names with malicious payloads.
A 2025 academic study tested 16 popular coding assistants and found they generated over 205,000 unique bogus package names. Commercial models hallucinated non-existent imports in 5.2% of cases; open-source models in 21.7%. This created a race condition: attackers monitoring LLM outputs could register suggested packages before legitimate developers realized they didn't exist.
The implications are staggering. As Microsoft's CEO projected that 95% of code may be AI-generated by 2030, the attack surface expands exponentially. Every hallucinated import becomes a potential vulnerability. Every AI-suggested dependency requires verification.
The Detection Arms Race
Security vendors scrambled to address evolving threats. Traditional vulnerability scanners, designed to detect known CVEs, proved inadequate against novel malware. New approaches emerged combining static analysis, dynamic behavior monitoring, and machine learning.
Socket.dev pioneered "deep package inspection," analyzing JavaScript packages for suspicious capabilities like unexpected network calls, filesystem access, or environment variable reading. Their system caught packages that would delete files on command, steal cryptocurrency, or establish reverse shells. In one quarter of 2025, Socket identified over 16,000 malicious packages.
For AI models, companies like Protect AI developed specialized scanners. Their Guardian tool processed millions of Hugging Face models, flagging unsafe code execution, embedded secrets, and suspicious model architectures. The open-source ModelScan project provided similar capabilities for organizations wanting to verify models before deployment.
But detection faces fundamental challenges. Attackers actively research bypasses. The "nullifAI" technique discovered in 2025 deliberately corrupted model files to crash scanners while remaining executable. By compressing files in unexpected formats and introducing partial corruption, attackers caused security tools to skip analysis while PyTorch still loaded the malicious code.
The Ecosystem Response
Package registries implemented new defenses throughout 2024-2025. npm mandated two-factor authentication for popular package maintainers. PyPI added automated malware scanning. Both registries established bug bounty programs specifically for supply chain vulnerabilities.
The results were mixed. While basic typosquatting attacks dropped 70% from 2023 to 2024, sophisticated attacks increased. Attackers adapted rather than retreated. The focus shifted from quantity to quality: fewer but more targeted attacks with higher success rates.
Industry initiatives emerged to address systemic issues. The Open Source Security Foundation launched projects like Sigstore for package signing and Scorecards for evaluating project security. The Supply-chain Levels for Software Artifacts (SLSA) framework defined standards for build integrity and provenance.
The Blast Radius Problem
Modern applications' dependency graphs amplify supply chain risks. A typical Node.js application includes hundreds of direct dependencies and thousands of transitive ones. Each represents a potential attack vector. When a popular package is compromised, the blast radius can encompass millions of applications.
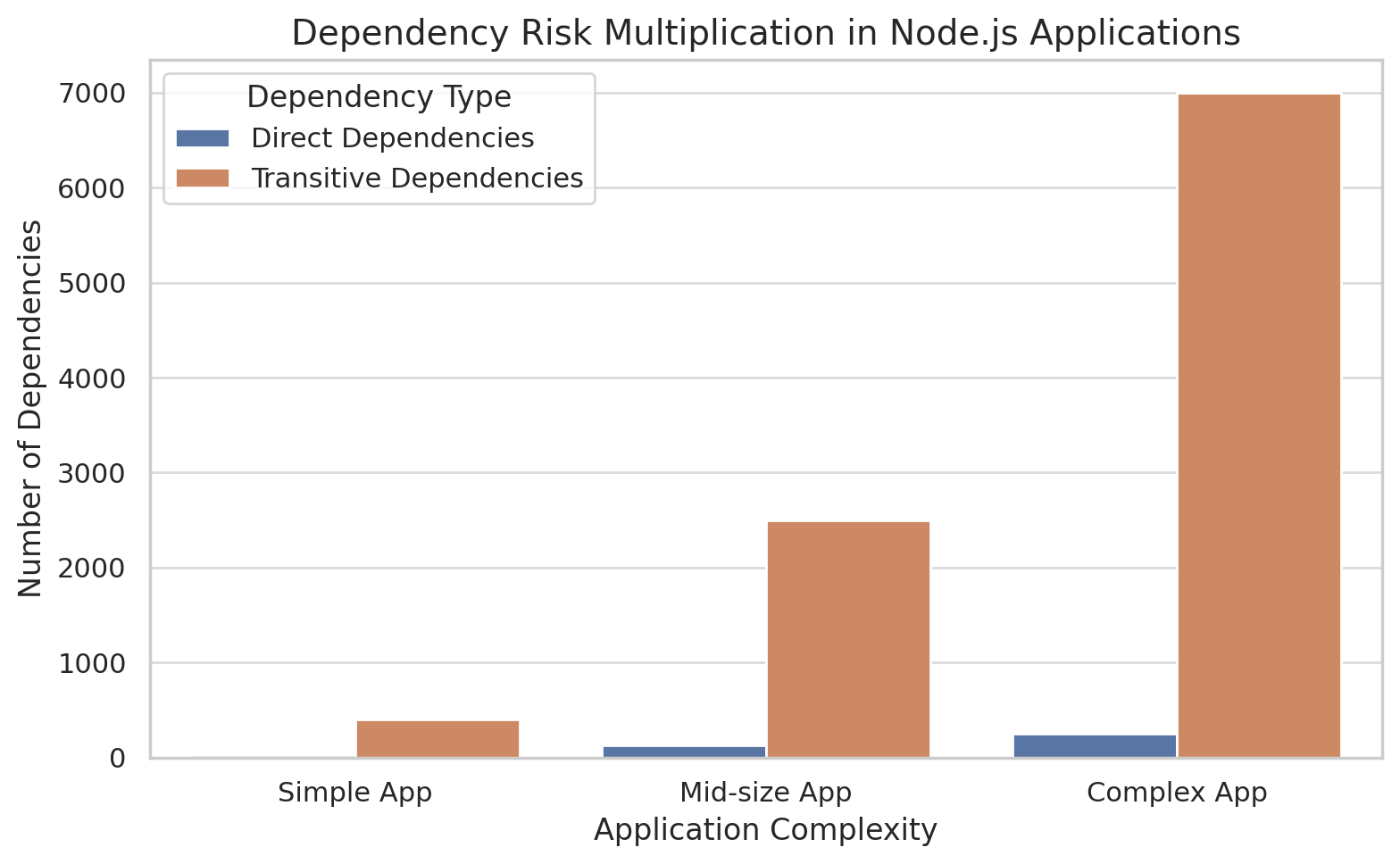
The React Native Aria incident demonstrated this multiplication effect. Sixteen compromised packages affected the entire Gluestack UI ecosystem. Organizations using Gluestack inadvertently installed malware across their entire React Native application portfolio. The attack's reach extended far beyond direct package users.
This interconnectedness creates single points of failure. Research shows that compromising certain highly-connected packages could impact over 50% of the npm ecosystem. These "crown jewel" packages become prime targets for sophisticated attackers.
The 2025 Threat Landscape
Current attack patterns show clear trends. Data exfiltration dominates, comprising 56% of malicious packages discovered in Q2 2025. Attackers prioritize stealing credentials, API keys, and source code over destructive payloads. This shift reflects the value of persistent access over one-time damage.

Geographic attribution increasingly points to state actors. Beyond North Korea's campaigns, researchers identified clusters of attacks originating from Russia, China, and Iran. These nations view supply chain attacks as asymmetric warfare: low-cost operations with potentially devastating impact on adversaries' digital infrastructure.
The convergence of traditional and AI supply chains creates compound risks. Attackers use AI to generate convincing phishing emails targeting package maintainers. They employ LLMs to obfuscate malicious code. Some campaigns use AI-generated documentation to make malicious packages appear legitimate.
Mitigation Strategies That Work
Organizations successfully defending against supply chain attacks share common practices. They maintain Software Bills of Materials (SBOMs) tracking every dependency. They use private registries with vetted packages rather than pulling directly from public sources. They implement behavioral monitoring in build environments to detect anomalous activity.
For AI dependencies, leading organizations extend these practices. They scan all models before deployment, verify model provenance, and monitor model behavior at runtime. Some maintain "model registries" equivalent to private package registries, ensuring only vetted AI components enter production.
The most effective defenses are proactive. Organizations conduct regular supply chain audits, implement least-privilege principles for build systems, and maintain incident response plans specific to supply chain compromises. They treat third-party code with the same scrutiny as external network connections.
The Road Ahead
Supply chain attacks will continue evolving. As defenses improve, attackers develop new techniques. The integration of AI into development workflows creates novel attack surfaces we're only beginning to understand. The economic incentives favor attackers: successful compromises yield high returns with relatively low investment.
For CISOs, the message is clear. Supply chain security can no longer be an afterthought. It requires dedicated resources, continuous monitoring, and constant adaptation. Organizations must balance the efficiency gains of modern development practices with the security risks they introduce.
The transformation from simple npm typosquatting to AI model poisoning represents a fundamental shift in software security. Attackers no longer need to breach perimeters directly. They compromise the building blocks of applications, achieving widespread impact through minimal effort. As software development increasingly relies on external components and AI assistance, supply chain attacks will remain a critical threat vector.
Success requires acknowledging an uncomfortable truth: perfect prevention is impossible. The focus must shift to rapid detection, containment, and recovery. Organizations that accept this reality and build accordingly will survive in an era where trust itself has become a vulnerability.
The rise of stealth supply chain attacks marks a new chapter in cybersecurity. From npm to AI dependencies, the evolution continues. CISOs who understand this trajectory and prepare for its implications will protect their organizations. Those who don't will become statistics in next year's breach reports.
Stay safe, stay secure.
The CybersecurityHQ Team
Reply