- CybersecurityHQ
- Posts
- Using predictive modeling to map cybersecurity breach cascades in enterprise network infrastructures
Using predictive modeling to map cybersecurity breach cascades in enterprise network infrastructures
CybersecurityHQ Report - Pro Members
Welcome reader to a 🔒 pro subscriber-only deep dive 🔒.
Brought to you by:
🏄♀️ Upwind Security – Real-time cloud security that connects runtime to build-time to stop threats and boost DevSecOps productivity
🔧 Endor Labs – Application security for the software development revolution, from ancient C++ code to bazel monorepos, and everything in between
🧠 Ridge Security – The AI-powered offensive security validation platform
Forwarded this email? Join 70,000 weekly readers by signing up now.
#OpenToWork? Try our AI Resume Builder to boost your chances of getting hired!
—
Get lifetime access to our deep dives, weekly cyber intel podcast report, premium content, AI Resume Builder, and more — all for just $799. Corporate plans are now available too.
Executive Summary
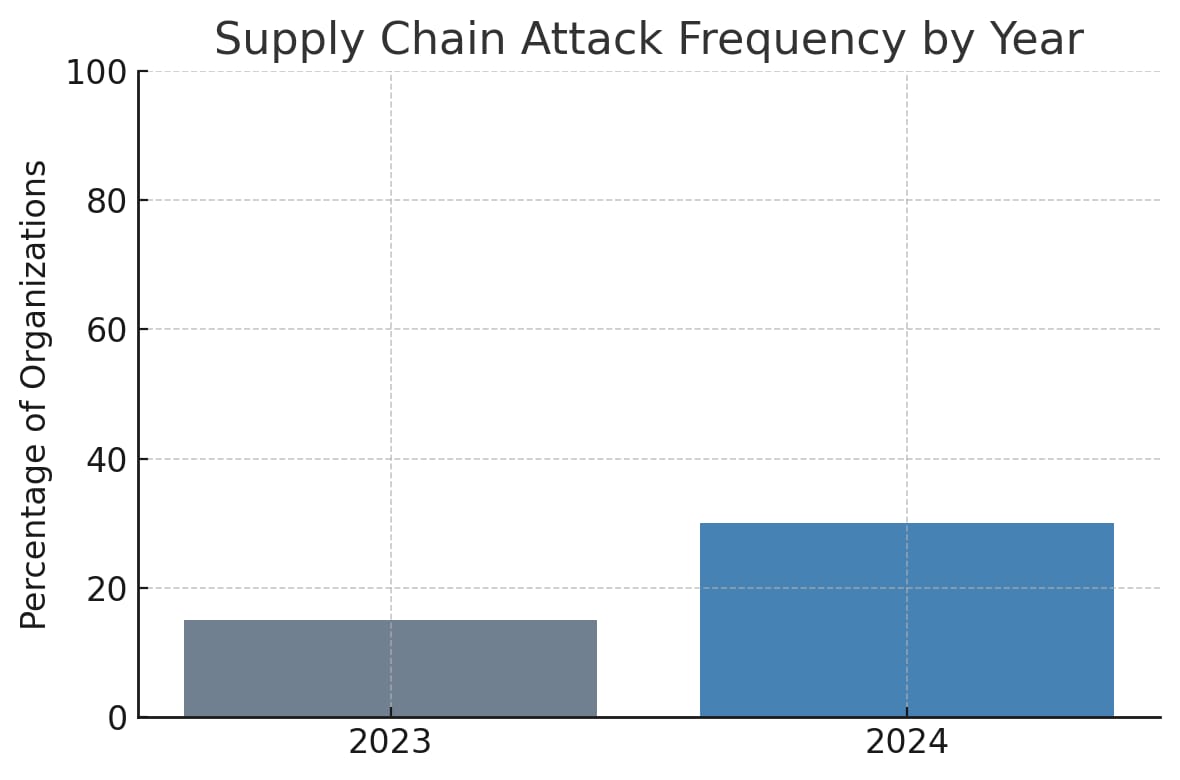
Enterprise networks face an escalating threat from cybersecurity breach cascades, where initial compromises propagate through interconnected systems, amplifying damage exponentially. Recent incidents demonstrate this reality: the 2024 Change Healthcare breach disrupted operations across multiple healthcare providers, insurers, and pharmaceutical companies, while supply chain attacks have doubled in frequency, affecting 30% of organizations in 2024 compared to 15% in 2023.
Predictive modeling offers a proactive defense against these cascading threats. By leveraging graph theory, machine learning, and Bayesian networks, organizations can map potential attack paths before breaches occur. Graph-based models visualize how attackers might navigate from entry points to critical assets, while machine learning algorithms detect anomalies and predict attack progression with up to 90% accuracy. Bayesian networks quantify the probability of various attack scenarios, enabling risk-based resource allocation.
Implementation varies by industry. Financial institutions use network models to assess systemic cyber risk, healthcare organizations employ digital twins to simulate attack propagation, and critical infrastructure operators utilize Bayesian attack graphs to prevent catastrophic failures. These techniques have proven effective: organizations using predictive modeling report 40-60% reductions in successful breach cascades.
For cybersecurity leaders, the implications are clear. Predictive modeling transforms security from reactive to proactive, enabling data-driven investment decisions and cross-functional collaboration. Success requires CEO-level commitment, workflow redesign, and continuous model refinement. As cyber threats evolve, organizations that master predictive breach cascade mapping will build resilience against tomorrow's sophisticated attacks.
Introduction
The digital transformation of enterprise operations has created unprecedented interconnectivity, but with it comes heightened vulnerability to cascading cyber failures. Modern organizations operate vast networks of interdependent systems where a single breach can trigger a domino effect, compromising multiple business functions and extending damage far beyond the initial point of entry.
Recent statistics underscore this growing threat. Cybersecurity damages are projected to reach $10.5 trillion annually by 2025, with breach cascades representing an increasingly significant portion of these losses. The 2024 Verizon Data Breach Investigations Report revealed that third-party involvement in breaches doubled from 15% to 30% in just one year, highlighting how interconnected digital ecosystems amplify risk. High-profile incidents like the 2024 Change Healthcare breach demonstrated how a single compromise can cascade across entire industries, disrupting hospitals, insurers, and pharmaceutical supply chains.
Traditional cybersecurity approaches, which focus on perimeter defense and isolated incident response, prove inadequate against cascade threats. Security teams need capabilities to anticipate how breaches might propagate through their networks, identify critical interdependencies, and implement targeted defenses at key chokepoints. This is where predictive modeling becomes essential.
Predictive modeling for breach cascade mapping represents a paradigm shift in cybersecurity strategy. Rather than waiting for attacks to unfold, organizations can simulate potential breach scenarios, visualize attack paths, and quantify cascade risks. These techniques draw from diverse fields including graph theory, machine learning, and probabilistic modeling to create comprehensive views of enterprise vulnerability.
This whitepaper examines how predictive modeling techniques enable organizations to map and mitigate potential breach cascades. We explore the underlying technologies, implementation approaches, industry applications, and strategic implications for cybersecurity leaders. Our analysis draws on the latest research and real-world deployments to provide actionable insights for organizations seeking to build cascade-resilient networks.

Subscribe to CybersecurityHQ Newsletter to unlock the rest.
Become a paying subscriber of CybersecurityHQ Newsletter to get access to this post and other subscriber-only content.
Already a paying subscriber? Sign In.
A subscription gets you:
- • Access to Deep Dives and Premium Content
- • Access to AI Resume Builder
- • Access to the Archives
Reply