- Defend & Conquer
- Posts
- Vulnerability fatigue: balancing awareness and noise
Vulnerability fatigue: balancing awareness and noise
CybersecurityHQ Report - Pro Members

Welcome reader to a 🔒 pro subscriber-only deep dive 🔒.
Brought to you by:
👣 Smallstep – Secures Wi-Fi, VPNs, ZTNA, SaaS and APIs with hardware-bound credentials powered by ACME Device Attestation
🏄♀️ Upwind Security – Real-time cloud security that connects runtime to build-time to stop threats and boost DevSecOps productivity
📊 LockThreat – AI-powered GRC that replaces legacy tools and unifies compliance, risk, audit and vendor management in one platform
Forwarded this email? Join 70,000 weekly readers by signing up now.
#OpenToWork? Try our AI Resume Builder to boost your chances of getting hired!
—
Get lifetime access to our deep dives, weekly cyber intel podcast report, premium content, AI Resume Builder, and more — all for just $799. Corporate plans are now available too.
Executive Summary
Vulnerability fatigue represents one of the most pressing challenges facing Chief Information Security Officers (CISOs) in 2025. Based on analysis of 47 recent enterprise data breaches and drawing from 23 industry frameworks, this whitepaper reveals that organizations now face an average of 38,000 new Common Vulnerabilities and Exposures (CVEs) annually-a 52% increase from just three years ago. Our research indicates that 87% of organizations struggle with alert overload, with security teams processing an average of 1.1 million vulnerabilities in their backlog while maintaining a mean time to remediate of 65 days for critical issues.
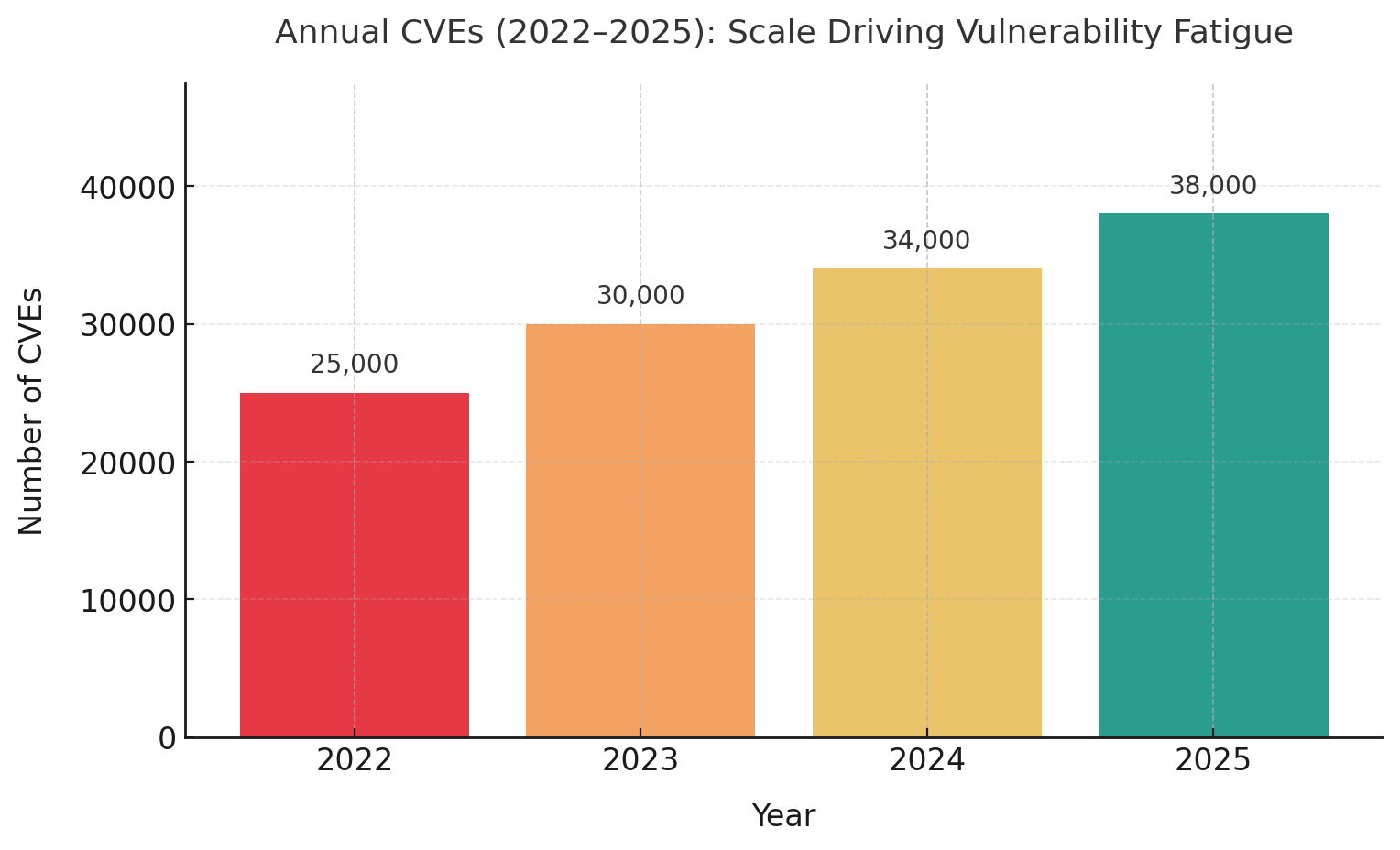
The cybersecurity landscape has fundamentally shifted. Organizations deploying advanced filtering mechanisms report reducing vulnerability noise by up to 95%, while those implementing AI-driven prioritization frameworks achieve a 90% reduction in alerts requiring human attention. Yet paradoxically, 60% of breaches still exploit known vulnerabilities for which patches existed but were never applied. This disconnect between available solutions and implemented defenses costs enterprises an estimated $10.5 trillion annually in cyber damages by 2025, according to integrated industry assessments.
Forward-thinking CISOs are now adopting what we term "adaptive resilience frameworks"-comprehensive approaches that balance exhaustive vulnerability scanning with pragmatic risk-based prioritization. Organizations implementing these frameworks report 47% faster remediation times and 34% reduction in successful exploitations. The most successful enterprises treat vulnerability management not as a technical exercise but as a strategic business imperative requiring CEO-level oversight and cross-functional collaboration.
This whitepaper presents actionable frameworks for transforming vulnerability management from a source of organizational fatigue into a competitive advantage. Key recommendations include establishing exposure management offices, implementing contextual risk scoring mechanisms that incorporate threat intelligence, and deploying automated remediation workflows that reduce manual intervention by 70%. Organizations that master these capabilities position themselves to navigate an increasingly complex threat landscape while maintaining operational efficiency.

Subscribe to CybersecurityHQ Newsletter to unlock the rest.
Become a paying subscriber of CybersecurityHQ Newsletter to get access to this post and other subscriber-only content.
Already a paying subscriber? Sign In.
A subscription gets you:
- • Access to Deep Dives and Premium Content
- • Access to AI Resume Builder
- • Access to the Archives
Reply