- Defend & Conquer: CISO-Grade Cyber Intel Weekly
- Posts
- Weekly CISO Intelligence Briefing: November 13 - 19, 2025
Weekly CISO Intelligence Briefing: November 13 - 19, 2025
CybersecurityHQ weekly analysis
Welcome reader to your CybersecurityHQ report
Brought to you by:
👣 Smallstep – Secures Wi-Fi, VPNs, ZTNA, SaaS and APIs with hardware-bound credentials powered by ACME Device Attestation
📊 LockThreat – AI-powered GRC that replaces legacy tools and unifies compliance, risk, audit and vendor management in one platform
Forwarded this email? Join 70,000 weekly readers by signing up now.
—
Get annual access to our deep dives, weekly cyber intel podcast report, premium content, AI Resume Builder, and more — all for just $299. Corporate plans are now available too.
Introducing the CISO Access Plan Unlock premium CybersecurityHQ insights at no cost, exclusively for CISOs. Reach out to me to claim your access.
Top Targeted Sectors & Attack Trends



Threat Highlights:
Government / Public — Highest-impact sector this week.
Government networks globally absorbed an unusually dense wave of state-linked activity.
Russia escalated hybrid operations (missile + cyber) against Ukrainian civilian infrastructure, while Taiwan reported 2.4M+ daily intrusion attempts from China-aligned clusters. Multiple Western agencies issued joint advisories as Oracle and Citrix zero-days were exploited to gain access to municipal and regulatory systems. DHS warned of federal shutdown–related exposure windows increasing attacker opportunity.
Technology & Cloud — Most active ecosystem by event volume.
This sector absorbed the week’s largest technical blasts:
Cloudflare’s outage disrupted 20% of global traffic, Microsoft weathered a 15 Tbps DDoS, and critical vulnerabilities hit Fortinet, WatchGuard, Cisco ISE, and Azure. Supply-chain breaches (Logitech, Washington Post, Oracle EBS via Cl0p) underscored how fragile cloud/SaaS trust boundaries have become. AI-enabled threat activity surged: Anthropic disrupted a live AI-orchestrated espionage chain, and Chinese actors used LLM agents to weaponize JSON-based malware delivery.
Financial Services — High fraud pressure, moderate breach depth.
No mega-breaches, but fraud-adjacent activity spiked.
Dozens of dark-web posts advertised stolen government and corporate datasets feeding tax fraud, payroll diversion, and synthetic-identity workflows. DoorDash’s breach exposed large consumer payment data flows, and secondary trading around that data increased exposure for banks. Multiple ransomware groups probed fintech APIs using Microsoft zero-day exploit chains.
Healthcare — Consistent pressure, selective high-impact incidents.
Ransomware crews continued hitting labs and diagnostics providers (Vikor Scientific, AGFA) with data exfiltration models rather than full lockups. AI-crafted phishing lures targeted clinical admins with near-perfect voice and writing mimicry. No Tier 1 outages, but several disclosures show footholds were established weeks prior, suggesting dormant access for future extortion phases.
Energy & Utilities — Elevated national-security relevance, limited operational disruption.
Russian attacks on Kyiv’s residential and energy infrastructure were the most visible hybrid event.
In the West, utilities saw renewed scanning against OT-adjacent Cisco/WSUS systems. New UK/EU resilience bills and cybersecurity mandates indicated rising regulatory synchronization around power, water, and gas operators. Threat intel units observed an uptick in OT-targeted botnet traffic leveraging compromised SOHO devices.
Telecom / Mobile — Notable targeted espionage vectors.
Russia’s 24-hour mobile internet blackouts on travelers signaled operational testing of telecom choke-point control.
Pre-installed spyware was discovered on certain Samsung Galaxy models, with exploitation chains tied to government-linked intermediaries. China-linked clusters probed mobile carriers’ identity systems as part of broader reconnaissance ahead of elections and regional events.
Industrial / Manufacturing — Active exploitation but localized impact.
UNC6485’s exploitation of Triofox for RCE created entry points in several manufacturing networks.
Belarus-linked infrastructure supported botnet activity targeting embedded and IoT controllers. Supply-chain exposure was highlighted again via the Oracle EBS zero-day, hitting engineering and logistics data at PACCAR and others.
Retail / Consumer — Rising credential theft and extension-targeted supply-chain attacks.
Malicious Chrome extensions and cloaked npm packages (Adspect-based crypto scams) continued targeting consumer and retail environments. Restaurant groups (Jean-Georges) suffered ransomware operations, though attackers favored data leaks over operational disruption. RAT-based credential harvesting tied to fake crypto apps expanded across retail payment ecosystems.
Ransomware — High activity, mostly data-theft-driven.
Everest, Play, and Cl0p were the dominant operators this week.
Everest hit Under Armour (343GB exfiltration) and multiple regional orgs. Play ransomware hit Valley Plains Equipment, continuing its trend of attacking mid-sized operational businesses. Data-theft rather than encryption remains the preferred extortion model across multiple families, guided by AI-generated social engineering.
Exploits — Severe exploitation wave across vendor stack.
Critical vulnerabilities hit Fortinet FortiWeb, WatchGuard Fireware, Cisco firewalls, Lynx Gateway, Django, and VS Code extensions.
Cl0p exploited Oracle EBS CVE-2025-61882 across multiple enterprises. Samsung device spyware delivered via a zero-day saw active in-the-wild use. CISA added the FortiWeb OS command injection CVE-2025-58034 to the KEV catalog, indicating active exploitation.
Phishing — AI-enhanced, more evasive, increasingly enterprise-tailored.
Actors deployed Cloudflare- and Microsoft-branded lures, RAT-laced fake crypto extensions, and campus-targeted spearphishing. AI-generated impersonations of board members and deans hit universities and hospital networks. Invisible Unicode manipulation helped bypass legacy mail filters.
AI / MCP Exploitation — Sharpest upward trajectory (+48% WoW).
Chinese clusters executed a severity-10 AI-assisted intrusion using Anthropic’s toolchain for mutation and obfuscation.
PROMPTFLUX-style adaptive AI malware resurfaced with multi-model evasion. Attackers leveraged LLM agents to write lateral-movement scripts, generate polymorphic phishing payloads, and craft C-suite deepfake communications. Multiple cloud vendors disclosed serious AI inference framework flaws (Meta, Nvidia, Microsoft).
CybersecurityHQ: This Week’s Reports Based on Technical Research and Academic Papers
→ Free
The hidden layer of “unowned systems” — the new silent failure CISOs are ignoring 👉 Read the report
→ Pro subscriber-only
Audit readiness for new regulations (e.g., data‐sovereignty, critical infrastructure) emerging in 2025 👉 Read the report
Translating evolving geopolitical threat (state‐sponsored activity) into board‐level actionable plans 👉 Read the report
How the EU's Cyber Solidarity Act changes cross-border incident collaboration 👉 Read the report
Zero trust segmentation at large scale: The executive mandate for east-west resilience 👉 Read the report
And more inside - check out the full list here.
Cybersecurity Stocks
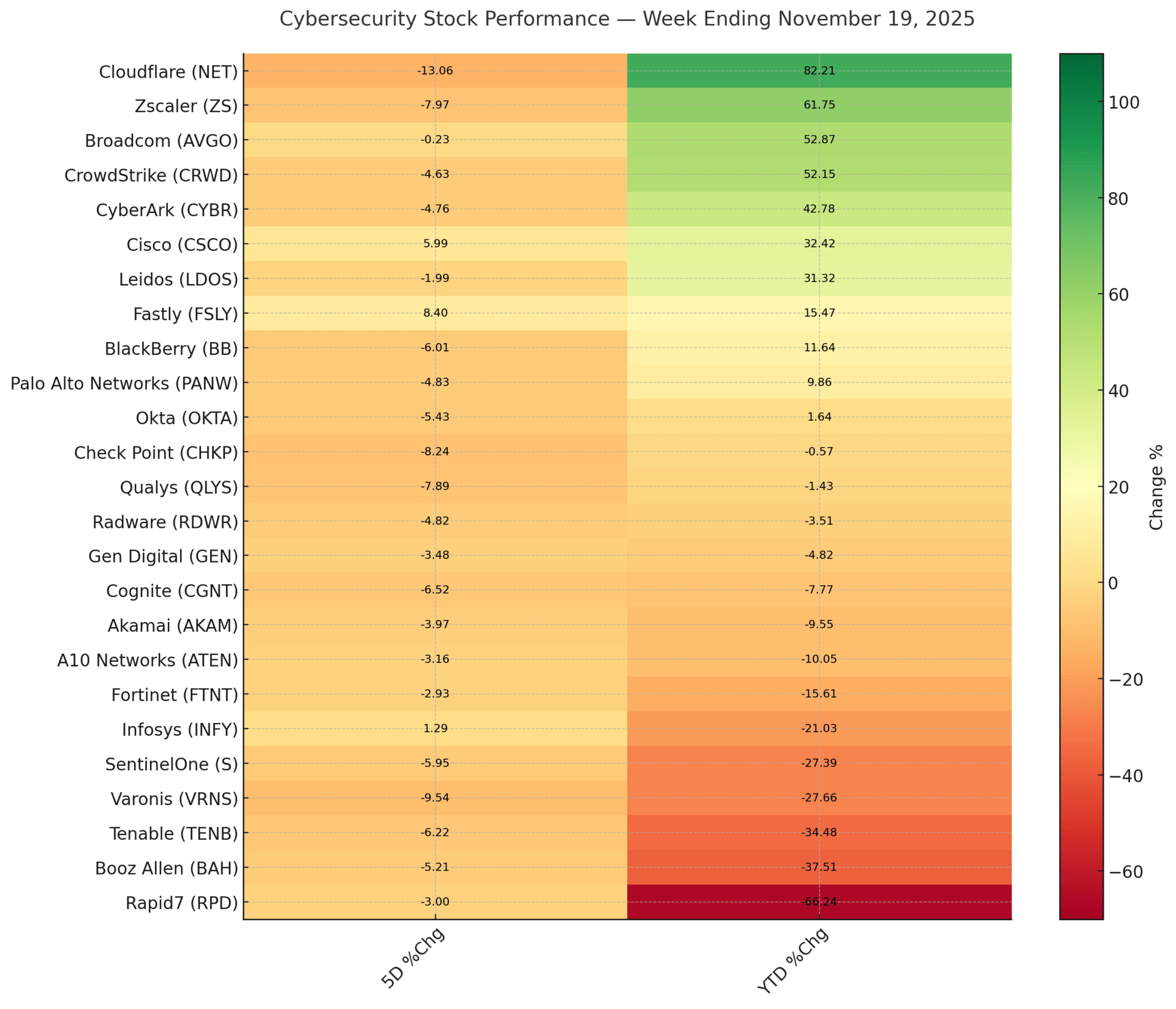
Market Intelligence
This week the market shifted toward resilience-driven security spending. The fallout from recent cloud outages pushed boards to reassess concentration risk and the operational fragility created by dependency on single providers. Investors paid closer attention to tools that reduce blast radius and maintain continuity during partial failures instead of simply detecting issues after they happen. AI is still a growth theme, but buyers favored products that automate real operational workflows and shorten recovery time rather than generic “AI-powered” claims.
Budget scrutiny increased across identity and access tools. Enterprises highlighted the cost of managing excessive credentials, inconsistent access paths, and duplicated identity systems. Vendors that simplify lifecycle management, shrink the identity footprint, and reduce manual work gained positive sentiment. The tactical posture for the week is to prioritize companies that lower operational overhead and dependency risk and to discount products that increase complexity without improving resilience.
Funding, Mergers, and Acquisitions
Cybersecurity
This week’s cybersecurity dealflow exposed a market shifting toward two forces: AI-driven consolidation at the top and aggressive capital rotation into exposure management, browser security, and security automation. SAFE’s acquisition of Balbix showed a decisive push toward unified exposure platforms built on AI-native risk modeling instead of legacy scoring. Palo Alto Networks’ 3.35 billion dollar acquisition of Chronosphere confirmed the same direction. Observability is being repositioned as a core security layer because AI-driven incident response depends on high-resolution telemetry.
Services continued consolidating. Amplix acquired 24By7Security to expand its MSSP footprint. TekSynap purchased JBA to deepen federal cyber operations support. Bugcrowd’s acquisition of MayhemSec fused crowdsourced offensive testing with automated exploit simulation.
Funding was fueled by AI-first defense platforms. Sublime Security’s 150 million dollar raise and Sweet Security’s 75 million dollar round signaled investor conviction in AI-powered threat detection and rapid containment. Nudge Security raised 22.5 million dollars for user-behavior driven automation. Apono secured 34 million dollars for continuous privileged access enforcement. Guardio raised 80 million dollars for browser-level defenses. The direction is unambiguous: capital flows are rewarding vendors that compress detection to action cycles and remove humans from bottleneck roles in exposure management.
Cloud Computing
Cloud and infrastructure M&A accelerated around one competitive truth. Control the compute and you control the market. Microsoft and Nvidia committed 15 billion dollars to Anthropic while Anthropic agreed to purchase 30 billion dollars of Azure compute. This redefined AI as an asset class where access to GPUs is a structural advantage. SoftBank sold 5.8 billion dollars of Nvidia stock to expand its OpenAI exposure and reinforced the same principle.
Google advanced its multi-billion euro expansion of AI data centers in Europe. Oracle-related data center financing continued scaling. Armis secured 435 million dollars at a 6.1 billion dollar valuation. Chaos Industries raised 510 million dollars for compute security infrastructure. Cloud M&A is now governed by sovereign compute needs and long-horizon GPU allocation. This is no longer a market-share contest. This is a resource control battle.
Quantum Computing
Quantum activity this week reflected a pivot from academic exploration to state-aligned infrastructure building. IonQ acquired Skyloom Global to integrate satellite-based quantum networking with terrestrial QPUs. Quantum Computing Inc. secured 1.5 billion dollars in funding to push neutral-atom and photonic architectures toward volume production.
The U.S. China Economic and Security Review Commission called for significant increases in federal quantum funding. Israel’s government-backed quantum programs showed signs of contraction. Infleqtion’s 1.8 billion dollar SPAC merger approached completion. The signal is clear. Quantum is entering a phase shaped by government strategy and long-term institutional capital, not speculative venture rounds.
Artificial Intelligence
AI remained the gravitational center of global capital. Cursor AI raised 2.3 billion dollars in a Series D round. Cohere secured 450 million dollars to expand enterprise AI capabilities. Thinking Machines entered funding discussions at a 50 billion dollar valuation. Hippocratic AI raised 126 million dollars at a 3.5 billion dollar valuation. Wonderful secured 100 million dollars for enterprise agents.
Saudi Arabia and the United States formalized a strategic AI partnership. SoftBank rotated capital into OpenAI. Metropolis raised 500 million dollars. Sakana AI raised 135 million dollars for Japanese LLMs. Early stage platforms such as Scribe, Sahara AI, Perle Labs, Avallon, uare.ai, and Freeda raised rounds across decentralized networks, security tooling, and industry automation.
AI has shifted into a capital maximalist phase where compute access, distribution control, and enterprise workflow penetration determine which platforms survive the next cycle.
Synthesis of Podcast Insights
This is what you missed in The CISO leadership brief sourced from top cybersecurity podcasts and webinars, if you haven’t upgraded your membership:
The Security Fundamental Every Fortune 100 CISO Admits Ignoring: A former cybercriminal turned consultant revealed the one vulnerability class behind almost every major breach. Your 40+ tool security stack can't fix it. Three CISOs built "inevitable security" frameworks that make this failure impossible. They haven't had an incident since. The framework requires dismantling everything you believe about security controls.
The Talent Metric That Predicts Breaches 6 Months Out: Security leaders track mean time to detect, mean time to respond, every possible metric except the one that matters. When this number hits a specific threshold, breaches become inevitable. One CISO's radical intervention cut this metric by 65% while improving performance. Your competitors are already recruiting from his playbook.
The External Force Taking Over Your Security Strategy in Q2 2026: They're already evaluating your security posture without your knowledge. They'll demand controls exceeding any compliance framework. Smart CISOs are turning this into board leverage for unprecedented budgets. The rest will discover the implications during their next incident. Three Fortune 100 security leaders share how they're preparing now.
Why Your Most Trusted Relationship Is Your Greatest Risk: Venture data reveals a shocking truth about your security vendor ecosystem that explains over half of enterprise breaches. The differentiation framework below shows how to evaluate 10,000+ vendors without missing critical indicators. Most CISOs discover this during post-incident analysis. You're about to learn it for $500K less.
And more insights in this week’s full CISO briefing.
Interesting Read
Palo Alto Networks Bets Big on Converged Cloud Security and Observability
Palo Alto Networks made a defining move this week by acquiring cloud-monitoring provider Chronosphere for $3.35B, signaling a shift in how security vendors view the modern threat surface. What looks like a traditional acquisition is actually a structural change: security, observability, and AI-driven detection are merging into a single category.
Chronosphere’s data-streaming and analytics capabilities will feed directly into Palo Alto’s Cortex AgentiX platform, allowing autonomous detection of both performance anomalies and security incidents. Palo Alto also raised its fiscal 2026 revenue guidance despite a short-term stock dip, highlighting how much confidence the company has in “observability as security” as the next multi-billion-dollar segment.
For security and engineering leaders, the message is clear: cloud monitoring is no longer a DevOps-only function. It is becoming part of the core security stack. CISOs who still treat observability, telemetry, and security analytics as separate budget lines will find themselves behind. The emerging competitive advantage lies in platforms that can ingest cloud-scale telemetry, correlate signals with threat behavior, and automate triage before humans ever enter the loop.
Organizations running fragmented toolchains such as APM tools on one side and SIEM or SOAR on another will feel pressure to consolidate. The future favors platforms that unify cloud performance data and security detection into one AI-driven workflow, reducing operational drag, integration debt, and alert fatigue.
→ Read more at Reuters
Fresh From the Field: Security Resources You Can Use
Title | Domain | Authors / Vendor | Key Insight (1 sentence) | Source Link |
|---|---|---|---|---|
#StopRansomware: Akira Ransomware – Updated Alert (Nov 13, 2025) | Cybersecurity, Ransomware | CISA, FBI | Documents Akira’s expanded targeting of enterprise virtualization stacks and provides updated detection and mitigation guidance. | |
Disrupting the First Reported AI-Orchestrated Cyber Espionage Campaign (Nov 17, 2025) | AI, Threat Intelligence | Anthropic | Reveals how a state actor used Claude Code to automate the majority of an espionage operation at near-human sophistication. | |
Microsoft Secure Future Initiative – November 2025 Progress Report | Cybersecurity, Cloud, Identity | Microsoft | Details Microsoft’s newest secure-by-default identity and cloud hardening requirements and their mapped implementation timeline. | |
Vying for Quantum Supremacy: U.S.–China Competition in Quantum Technologies (Nov 2025) | Quantum, Geopolitics | USCC | Analyzes the accelerating U.S.–China race in quantum hardware and applications and its implications for national security. | |
Cloud Security and Access Control (Nov 2025) | Cloud Security | IRJMETS | Surveys emerging access-control models shaping enterprise cloud security strategies for the next generation of workloads. |
OKX
San Jose, CA, US
El Paso County, Colorado, USA
Colorado Springs, CO, US
HARDESTY & HANOVER CONSTRUCTION SERVICES, LLC
New York, NY, US
Virtual Chief Information Officer
Endurance IT Services
Hampton Roads, Virginia Metropolitan Area, US
Dynamic Campus
Charleston, South Carolina Metropolitan Area, US
F5
Greater Seattle Area, US
Colorado Department of Revenue
Denver, CO, US
Inside Higher Ed
Boston, MA, US
RethinkFirst
Remote
Stay safe, stay secure.
The CybersecurityHQ Team

Reply