- Defend & Conquer
- Posts
- When defense became impossible: The 18-minute collapse of corporate security
When defense became impossible: The 18-minute collapse of corporate security
CybersecurityHQ - Free in-depth report

Welcome reader to a 🔍 free deep dive. No paywall, just insights.
Brought to you by:
👣 Smallstep – Secures Wi-Fi, VPNs, ZTNA, SaaS and APIs with hardware-bound credentials powered by ACME Device Attestation
📊 LockThreat – AI-powered GRC that replaces legacy tools and unifies compliance, risk, audit and vendor management in one platform
Forwarded this email? Join 70,000 weekly readers by signing up now.
#OpenToWork? Try our AI Resume Builder to boost your chances of getting hired!
—
CybersecurityHQ’s premium content is now available exclusively to CISOs at no cost. As a CISO, you get full access to all premium insights and analysis. Want in? Just reach out to me directly and I’ll get you set up.
—
Get one-year access to our deep dives, weekly Cyber Intel Podcast Report, premium content, AI Resume Builder, and more for just $299. Corporate plans are available too.
Ransomware is winning again, but not for the reasons security leaders expect. In 2025, attacks spiked to 24% of organizations, up from 18.6% in 2024, ending a three-year decline. The reversal is not about criminal innovation or defender complacency. It is about mathematics. Attackers have compressed the time between network breach and lateral movement from 48 minutes to 18 minutes. The average security operations center needs eight hours to contain an incident. Defenders now operate at a 26-to-1 time disadvantage, and the gap is widening.
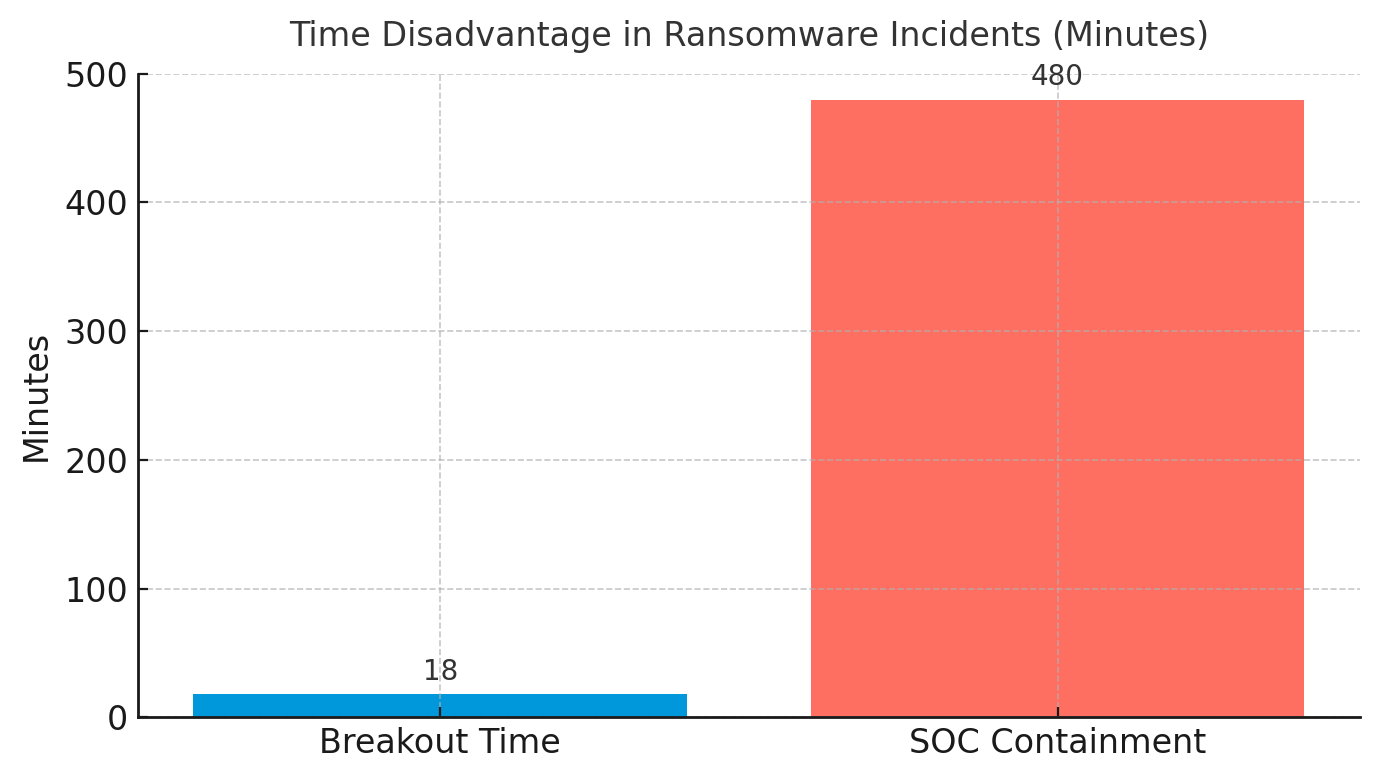
This velocity crisis renders traditional incident response obsolete. Consider Jaguar Land Rover in September 2025. Attackers halted production across global facilities, costing £50 million per week. The company required a £1.5 billion government loan guarantee to stabilize operations. The breach followed a now-familiar pattern: compromised credentials enabled network access, automated tools achieved lateral movement in minutes, and encryption deployed before human defenders could respond. When Unit 42 researchers simulated an AI-augmented attack, they moved from initial access to complete data exfiltration in 25 minutes, a 100-fold acceleration over traditional manual intrusions. By mid-2025, groups like Akira had reduced breakout time to six minutes.
The uncomfortable truth is that most organizations cannot defend against attacks that operate at machine speed. Human decision-making has become the rate-limiting factor in cybersecurity, and no amount of training or process improvement can close a 26-to-1 time gap.
The Economic Inversion That Changed Everything
Something unexpected happened in 2025: defenders started winning the economics war. Only 13% of ransomware victims paid ransoms, down from 16.3% in 2024. This decline represents the first meaningful shift in bargaining power since ransomware industrialized. Organizations achieved this through a straightforward insight: immutable backups are cheaper than ransom payments. The adoption rate reached 62% of enterprises, while 82% maintain tested disaster recovery plans. These investments fundamentally altered criminal economics.
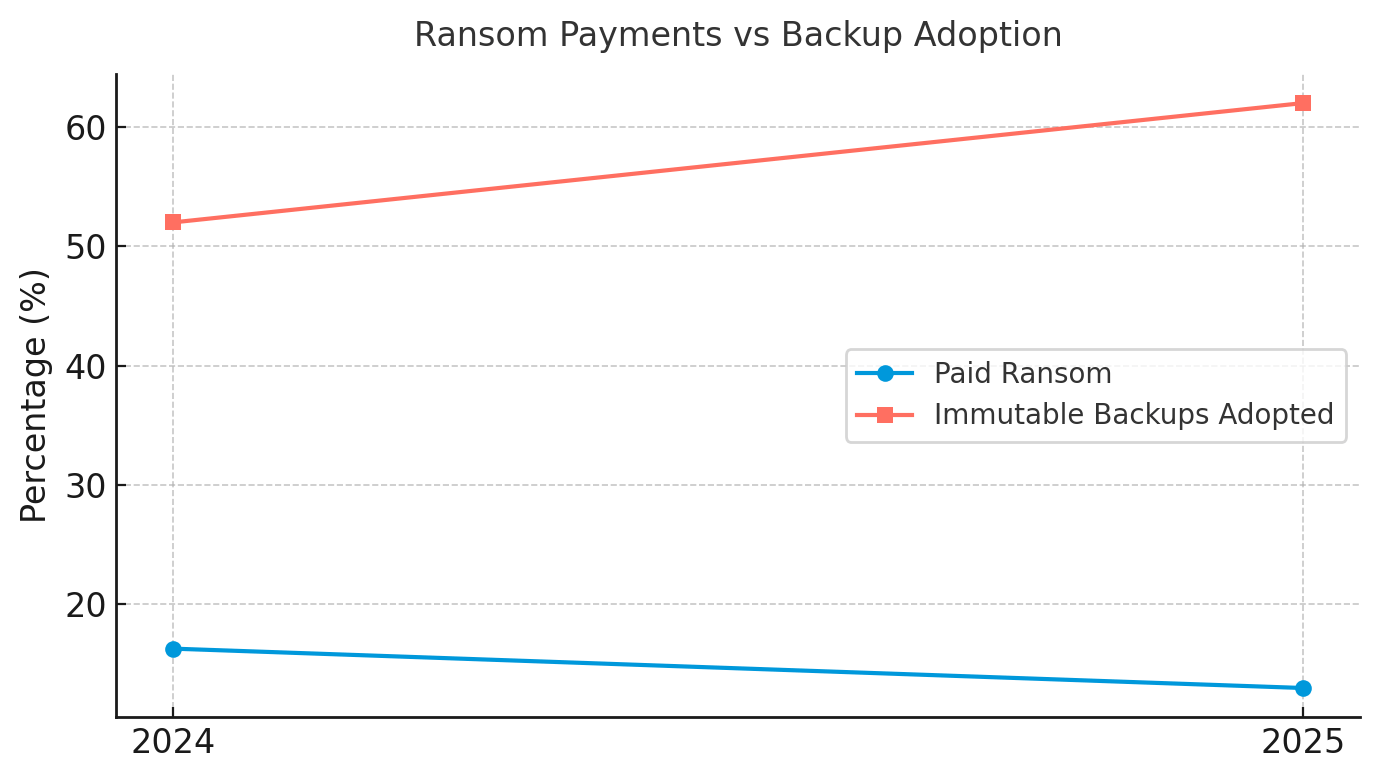
The math is compelling. A comprehensive immutable backup infrastructure costs approximately $500,000 to $2 million for mid-sized enterprises, depending on data volume and retention requirements. The average ransom demand in 2025 exceeded $1.5 million, with critical infrastructure targets facing demands in the tens of millions. Organizations performing this calculation recognized that one-time infrastructure investment delivers permanent protection against encryption-based extortion, while ransom payment provides temporary relief with high recurrence probability.
Criminals adapted predictably. They stopped treating encryption as the primary revenue source and pivoted to data theft. The so-called "double extortion" model is now simply extortion. Current data shows 93% of victims had data stolen regardless of whether ransomware encrypted anything. Attackers recognized that backup maturity made encryption unreliable as a revenue mechanism. Data theft creates regulatory exposure, reputational damage, and competitive intelligence loss that backups cannot solve.
Ransomware-as-a-Service platforms accelerated this evolution. Analysis of major RaaS operations shows over 50% now offer AI-driven capabilities to their affiliate networks. The LockBit group, before its disruption by international law enforcement in 2024, operated with corporate-style infrastructure including affiliate onboarding, technical support helpdesks, and performance metrics. When the group reconstituted in 2025, it incorporated AI-enhanced reconnaissance that could map network topologies without human intervention. The Qilin group demonstrated similar sophistication, accounting for 15% of global activity in Q2 2025 through exploitation of Fortinet vulnerabilities. These operations now demonstrate faster time-to-market for attack capabilities than most enterprise security vendors achieve with defensive updates.
This economic inversion has created a paradox. Organizations improved their ability to recover from encryption, so criminals stopped encrypting. The 24-day average downtime and 60% revenue loss figures now stem primarily from investigation, containment, and legal response rather than system restoration. The game shifted from business continuity to risk management, but most security programs still optimize for the wrong threat model.

The insurance market validates this shift. Cyber insurance adoption dropped to 46% as carriers increased premiums, tightened coverage, and excluded data theft from encryption-only policies. Insurers correctly identified that the risk profile changed: attackers now target regulatory penalties and reputational damage rather than operational disruption. Organizations paying for traditional ransomware coverage are insuring against last year's threat.
The Credential Economy Ate Network Security
Network perimeters no longer exist in any meaningful sense. Current data shows 79% of successful intrusions use valid credentials rather than malware. This statistic represents the security industry's most significant failure: defenders spent three decades building detection systems optimized for malicious code while attackers simply logged in using stolen passwords.
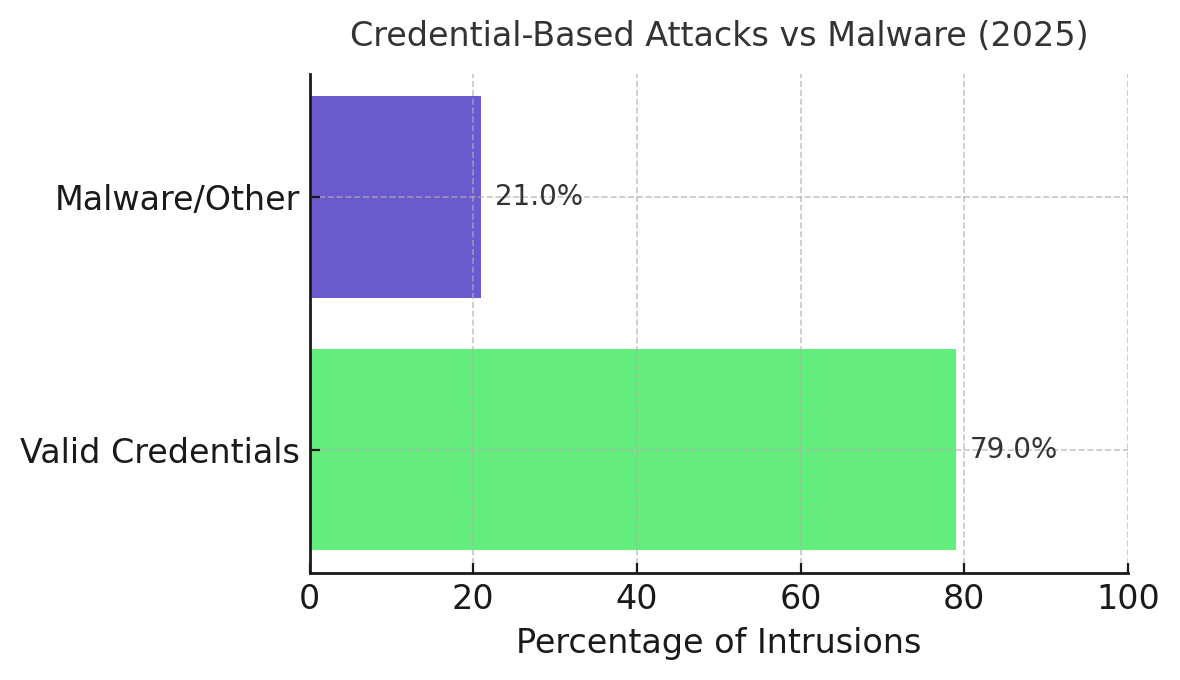
The credential theft supply chain operates with industrial efficiency. Information-stealing malware harvests credentials from browsers, password managers, and authentication apps. Access brokers verify and package these credentials for sale on marketplace platforms that process 50% more volume year-over-year. Domain administrator credentials for mid-sized enterprises sell for $3,000 to $5,000, a trivial investment against potential seven-figure ransoms.
The economics explain why phishing persists despite declining from 52.3% to 46% of incidents. AI-enhanced phishing achieves higher success rates with lower volume. When attackers can generate contextually perfect messages free from grammatical errors, detection becomes nearly impossible. The more troubling development involves deepfake voice and video. Vishing attacks using AI-generated voices spiked 442% in late 2024. The Muddled Libra group successfully used AI-generated video to convince helpdesk staff to reset passwords, demonstrating that voice verification has joined email links as an unreliable authentication method.
Organizations responded by deploying multi-factor authentication, but implementation quality undermines security benefits. Stolen credentials account for 25% of successful incidents despite widespread MFA adoption, revealing systematic failures in deployment. SMS-based MFA remains vulnerable to SIM swapping. App-based codes can be phished through social engineering. Only FIDO2 hardware tokens provide meaningful protection against credential theft and phishing attacks, yet adoption remains minimal due to cost and deployment complexity.
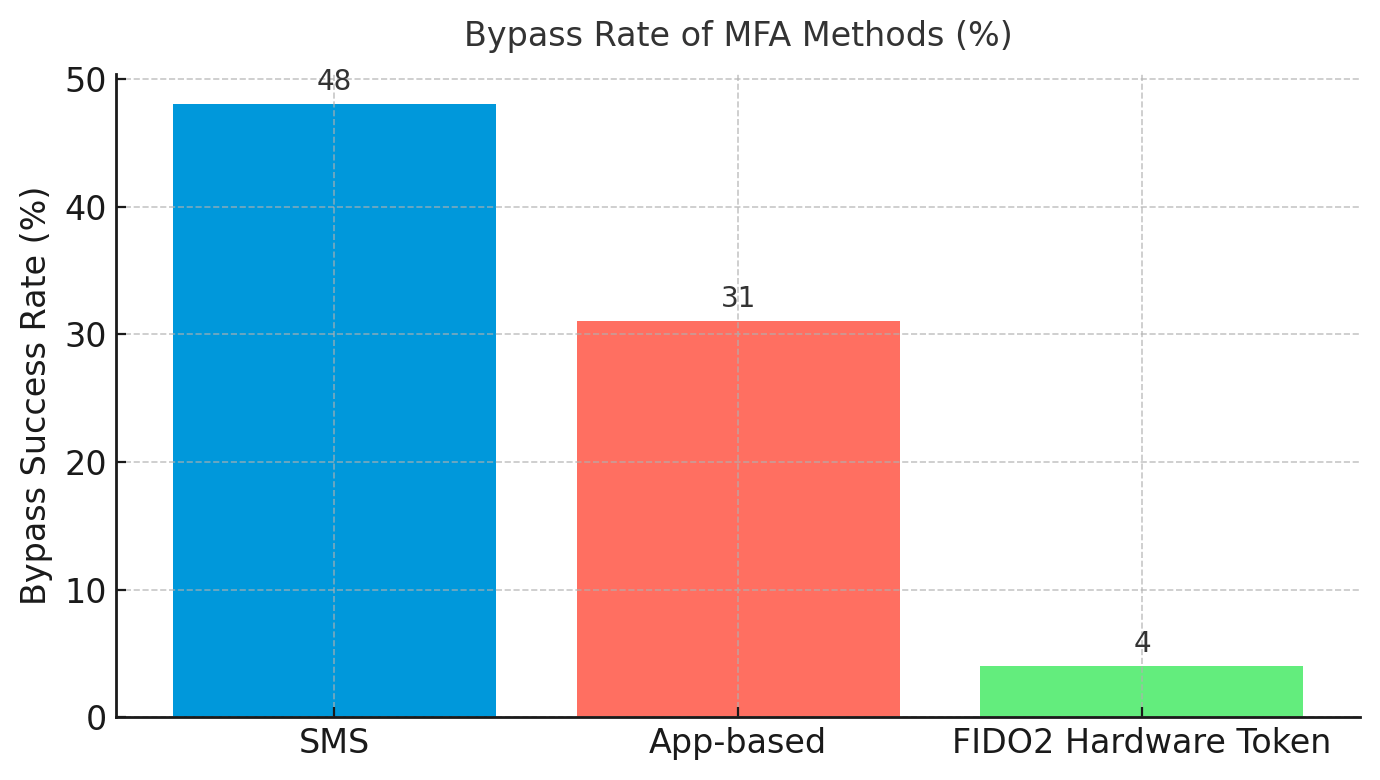
The uncomfortable reality is that identity has replaced the network as the primary attack surface, but most existing security architectures still assume network boundaries matter. This misalignment between threat reality and defensive posture explains why credential-based attacks succeed at such high rates.
The Cloud Multiplier Effect
Software-as-a-Service platforms have created a new vulnerability class that criminals systematically exploit. The PowerSchool breach demonstrated the multiplier effect. Attackers compromised one education technology provider and gained access to data from dozens of school districts, enabling parallel extortion campaigns that treated each district as a separate revenue opportunity. This "breach one, extort many" model fundamentally changes attack economics.
The pattern extends across sectors. In retail, Scattered Spider persisted for months before deploying ransomware on VMware ESXi hypervisors, effectively ransoming an entire private cloud infrastructure through a single encryption operation. The targeting of virtualization layers represents a brutal efficiency calculation: why encrypt thousands of individual machines when you can encrypt the hypervisor hosting all of them?
Cloud environments introduce specific vulnerabilities that signature-based detection cannot address. API abuse has emerged as the preferred exfiltration method. Once attackers obtain OAuth tokens or cloud credentials, they exfiltrate data through legitimate API channels that security tools are designed to trust. This traffic is indistinguishable from normal business operations. One documented breach involved hundreds of thousands of customer records exfiltrated through a misconfigured AWS S3 bucket that lacked basic access controls.
The SaaS security challenge is not technical. Organizations understand the risks. The problem is that cloud security requires behavior-based detection that establishes baselines and flags anomalies. Building these baselines requires months of telemetry collection. Organizations migrating to SaaS often skip this foundational work, leaving detection systems unable to distinguish normal from malicious activity. Attackers exploit this predictable gap during the migration window when security visibility is lowest.
What CISOs Get Wrong About Board Communication
The translation problem between CISOs and boards is not about jargon or technical complexity. It is about intellectual honesty. Most CISOs ask boards for security budgets without quantifying expected loss. This approach positions cybersecurity as a cost center rather than risk management, guaranteeing under-investment.
The correct framework requires three explicit calculations. First, what does downtime cost per hour across critical business processes? For most enterprises, the answer is measured in millions. A 24-day ransomware incident translates to specific revenue loss, productivity reduction, and customer attrition. Second, what is the organization's recovery time objective for each critical system, and is that objective validated through regular testing? The 40% backup failure rate during actual incidents reveals the gap between theoretical and actual recovery capability.
Third, what is the board's ransom payment risk appetite? Organizations avoid this discussion because it forces uncomfortable decisions. A no-payment policy requires significant investment in backup infrastructure and incident response automation. Payment flexibility as a last resort option requires different insurance coverage and crisis management capabilities. Most organizations maintain ambiguous policies that create decision paralysis during actual incidents.
The statistical evidence makes the investment case straightforward. Organizations that paid ransoms were targeted again at an 83% rate. Payment does not reduce future risk; it increases organizational visibility as a proven payer. The 93% data theft rate regardless of payment shows that encryption is no longer the primary threat. Organizations optimizing for business continuity are solving yesterday's problem.
The more provocative insight is that most security incidents reflect board-level failures, not technical shortcomings. When Jaguar Land Rover had no active cyber insurance despite operating critical manufacturing infrastructure, that represents a governance failure. When 40% of organizations discover their backups do not work during actual ransomware incidents, that represents inadequate testing oversight. When organizations deploy MFA but leave service accounts with domain administrator privileges unprotected, that represents failure to validate that security investments actually reduce risk.
CISOs should present one metric at every board meeting: expected loss exposure measured in dollars per day during a ransomware incident, multiplied by the organization's manual containment time. If that number exceeds the cost of automation investments, the decision is binary: invest or accept the expected loss.
The Automation Gap Is Actually a Decision-Making Gap
Organizations approach security automation as a capability problem. The real constraint is decision authority. Security operations centers detect anomalies in minutes, but human approval processes for containment actions introduce hours of delay. The average SOC analyst needs 30 minutes to triage an alert, validate it represents a genuine threat, and escalate to decision-makers. Meanwhile, attackers achieve lateral movement in 18 minutes.
The solution is not faster detection. Organizations already have the telemetry. The constraint is willingness to grant automated systems the authority to isolate compromised systems, rotate credentials, and block communications without human approval. This requires accepting that some automated actions will be false positives that disrupt business operations. Organizations prefer the certainty of breach over the uncertainty of false positive disruption, even when the expected cost of breach far exceeds the cost of occasional false positive incidents.
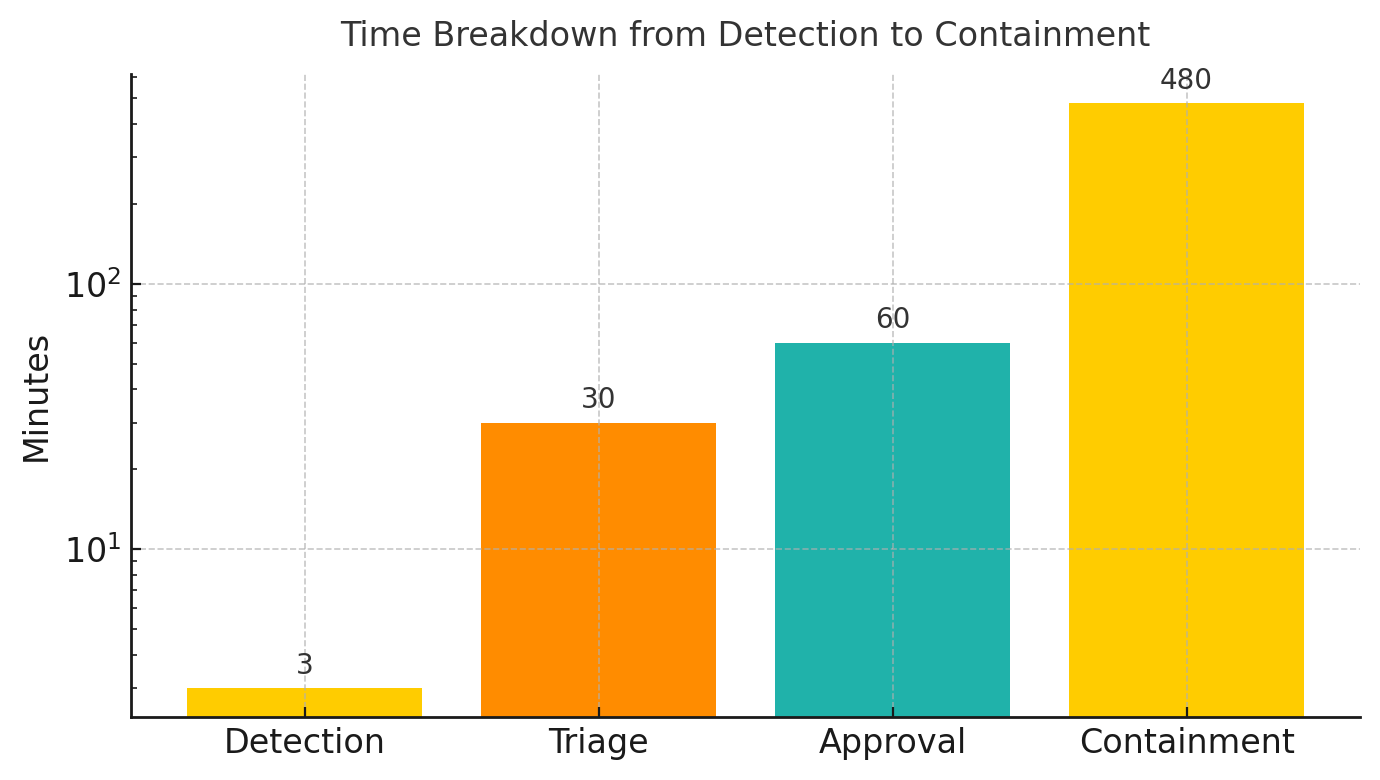
The organizations achieving sub-10-minute containment times through Security Orchestration, Automation, and Response platforms made a specific architectural decision: automated systems have authority to take containment actions based on predefined behavioral indicators. When a service account that normally accesses ten resources suddenly attempts to access hundreds, automated isolation triggers immediately. When API usage patterns suggest mass data exfiltration, automated blocking occurs without human approval.
This approach requires accepting operational risk in exchange for security risk reduction. Most organizations claim this tradeoff is unacceptable, but their actual behavior reveals a different calculation. They accept the operational risk of 24-day downtime during ransomware incidents rather than the operational risk of occasional false positive system isolation. The first risk is certain but delayed. The second is uncertain but immediate. Organizations consistently choose certain future pain over possible present disruption.
The Specific Tactical Failures That Matter
Security operations teams should monitor four behavioral indicators that predict ransomware with high confidence. First, service account activity outside established baselines. Most organizations grant service accounts excessive privileges and never audit actual usage patterns. When attackers compromise these accounts, they immediately exhibit anomalous behavior: accessing resources the account never touched, authenticating from unusual locations, or executing commands outside normal patterns.
Second, simultaneous authentication attempts across multiple systems in compressed timeframes. Human administrators authenticate serially, taking seconds or minutes between systems. Automated attack tools authenticate in parallel, generating login events across dozens of systems within seconds. This pattern is nearly impossible to achieve through legitimate activity.
Third, API usage spikes in SaaS environments, particularly bulk file operations or mass data access outside normal business hours. Legitimate users rarely interact with hundreds of files simultaneously. Attackers using API credentials for data exfiltration create usage patterns that differ fundamentally from human behavior.
Fourth, unusual SMB protocol activity from endpoints that do not normally serve files. Ransomware operators frequently use SMB to encrypt data on network shares remotely. An endpoint suddenly generating high-volume SMB traffic to multiple file servers creates a signature that detection systems should flag immediately.
Organizations that integrate these four indicators into automated containment policies can achieve sub-10-minute response times. The technical implementation is straightforward: identity platforms have APIs that enable automated credential rotation; network systems support automated host isolation; SIEM platforms can trigger these actions based on behavioral rules. The constraint is organizational willingness to grant automated systems this authority.
What Agentic AI Actually Means for CISOs
The current threat landscape involves AI-augmented attacks where human operators use automated tools for specific tasks. The next phase involves agentic AI: autonomous systems that independently set goals, make tactical decisions, and execute complete attack chains without human supervision. Industry analysts project 40% of enterprise applications will use task-specific AI agents by 2026. Criminal organizations will deploy comparable capabilities.
The operational difference is elimination of human latency. Current attacks require operators to analyze reconnaissance data, select targets, coordinate tool usage, and adapt to defensive responses. Each decision introduces delay. Autonomous agents eliminate these delays, operating at the speed of computation rather than human cognition. A single agent could orchestrate thousands of parallel intrusions, learn from each engagement, and share knowledge across the criminal ecosystem in real time.
This evolution creates an accountability crisis. When an AI agent executes an attack chain autonomously, attributing responsibility becomes complex. Criminal operators can credibly claim they provided general instructions rather than specific attack commands. Legal frameworks assume human decision-makers at each stage of an intrusion. Agentic systems challenge this assumption, potentially creating liability gaps that criminals will exploit.
The defensive response requires symmetry. Organizations must deploy defensive agents with equivalent autonomy: systems that can analyze threats, make containment decisions, and execute responses without human approval. This is not a technical challenge. The constraint is organizational willingness to cede decision authority to automated systems. Organizations that maintain human approval requirements will face agents that operate faster than human decision-making allows.
The geopolitical dimension compounds this challenge. Nation-state actors are already exploring agentic AI for offensive operations. The convergence of state-sponsored capabilities with financially motivated criminal operations suggests future attacks may combine zero-day exploits, sophisticated persistence mechanisms, and advanced evasion tactics with the scale and volume of criminal ransomware. The 500% increase in energy sector attacks during 2024-2025 demonstrates targeting patterns that blend financial and strategic objectives.
The Quantum Timeline Is Shorter Than Expected
Organizations treat post-quantum cryptography as a distant future concern. This is incorrect. The "harvest now, decrypt later" strategy creates immediate risk for any organization with data that retains sensitivity beyond five years. State-sponsored actors are actively collecting encrypted data with the expectation that quantum systems will enable retrospective decryption. Organizations holding intellectual property, trade secrets, or personal information with multi-decade sensitivity face current exposure.
The transition timeline is compressing. NIST published post-quantum cryptography standards in 2024. Organizations should complete crypto-agility assessments and begin migration planning immediately. The cryptographic inertia problem is severe: most organizations have encryption dependencies embedded in legacy systems, third-party integrations, and compliance frameworks that require years to modify. Organizations that wait for quantum computing maturity before beginning migration will discover they cannot complete the transition before current encryption becomes vulnerable.
The risk is not symmetric. Organizations with short-lived data can defer post-quantum migration. Organizations in financial services, healthcare, defense, and critical infrastructure sectors with long-lived sensitive data face immediate requirements. The uncomfortable reality is that data encrypted today using current standards may be decrypted within a decade, and potentially much sooner if quantum computing advances accelerate.
The Binary Choice
The ransomware resurgence of 2025 has exposed a fundamental architectural failure. Security programs optimized for prevention cannot succeed when attacks operate at machine speed using valid credentials. The 18-minute breakout time is not an outlier; it is the new baseline. Organizations face a binary choice: transform security architecture to match attack velocity through automation and resilience investments, or accept that breaches will result in operational disruption, financial loss, and regulatory exposure.
The data eliminates ambiguity. Organizations with immutable backups, automated response capabilities, and tested recovery procedures resist extortion successfully. Those relying on manual processes, signature-based detection, and prevention-focused strategies fail at known rates. The middle ground disappeared when attackers achieved 26-to-1 time advantage.
The business case is equally unambiguous. A single prevented incident justifies substantial automation investment. The cumulative risk of multiple annual attacks makes the investment case overwhelming. Boards that quantify downtime costs, establish explicit risk appetite, and fund appropriate capabilities position their organizations for survival. Those treating cybersecurity as operational IT expense rather than strategic risk management will continue appearing in breach notifications.
The uncomfortable conclusion is that most organizations already know what needs to change. The constraint is not knowledge or resources. It is willingness to make uncomfortable decisions: granting automated systems containment authority, accepting false positive disruption as preferable to breach certainty, and admitting that current security investments are optimized for threats that no longer exist.
The future belongs to organizations that recognize this reality. Those that cling to human-speed decision-making in a machine-speed threat environment will fail. Those that transform security from cost center to risk management function will survive. The 18-minute crisis eliminated the comfortable middle ground where organizations could claim adequate security through compliance checkbox exercises. The velocity gap forces a choice between transformation and failure. Organizations that delay this decision are simply choosing slowly what others chose quickly: acceptance of breach as inevitable outcome. The only remaining question is whether boards will acknowledge this reality before or after it appears in public breach disclosures.
Stay safe, stay secure.
The CybersecurityHQ Team

Reply