- Defend & Conquer
- Posts
- When ransomware hits the factory floor
When ransomware hits the factory floor
CybersecurityHQ - Free in-depth report
Welcome reader to a 🔍 free deep dive. No paywall, just insights.
Brought to you by:
👣 Smallstep – Secures Wi-Fi, VPNs, ZTNA, SaaS and APIs with hardware-bound credentials powered by ACME Device Attestation
🏄♀️ Upwind Security – Real-time cloud security that connects runtime to build-time to stop threats and boost DevSecOps productivity
📊 LockThreat – AI-powered GRC that replaces legacy tools and unifies compliance, risk, audit and vendor management in one platform
Forwarded this email? Join 70,000 weekly readers by signing up now.
#OpenToWork? Try our AI Resume Builder to boost your chances of getting hired!
—
CybersecurityHQ’s premium content is now available exclusively to CISOs at no cost. As a CISO, you get full access to all premium insights and analysis. Want in? Just reach out to me directly and I’ll get you set up.
—
Get one-year access to our deep dives, weekly Cyber Intel Podcast Report, premium content, AI Resume Builder, and more for just $299. Corporate plans are available too.
Colonial Pipeline paid $4.4 million in Bitcoin to ransomware attackers in May 2021. The decryption tool provided by DarkSide moved so slowly that Colonial's recovery depended entirely on internal backups and manual restoration efforts. By then, panic buying had emptied gas stations across the Eastern United States, which depends on Colonial for 45% of its fuel supply.
The attack never touched a single pipeline control system. Colonial executives shut down all operations preemptively because they lacked network segmentation between their billing systems and operational technology. Investigation later confirmed the attackers had compromised billing and business systems rather than industrial controls. The company proactively shut down OT systems to prevent spread, effectively stopping fuel distribution for nearly six days. Colonial Pipeline's lack of network segmentation between IT and OT made this all-or-nothing response necessary.
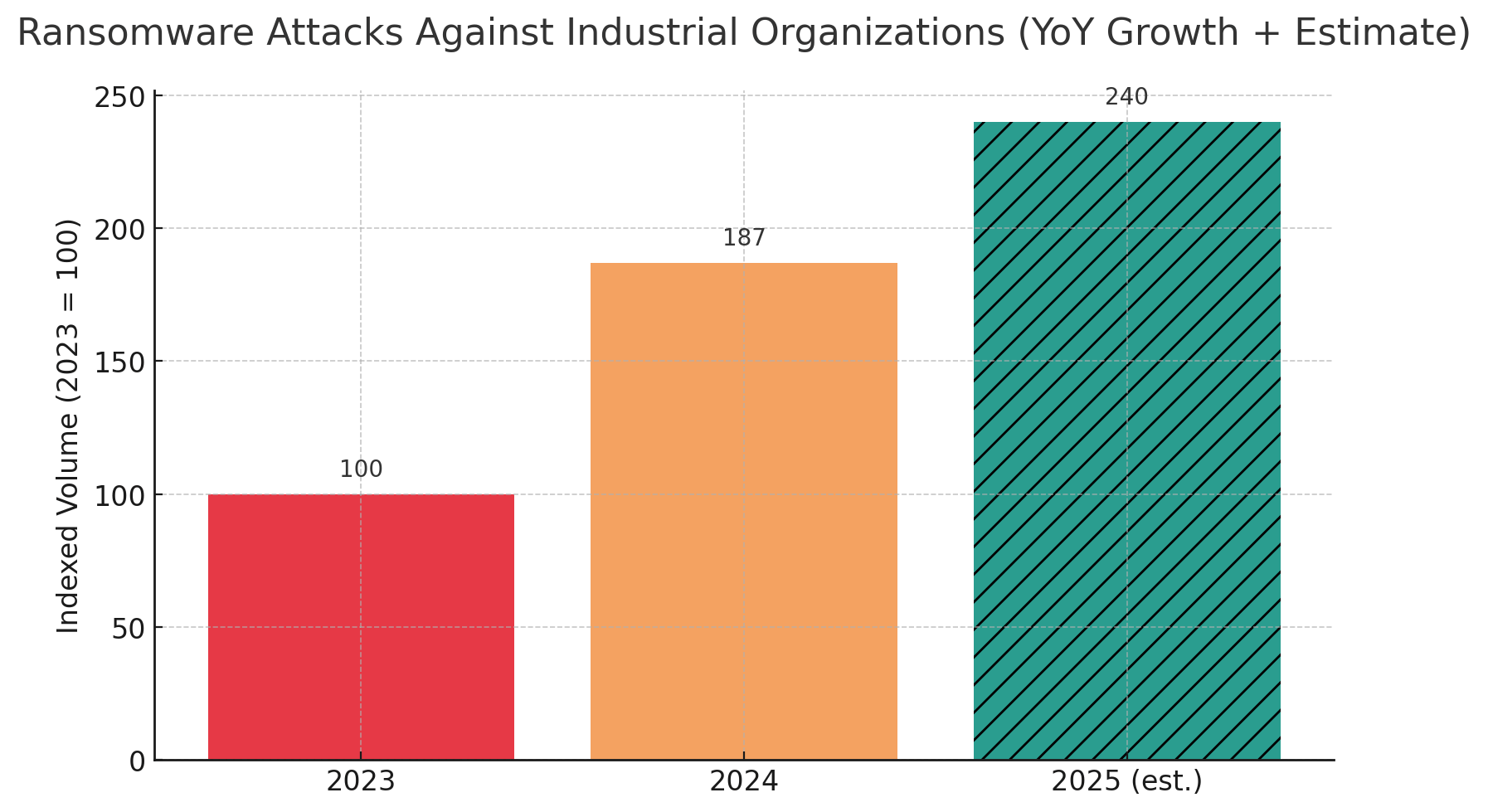
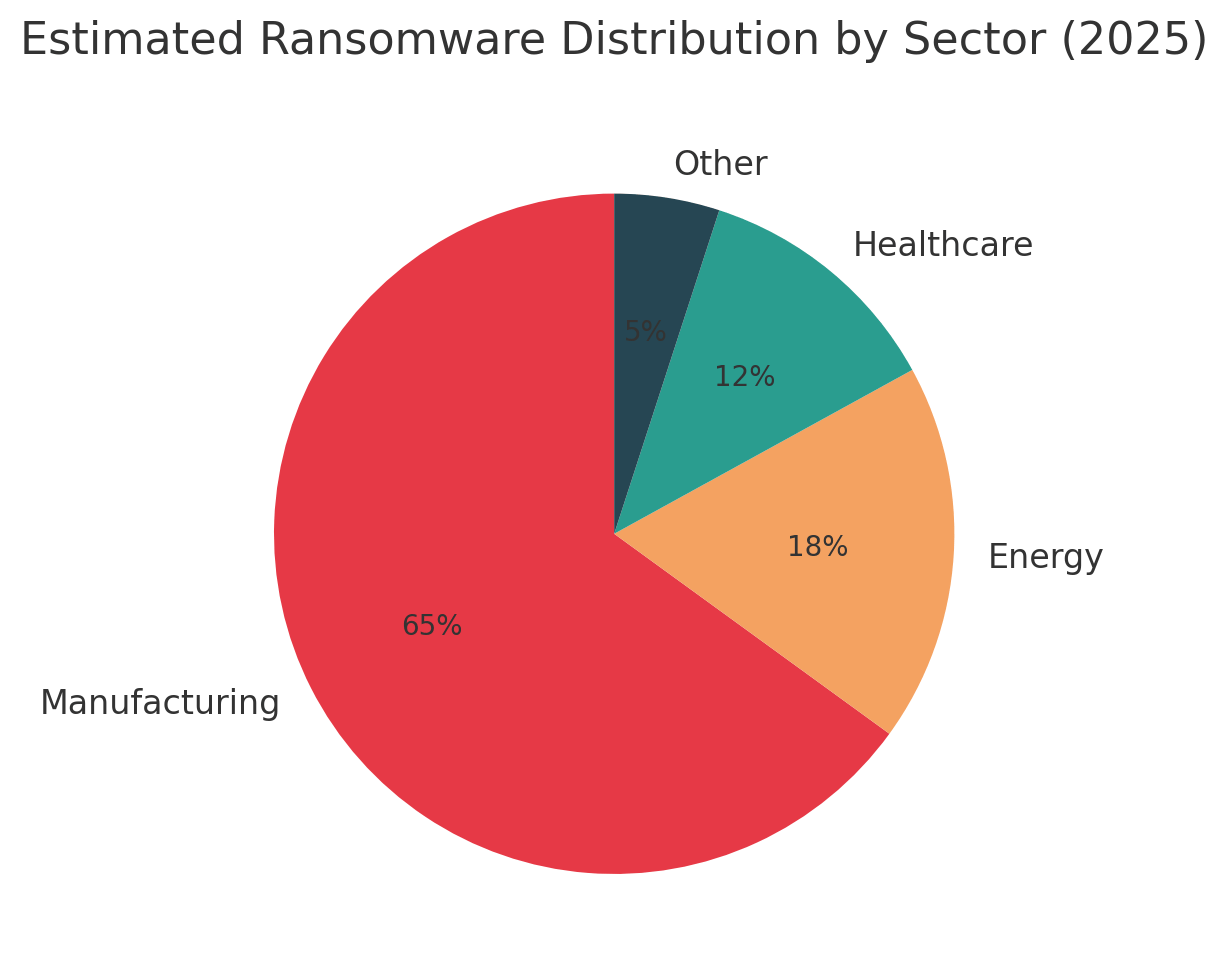
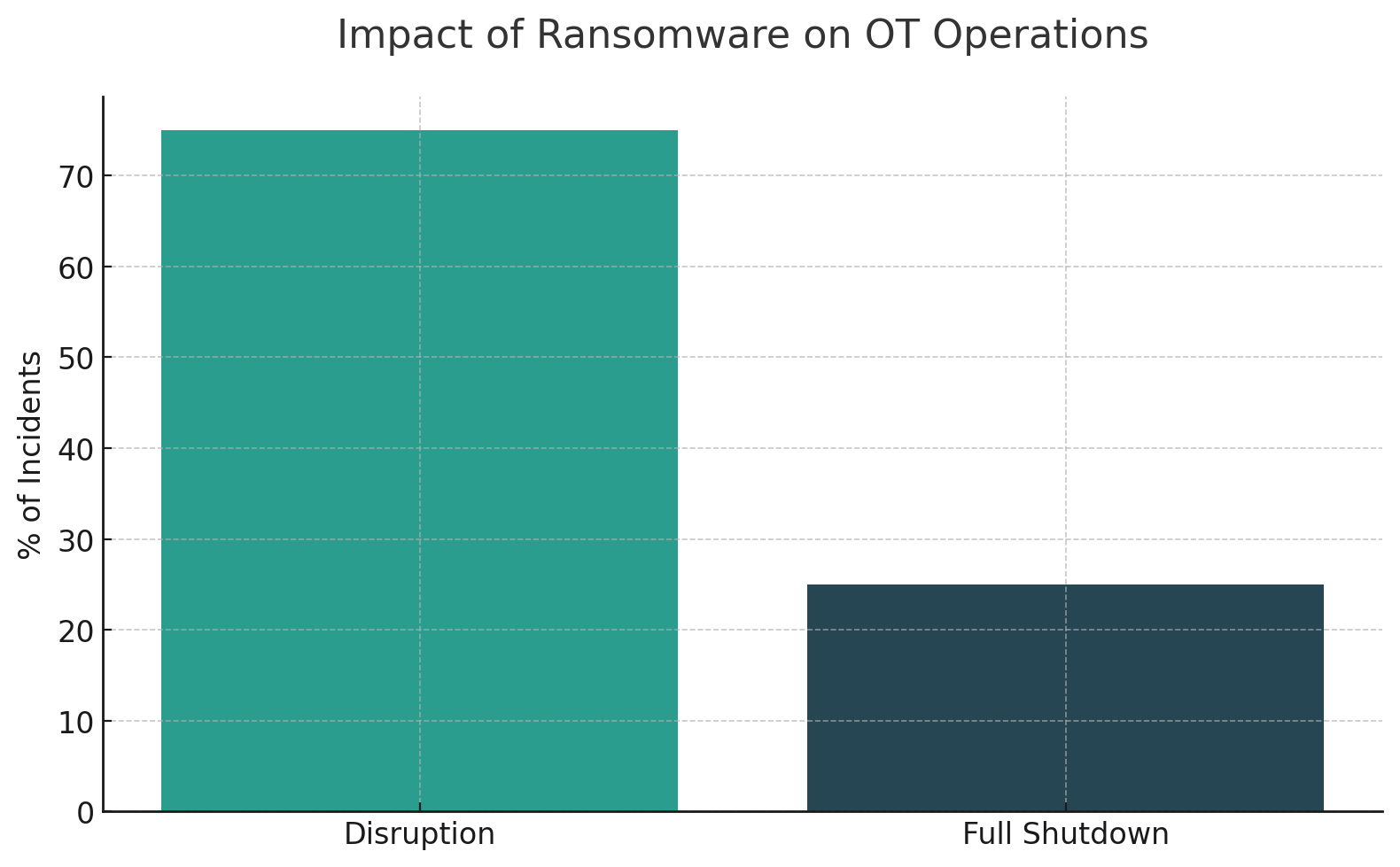
This pattern repeats across industries. According to Dragos incident data, ransomware attacks against industrial organizations surged 87% year-over-year in 2024, with manufacturing accounting for nearly 70% of recorded attacks. Over 80 ransomware groups were observed attacking an average of 34 industrial organizations per week in the first half of the year. Among ransomware incidents Dragos responded to in 2024, 75% caused disruption to OT operations and 25% resulted in full shutdown of an OT site.
The Convergence Problem
The numbers reveal a troubling reality. Sites experiencing physical operational impairment from cyber attacks rose 146% in 2024, climbing from 412 to 1,015 affected sites, according to tracking data. Ransomware groups targeted OT in 87% more industrial attacks year-over-year in 2024, making it the top sector for four consecutive years.
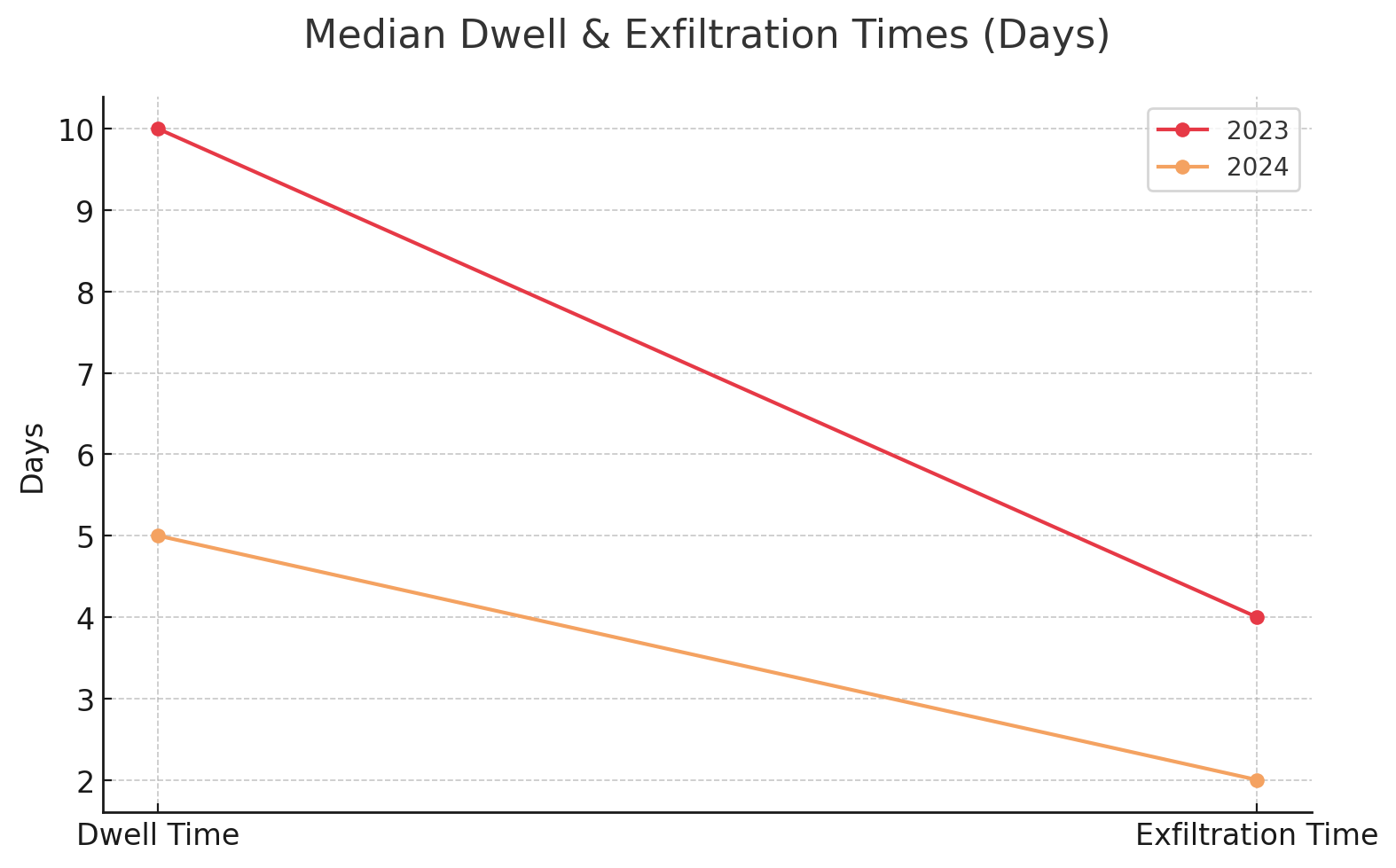
What distinguishes modern ransomware campaigns from earlier attacks is their deliberate exploitation of gaps between information technology, operational technology, and physical security domains. Dwell time—the period attackers remain undetected—has declined from 10 days to 5 days on average, signaling faster operations. Median exfiltration time in 2024 was about two days, with global medians at 26 days for external notifications and 10 days overall.
Consider what happened at JBS Foods in June 2021. The REvil ransomware group hit the world's largest meat processor's IT systems, forcing the shutdown of five major beef plants across the U.S. for three days. JBS paid an $11 million ransom to expedite recovery. Like Colonial, the incident started on IT systems but led the company to preemptively halt OT operations to contain the threat.
A.P. Møller-Maersk's experience with NotPetya in June 2017 demonstrates the scale of potential impact. The worm knocked Maersk's entire global IT infrastructure offline within hours, freezing port terminals and shipping logistics for days. Three out of four business segments were disrupted, forcing employees to revert to manual processes at ports worldwide. The financial cost reached $250-300 million in losses. Maersk had to rebuild thousands of servers and 45,000 PCs from scratch, a recovery made possible only by finding one surviving domain controller at a remote office.
What Works: Evidence from the Field
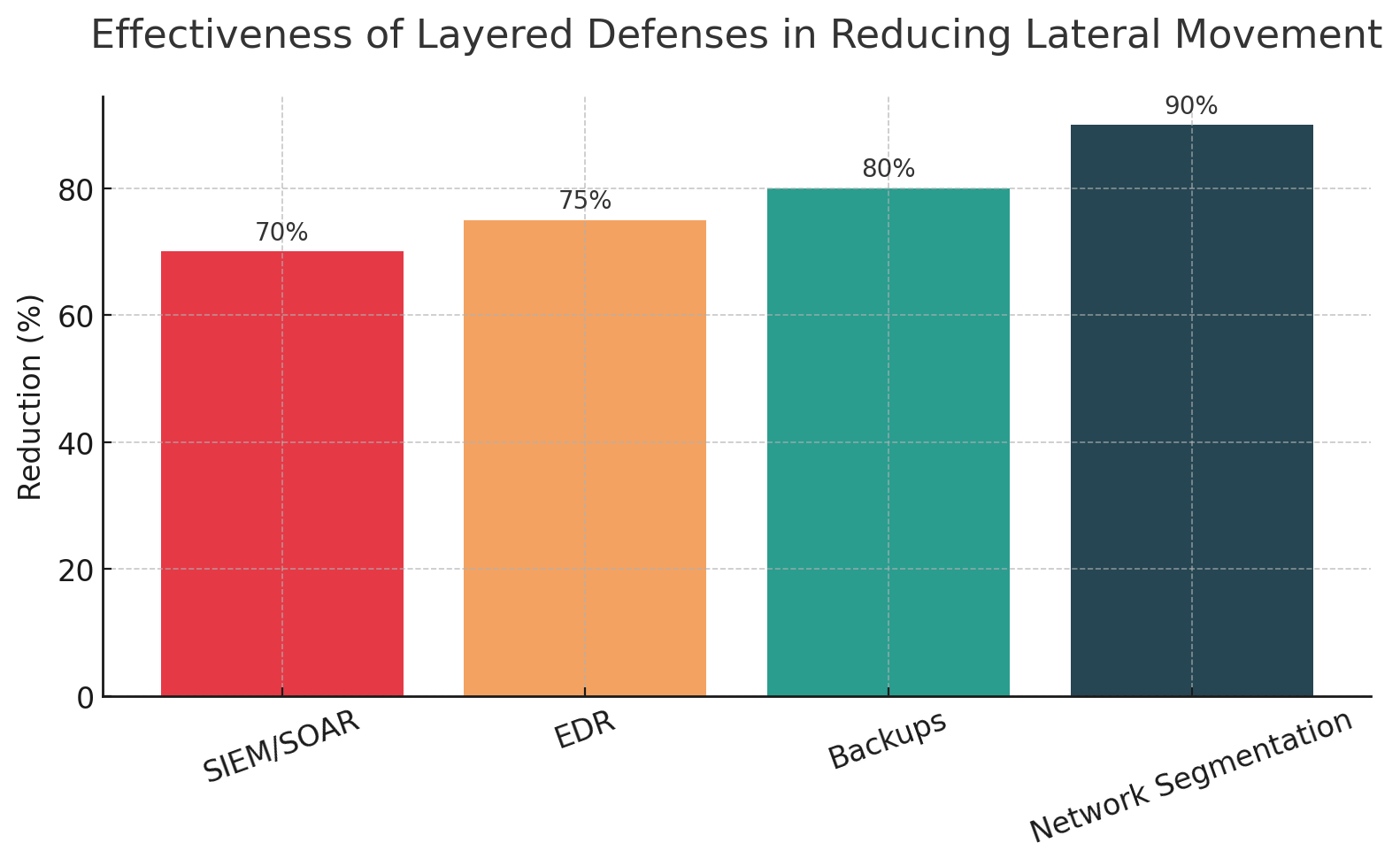
Research examining integrated response strategies across healthcare, critical infrastructure, and energy sectors reveals clear patterns. Studies found that layered defense measures—encompassing network segmentation, Endpoint Detection and Response, SIEM/SOAR, and robust backup systems—achieved reductions in lateral movement of 60% to 90% and mitigation rates exceeding 90%.
Organizations that successfully managed ransomware incidents shared specific characteristics. Those with incident command structures and multidisciplinary teams aligning IT, OT, and physical security efforts reported faster response times and reduced downtime. Simulation and tabletop exercises exposed procedural gaps and refined recovery protocols. Manual or analog workflows maintained critical operations when digital systems were compromised.
Norsk Hydro's response to LockerGoga ransomware in 2019 exemplifies effective preparation. When the attack hit, the aluminum manufacturer switched smelting plants to manual mode for weeks. Despite an estimated $70 million cost, the company refused to pay ransom and maintained transparency throughout recovery, earning praise for having pre-defined manual workarounds that preserved safety and trust.
In contrast, a 2020 ransomware incident at a German hospital in Düsseldorf knocked systems offline, indirectly leading to the rerouting of an emergency patient who later died—a tragic illustration of potential physical harm from cyberattacks.
The Regulatory Hammer
New regulations are forcing organizations to formalize integrated response capabilities. The EU's NIS2 Directive, which came into force in late 2024, broadens the scope of sectors and imposes stricter incident response duties on critical infrastructure operators. Companies must report significant incidents to their national CSIRT within 24 hours as an initial alert, followed by a detailed incident report within 72 hours, and a final report no later than one month.
NIS2 introduces potential fines up to €10 million or 2% of global turnover for non-compliance. Critically, NIS2 holds executives and board members personally liable for ensuring cybersecurity measures are in place. Organizations must vet the security of critical suppliers and have backup arrangements.
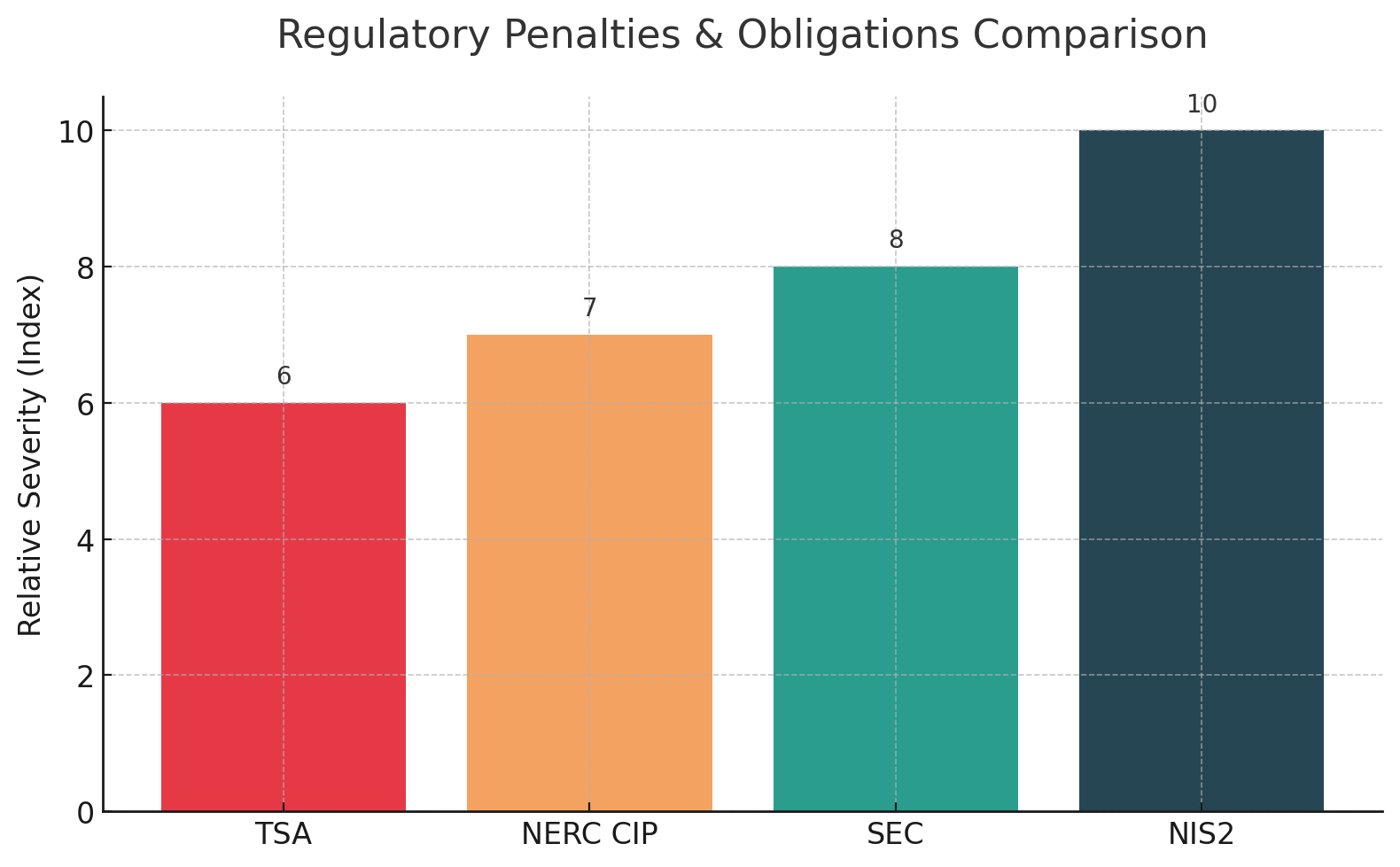
The U.S. Securities and Exchange Commission's 2023 cybersecurity disclosure rules require public companies to file an 8-K disclosure within 4 business days of determining a cyber incident is material. Companies must describe in their annual 10-K the board's oversight of cyber risks and management's governance practices. Except in rare national security cases, law enforcement can no longer ask companies to delay breach disclosure.
After the Colonial Pipeline incident, the Transportation Security Administration issued Security Directives for pipeline operators mandating network segmentation, continuous monitoring, and an up-to-date incident response plan tested yearly. Pipeline companies must report cybersecurity incidents to CISA within 24 hours.
In the energy sector, NERC CIP standards require electric utilities to maintain a Cyber Security Incident Response Plan (CIP-008) with annual drills and prompt incident reporting. CIP-008-6 obligates utilities to document how they identify, classify, respond to, and notify about incidents affecting the Bulk Electric System, often within 1 hour to the Electricity ISAC.
Building the Integrated Playbook
NIST's Cybersecurity Framework provides structure for integrated response, organized around five functions: Identify, Protect, Detect, Respond, Recover. NIST has published a Ransomware Risk Management Profile mapping CSF to ransomware scenarios. NIST SP 800-61 outlines the incident response life cycle, while NIST SP 800-82 provides guidance for industrial environments.
MITRE ATT&CK for ICS extends the framework to cover behaviors seen in industrial control system intrusions. It maps 12 tactics with techniques relevant to ransomware, such as Initial Access (12 techniques) for entry, Lateral Movement (7 techniques) for spreading to OT, and Impact (12 techniques) for shutdowns. This helps teams develop targeted detective and protective measures. For instance, knowing that "Data Encrypted for Impact" is a technique in the matrix, playbooks can include steps to check for abnormal file encryption on HMI or engineering workstations.
International standards provide additional structure. ISO/IEC 27035 is dedicated to incident management, outlining how to establish an incident response organization. IEC 62443 contains sections on incident response requirements for industrial operations, emphasizing defensible architecture, timely detection, managed response, and recovery testing.
The playbook structure follows these frameworks while addressing cross-domain coordination. During preparation, organizations must establish unified incident command structures bringing together IT security, OT engineering, and physical security under clear leadership. One critical element: pre-defined decision matrices specifying who can authorize OT network isolation and under what conditions to shut down production.
Detection in OT environments differs fundamentally from IT. While security operations centers generate automated alerts, OT incidents often surface as operator observations of unusual HMI behavior or unexpected equipment states. Many OT environments rely more on operator vigilance and anomalous process conditions than on security tools.
Containment requires careful orchestration. Network isolation typically serves as the primary measure to protect OT. But in OT environments, segment isolation can halt processes. SANS notes that containment often means isolating entire network segments or sites—not ideal but sometimes necessary. If control system integrity is in doubt, emergency shutdown procedures must follow safety protocols.
Eradication faces unique OT challenges. Legacy OT devices often run old operating systems or proprietary firmware where conventional antivirus won't run. Some PLCs might need firmware re-flash if compromised. For systems that cannot be quickly patched or cleaned, the playbook might incorporate "containment until decommission."
Recovery prioritizes systems based on business impact analysis. Colonial Pipeline's experience underscored the value of segmented networks and out-of-band manual controls. Maersk's recovery showcased the importance of offline backups and disaster recovery plans.
Measuring What Matters
Boards increasingly demand quantifiable evidence of incident response capability. Key metrics span preparation, response, and recovery phases.
Preparation metrics include percentage of critical systems with tested backups, training and drill frequency, and patch timeliness for critical vulnerabilities. Leading firms conduct combined-modality tabletop exercises including IT incident handlers, control room operators, and facility managers in the same scenario.
Response speed metrics track Mean Time to Detect (MTTD), Mean Time to Acknowledge (MTTA), Mean Time to Contain (MTTC), and critically for OT, Mean Time to Recover (MTTR). Reducing mean time to recovery is cited as the most important metric for OT incident response and recovery efforts by industry experts.
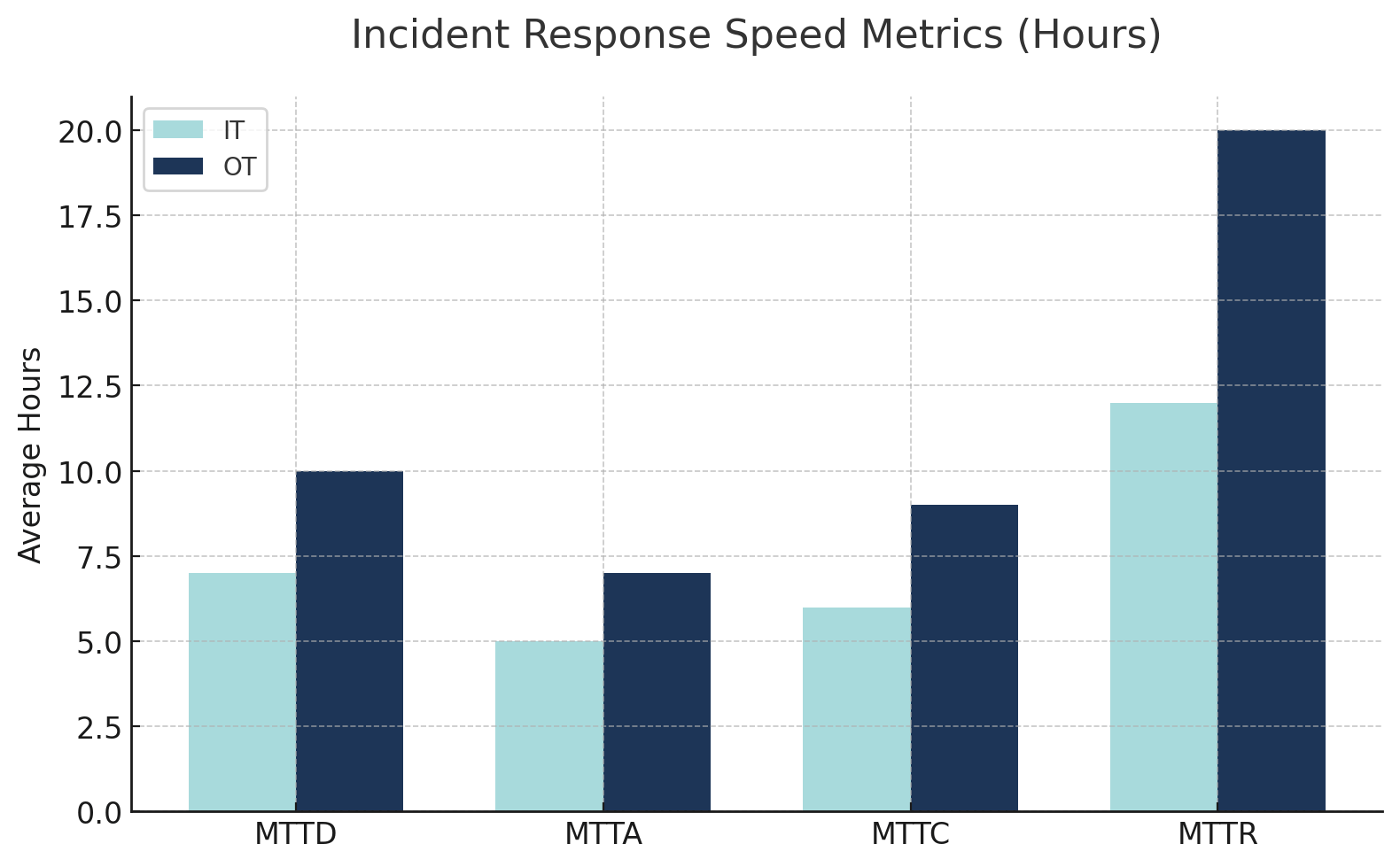
Post-incident metrics capture total downtime, data loss, incident costs, and time to root cause remediation. Compliance metrics track whether regulatory notifications were made on time. The lessons learned process should produce a formal report identifying gaps and tracking improvement actions to closure.
The Threat Evolution
The ransomware landscape shows marked sophistication increases. Using MITRE ATT&CK categorization, attackers exploit techniques like abusing default credentials or remote services to pivot from IT to OT networks. Common tactics include initial access via phishing, privilege escalation, and discovery of OT assets, followed by impairing process controls to cause shutdowns.
Ransomware variants spread via exposed remote access tools or unpatched systems, targeting ICS to disrupt operations. State-sponsored and hacktivist groups amplified manufacturing attacks by 71% in 2024. Some hacktivist groups even combined ransomware with disruptive ICS attacks—a concerning convergence of tactics.
Adversaries specifically favor victims with low downtime tolerance to amplify pressure to pay ransoms. Manufacturing incidents rose from 424 in Q4 2024 to 480 in Q1 2025. In the U.S., infrastructure attacks increased 9% in 2024, with over 1,300 complaints.
Future Considerations
Organizations are moving toward integrated Cyber Fusion Centers housing threat intelligence, security operations, and incident response for both enterprise and industrial environments under one roof. This helps break down silos by design.
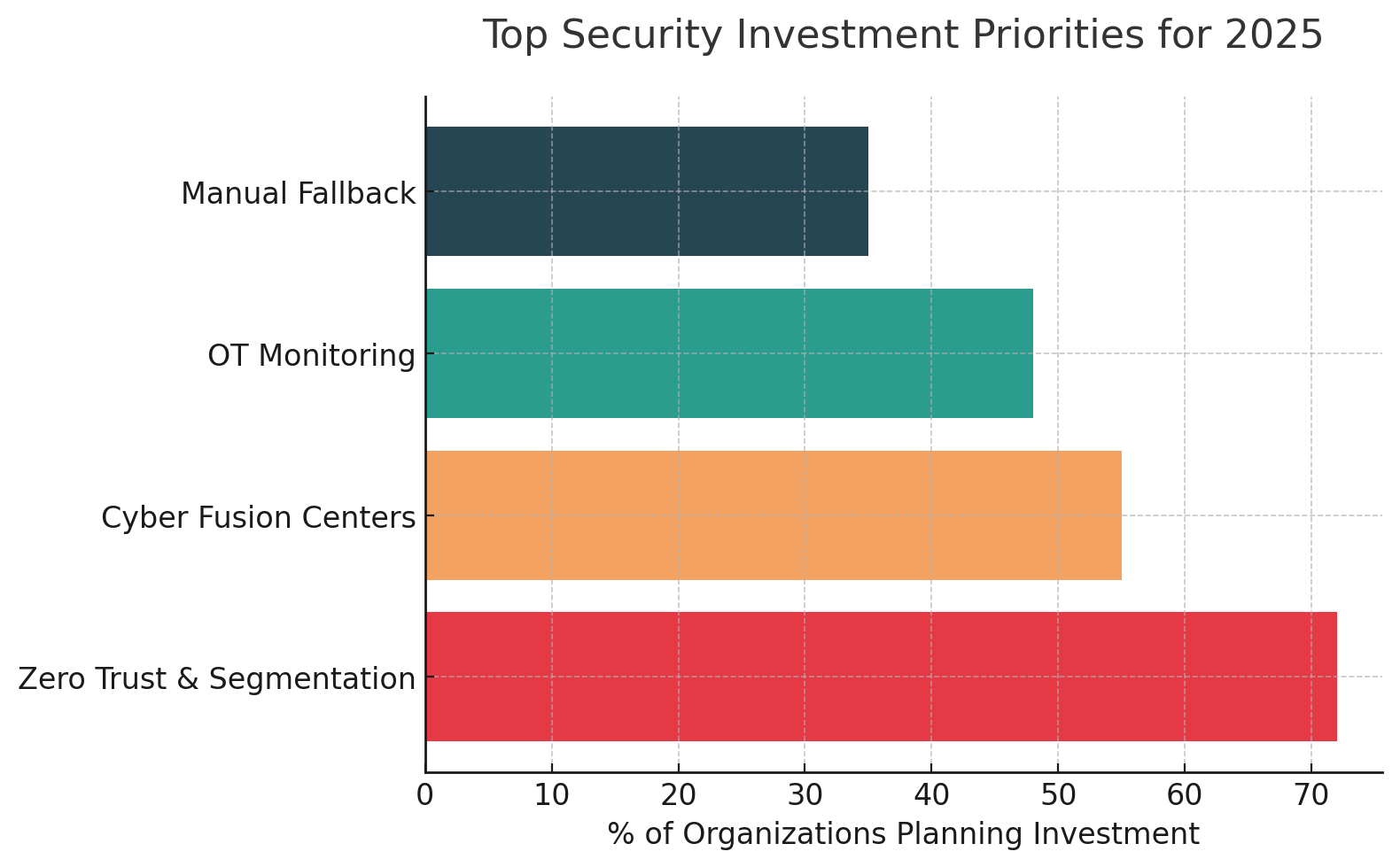
Zero Trust architectures paired with sector-specific playbooks enhance system isolation and limit unauthorized access. However, implementation in OT environments faces challenges with legacy system compatibility and the complexity of industrial networks designed for availability over security.
The playbook should evolve to address emerging threats while maintaining focus on fundamentals. As one expert noted, identifying and eliminating root cause is vital to prevent re-infection. Whether it's a vulnerability, misconfiguration, or stolen credential, the underlying issue must be addressed.
Regular cross-functional meetings and drills build trust between teams. By rehearsing scenarios, organizations uncover and fix coordination problems in advance—like when and how the IT SOC should contact a plant's emergency response team, or how physical security might assist by securing server rooms or escorting forensic personnel on site.
The Integration Imperative
The evidence from real incidents demonstrates that siloed responses fail when ransomware crosses domains. Colonial Pipeline's shutdown wasn't caused by OT compromise but by the inability to assess cross-domain risk. JBS Foods paid millions because they lacked confidence in their containment capabilities. Maersk lost hundreds of millions due to insufficient segmentation and backup strategies.
In contrast, organizations with integrated playbooks, tested procedures, and cross-domain coordination achieve better outcomes. Research shows that layered defense with proper segmentation reduces lateral movement by 60% to 90%. Incident command structures aligning IT, OT, and physical teams deliver faster response and reduced downtime. Manual operation capabilities maintain critical functions during digital outages.
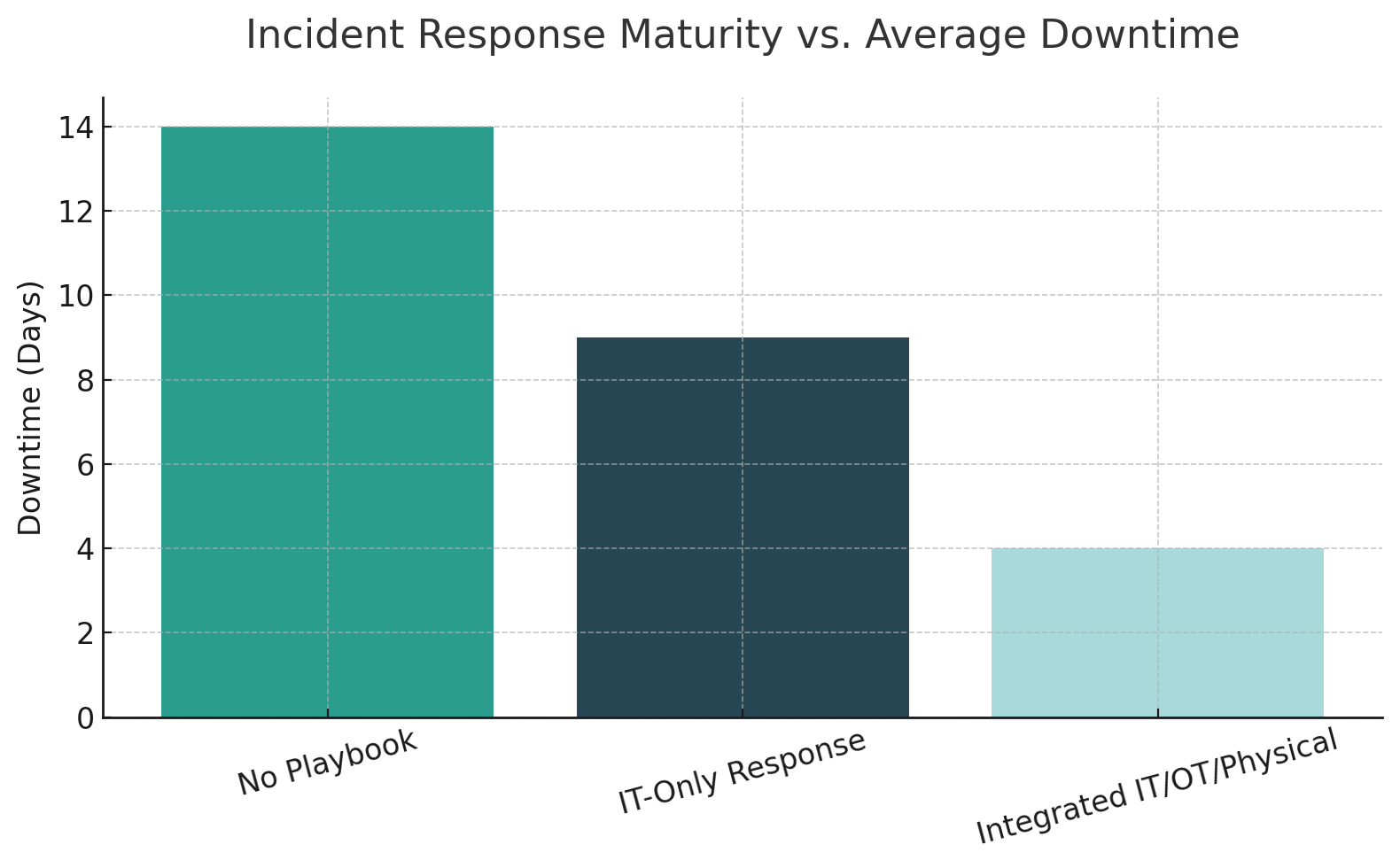
The regulatory environment reinforces this integration imperative. NIS2's personal liability provisions, SEC's materiality disclosure requirements, and sector-specific mandates all assume organizations can rapidly assess and respond to incidents spanning multiple domains. Boards expect CISOs to demonstrate that the company can detect, respond to, and recover from ransomware with minimal damage.
Building effective integrated response takes time and cultural change. It requires IT security staff who understand control systems and OT engineers open to learning cyber threats. It demands creating translation glossaries so everyone knows what "HMI server" or "PLC" means. Most importantly, it requires centering everyone's focus on shared goals: safety and business continuity.
The question facing CISOs is not whether to integrate IT, OT, and physical security response, but how quickly to achieve it. With ransomware attacks against industrial organizations up 87% year-over-year and 25% resulting in full site shutdowns, delay increases risk. Every organization running industrial processes without integrated defenses gambles with operational continuity, regulatory compliance, and ultimately, public safety.
Stay safe, stay secure.
The CybersecurityHQ Team

Reply