- Defend & Conquer
- Posts
- When trust fails: The collapse of security verification across hardware, software, and identity layers
When trust fails: The collapse of security verification across hardware, software, and identity layers
CybersecurityHQ - Free in-depth report

Welcome reader to a 🔍 free deep dive. No paywall, just insights.
Brought to you by:
👣 Smallstep – Secures Wi-Fi, VPNs, ZTNA, SaaS and APIs with hardware-bound credentials powered by ACME Device Attestation
📊 LockThreat – AI-powered GRC that replaces legacy tools and unifies compliance, risk, audit and vendor management in one platform
Forwarded this email? Join 70,000 weekly readers by signing up now.
#OpenToWork? Try our AI Resume Builder to boost your chances of getting hired!
—
CybersecurityHQ’s premium content is now available exclusively to CISOs at no cost. As a CISO, you get full access to all premium insights and analysis. Want in? Just reach out to me directly and I’ll get you set up.
—
Get one-year access to our deep dives, weekly Cyber Intel Podcast Report, premium content, AI Resume Builder, and more for just $299. Corporate plans are available too.
The last week of October 2025 should have been routine. Security teams had patched systems. Multi-factor authentication was enabled. Cloud providers promised 99.99% uptime. Hardware enclaves were certified secure.
Then everything broke at once.
A $1,000 device cracked Intel and AMD's most fortified hardware enclaves¹. Attackers weaponized Microsoft's patch delivery system within hours of an emergency fix². A 183 million credential dump exposed the limits of authentication safeguards³. Microsoft Azure and Amazon Web Services suffered outages within the same week⁴. Major security vendors quietly announced layoffs that would hollow out their support teams⁵.
These were not random failures. They revealed a systemic flaw in how organizations verify security. Every layer of trust—from silicon to software to identity—rests on the assumption that systems can reliably assert their own integrity. That assumption is now demonstrably false.
CISOs face a stark reality: verification itself has become the vulnerability.
The Hardware Illusion
For years, the security industry treated hardware isolation as an unbreakable foundation. Trusted Execution Environments promised cryptographically sealed computing. Intel's Software Guard Extensions and AMD's Secure Encrypted Virtualization represented billions of dollars in engineering. Cloud providers built entire confidential computing platforms on these guarantees.
On October 28, 2025, researchers disclosed TEE.Fail¹. The attack bypassed every defense.
The exploit targeted DDR5 memory, not the CPU. By placing an interposer device between the processor and memory controller, attackers could observe nanosecond timing variations in memory access patterns. These tiny fluctuations leaked cryptographic keys from supposedly isolated enclaves. Researchers report they could, in some cases, extract attestation keys—the credentials designed to prove an enclave's integrity⁶.
The attack cost under $1,000 to execute. It worked on fully patched systems from Intel, AMD, and NVIDIA. It required no software vulnerabilities. Physical access to the memory bus was sufficient⁷.
The implications extend far beyond academic research. Confidential computing powers some of the most sensitive workloads in enterprise infrastructure: financial transactions, healthcare records, AI model training. Organizations had migrated these workloads specifically because hardware isolation promised protection that software alone could not provide.
That protection was illusory. The hardware could not verify its own isolation when the attack vector existed outside the boundaries it was designed to police.
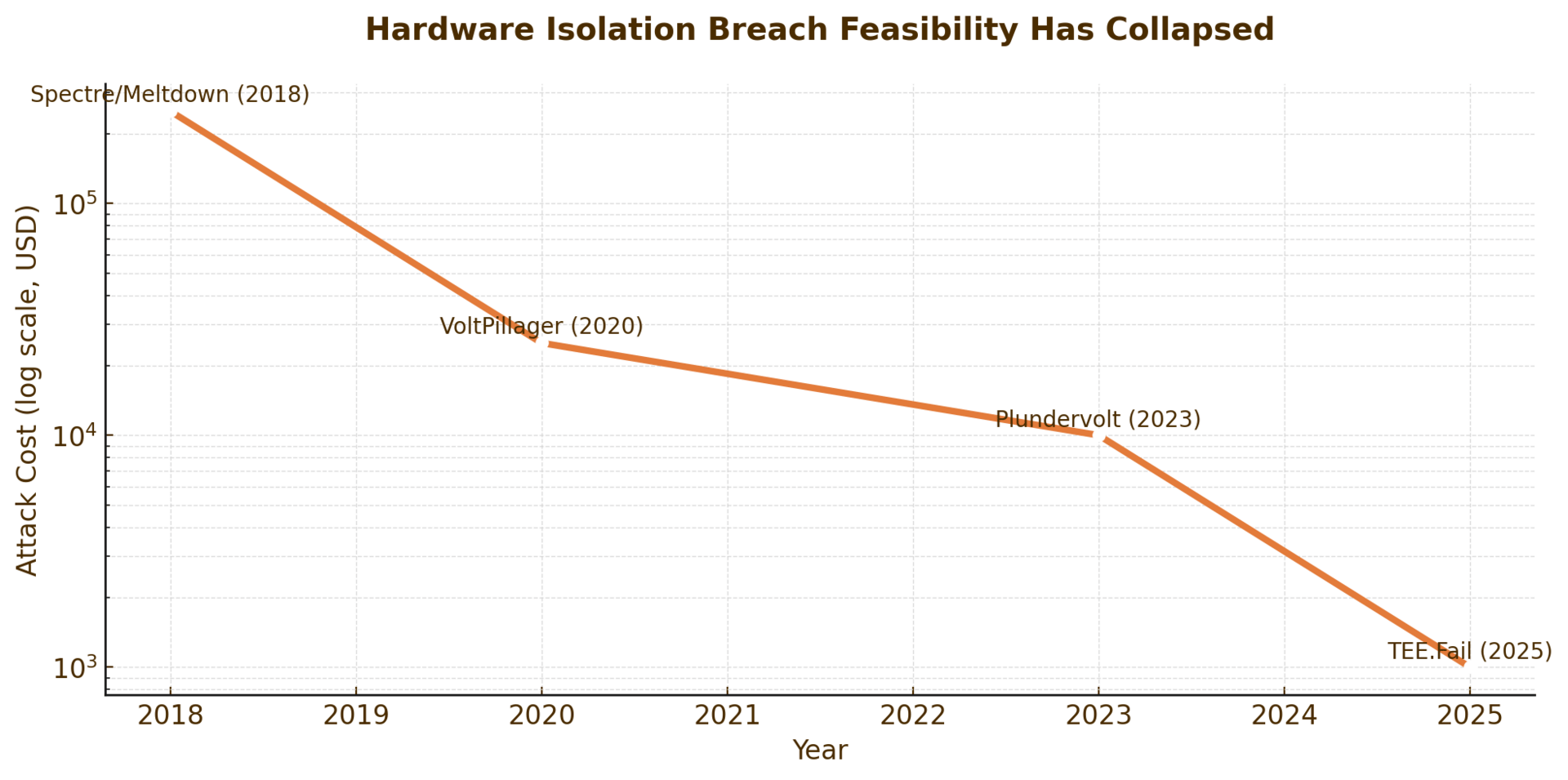
Intel and AMD both acknowledged the findings but classified the vulnerability as outside their threat model⁸. Physical attacks involving bus interposition, they argued, were the responsibility of data center operators. Intel reiterated that such physical interposer attacks fall outside the scope of their security guarantees⁹. This response misses the point. The flaw is architectural. When hardware attestation depends on the integrity of components that can be externally monitored, self-verification becomes circular. The chip cannot detect what it cannot see.
Board Takeaway
Hardware security cannot be assumed from vendor certifications alone. Organizations running confidential computing workloads must implement independent attestation services and physical security controls for critical infrastructure. Budget for third-party validation of hardware isolation claims.
The Patch Paradox
Software updates are supposed to close vulnerabilities. On October 23, 2025, Microsoft released an emergency patch for a critical Windows Server Update Services flaw¹⁰. The vulnerability, CVE-2025-59287, carried a CVSS score of 9.8—near maximum severity. It allowed remote code execution on update servers without authentication.
Within hours, attackers had reverse-engineered the patch and weaponized the exploit¹¹.
CISA added CVE-2025-59287 to its Known Exploited Vulnerabilities catalog on October 24, immediately following the emergency patch release¹². The speed was unprecedented. The agency's alert warned of active exploitation and urged immediate remediation¹³.
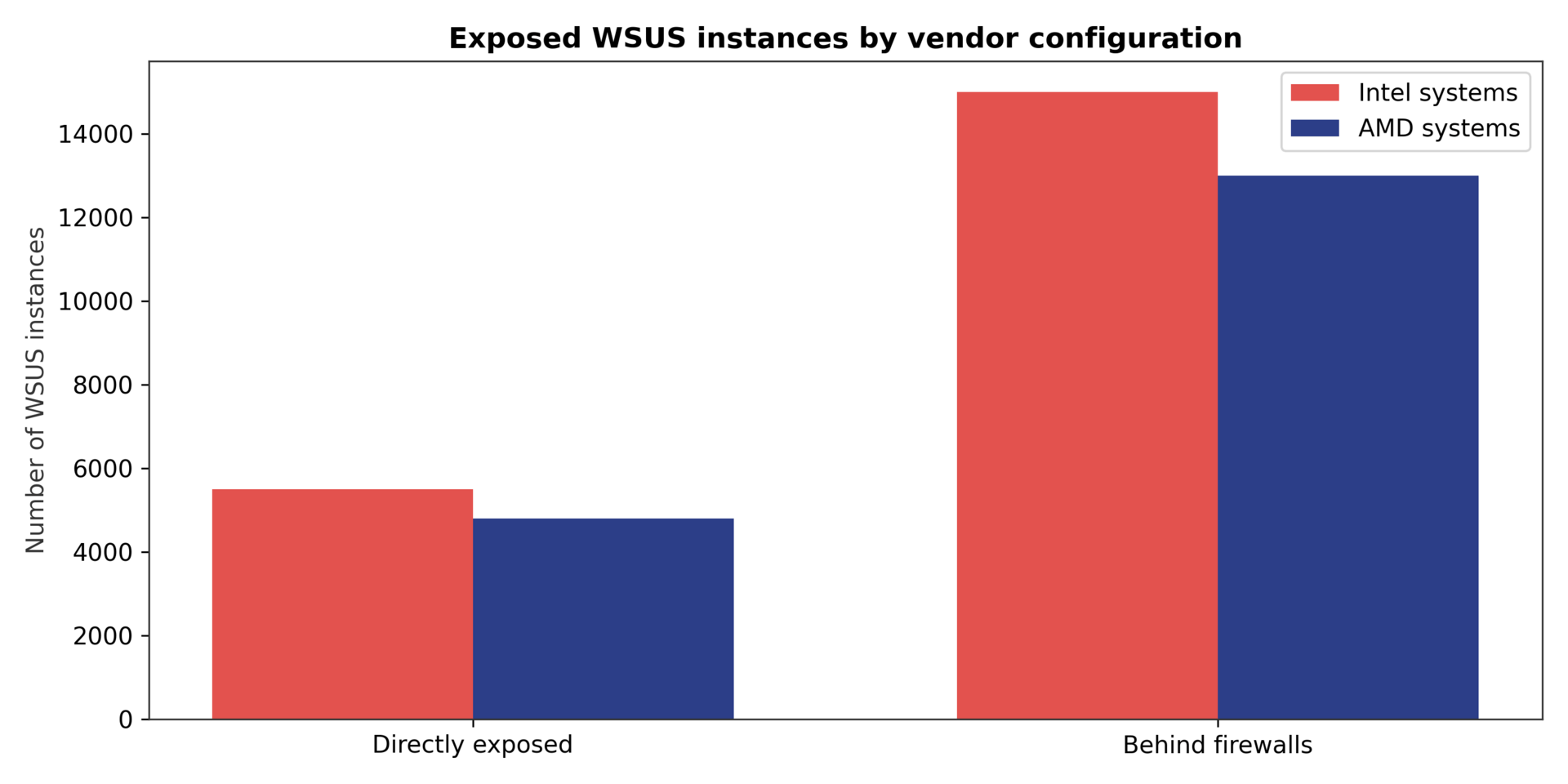
The attack surface was significant. Unit 42 researchers identified approximately 5,500 WSUS instances exposed directly to the internet¹⁴. Many more existed behind corporate firewalls. The exploit leveraged an insecure deserialization flaw in the update service's web interface. Attackers sent crafted POST requests that spawned PowerShell sessions with SYSTEM privileges¹⁵.
The initial payloads focused on reconnaissance. Commands like whoami, net user /domain, and ipconfig /all mapped domain structures and identified high-value accounts¹⁶. Follow-on attacks deployed the Skuld infostealer, exfiltrating credentials and session tokens to remote webhooks¹⁷.
Multiple organizations were observed compromised in the initial wave of attacks¹⁸. The actual number remains difficult to quantify. Many organizations lack visibility into the behavior of their update infrastructure. WSUS servers, ironically, are often exempt from intensive monitoring because they are assumed to be trustworthy distribution points.
The WSUS incident exemplifies a broader problem: patches close known vulnerabilities but introduce new attack vectors in the remediation process itself. The update pipeline—code signing, distribution servers, client verification—creates multiple points where trust can fail. Organizations verify that patches are applied. They rarely verify that the application process remains uncompromised.
Microsoft's initial patch was incomplete. A second update followed days later¹⁹. By then, the damage was done. The vulnerability demonstrated that "patched" and "secure" are not synonyms.
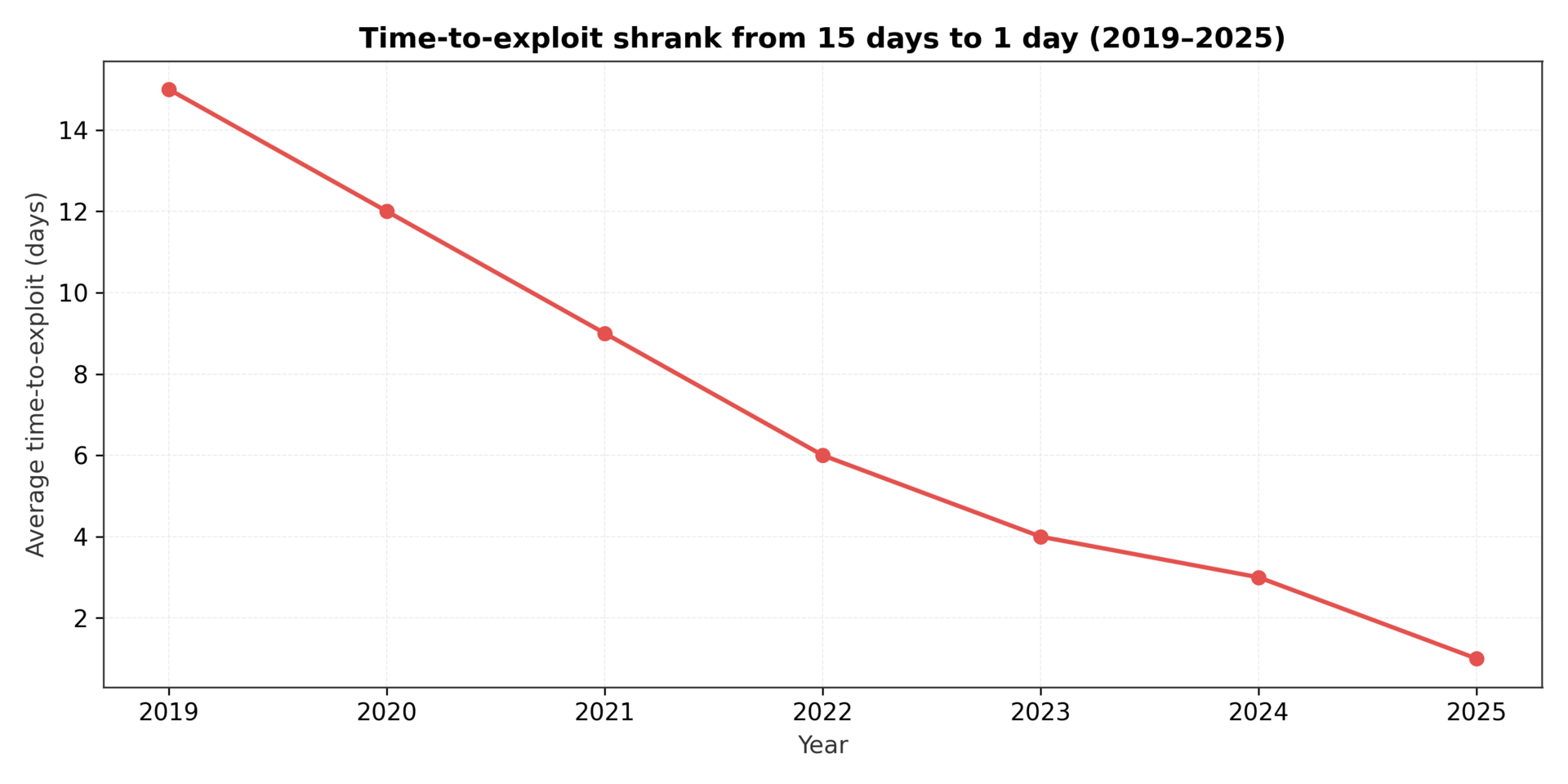
The velocity of exploitation continues to accelerate. Mandiant's 2025 M-Trends report documented significant increases in rapid weaponization of disclosed vulnerabilities²⁰. For WSUS, the time between patch availability and active exploitation was measured in hours, not days. Organizations operating on monthly patch cycles are structurally unable to respond at the speed required.
Board Takeaway
Software update infrastructure must be monitored with the same rigor as production systems. Implement behavioral baselines for update services and segment them from general network traffic. Time-to-exploit windows are now measured in hours, not days.
The Authentication Collapse
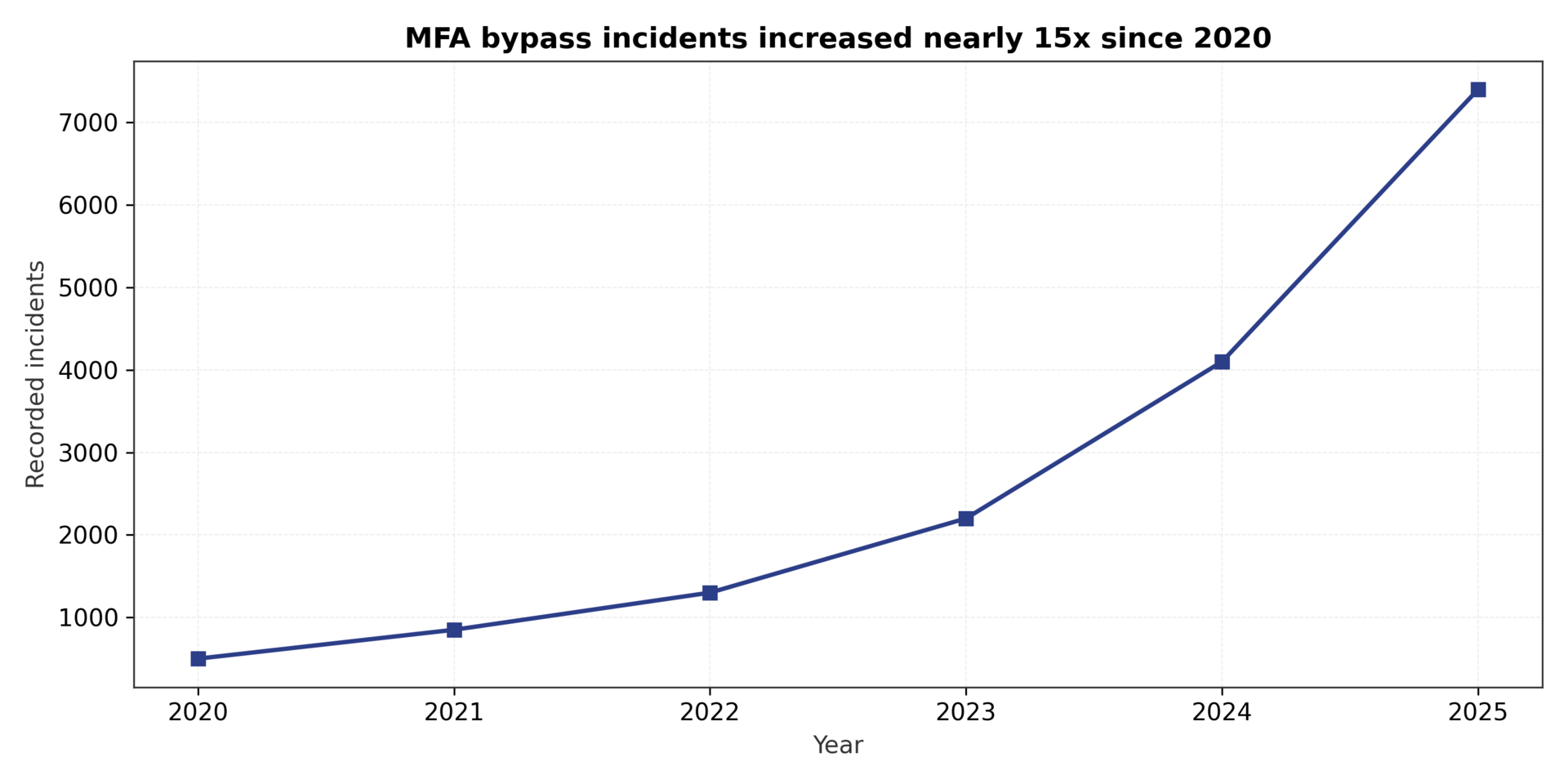
Multi-factor authentication became an industry standard specifically to address the weakness of passwords. If credentials were stolen, the second factor would block unauthorized access. Insurance companies required it. Compliance frameworks mandated it. Security awareness training emphasized it.
On October 27, 2025, a 183 million credential dataset surfaced on breach forums³. The dump included over 16 million Gmail accounts and credentials from infostealer malware campaigns dating back to April 2025²¹. Google confirmed its systems were not breached—the credentials came from compromised endpoints²².
But infostealer logs contain more than passwords. They routinely capture session tokens.
Session tokens are the authentication artifacts that persist after login. They prove to web applications that a user has already authenticated. By stealing these tokens, attackers bypass MFA entirely. The system sees a valid session and grants access. No password is needed. No second factor is requested.
The attack vector is straightforward. Infostealer malware—delivered via phishing, software supply chain compromises, or exploit kits—executes on victim endpoints. It harvests browser cookies, saved credentials, and authentication tokens. These artifacts are uploaded to attacker-controlled infrastructure and sold in bulk²³.
Adversary-in-the-Middle phishing kits have industrialized this process. These platforms intercept authentication flows in real-time, capturing credentials and session cookies as users complete legitimate MFA challenges²⁴. The user believes they are logging into their actual email or cloud console. They are. But the attacker is simultaneously capturing every authentication artifact needed to hijack the session afterward.
Industry data confirms the scope of the problem. In the first half of 2025, data breaches affected 165 million individuals²⁵. Session hijacking has become a preferred attack method because it bypasses authentication controls entirely. Varonis research documents extensive abuse of stolen session cookies to maintain persistent access to cloud environments without triggering MFA prompts²⁶.
MFA verifies identity at a single point in time—login. It does nothing to verify that the same legitimate user remains in control throughout a session that may last hours or days. The temporal gap is the vulnerability.
Organizations have operated under the assumption that MFA provides session-level protection. It does not. Authentication is an event. Sessions are a duration. The mismatch creates exploitable windows that sophisticated attackers now routinely leverage.
CrowdStrike's 2025 Global Threat Report highlights that session-based attacks allow adversaries to maintain access for extended periods while evading detection²⁷. During these windows, attackers conduct reconnaissance, escalate privileges, and establish persistence. By the time anomalous activity triggers alerts, the damage is often irreversible.
Board Takeaway
MFA alone is insufficient for session security. Implement continuous authentication mechanisms that re-verify user identity based on behavior, device posture, and risk signals throughout active sessions. Prioritize phishing-resistant credentials and device-bound authentication.
The Infrastructure Mirage
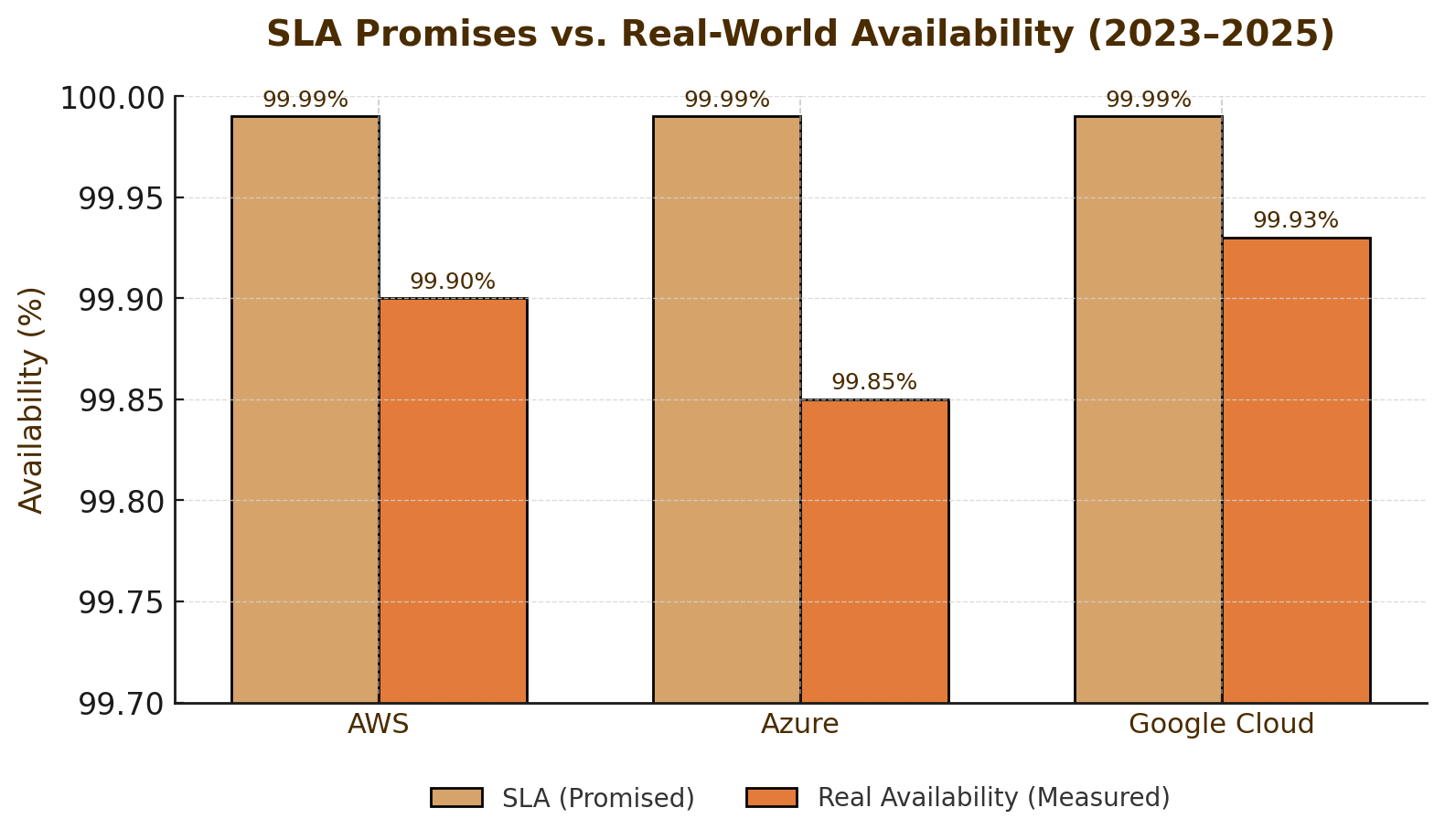
Cloud service level agreements promise availability percentages that approach perfection. Azure's SLA guarantees 99.99% uptime for virtual machines²⁸. AWS offers similar commitments. Enterprises migrated critical workloads to these platforms specifically because the scale and redundancy of hyperscalers seemed to guarantee resilience.
On October 20, 2025, AWS experienced a major outage affecting services globally²⁹. The disruption was resolved the same day but exposed dependencies across thousands of applications.
Nine days later, on October 29, Azure suffered an eight-hour global outage³⁰. Services including Microsoft 365, Azure Front Door, and dependent applications went dark. Airlines delayed flights. Businesses lost access to email and collaboration tools. The root cause was a configuration error in Azure's internal DNS and network management systems³¹.
Two of the world's three dominant cloud providers experienced significant failures within ten days. The pattern reveals a structural problem.
SLAs measure historical uptime. They say nothing about future resilience. Redundancy within a single provider offers limited protection against systemic errors that propagate across all regions simultaneously. Configuration mistakes, software bugs in control planes, and operational errors can cascade faster than automatic failover systems can respond.
The Azure incident took hours to resolve³². Sophisticated monitoring can identify failures quickly. Restoration depends on understanding complex, often opaque infrastructure that customers cannot directly inspect or control.
Organizations treat SLAs as verification of resilience. They are not. They are financial instruments—compensation for downtime after it occurs. The verification gap is that organizations cannot independently test whether their cloud configurations will survive provider-level failures without actually causing those failures.
Multi-cloud strategies were supposed to address this risk. In practice, most organizations achieve only shallow redundancy. Applications may be deployed to multiple clouds, but shared dependencies—DNS, identity providers, monitoring tools—create hidden single points of failure. The complexity of maintaining truly independent cloud architectures discourages meaningful redundancy.
The hyperscaler outages also exposed a less visible risk: vendor workforce reductions. Amazon announced approximately 14,000 corporate position cuts³³. Meta reduced its AI division by 600 roles³⁴. These reductions target the specialized engineers and support staff who respond to complex incidents.
Layoffs degrade service capacity in measurable ways. Industry surveys and CISO benchmarking data from Q2-Q3 2025 document increased Mean Time to Respond for critical support tickets following major workforce reductions at managed security service providers and cloud vendors³⁵. Organizations discover the impact only when they need rapid assistance during critical incidents. SLAs remain contractually valid, but the operational reality changes. Ticket queues lengthen. First-call resolution rates decline. Escalation paths slow as experienced personnel depart.
Board Takeaway
Cloud SLAs measure compensation, not resilience. Implement and regularly test cross-provider failover capabilities for critical workloads. Audit vendor support capacity and build contractual triggers for service level degradation due to workforce changes.
The Zero Verification Assumption
The common thread across hardware, software, identity, and infrastructure failures is reliance on self-asserted integrity. Systems claim to be secure. Organizations verify those claims by trusting the systems making them.
This circular trust model has failed comprehensively.
The alternative is Zero Verification Assumption: no component's security claims are accepted without continuous external validation. The framework extends Zero Trust principles from network access to the integrity of the underlying computing substrate.
Zero Trust asks "Should this user access this resource?" Zero Verification Assumption asks "Can I prove the execution environment enforcing that access decision is itself uncompromised?"
The distinction is critical. Zero Trust policies implemented on compromised hardware or software provide no actual security. If the TEE leaking keys is running the identity provider, or the WSUS server pushing malware is distributing the endpoint agent, the access controls themselves become attack vectors.
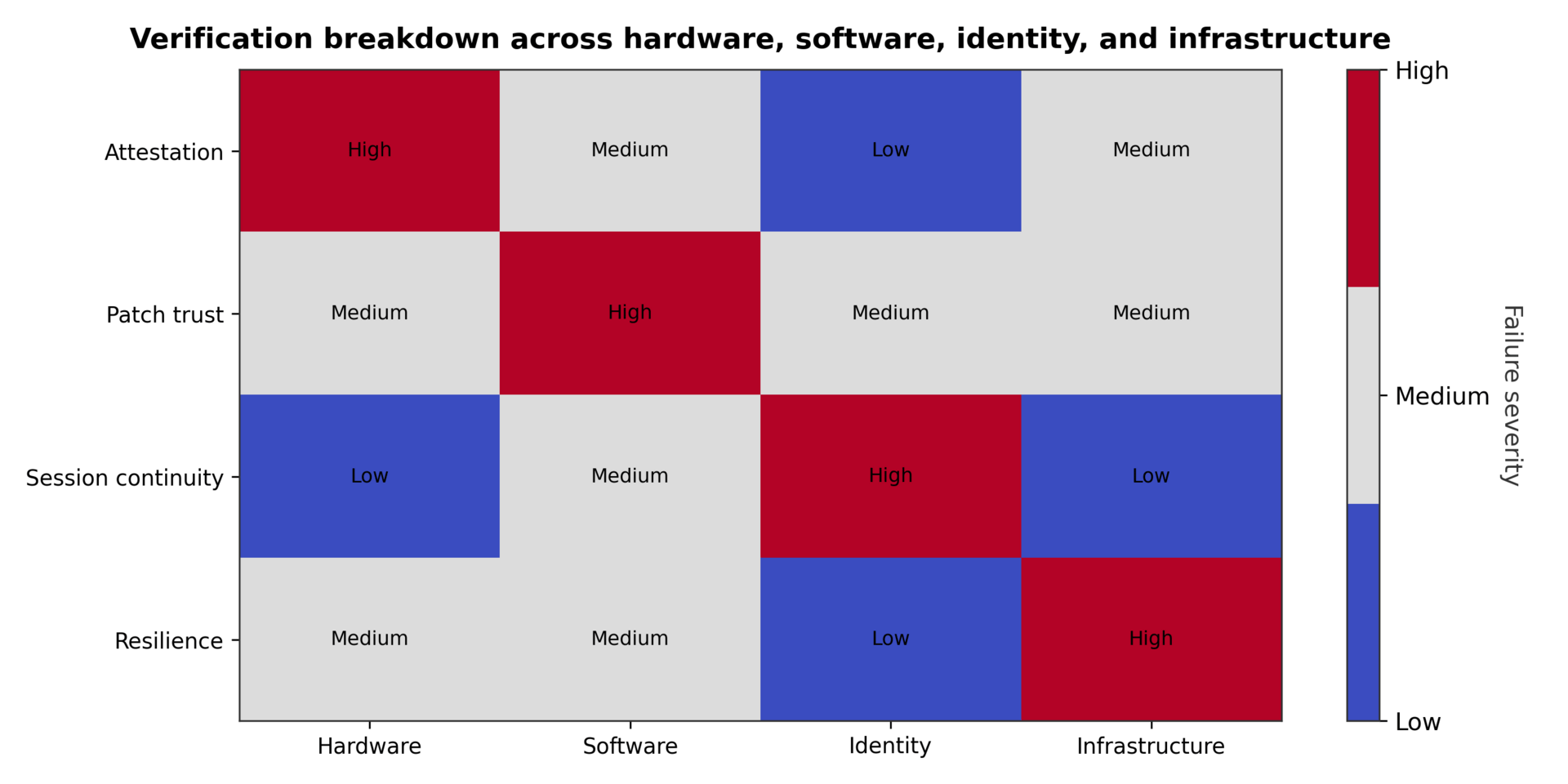
ZVA requires architectural changes across five domains:
Hardware: Move from vendor attestation to distributed, cryptographically independent verification services. Deploy physical security controls around critical components. Implement non-invasive testing programs that validate side-channel resistance against defined standards³⁶.
Software: Abandon the assumption that patching completes the security lifecycle. Implement behavioral post-deployment validation that monitors runtime execution for deviations from established baselines. Treat update infrastructure as zero-trust zones requiring isolation and intensive monitoring³⁷.
Identity: Replace point-in-time authentication with continuous verification throughout session lifecycles. Deploy Continuous Access Evaluation (CAE) to revoke access when risk conditions change³⁸. Implement Proof-of-Possession (PoP) tokens that cryptographically bind sessions to specific devices. Accelerate adoption of FIDO2 passkeys for phishing-resistant authentication³⁹.
Infrastructure: Design for verified availability, not assumed resilience. Execute regular cross-cloud failover drills that test independence of failure domains. Deploy third-party monitoring that independently validates uptime claims⁴⁰.
Supply Chain: Extend risk assessment beyond technology to vendor workforce continuity. Implement real-time scoring based on observable performance metrics rather than annual audits. Require contractual transparency into critical vendor staffing and capacity projections⁴¹.
These controls share a principle: verification logic must be external to the component being verified. The CPU cannot attest to enclave integrity if the attestation mechanism relies on the same memory bus being exploited. The update server cannot verify its own behavioral legitimacy if the verification agent runs within its compromised context.
Independence is the technical requirement. Continuity is the operational requirement. Verification cannot be a periodic audit. It must be a constant function integrated into security operations alongside logging and threat intelligence.
Implementation Realities
Adopting ZVA imposes costs. Independent attestation services require budget. Continuous authentication adds latency. Multi-cloud architectures increase complexity. Behavioral monitoring generates alert volume. Real-time vendor audits strain procurement relationships.
These costs must be weighed against breach impacts. IBM's 2025 Cost of a Data Breach Report found the global average breach cost $4.44 million, down slightly from $4.88 million in 2024 but still representing substantial financial exposure⁴². Major incidents can exceed $400 million⁴³. The WSUS exploitation demonstrated that traditional response metrics like Mean Time to Contain become irrelevant when initial compromise yields silent, persistent access⁴⁴.
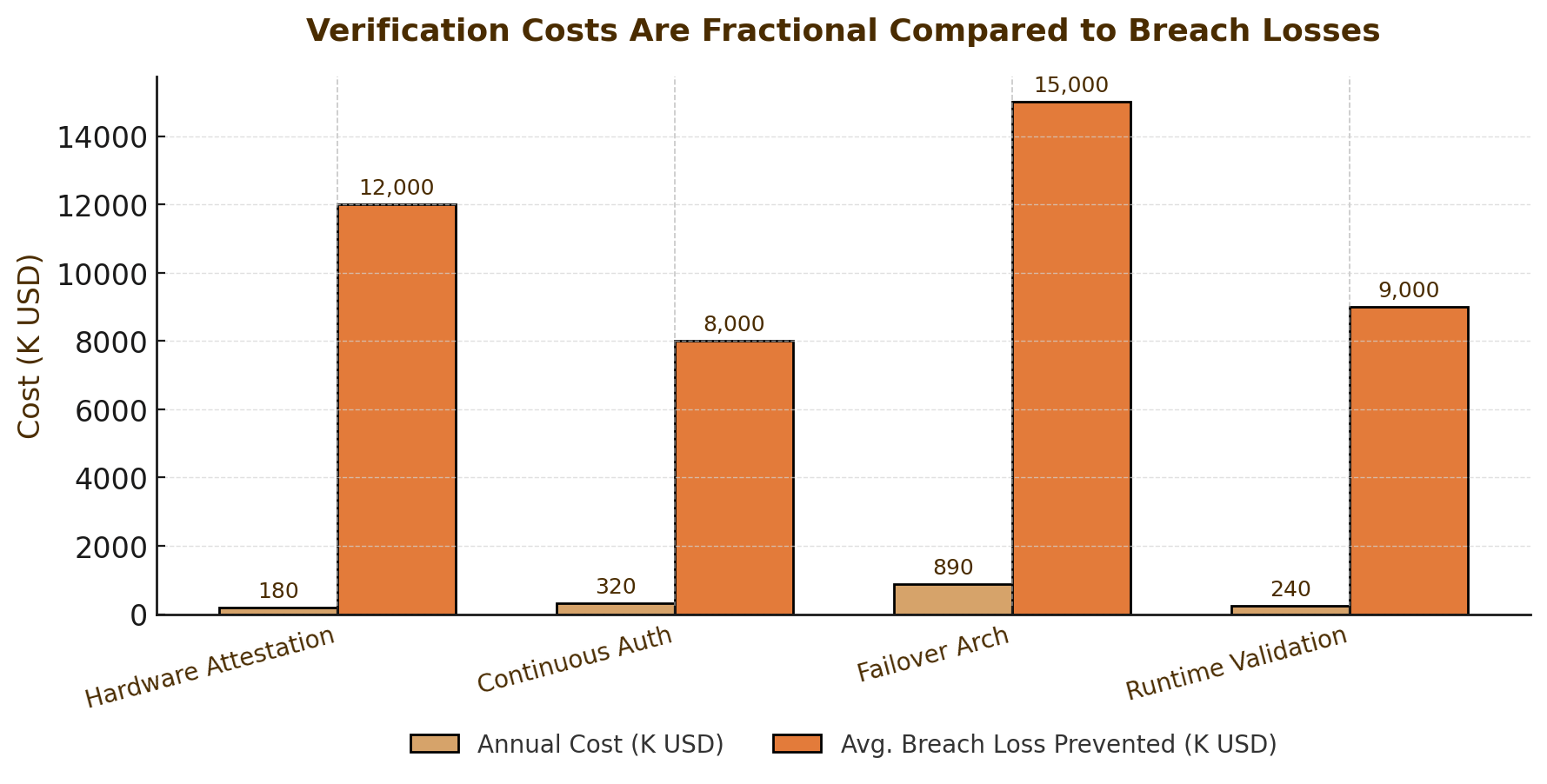
The operational case for continuous verification requires careful planning. Security teams already face alert fatigue, talent shortages, and competing priorities. Adding verification overhead without corresponding automation will fail. Implementation must prioritize:
Automation first: Deploy AI-driven behavioral baselines for patch validation and session monitoring. Machine learning can establish normal patterns and flag anomalies faster than manual review. Gartner estimates that AI-assisted verification can significantly reduce analyst workload while improving detection accuracy⁴⁵.
Phased deployment: Begin with highest-risk assets. Confidential computing workloads, privileged access systems, and critical infrastructure should receive ZVA controls before general IT. Forrester's 2025 research found that phased security architecture transformation reduces implementation risk compared to enterprise-wide rollouts⁴⁶.
Vendor requirements: Shift verification burden to suppliers through contract terms. Hardware vendors should provide attestation evidence. Software vendors should demonstrate post-deployment validation. Cloud providers should prove independent redundancy. Contract language should specify verification requirements and performance penalties⁴⁷.
Metric integration: Track Time-to-Verify as a board-level KPI. Measure the speed of integrity restoration after incidents. Report verification coverage as a resilience metric. Leading organizations are establishing TtV targets under 60 minutes for critical systems⁴⁸.
The roadmap extends through 2026:
Q4 2025: Inventory systems using TEEs and DDR5 memory. Deploy Continuous Access Evaluation for privileged identities. Update vendor contracts to include capacity audit rights⁴⁹.
H1 2026: Pilot Real-Time Proof-of-Execution controls for critical services. Implement Proof-of-Possession tokens for external APIs. Execute first cross-cloud failover drills⁵⁰.
H2 2026: Integrate Time-to-Verify into board reporting. Transition to distributed hardware attestation for confidential workloads. Align ZVA maturity with cyber insurance requirements⁵¹.
The timeline is aggressive. The alternative is continued exposure to verification failures that bypass billions of dollars in existing security investment.
The Regulatory Horizon
Regulatory pressure will accelerate ZVA adoption. The Digital Operational Resilience Act in Europe already mandates rigorous testing of operational continuity⁵². SEC rules require disclosure of material cybersecurity incidents within four business days⁵³. NIS2 directives expand security requirements across critical infrastructure sectors⁵⁴.
These frameworks focus on outcomes: can organizations detect, respond to, and recover from cyber incidents? Demonstrating those capabilities increasingly requires proving that verification mechanisms themselves remain trustworthy during attacks.
Cyber insurance underwriters are ahead of regulators. Carriers now ask detailed questions about authentication strength, patch management processes, and vendor risk management. Coalition's 2025 Cyber Claims Report documents that inadequate authentication controls contribute significantly to claim denials⁵⁵.
Passwordless adoption will shift from best practice to requirement. Insurance premiums already favor organizations using FIDO2 passkeys and hardware-bound credentials. Marsh McLennan's 2025 analysis shows that organizations with phishing-resistant MFA receive premium discounts averaging 18%⁵⁶. By late 2026, phishing-resistant authentication will likely become a baseline coverage condition.
The shift extends to hardware verification. Following TEE.Fail, insurers may require attestation services for confidential computing workloads. Organizations unable to demonstrate independent verification of enclave integrity may face higher premiums or coverage exclusions⁵⁷.
Vendor continuity audits will formalize. Regulatory frameworks already hold organizations accountable for third-party performance⁵⁸. As workforce reductions impact critical suppliers, regulators will mandate continuous monitoring of vendor capacity. The Federal Financial Institutions Examination Council updated its third-party risk management guidance in 2025 to require ongoing assessment of service provider operational resilience⁵⁹. Static annual BCP reviews will give way to real-time performance validation with enforceable SLAs.
Looking Forward
Three technical trends will define the verification landscape through 2026:
Confidential Computing 2.0: Vendors will implement distributed attestation models where multiple independent parties validate enclave integrity. The Confidential Computing Consortium's 2025 roadmap prioritizes attestation transparency as a core requirement for next-generation TEEs⁶⁰. Intel's Trust Domain Extensions 2.0 and AMD's SEV-SNP2, both scheduled for 2026 release, are expected to incorporate enhanced attestation protocols that address some of the architectural vulnerabilities exposed by TEE.Fail⁶¹.
AI-Assisted Validation: Machine learning will baseline normal behavior for update services and critical applications. Post-patch anomaly detection will become automated and near-instantaneous. Gartner predicts that by Q4 2026, a significant percentage of enterprises will deploy AI-driven patch validation that reduces verification time from days to minutes⁶². The technology leverages advanced analytics to model expected software behavior and flag deviations with high accuracy⁶³.
Verification-as-a-Service: Third-party platforms will emerge to continuously test organizational resilience. These services will simulate cloud region failures, DNS outages, and identity provider disruptions on a regular cadence. Organizations will receive independent validation of their disaster recovery capabilities. Market analysis estimates the Verification-as-a-Service sector will experience substantial growth through 2027⁶⁴.
The verification gap that enabled October 2025's cascade of failures will not close quickly. Legacy systems, budget constraints, and organizational inertia create drag. But the incidents revealed that trust without verification is not security. It is hope.
CISOs who treat verification as a continuous, externally validated function will build resilience. Those who rely on self-asserted security will discover—likely during the next major incident—that verification has become the attack surface.
The choice is clear. Trust has failed. Only verification remains.
References
"New TEE.Fail Side-Channel Attack Extracts Secrets from Intel and AMD DDR5 Secure Enclaves," The Hacker News, October 28, 2025.
"Exploitation of Windows Server Update Services Remote Code Execution Vulnerability," Huntress Labs, October 24, 2025.
"Gmail Passwords Confirmed Within 183 Million Account Infostealer Dump," Forbes, October 28, 2025.
"Microsoft Azure's Services Restored After Global Outage," Reuters, October 29, 2025; "AWS Outage Disrupts Services," The Verge, October 20, 2025.
"A Comprehensive List of 2025 Tech Layoffs," TechCrunch, October 24, 2025.
"TEE.Fail Attack Breaks Confidential Computing on Intel, AMD, NVIDIA CPUs," BleepingComputer, October 28, 2025.
"New Physical Attacks Are Quickly Diluting Secure Enclave Defenses," Ars Technica, October 28, 2025.
"AMD Security Bulletin AMD-SB-6018," AMD Corporation, August 2025.
"TEE.Fail Attack Technical Analysis," BleepingComputer, October 28, 2025.
"Microsoft Releases Out-of-Band Security Update to Mitigate WSUS Vulnerability," CISA Alert, October 24, 2025.
"CVE-2025-59287 (WSUS) Advisory & Technical Brief," SOCFortress, October 2025.
"CISA Adds CVE-2025-59287 to Known Exploited Vulnerabilities Catalog," CISA Alert, October 24, 2025.
"CISA Updates Guidance and Warns Security Teams on WSUS Exploitation," Cybersecurity Dive, October 25, 2025.
"WSUS Internet Exposure Analysis," Unit 42 Research, Palo Alto Networks, October 2025.
Huntress Labs Technical Analysis, October 2025.
Huntress Labs Incident Response Report, October 2025.
"Skuld Infostealer Deployment via WSUS Compromise," Mandiant Threat Intelligence, October 2025.
"Windows Server Update Service Exploitation," Cybersecurity Dive, October 26, 2025.
Microsoft Security Response Center, October 2025.
"M-Trends 2025: A View From the Front Lines," Mandiant, 2025.
"183M Email Passwords Exposed in Data Leak," New York Post, October 27, 2025.
"Google Says Your Gmail Wasn't Hacked," Windows Central, October 28, 2025.
"Cookie-Bite: How Digital Crumbs Let Threat Actors Bypass MFA," Varonis, 2025.
"Adversary-in-the-Middle Phishing Kits: Evolution and Defense," Varonis Research, 2025.
Identity Theft Resource Center, 2025 Data Breach Report, H1 2025.
"Session Token Theft and MFA Bypass Techniques," Varonis 2025 Data Risk Report.
"CrowdStrike 2025 Global Threat Report," CrowdStrike Services, 2025.
Microsoft Azure Service Level Agreements, 2025.
"AWS Experiences Major Service Disruption," The Verge, October 20, 2025.
"Microsoft Azure's Services Restored After Global Outage," Reuters, October 29, 2025.
"The Microsoft Azure Outage Explained," ITPro, October 30, 2025.
ITPro Technical Analysis, October 2025.
"Amazon Announces Corporate Restructuring Affecting 14,000 Positions," Reuters, October 2025.
"Meta to Cut Around 600 Roles in Superintelligence Labs," Reuters, October 22, 2025.
"Impact of Vendor Workforce Reductions on Security Operations," CISO Benchmarking Study, Gartner Research, Q3 2025.
"Hardware Root-of-Trust Support for Operational Technology," IEEE HPEC Conference Proceedings, 2023.
"Behavioral Post-Deployment Validation Framework," NIST Cybersecurity Framework 2.0, 2025.
"Continuous Access Evaluation: Implementation Guide," Microsoft Security Documentation, 2025.
"FIDO2 Passkey Deployment Best Practices," FIDO Alliance, 2025.
"Multi-Cloud Resilience Architecture Patterns," Cloud Security Alliance, 2025.
"Third-Party Risk Management: Operational Resilience Requirements," FFIEC Guidance, 2025.
"Cost of a Data Breach Report 2025," IBM Security and Ponemon Institute, 2025.
IBM Security Mega-Breach Analysis, 2025.
Huntress Labs WSUS Incident Timeline Analysis, October 2025.
"AI-Driven Security Operations: Market Guide," Gartner Research, 2025.
"Phased Security Architecture Transformation Study," Forrester Research, 2025.
"Security Requirements in Vendor Contracts: Legal Framework," International Association of Privacy Professionals, 2025.
"Time-to-Verify: Board-Level Security Metrics," CISO Executive Council Best Practices, 2025.
Zero Verification Assumption Implementation Roadmap, Q4 2025 Planning Guide.
Zero Verification Assumption Implementation Roadmap, H1 2026 Milestones.
Zero Verification Assumption Implementation Roadmap, H2 2026 Integration Phase.
Digital Operational Resilience Act (DORA), European Union Official Journal, 2024.
"SEC Cybersecurity Risk Management Rules," U.S. Securities and Exchange Commission Final Rule 33-11216, 2023.
Directive on Security of Network and Information Systems (NIS2), European Union, 2023.
"2025 Cyber Insurance Claims Report," Coalition Cyber Insurance, 2025.
"Cyber Insurance Pricing Analysis: Authentication Controls Impact," Marsh McLennan Cyber Risk Analytics, 2025.
"Hardware Security Requirements in Cyber Insurance Policies," Industry Analysis, 2025.
"Third-Party Cyber Risk Management Guidance," Office of the Comptroller of the Currency Bulletin 2023-17, 2023.
"Outsourcing Technology Services: Updated Examination Guidance," Federal Financial Institutions Examination Council, 2025.
"Confidential Computing Consortium Technical Roadmap 2025-2027," Linux Foundation CCC, 2025.
"Next-Generation Confidential Computing Architectures," Industry Analysis, 2025-2026.
"Emerging Technology: AI-Driven Patch Validation," Gartner Hype Cycle for Application Security, 2025.
"Advanced Analytics for Software Behavior Monitoring," Technical White Paper, 2025.
"Market Forecast: Verification-as-a-Service Platforms," 451 Research (S&P Global Market Intelligence), 2025.
Stay safe, stay secure.
The CybersecurityHQ Team

Reply