- Defend & Conquer
- Posts
- JLR shutdown extends beyond November
JLR shutdown extends beyond November
CybersecurityHQ weekly analysis
Welcome reader to your CybersecurityHQ report
Brought to you by:
👣 Smallstep – Secures Wi-Fi, VPNs, ZTNA, SaaS and APIs with hardware-bound credentials powered by ACME Device Attestation
📊 LockThreat – AI-powered GRC that replaces legacy tools and unifies compliance, risk, audit and vendor management in one platform
Forwarded this email? Join 70,000 weekly readers by signing up now.
—
Get annual access to our deep dives, weekly cyber intel podcast report, premium content, AI Resume Builder, and more — all for just $299. Corporate plans are now available too.
Introducing the CISO Access Plan Unlock premium CybersecurityHQ insights at no cost, exclusively for CISOs. Reach out to me to claim your access.
CISO Weekly Tactical Brief: Government Accelerates AI Adoption While FEMA Breach Exposes Federal Vulnerabilities, Mobile Malware Explodes
GSA signs $300M+ deal deploying Grok AI across federal agencies while FEMA/CBP breach via Citrix vulnerability exposes "widespread" employee data theft, revealing critical gaps in government cybersecurity. Trump executive order directs $50M toward AI-powered childhood cancer research as OpenAI launches Sora video generation social network rivaling TikTok.
CoreWeave inks $14.2B AI cloud deal with Meta while mobile malware variants Datzbro and Klopatra target Android devices with device takeover attacks. Cisco ASA zero-day actively exploited by state actors as China-linked Phantom Taurus emerges with stealth government targeting. Jaguar Land Rover shutdown extends indefinitely beyond November while Microsoft cuts Israeli military cloud access amid surveillance concerns.
Quantum computing achieves 6,100-qubit milestone as PsiQuantum breaks ground on America's largest quantum facility. CMMC compliance now mandatory for DoD contractors with immediate certification requirements affecting existing contracts. Talent shortage reaches crisis levels with 86% of organizations affected and only 14% fully staffed.
Strategic Assessment
This week crystallized the paradox of government AI acceleration amid catastrophic security failures. While GSA rapidly deployed Grok AI to federal agencies and Trump directed AI toward cancer research, the "widespread" FEMA/CBP breach through Citrix vulnerabilities proved government infrastructure remains fundamentally compromised. The contrast between AI ambition and basic security failures demands immediate attention.
Mobile devices emerged as the dominant attack surface with Android malware variants achieving device takeover capabilities while targeting elderly users. WhatsApp's 0-click exploit via DNG files demonstrates attackers no longer require user interaction for complete compromise. Combined with state-actor deepfakes forging military credentials, the endpoint security model built for desktops has collapsed under mobile-first threats.
The $14.2B CoreWeave-Meta infrastructure deal alongside Samsung-OpenAI partnership reveals AI compute becoming concentrated in few hands, creating systemic dependencies. When coupled with Microsoft's geopolitical cloud restrictions and extended automotive shutdowns, supply chain resilience requires fundamental rethinking beyond vendor diversification.
Critical talent shortage constraining all initiatives: 86% of organizations report cybersecurity staffing gaps while only 14% are fully staffed, creating implementation bottlenecks regardless of budget availability.
Key Developments
Government Cybersecurity Crisis Deepens
FEMA/CBP breach: "Widespread cybersecurity incident" enables employee data theft via Citrix vulnerability
Federal exposure: Multiple agencies potentially compromised through shared infrastructure
CISA response: Emergency Directive ED 25-03 for Cisco device compromise identification
Cisco ASA zero-day: State-backed actors deploy RayInitiator malware across government networks
Timeline: Vulnerability exploited before patches available; full scope unknown
Institutional impact: Questions arise about federal cybersecurity fundamentals during AI expansion
Aggressive Government AI Deployment
GSA-xAI deal: September 25 agreement brings Grok AI to federal agencies ($300M+ value)
Trump executive order: September 30 directive allocates $50M for AI childhood cancer research
Strategic timing: Rapid AI adoption concurrent with major security failures
Operational questions: Security frameworks for AI tools in classified environments unclear
Policy gap: No visible AI safety standards accompanying deployment mandates
Vendor concentration: Federal AI capabilities increasingly dependent on private sector platforms
Platform launch: On September 30, OpenAI unveiled video generation AI with social network integration
Capability scope: Text-to-video creation including personalized footage insertion
Market positioning: Direct competition with TikTok, YouTube, Instagram
Deepfake implications: High-quality synthetic video generation widely accessible
Content verification crisis: Authentication systems unprepared for scale of synthetic media
Enterprise risk: Brand impersonation and executive deepfakes democratized
Mobile Malware Reaches Critical Mass
Datzbro trojan: Android banking malware with device takeover (DTO) targeting elderly
Klopatra emergence: Hidden VNC enables complete smartphone control
WhatsApp vulnerability: 0-click exploits via DNG files enable remote compromise without user interaction
Smishing surge: Millions targeted in coordinated campaigns across Europe
BYOD vulnerability: Corporate policies create ungoverned attack surface
Milesight router exploitation: Compromised routers deliver phishing SMS
120 Android CVEs: Google patches including 2 actively exploited zero-days (September 30)
Defensive innovation: Google Drive deploys AI-powered ransomware detection
State-Sponsored Threat Evolution
Phantom Taurus: New China-linked APT targeting governments with stealth malware
North Korean deepfakes: Military ID forgery using advanced synthetic media
APT41 persistence: AI-enhanced operations targeting U.S. economic policy experts
Attribution challenge: Stealth techniques delay detection by 18+ months
Geopolitical alignment: Attacks correlate with Gaza conflict and Ukraine war timing
Technique advancement: Traditional attribution methods increasingly ineffective
Cloud Infrastructure Mega-Deals
CoreWeave-Meta: $14.2B AI cloud deal through 2031 (largest infrastructure contract)
Samsung-OpenAI: Strategic partnership for global AI infrastructure advancement
Oracle positioning: $300B+ capacity deals with Meta and OpenAI
Concentration risk: Top 3 cloud providers control 70%+ of AI compute
Hyperscale growth: Market projected 18.8% CAGR through 2029 ($461B in 2025)
Dependency mapping: Critical to identify single points of AI infrastructure failure
Extended Automotive Disruption
Jaguar Land Rover: Production shutdown now indefinite beyond November target
Supplier cascade: Multiple Tier-1 suppliers request government assistance
Stellantis breach: September 20 customer data exposure via Salesforce connection
Supply chain fragility: Connected vehicles expand attack surface geometrically
Recovery timeline: Months not weeks becoming standard for cyber incidents
Manufacturing impact: Q4 production targets now unachievable across sector
Geopolitical Cyber Actions
Microsoft-Israel: Cloud service restrictions to military units over surveillance concerns
Russian infrastructure: Sanctions ineffective as operations rebrand within days
Afghanistan blackout: Taliban nationwide internet shutdown enters second week
European drone incursions: Denmark, Sweden airports closed; NATO shoot-down considered
Ukraine operations: Strikes on Russian refineries; requests for Tomahawk missiles
Supply disruptions: Crimea fuel shortages complicate Russian logistics
Critical Metrics
Metric | Value | Date | Impact |
|---|---|---|---|
FEMA/CBP breach | "Widespread" | Sept 29 | Federal data compromise |
GSA-xAI deal | $300M+ | Sept 25 | Federal AI deployment |
CoreWeave-Meta deal | $14.2B | Sept 27 | Infrastructure concentration |
Android CVEs | 120 (2 active) | Sept 30 | Mobile fleet at risk |
JLR shutdown | Beyond November | Sept 30+ | Extended disruption |
Quantum milestone | 6,100 qubits | Sept 28 | Computing paradigm shift |
AI backlog | $1T+ | Sept 27 | Infrastructure demand |
Talent shortage | 86% affected | Sept 30 | Implementation capacity constrained |
Board Priorities
Federal breach response: Assess Citrix infrastructure and shared services exposure
Mobile security overhaul: Address Android malware and device takeover risks
AI deployment security: Establish governance before widespread adoption
Supply chain resilience: Map dependencies beyond Tier-1 automotive/cloud providers
Deepfake defense: Implement synthetic media detection and authentication upgrades
CMMC compliance: Immediate action required for DoD contractor certification
Talent acquisition: Address critical staffing gaps constraining all initiatives
30-Day Roadmap
Immediate (72 hours)
Audit all Citrix infrastructure for FEMA/CBP vulnerability indicators
Emergency scan mobile fleet for Datzbro, Klopatra malware variants
Review any GSA/federal AI tool implementations for security gaps
Patch Cisco ASA zero-day and Chrome vulnerabilities immediately
Document automotive supply chain dependencies through Tier-3
Initiate emergency talent acquisition for critical positions
Week 1
Establish AI deployment security framework before tools reach production
Deploy mobile threat detection across all BYOD devices including WhatsApp exploit monitoring
Map federal shared service dependencies (if applicable)
Analyze Phantom Taurus and North Korean deepfake indicators
Implement emergency smishing awareness campaign
Launch accelerated hiring with premium compensation packages
Weeks 2-4
Design comprehensive AI safety and governance protocols
Upgrade identity verification systems for deepfake resistance
Negotiate alternative suppliers for critical automotive/cloud dependencies
Implement behavioral detection for state-sponsored actors
Prepare CMMC certification documentation (if DoD contractor)
Conduct tabletop exercise for extended supply chain disruption
Complete talent gap analysis with training and outsourcing alternatives
Risk Matrix
Domain | Severity | This Week's Change | Required Action |
|---|---|---|---|
Federal Infrastructure | Critical | FEMA/CBP breach active | Citrix audit immediately |
Mobile Threats | Critical | 2 zero-days + malware surge | Fleet protection urgent |
Talent Shortage | Critical | 86% understaffed | Emergency acquisition |
AI Governance | High | Rapid deployment without security | Framework before adoption |
Supply Chain | High | JLR indefinite shutdown | Alternative suppliers |
Deepfakes | High | NK military ID forgery proven | Authentication upgrade |
State Actors | High | Phantom Taurus emergence | Threat intel integration |
This Week's Timeline
Sept 25: GSA signs Grok AI deal; Cisco ASA zero-day disclosed; Android banking trojan identified
Sept 26: Harrods breach (430K records); China replaces high-level diplomat after detention
Sept 27: CoreWeave-Meta $14.2B deal announced; quantum computing trends published
Sept 28: 6,100-qubit processor record; OpenAI revenue $4.3B first half reported
Sept 29: FEMA/CBP widespread breach revealed; WestJet passenger data exposed
Sept 30: Trump AI cancer research executive order; OpenAI Sora launch; PsiQuantum Chicago groundbreaking; JLR shutdown extended; Chrome/Android patches; Microsoft cuts Israeli military access; talent shortage statistics published
Oct 1: G7 increases Russia pressure; Claude Sonnet 4.5 release; Afghanistan blackout continues; CMMC requirements effective November 10
Analysis
Government's AI Paradox
GSA deployed Grok AI to federal agencies on September 25 while the FEMA/CBP breach was revealed September 29—a 4-day window exposing the fundamental mismatch between AI ambition and security capability. This isn't poor timing; it's systemic failure. When government can't secure Citrix environments, how will it protect AI systems with access to classified data and decision-making authority? Organizations must demand AI security frameworks exist before deployment, not after breaches.
Mobile's Complete Takeover
The convergence of Datzbro and Klopatra achieving device takeover, WhatsApp's 0-click DNG exploit, and 120 CVEs including 2 actively exploited proves mobile is now the primary attack surface. The 0-click nature eliminates the last defense—user awareness—making compromise inevitable without technical controls. While enterprises focused on cloud and endpoints, attackers pivoted to personal devices largely outside corporate security controls. The elderly-targeting aspect reveals threat actors exploiting demographics least prepared for mobile threats.
Cloud Concentration Crystallizes
CoreWeave's $14.2B Meta deal, Samsung-OpenAI partnership, and Oracle's $300B+ commitments create unprecedented concentration where 3-4 providers control 70%+ of AI infrastructure. A single compromise or geopolitical action affects entire industries simultaneously. Microsoft's cut-off of Israeli military access demonstrates how quickly cloud access becomes geopolitical leverage. Dependency mapping must extend beyond vendor diversity to geographic and regulatory risk.
State Actors Go Invisible
Phantom Taurus operating undetected for 18+ months, North Korean deepfakes forging military credentials, and APT41's AI-enhanced persistence represent attribution's collapse. Traditional threat intelligence built on observable indicators fails when actors operate in stealth mode for years. The Afghanistan Taliban internet blackout shows authoritarian regimes now wield cyber as population control, while Russian infrastructure rebrandings within days of sanctions prove static blocklists are theater.
Automotive's Long Tail
JLR's indefinite shutdown extension beyond November, combined with Stellantis breach via Salesforce, illustrates modern manufacturing's cyber fragility. Connected vehicles create supply chain dependencies where cyber incidents cascade through Tier-2 and Tier-3 suppliers. The request for government assistance signals systematic vulnerability across manufacturing requiring months to remediate—not one company's problem but an industry crisis.
Quantum's Readiness Signal
The 6,100-qubit milestone and PsiQuantum's Chicago facility groundbreaking mark quantum computing's transition from research to infrastructure. Organizations have 3-5 years maximum to implement post-quantum algorithms. The timing coincides with NIST's finalized standards, creating a defined compliance window that closes faster than most procurement cycles.
Talent Bottleneck
Budget approvals mean nothing without personnel to execute. Quantum expertise, mobile security specialists, and AI governance professionals are in particularly short supply. Organizations must factor 3-6 month recruitment timelines into all initiatives, consider training existing staff, and evaluate managed service alternatives. The premium for specialized talent has reached 15-20% above market rates, yet positions remain unfilled for months.
Implementation Guide
Budget Planning
Federal Infrastructure Audit
Citrix security assessment: 2% of infrastructure budget
Shared service dependency mapping: 4-week project, 3 FTEs
Federal AI tool security review: $150K external assessment
Ongoing monitoring: 1 dedicated federal security analyst
Mobile Security Emergency
Android malware detection platform: 5% of endpoint budget (Lookout/Zimperium)
Device takeover prevention: 2% of security budget
WhatsApp exploit monitoring: Included in mobile threat detection
Smishing awareness program: 1% of training budget
Emergency response team: 2 mobile security specialists
Talent acquisition: 15% premium for scarce mobile security specialists
AI Governance Framework
Security standards development: $200K consulting (if no internal expertise)
AI deployment controls: 3% of application security budget
Vendor security assessments: 2% per major AI tool
Ongoing governance: 2 FTEs for AI security oversight
Supply Chain Resilience
Dependency mapping through Tier-3: 6-week assessment
Alternative supplier negotiation: 20% premium acceptable for critical components
Manual process documentation: 1.5% of operations budget
6-month inventory buffer: CFO approval required for cash flow impact
Talent Acquisition and Retention
Competitive compensation: 15-20% premium for specialists
Accelerated hiring: External recruiter fees 20-25% of first-year salary
Training programs: 3% of security budget for upskilling
Managed services: 10-15% premium vs. internal staffing as alternative
Success Metrics (30 Days)
Citrix infrastructure audited with remediation plan documented
100% mobile fleet scanned with active threats removed
AI governance framework approved and deployment gates implemented
Supply chain dependencies mapped through Tier-3 with alternatives identified
Deepfake detection pilot operational on authentication systems
CMMC gap analysis completed (if applicable)
Talent gap analysis completed with hiring plan and interim solutions approved
Industry Adjustments
Financial Services
Priority: Shared infrastructure exposure following FEMA breach pattern
Mobile risk: Banking app device takeover threatens customer funds directly
AI governance: Trading algorithms and fraud detection require safety frameworks
Talent constraint: Critical shortage in financial cybersecurity specialists
Timeline: October 15 implementation before Q4 earnings
Healthcare
Priority: Government AI adoption pressure without security frameworks
Mobile threats: Clinical device malware implications for patient safety
Deepfake risk: Prescription fraud and insurance claim deepfakes
Staffing challenge: 90%+ report shortages in healthcare security roles
Timeline: Immediate given regulatory and patient safety exposure
Manufacturing
Priority: JLR scenario planning for indefinite cyber-driven shutdowns
Supply chain: 6-month buffers for all critical components
Cloud concentration: Map AI dependencies in design and production systems
Talent scarcity: OT security expertise extremely limited
Timeline: 120-day resilience implementation required
Technology/SaaS
Priority: Customer data in CRM systems following Stellantis-Salesforce model
AI security: Rapid AI feature deployment without safety testing
Mobile apps: Consumer applications vulnerable to device takeover attacks
Staffing competition: Competing for same talent pool driving 20%+ premiums
Timeline: Pre-holiday release cycle security reviews
Federal Contractors
Priority: CMMC certification mandatory November 10 for existing contracts
Citrix audit: FEMA breach pattern threatens clearance status
AI deployment: Conflicting pressures for adoption vs. classification
Clearance requirement: Limits talent pool significantly
Timeline: 45-day compliance window closing rapidly
Executive One-Pager
The Ask
Emergency funding totaling 15-18% security budget increase for federal infrastructure audit, mobile security overhaul, AI governance, and talent acquisition, plus supply chain resilience investments requiring CFO approval.
The Threat
FEMA/CBP: "Widespread" government compromise via Citrix on Sept 29
GSA AI: $300M+ federal AI adoption without visible security framework on Sept 25
Mobile malware: Device takeover attacks targeting funds and credentials
Cloud concentration: $14.2B deals create dependency on 3-4 providers
Talent crisis: Implementation capacity constrained despite budget availability
The Business Impact
Regulatory: CMMC compliance mandatory for DoD contracts (November 10)
Operational: JLR indefinite shutdown model applies across manufacturing
Financial: Customer funds vulnerable to mobile device takeover
Reputational: Government breach patterns expose shared infrastructure weakness
Capacity: Unfilled positions prevent execution regardless of funding
Required Actions (72 Hours)
Audit Citrix infrastructure for FEMA vulnerability (2% budget)
Emergency mobile malware scan and remediation (5% endpoint budget)
Halt AI deployments pending security framework ($200K governance project)
Map supply chain through Tier-3 for critical dependencies (6-week assessment)
Launch emergency talent acquisition (15-20% premium compensation)
The Decision
Government demonstrates it cannot secure basic infrastructure while racing to deploy AI. Mobile devices achieved complete compromise capability without requiring user interaction. Supply chains require months to recover from cyber incidents. Talent shortages prevent execution of initiatives regardless of budget approval. The window for proactive response is measured in weeks, not quarters.
CISO Toolkit
Immediate Detection Steps
Citrix audit: Review all instances for CVE indicators from FEMA breach
Mobile malware: Force Android security updates and scan for Datzbro/Klopatra variants
WhatsApp exploit: Check for anomalous DNG file processing
Cisco devices: Implement CISA Emergency Directive ED 25-03 immediately
AI deployments: Inventory all federal or government AI tools in use
Deepfake indicators: Check authentication logs for anomalous patterns
Automotive exposure: List all JLR or connected vehicle dependencies
Talent assessment: Immediate audit of critical skill gaps
Quick Wins (72 Hours)
Block known smishing campaign domains from mobile security intelligence
Draft AI deployment security requirements before next approval
Implement MFA on all Citrix access points
Enable enhanced authentication for mobile banking/payment apps
Document top 10 supply chain single points of failure
Share Phantom Taurus IoCs across security stack
Deploy Google Drive AI ransomware detection if using Google Workspace
Post priority positions with premium compensation packages
Available Tools
Mobile security: Lookout, Zimperium for Android malware/device takeover detection
AI governance: Microsoft Purview, Google Vertex AI safety controls
Deepfake detection: Sentinel, Reality Defender (70-80% accuracy), Microsoft Video Authenticator
Threat intelligence: Recorded Future, Mandiant for Phantom Taurus indicators
Supply chain: Existing ERP/MRP systems have dependency mapping (often underutilized)
Ransomware detection: Google Drive AI-powered scanning (preventive)
Talent platforms: ISC2 Career Center, ClearanceJobs for specialized roles
What Doesn't Exist Yet
Comprehensive government AI security frameworks (GSA deployed without visible standards)
Real-time device takeover prevention for Android (detection only)
Automated automotive supply chain cyber resilience mapping
Effective sanctions enforcement for rapidly rebranding threat infrastructure
Standardized quantum-safe migration paths (NIST standards exist but implementation unclear)
Sufficient talent pipeline for specialized cybersecurity roles
Why This Week Matters
September 25-October 1, 2025 exposed three critical failures simultaneously: government deployed $300M+ in AI without security frameworks while suffering "widespread" breaches, mobile devices achieved user-interaction-free compromise, and organizations discovered that 86% face talent shortages preventing response regardless of budget.
The 4-day window between GSA's Grok AI deal (Sept 25) and FEMA/CBP breach disclosure (Sept 29) crystallizes 2025's security paradox. State actors went invisible with Phantom Taurus undetected for 18+ months. The $14.2B CoreWeave-Meta deal created systemic dependencies where 3-4 providers control 70%+ of AI compute. JLR's indefinite shutdown proves cyber incidents now require months of recovery.
Organizations must address five converging crises within 30 days, as detailed in the roadmap above. Those waiting for comprehensive guidance or perfect solutions will find adversaries, regulators, supply chain physics, and unfilled positions have already determined outcomes.
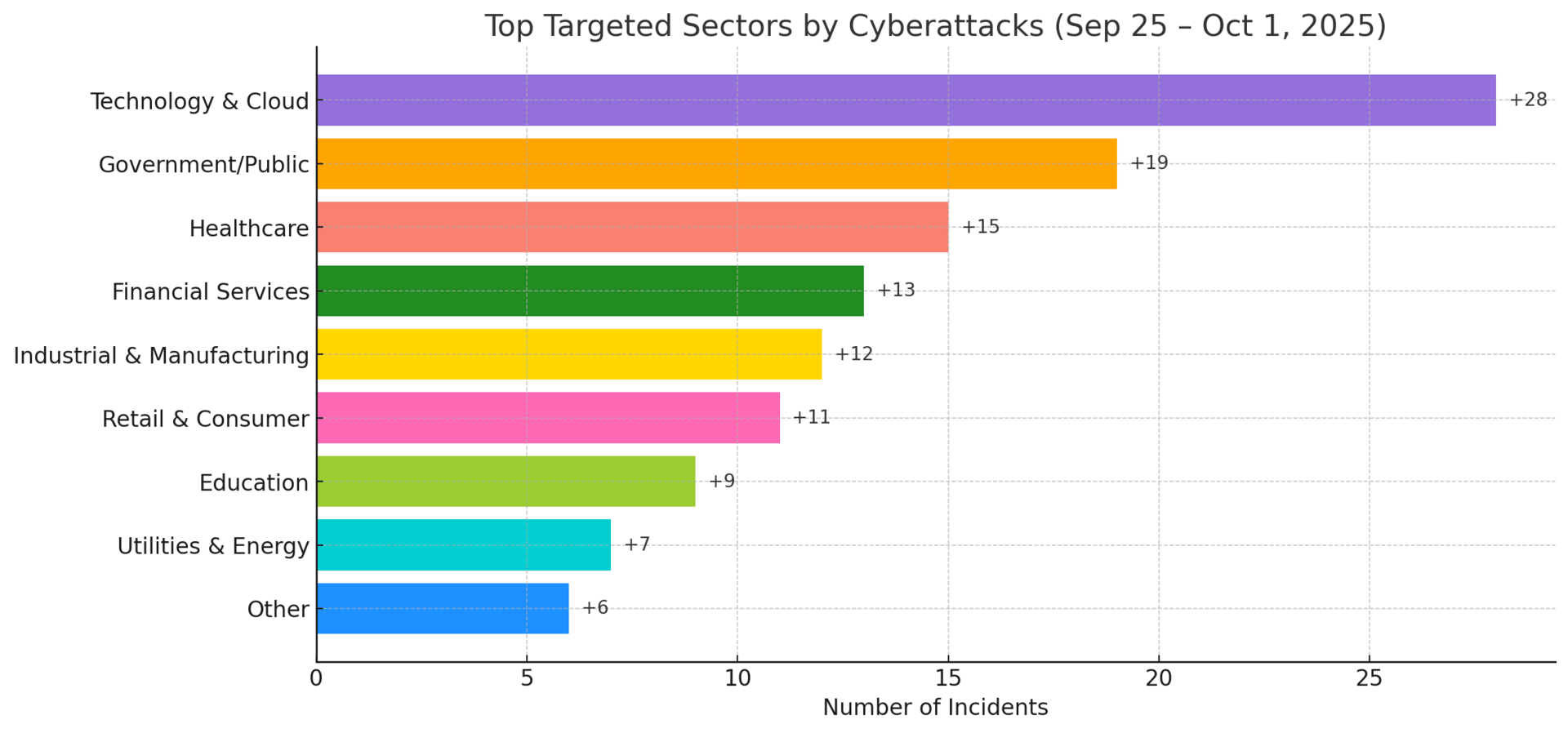
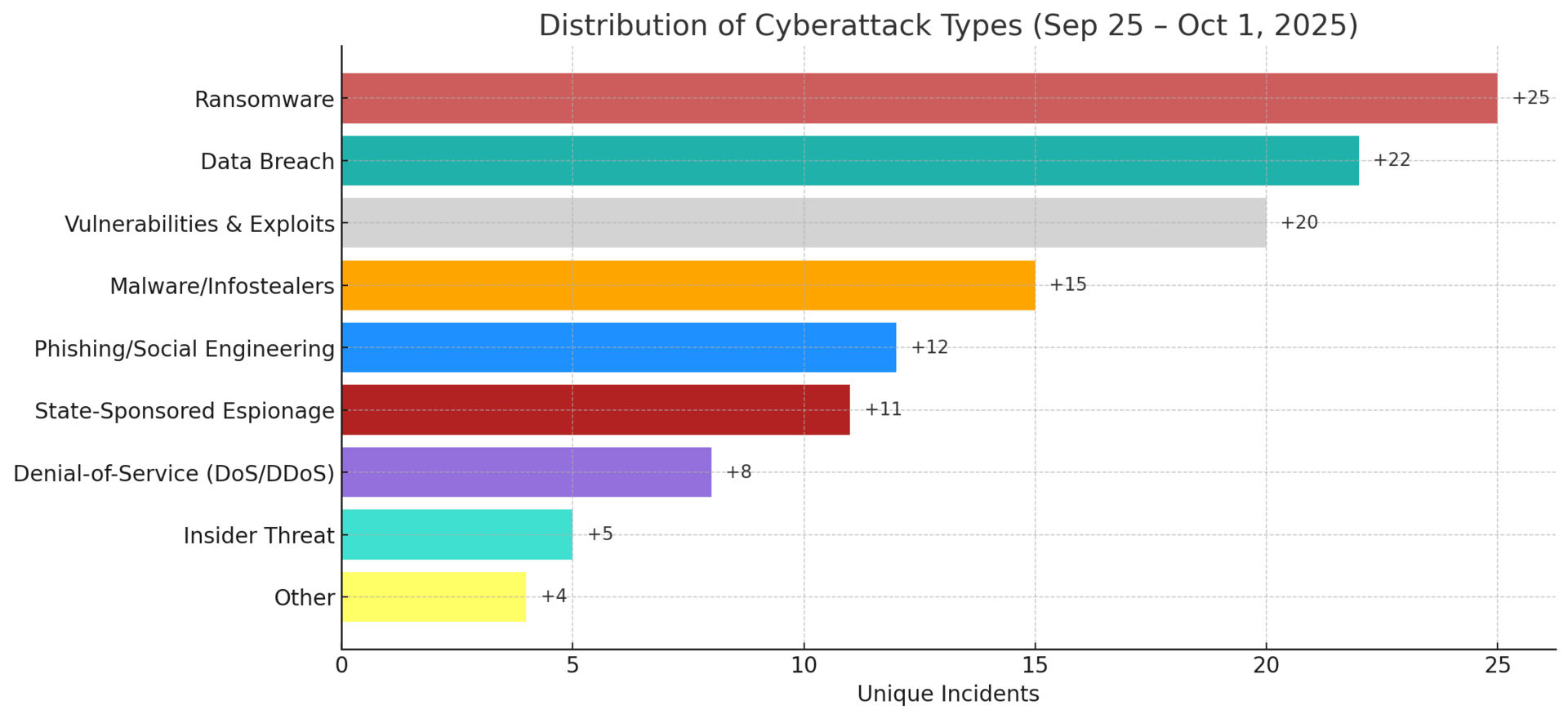
Top Targeted Sectors & Attack Trends
Threat Highlights:
Government/Public: Spike from Cisco firewall exploits; state-backed campaigns active.
Healthcare: Quiet week; ransomware steady but few new breach disclosures.
Financial Services: Fewer visible incidents; delayed filings still a concern.
Technology & Cloud: Still top target; Intel, Red Hat, Google AI flaws dominated.
Industrial/Manufacturing: Slight rise tied to supply-chain exposures.
Ransomware: Broader global spread; schools and EU routers hit.
Exploits: Remain #1 vector; notable hardware/software flaws disclosed.
Phishing: Stable; retail-focused campaigns intensified.
4-Week Threat Momentum
Looking across the past month reveals critical patterns invisible in weekly snapshots. Quantum timeline compressed 3x, government demonstrated deployment-without-security at scale, mobile evolved to zero-interaction compromise, and supply chains progressed from recoverable to indefinite disruption. These trends show velocity increasing, not stabilizing.
Critical Accelerations
Domain | Week 1 (Sept 4-10) | Week 4 (Sept 25-Oct 1) | Trajectory |
|---|---|---|---|
Quantum Weaponization | $1.6B funding signals commercialization | 6,100-qubits operational, infrastructure phase begins | Timeline: 36→18→12 months compressed |
Government Security Model | Regulatory enforcement launches (FTC) | $300M AI deployment + "widespread breach" same week | Adoption velocity inverse to security capability |
Mobile Attack Surface | Not yet primary concern | 120 CVEs + 0-click exploits operational | Desktop-era defenses obsolete |
Cloud Monopolization | $300B Oracle-OpenAI (40% compute) | $320B+ total, 70% in 3-4 providers | Geopolitical leverage demonstrated |
Supply Chain Recovery | Incidents measured in days-weeks | "Indefinite" disruptions, no endpoint | Quarter-long baseline established |
Talent Capacity | Shortage implied | 86% affected, 14% fully staffed | Implementation bottleneck quantified |
State Actor Detection | Attribution still functioning | 18+ month dwell times, methods failed | Invisibility now achievable at scale |
Three Mega-Trends
1. The 18-Month Convergence Pattern
Quantum timeline compressed to 18 months (from 36+)
Shadow AI systems double every 18 months
Discovery assessments require 18+ weeks (systems double during assessment)
State actor detection lags 18+ months behind operations
Strategic planning horizon maximum now 18 months
Business Impact: All planning cycles longer than 18 months operate on obsolete assumptions. Multi-year strategies disconnected from threat velocity.
2. Security Capability Inversion
Week 1: Attackers achieve 40% deepfake phishing success; defenders discover security tools themselves compromised
Week 2: Organizations find 60% of AI deployments invisible to security teams
Week 3: MIT confirms 95% of defensive GenAI initiatives fail; attackers demonstrate operational success
Week 4: Government deploys $300M AI while suffering "widespread breach" same week
Measured Reality: 18-24 month lag between offensive and defensive capabilities widening, not narrowing
3. Disruption Timeline Elongation
Manufacturing: Days → weeks → months → indefinite (no recovery endpoint)
Patch windows: Monthly → weekly → 3x baseline capacity permanent
Talent acquisition: Normal hiring → 3-6 months → 86% can't fill positions
Planning cycles: Multi-year → annual → 18-month maximum viable
Supply buffers: Just-in-time → 3-month → 6-month minimum
Key Pattern: Every timeline assumption from 2024 failed by 2025. "Temporary" crises became permanent baseline.
Emerging Cross-Week Patterns
Quantum Infrastructure Shift: Research funding → Commodity hardware breakthrough → 6,100-qubit scale → Facility construction = Commercial deployment in 12 months, not theoretical threat in years
Government Paradox Crystallized: Liability established → Enforcement launched → Rapid adoption → Catastrophic breach during deployment = Private sector cannot follow government model
Mobile Zero-Interaction: Malware requiring clicks → Campaigns targeting millions → 120 vulnerabilities → 0-click exploits = User awareness eliminated as defense layer
Cloud Geopolitical Weaponization: Concentration concerns → Mega-deals compound → 70% in few providers → Political cutoffs demonstrated = Technical risk became political leverage
Supply Chain Indefinite State: Initial incidents → Extended timelines → Quarter-long impacts → No recovery date = "When will it end?" replaced by "How do we operate indefinitely?"
Talent Market Failure: Shortage suspected → Delays observed → Competition intensifies → 86% unfilled = Market cannot supply personnel regardless of budget
Attribution Collapse: Traditional methods → Longer dwell times → Advanced techniques → 18+ months undetected = Threat intelligence model fundamentally broken for state actors
Strategic Implications
Patch Management: 3x normal capacity is permanent baseline, not surge response (sustained across all 4 weeks)
Quantum Clock: 12-month window closing; organizations assuming 3-5 years operating on failed timeline
Planning Compression: 18-month maximum viable horizon; convergence pattern across multiple domains
Mobile-First Mandatory: 0-click attacks mean awareness training provides zero protection; architecture must change
Multi-Cloud Strategic: 70% concentration + geopolitical leverage = vendor diversity now insufficient; geographic/political diversity required
Government Independence: Federal deployment patterns unsafe to follow; private sector must establish frameworks independent of government
Zero-Trust Vendors: Security tools compromised in supply chains; vendor trust model collapsed
Indefinite Operations: Quarter-long disruptions with no endpoint; 6-month buffers minimum for critical dependencies
Talent Realism: 86% shortage means most organizations cannot execute recommendations; must prioritize ruthlessly and consider managed services
Budget Escalation: 15-18% increase minimum (up from 8-10% mid-month) as compounding threats and talent premiums accumulate
Regulatory Radar
Recently Passed Actions
Regulation | Deadline | Impact | Readiness Actions | Outcome |
|---|---|---|---|---|
NIST IR 8259 Revision 1 Second Public Draft | November 14, 2025 (comment period) | Updates foundational cybersecurity activities for IoT product manufacturers, emphasizing secure device integration and risk mitigation in connected ecosystems | Review draft and submit feedback; align IoT deployment strategies with enhanced manufacturer guidelines to address vulnerabilities in supply chains | Second public draft released September 30, 2025; seeks input on improving IoT security baselines. |
NIST SP 800-172 Drafts for Enhanced CUI Protection | November 14, 2025 (comment period) | Introduces enhanced security requirements and assessment procedures for protecting controlled unclassified information (CUI) in nonfederal systems, focusing on advanced persistent threats | Conduct internal audits of CUI handling; prepare for implementation by testing new controls against current protocols | Drafts released September 29, 2025; public comments invited to refine protections amid rising threats. |
NIST Cybersecurity Framework 2.0 Manufacturing Profile | Ongoing implementation | Provides tailored guidance for manufacturing sector to strengthen risk management, integrating CSF 2.0 with industry-specific controls | Map existing cybersecurity practices to the profile; prioritize updates to vulnerability management in operational technology | Published September 30, 2025; aims to bolster resilience in critical manufacturing environments. |
California AI Safety Law (SB 1047) | Effective January 1, 2026 | Establishes strongest U.S. regulations for AI safety, requiring developers to implement safeguards for high-risk models and report on potential harms | Audit AI systems for compliance; develop safety testing protocols and prepare for state oversight | Signed into law by Governor Newsom on September 29, 2025; focuses on preventing catastrophic risks from advanced AI. |
Immediate Action Required
Regulation | Deadline | Impact | Readiness Actions |
|---|---|---|---|
Cybersecurity Information Sharing Act (CISA 2015) Renewal | October 1, 2025 (expiration) | Potential lapse in private-sector threat sharing with government, hindering collective defense against cyber attacks | Lobby for reauthorization; review information-sharing agreements and prepare contingency plans for reduced federal coordination |
Ohio Acceptance of Crypto Payments for State Fees | Implementation ongoing (announced September 2025) | Enables cryptocurrency options for state transactions, responding to demand and integrating digital assets into public services | Update payment systems for crypto integration; ensure compliance with AML/KYC for affected operations |
Active Compliance Changes
Regulation | Status | Impact | Readiness Actions |
|---|---|---|---|
CMMC Program Expansion | Effective November 10, 2025 | Requires DoD contractors to certify cybersecurity maturity levels, with phased rollout and considerations for small businesses | Begin Level 2 self-assessments; engage third-party certifiers and train teams on updated requirements |
EU AI Act Serious Incident Reporting | Draft guidance issued September 2025; ongoing | Mandates providers of high-risk AI systems to report incidents to authorities, enhancing accountability and risk oversight | Establish incident reporting mechanisms; train staff on identification and escalation of AI-related issues |
SEC/CFTC Crypto Harmonization | Roundtable held September 29, 2025 | Joint efforts to reduce overlap in oversight, including stablecoins as collateral and unified reporting for digital assets | Align cross-agency filings; monitor outcomes from the roundtable on investor protection and market structure |
UK FCA Crypto Handbook Application | Consultation opened September 17, 2025 | Applies existing rules to regulated crypto activities, with proposals for exemptions on integrity and conduct to promote innovation | Assess applicability of exemptions; update AML/CTF and operational resilience frameworks |
New This Week - Crypto & AI Shifts Immediate Effect:
NIST Password Guidelines 2025: Updated recommendations emphasize modern authentication practices, phasing out outdated requirements to enhance security amid evolving threats.
SEC Generic Listing Standards Impact: Following September 17-18 approvals, exchanges can now list commodity-based trust shares without case-by-case reviews, accelerating ETFs for assets like Solana and XRP.
California AI Regulations: New law mandates safety measures for AI developers, setting a benchmark for U.S. states and contrasting with federal approaches.
SEC/FINRA Investigations: Probes into unusual trading ahead of crypto treasury announcements by over 200 firms, highlighting scrutiny on insider activities.
Emerging Requirements Expected Within 30 Days:
CLARITY Act Passage: Anticipated by October 2025, clarifying SEC/CFTC roles in crypto markets to reduce uncertainty and support innovation.
Post-Quantum Cryptography Transitions: NIST timelines for deprecating traditional algorithms by 2030, with migrations expected by 2035, urging early adoption in medical devices and beyond.
State-Level AI Legislation: Expansions in ethics and bias mitigation, including California's new law, with more bills targeting public sector use in upcoming sessions.
Cyber Threat-Sharing Reauthorization: Urgent calls to extend CISA 2015 beyond October 1 expiration, preserving intelligence sharing amid rising attacks.
Critical Comment Periods:
NIST Drafts Feedback: Open through November 14, 2025, on enhanced CUI protections and IoT activities to shape federal cybersecurity standards.
EU AI Act Incident Guidance: Commission seeking input on reporting templates to ensure consistent implementation across high-risk systems.
Global Crypto Surveillance: SEC/CFTC joint statement comments due October 1 on privacy and monitoring in markets, tied to September 29 roundtable.
EU DORA Phased Rollout: Comments on AI intersections and digital resilience for financial sectors due October 10, supporting simplification efforts.
Regulatory Velocity Increase Pattern Recognition:
Accelerated NIST Releases: Multiple drafts in late September (e.g., CUI, IoT, manufacturing) reflect urgency in standardizing defenses against advanced threats, including AI integrations.
Crypto Regulatory Thaw: SEC's ETF streamlining, CFTC stablecoin collateral allowances, and joint harmonization indicate a pivot from enforcement to facilitation, enabling faster market growth.
AI Governance Momentum: California's safety law and EU incident reporting advancements highlight a U.S. shift toward state-led rules, contrasting with international calls for balanced global frameworks.
Federal-State Tensions: CISA expiration risks and state initiatives like Ohio's crypto payments underscore challenges in aligning decentralized enforcement with national priorities.
Action Priority: Focus on submitting comments to NIST drafts by November 14 to influence evolving cybersecurity standards, while monitoring CISA renewal outcomes post-October 1 to safeguard threat-sharing capabilities. With crypto ETF expansions and joint SEC/CFTC efforts accelerating digital asset integration, and AI safety laws gaining traction at state levels, dedicate resources to multi-domain compliance audits—addressing post-quantum shifts and agentic AI risks will be essential for resilient operations in this dynamic regulatory landscape.
CybersecurityHQ: This Week’s Reports Based on Technical Research and Academic Papers
→ Free
The new normal of silent breaches: Why disclosure lag is becoming the biggest blind spot in cyber risk 👉 Read the report
→ Pro subscriber-only
The agentic enterprise: A CISO's strategic guide to identity scoping in chained AI workflows 👉 Read the report
Preventing oversharing in enterprise search deployments 👉 Read the report
Evaluating vendor-native vs. third-party cloud security tooling 👉 Read the report
Defining identity trust levels in MCP-driven workflows 👉 Read the report
And more inside - check out the full list here.
Cybersecurity Stocks
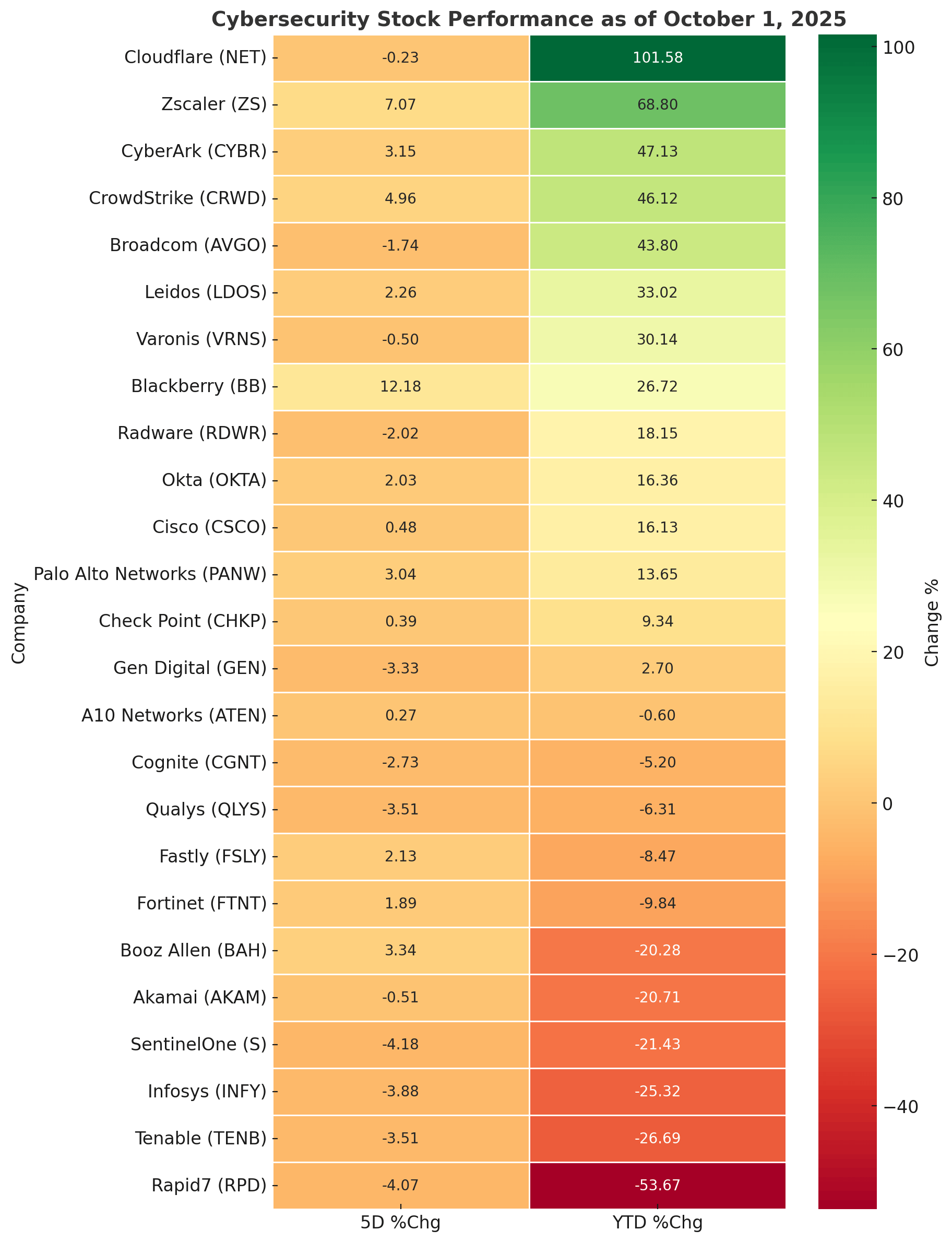
Market Intelligence
The cybersecurity sector posted mixed results this week, averaging +0.4% 5D, with strong rebounds in cloud-native players offset by persistent weakness in network and consulting-heavy names.
BlackBerry (+12.2% 5D) was the standout, jumping on renewed speculation of Canadian government contract wins. Zscaler (+7.1% 5D) extended its rally, fueled by demand for AI-powered zero trust deployments. Leidos (+2.3% 5D) also climbed, supported by a steady flow of U.S. federal security contracts.
On the flip side, Rapid7 (-4.1% 5D, -53.7% YTD) slid deeper into distress territory, while SentinelOne (-4.2% 5D) and Tenable (-3.5% 5D) highlighted continued investor skepticism around mid-cap endpoint and vulnerability players. Consulting-linked names like Infosys (-3.9% 5D) also dragged as margins remain under pressure.
Year-to-date, Cloudflare (+101.6%), Zscaler (+68.8%), and CyberArk (+47.1%) dominate the leaderboard, showcasing cloud-first adoption and hardware-bound identity security. At the other end, RPD, TENB, and INFY underscore ongoing difficulties for players without scale or differentiated IP.
Forward outlook: Sector divergence is widening — high-multiple SaaS security remains well bid, while legacy infrastructure and consulting stocks face rotation risk into Q3 earnings. AI-native security, endpoint consolidation, and federal contract flow will define near-term winners.
Tactical view: Accumulate NET and ZS on weakness; keep an eye on BB’s contract-driven rally and watch TENB/S for capitulation signals.
Cyber Intel Brief: Key Insights from Leading Security Podcasts
This is what you missed in this week’s Cyber Intel Report sourced from top cybersecurity podcasts and webinars, if you haven’t upgraded your membership:
Shadow AI crisis erupts as 90% employee adoption with zero governance bleeds sensitive data into public models while 50-80% cloud workloads run completely unsecured enabling lateral movement attacks, industrialized cybercrime syndicates wielding AI automation slash attack costs to zero launching million-company simultaneous strikes, nation-state Typhoon campaigns pre-position in critical infrastructure with multi-year dormancy before £50M/week JLR-scale manufacturing devastation, sextortion targeting minors explodes 18,600% creating institutional liability nightmares for education sectors, and network security blindspot from cloud migration leaves thousands of mini-perimeters undefended as adversaries think in graphs navigating to crown jewels undetected.
Edge AI Defense cuts cloud costs 60% and analyst triage 80% through on-device NPU inference with XCarbon EDI correlating ECU telemetry for real-time threat detection without latency
Platform Consolidation rationalizes 100-vendor chaos to 5-7 integrated platforms reducing alert fatigue from 500K vulnerabilities to 52 actionable items via surgical AI prioritization
Continuous Monitoring eliminates annual audit scrambles achieving real-time compliance across multiple frameworks with automated evidence collection slashing assessment time from full-day to 1-2 hours
And more insights in this week’s full CISO briefing.
Interesting Read
The U.S. Cyber Information-Sharing Act expires, creating a vulnerability gap for defenders
Expiration of Cyber Information-Sharing Act Leaves U.S. Vulnerable
The 2015 Cybersecurity Information Sharing Act (CISA) officially expired on October 1, 2025, amid congressional gridlock and broader federal funding stalemates.
CISA had provided legal shields and liability protections to encourage private companies—especially critical infrastructure operators and software vendors—to share cyber threat intelligence with federal agencies. Its lapse threatens to stymie real-time collaboration between industry and government just as sophisticated state-sponsored operations are on the rise.
What’s at stake for CISOs & security leaders:
Slower detection, longer dwell times: Without safe harbor protections, firms may hesitate to disclose advanced indicators, TTPs, or logs that could accelerate national threat mitigation. The absence of legal clarity could bring chilling effects on collaboration.
Fragmented defense posture: States, local governments, and public-private alliances may try to step in, but inconsistent policies across jurisdictions will increase friction and reduce cohesion in coordinated defense.
Governance and exposure risk: CISOs must now reassess internal policies around threat data sharing, balancing compliance and liability with national security responsibilities.
Strategic pressure on vendors: Providers of security tools and platforms may feel increased legal risk, potentially pulling back on telemetry sharing or joint threat hunts unless new protections are defined.
Bottom line: The expiration of CISA marks one of the rare times that U.S. federal policy has turned from an enabler of resilience into a structural vulnerability for defenders. For security leaders, this is not just a legislative footnote — it’s a potential force multiplier for attackers. Enshrining trust and safe-sharing regimes will be a priority for board-level advocacy and lobbying in the months ahead.
→ Read more at TechRadar
Fresh From the Field: Security Resources You Can Use
Title | Domain | Authors / Vendor | Key Insight | Source |
|---|---|---|---|---|
Cybersecurity for Small Businesses | Cybersecurity | Comcast Business | Regular updates, employee AI-phishing training, and MFA drastically reduce risks from malware, botnets, and credential abuse. | |
AI Faithful Reasoning | Artificial Intelligence | Tianyu Zhang, Yizhou Zhang, Hanxue Liang, etc. | FRIT fine-tuning improves chain-of-thought faithfulness by 3.4 pp and accuracy by 7.6 pp, increasing reliability without human labeling. | |
AI LLM Fingerprinting | AI / Security | Fengyuan Liu, Junxiao Yang, Zheng Li, etc. | SeedPrints uses random initialization “birth fingerprints” for persistent model provenance, robust even after fine-tuning or quantization. | |
Secure Cloud for Health Systems | Cloud Security | Oracle / OCI | Zero-trust cloud architecture, proactive monitoring, encryption with customer-controlled keys, and GCC data residency strengthen security and compliance. | |
Secure Quantum Computing Challenges | Quantum Computing | Baheri B., Giusto E., Xu S., Smith K.N., Younis E., Cao P. | QTEEs and hybrid HPC-quantum workflows mitigate insider/vendor threats and can boost performance by up to 190× while preserving confidentiality. |
Rubrik
Palo Alto, CA, US
DoD RMF, Compliance and Risk Management Leader
Credera
Dallas, TX, US
Analyst/Sr Analyst, Risk Management
American Airlines
Dallas, TX, US
Akkodis
Dallas, TX, US
Community Mental Health Authority of Clinton, Eaton and Ingham Counties
Lansing, MI, US
Organizational Change Management Lead (Remote)
CrowdStrike
Remote
Optimum
Bethpage, NY, US
Strada
Remote
Chief Information Officer (CIO)
Edison State Community College
Piqua, OH, US
Stay safe, stay secure.
The CybersecurityHQ Team


Reply