- Defend & Conquer
- Posts
- SharePoint zero-day crisis unfolds
SharePoint zero-day crisis unfolds
CybersecurityHQ weekly analysis

Welcome reader to your CybersecurityHQ report
Brought to you by:
👣 Smallstep – Secures Wi-Fi, VPNs, ZTNA, SaaS and APIs with hardware-bound credentials powered by ACME Device Attestation
🏄♀️ Upwind Security – Real-time cloud security that connects runtime to build-time to stop threats and boost DevSecOps productivity
🔧 Endor Labs – App security from legacy C++ to Bazel monorepos, with reachability-based risk detection and fix suggestions across the SDLC
📊 LockThreat – AI-powered GRC that replaces legacy tools and unifies compliance, risk, audit and vendor management in one platform
Forwarded this email? Join 70,000 weekly readers by signing up now.
—
Get annual access to our deep dives, weekly cyber intel podcast report, premium content, AI Resume Builder, and more — all for just $299. Corporate plans are now available too.
Introducing the CISO Access Plan Unlock premium CybersecurityHQ insights at no cost, exclusively for CISOs. Reach out to me to claim your access.
The cybersecurity landscape has deteriorated dramatically since last week, with Microsoft SharePoint zero-day (CVE-2025-53770) now actively weaponized by Chinese APTs, Salt Typhoon's catastrophic year-long compromise of US National Guard infrastructure revealed, and healthcare ransomware attacks surging beyond previous projections. With 200+ new security incidents this week alone, multiple unpatched zero-days, and AI-weaponized malware evolution accelerating, organizations face a 24-hour window to implement emergency defenses before joining the growing victim list.
Key Messages for Board
SharePoint CVE-2025-53770 actively exploited by Chinese APTs with hundreds of organizations already breached via ToolShell malware.
Salt Typhoon's 12-month military network compromise exposes catastrophic defense supply chain vulnerabilities, including exfiltration of administrator credentials and network diagrams.
Healthcare ransomware surge: Anne Arundel (1.9M), Virginia Radiology (1.4M), European networks under coordinated attack, with overall 2024 breaches hitting record highs like the Change Healthcare incident affecting 190 million.
New AI threats emerged: LameHug LLM malware, PoisonSeed FIDO bypass demonstrating next-gen attack capabilities.
Cisco ISE and CrushFTP zero-days join critical vulnerability list requiring immediate patching.
Recommended Board Actions
Emergency SharePoint patching within 24 hours with hourly progress reporting to board.
Authorize additional funds for Salt Typhoon incident response and infrastructure rebuild.
Mandate healthcare sector security audit given coordinated ransomware campaign.
Approve CISA/FBI partnership for nation-state threat intelligence sharing.
Establish 24/7 war room for current crisis response coordination.
Critical Threat Dashboard - Week-over-Week Changes
New Critical Statistics This Week
200+ new security incidents (vs. 60 last week)
SharePoint zero-day added to critical vulnerability list, with exploits dating back to early July.
Salt Typhoon compromise revealed: Year-long National Guard infiltration, potentially since 2024.
15.5M new healthcare records exposed: Major hospital breaches, part of a 2024 surge where healthcare reported most cyberthreats.
CrushFTP and Cisco ISE zero-days discovered and exploited
LameHug and PoisonSeed AI malware variants identified
$71M cryptocurrency theft (CoinDCX + BigONE)
Risk Matrix - New and Evolving Threats
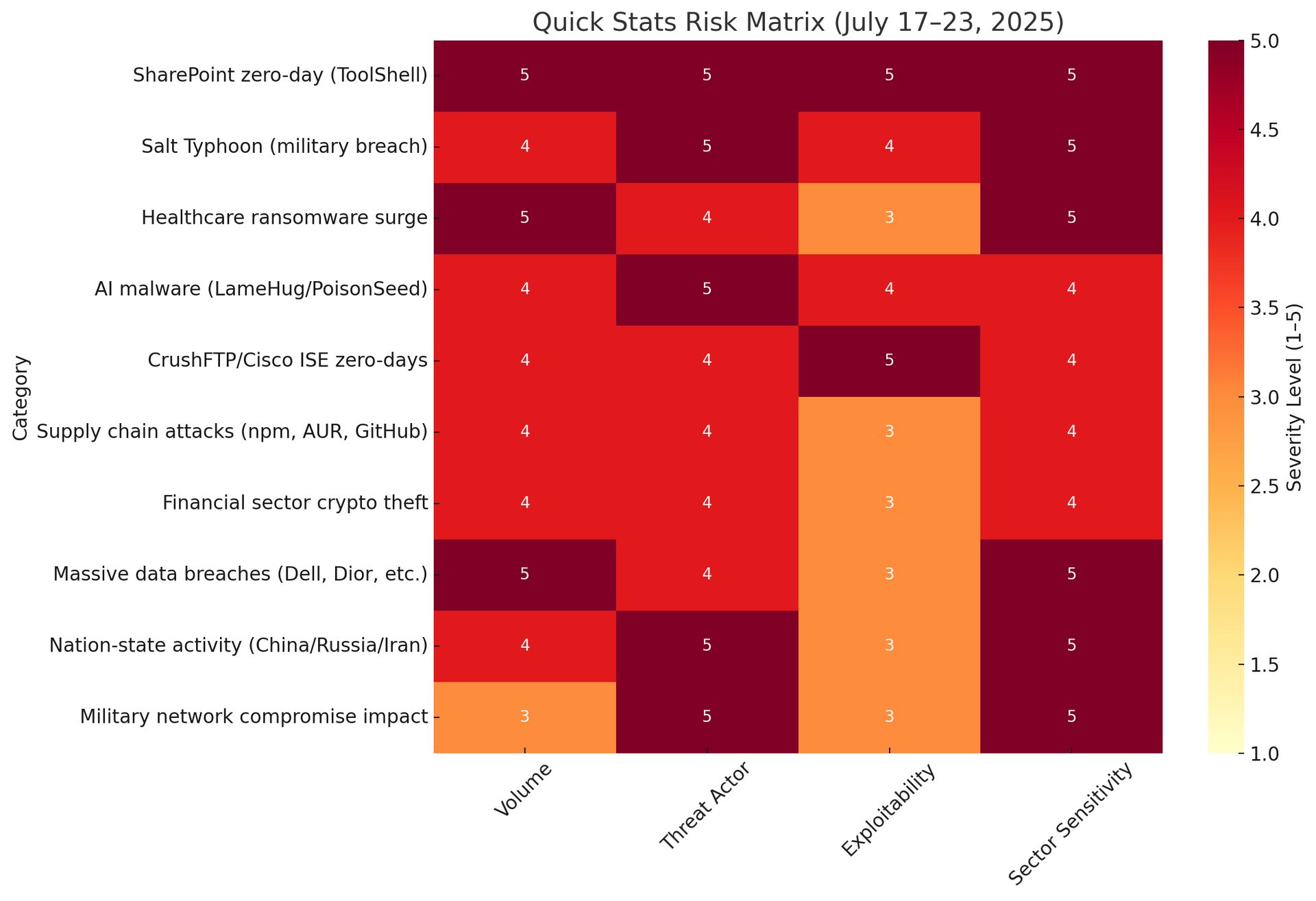
Priority 1: New Zero-Day Vulnerabilities (CRITICAL - 24 Hour Response)
This Week's New Critical CVEs
CVE | System | Vulnerability | Severity | Status | ATT&CK |
|---|---|---|---|---|---|
CVE-2025-53770 | SharePoint | RCE via ToolShell | CRITICAL | EXPLOITED | T1190 |
CVE-2025-54309 | CrushFTP | Zero-day hijack | CRITICAL | EXPLOITED | T1190 |
Multiple | Cisco ISE | Unauth root access | CRITICAL | EXPLOITED | T1059 |
CVE-2025-7877 | Helmholz Routers | Remote exploit | CRITICAL | NEW | T1059 |
CVE-2025-7396 | Curve25519 | Crypto bypass | HIGH | NEW | T1059 |
CVE-2025-7394 | OpenSSL | Elliptic curve | HIGH | NEW | T1083 |
ToolShell malware campaign launched by Chinese APTs.
Hundreds of organizations compromised with persistent backdoors.
Attack progression: Zero-day → Credential theft → AD compromise → Data exfiltration
Microsoft emergency patch released, adoption rate critically low.
CrushFTP Emergency (NEW)
1,000+ servers vulnerable to authentication bypass.
No patch available - vendors scrambling for fix.
Active exploitation for complete server takeover.
Mitigation: Immediate isolation required.
Priority 2: Salt Typhoon Revelation (NEW - Strategic Crisis)
Catastrophic Military Infrastructure Compromise
NEW DISCLOSURE: 12-month undetected presence in US National Guard.
Exfiltrated: Network diagrams, admin credentials, operational data.
Attribution: Advanced Chinese APT with custom evasion tools, operated by MSS since at least 2019.
Scope expansion: Italian telecommunications also compromised; links to broader telecom and Treasury hacks.
Response mandate: Complete infrastructure rebuild required, with experts warning all US forces should assume networks are compromised.
Priority 3: Healthcare Ransomware Explosion (NEW ATTACKS)
This Week's Healthcare Victims
Anne Arundel Dermatology: 1.9M records (NEW)
Virginia Radiology: 1.4M records (NEW)
European Healthcare Network: Multiple hospitals (NEW)
Alcohol & Drug Testing Service: 750K records (NEW)
New Ransomware Groups Active
Interlock: FBI warning issued this week
Kawa4096: ICM Document Solutions hit
Nova/Fog: Evolved Phobos variant
Broader 2024 Context: Surge includes Change Healthcare (190M records exposed, $2.4B cost) and OneBlood attack disrupting services.
Priority 4: AI-Weaponized Malware Evolution (EMERGING)
New AI Threats This Week
LameHug: First confirmed LLM-powered data theft malware
Uses generative AI for real-time analysis
Adapts exfiltration based on discovered data
Traditional AV detection rate: <5%
PoisonSeed: FIDO2 authentication bypass
QR code phishing downgrade attacks
Bypasses hardware security keys
Active campaigns against financial sector
Coyote Banking Trojan: Microsoft UIA exploitation
New variant targeting Latin American banks
AI-enhanced credential harvesting
Priority 5: New Supply Chain Attacks
This Week's Supply Chain Incidents
npm phishing success: eslint-config-prettier compromised
AUR Linux backdoors: Chaos RAT in multiple packages
GitHub weaponization: New Lumma/Redline distribution
Dell test platform: World Leaks claims 1.3TB theft
Major New Data Breaches (This Week)
Technology Sector
Dell: 1.3TB claimed stolen (disputed as "fake")
Ring cameras: Widespread unauthorized access reports
ExpressVPN: IP exposure during RDP sessions
Financial Sector
CoinDCX: $44M cryptocurrency theft (NEW)
BigONE Exchange: $27M stolen (NEW)
KEP Credit Union: Qilin ransomware encryption (NEW)
Fashion/Retail
SABO: 3.5M customer records (NEW)
Dior: US customer notification of breach (NEW)
Week-over-Week Threat Evolution
Escalations from Last Week
Chrome vulnerabilities: Now paired with SharePoint for chained attacks
Fortinet patches: Slow adoption leading to active compromises
WordPress plugins: Gravity Forms added to compromise list
IoT vulnerabilities: Exploitation campaigns launched
New Threat Vectors
Military infrastructure compromise (Salt Typhoon)
AI-powered malware (LameHug, PoisonSeed)
Healthcare sector coordinated attacks
Cryptocurrency exchange targeting
Financial Impact Analysis (Updated)
Risk Category | Last Week | This Week | Change |
|---|---|---|---|
Zero-day exploitation | $10-25M | $25-50M | +100% |
Ransomware recovery | $2.8M | $3.2M | +14% |
Healthcare sector risk | N/A | $45-100M | NEW |
Military/Defense impact | N/A | $100M+ | NEW |
AI malware defense | N/A | $10-30M | NEW |
Strategic Action Framework (Updated Priorities)
Immediate Response (0-24 Hours) - NEW ACTIONS
SharePoint emergency patching - CVE-2025-53770 highest priority.
CrushFTP server isolation - No patch available
Cisco ISE firmware updates - Multiple critical vulnerabilities
Salt Typhoon hunt - Check for persistence mechanisms.
Healthcare sector lockdown - Ransomware prevention mode
This Week's Specific Mitigations
Deploy ToolShell detection signatures.
Block QR code phishing (PoisonSeed)
Implement LLM-aware security monitoring
Isolate military contractor networks
Enable ransomware canaries in healthcare
New Intelligence Requirements
SharePoint additional zero-days timeline
Salt Typhoon secondary targets.
Healthcare attack coordination source
AI malware command infrastructure
Cryptocurrency exchange attack patterns
Industry Developments This Week
Mergers & Acquisitions and Funding
M&A Activity
Datadog-Upwind Security (Pending): Datadog in advanced talks to acquire Israeli CNAPP specialist Upwind Security for up to $1B - would be Datadog's largest Israeli acquisition, strengthening real-time cloud security and observability capabilities.
Thoma Bravo-Darktrace: Completed acquisition to enhance network detection capabilities through private equity expertise (financial terms undisclosed)
Funding Rounds
Vanta Series D: $150M raised at $4.15B valuation (July 23) - Led by Wellington Management, funds will support AI-driven compliance and trust verification expansion.
iCOUNTER Series A: $30M raised (July 17) - Emerged from stealth with SYN Ventures leading, platform uses AI/behavioral analytics for proactive cyber risk management
Market Implications
Cloud Security Consolidation: Datadog-Upwind signals accelerating CNAPP market consolidation amid rising cloud threats.
AI-Driven Security Investment: Both Vanta and iCOUNTER funding highlight investor confidence in AI-enhanced security platforms
Valuation Trends: Vanta's $4.15B valuation demonstrates continued high multiples for compliance/trust platforms.
SentinelOne Rumors: Unconfirmed acquisition talks with Palo Alto Networks indicate potential mega-deals ahead
Law Enforcement Actions
NEW: XSS Forum admin arrested in Ukraine
NEW: Armenian nationals charged in Ryuk attacks
NEW: Phobos ransomware decryptor released
NEW: Google sues BADBOX 2.0 operators
Geopolitical Escalations
China: Salt Typhoon year-long breach, SharePoint weaponization, Taiwan semiconductor attacks, undersea cable concerns.
Russia: GRU Snake malware, NoName057(16) dismantled, NATO targeting intensified
Iran: AI-powered phishing, DCHSpy spyware, DHS retaliation warnings
North Korea: NPM supply chain infiltration for crypto theft
France: Unprecedented government service cyberattack
Critical Gaps Since Last Week
What We Didn't Know Last Week
Salt Typhoon's year-long persistence.
SharePoint zero-day existence.
Healthcare sector coordination
AI malware operational deployment
Military network compromise extent
What We Still Don't Know
Additional SharePoint vulnerabilities
Full Salt Typhoon victim list.
Healthcare attack coordination mechanism
Next AI malware variants
Timeline for major attacks
Conclusion and Executive Mandate
This week's revelations transform our understanding of the threat landscape. Salt Typhoon's year-long military compromise and SharePoint's active exploitation represent fundamental security failures requiring immediate board intervention. The emergence of AI-weaponized malware and coordinated healthcare attacks signals a new era of cyber warfare.
IMMEDIATE BOARD ACTION: SharePoint patching must complete within 24 hours. Salt Typhoon response requires dedicated task force. Healthcare organizations need emergency ransomware defenses activated immediately.
The difference between last week and this week is stark: we've moved from potential threats to active catastrophic compromises. The organizations have hours, not days, to respond.
THIS IS NOT A DRILL: Multiple zero-days are being exploited NOW. Nation-states have been inside military networks for a YEAR. Act accordingly.
Cyber Threats & Attack Trends
CybersecurityHQ: This Week’s Reports Based on Technical Research and Academic Papers
→ Free
The rise of ‘stealth supply chain attacks’: From npm to AI dependencies 👉 Read the report
→ Pro subscriber-only
Centralizing DLP policy enforcement for remote users: Evaluating effectiveness and enterprise challenges 👉 Read the report
Operationalizing SBOM validation in CI/CD pipelines 👉 Read the report
Protecting data integrity during vendor transitions 👉 Read the report
And more inside - check out the full list here.
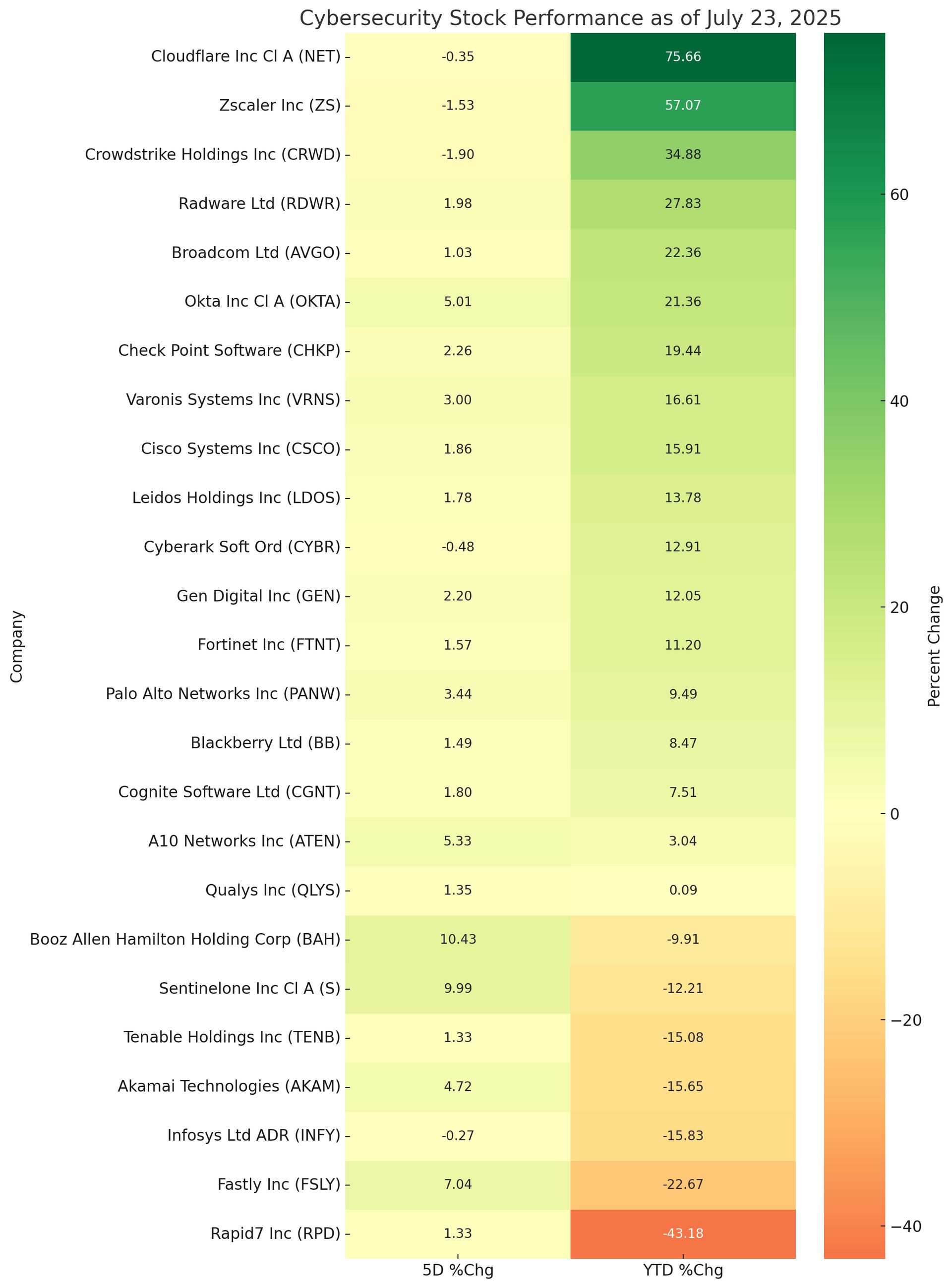
Cybersecurity Stocks
Cyber Intel Brief: Key Insights from Leading Security Podcasts
This is what you missed in this week’s Cyber Intel Report sourced from top cybersecurity podcasts and webinars, if you haven’t upgraded your membership:
⤷ Pentagon Cloud Breach reveals Chinese nationals supporting classified DoD systems with minimal oversight as Microsoft's contractor arrangement exposes catastrophic third-party risk failures
⤷ 90% Burnout Crisis threatens cybersecurity sustainability as 24/7 operational stress drives talent exodus faster than replacement while isolation amplifies team dysfunction
⤷ 560M Snowflake Cascade demonstrates authentication architecture collapse affecting 165+ organizations through single SSO failure with supply chain dependencies
⤷ BOF Memory Attacks bypass traditional endpoint detection enabling 70+ day dwell times as North Korea funds 45% of nuclear program through cryptocurrency theft
⤷ AI-SOC Revolution achieves 70% efficiency gains and 50% false positive reduction while only 19% of data centers possess AI-ready infrastructure
⤷ $2.17B Crypto Theft in H1 2025 normalizes ransom negotiations as GMX pays $5M "bounty" while exchanges lose $42-44M per incident
⤷ Wi-Fi Surveillance Breakthrough enables through-wall 3D human reconstruction using existing infrastructure as DensePose AI transforms radio signals into tracking
And more insights in this week’s full CISO briefing.
Interesting Read
Cyberwar’s Human Capital: The Case for a U.S. Advanced Technology Academy
On July 22, The Washington Post published an op‑ed proposing a bold new institution, the U.S. Advanced Technology Academy (USATA), dedicated to training the next generation of cyber defenders in AI, quantum, and cybersecurity. This academy, envisioned along the Erie Canal in Upstate New York, would offer tuition‑free education (in exchange for five years of national service), targeting the Pentagon’s cyber talent shortfall (estimated at ~30,000), and modeling itself after West Point, Annapolis, and the Air Force Academy
Why it matters:
Human capital is critical as AI and quantum threats rise—technical talent is now strategic infrastructure.
Geopolitical urgency: China’s STEM surge puts U.S. digital defense at a disadvantage without action.
Future-ready training: Cadets would gain skills in quantum encryption and AI-driven cyber ops.
Broader impact: USATA could strengthen national security and improve socioeconomic mobility.
Why CISOs care:
Solves talent shortages by creating a new pipeline of skilled cyber professionals.
Enables public-private partnerships to shape workforce development.
Tabletop relevance: Model risks from talent gaps, not just tech failures.
Fresh From the Field: Security Resources You Can Use
Title | Publisher / Authors | Focus | Access Link |
|---|---|---|---|
State of Cybersecurity 2025 | CompTIA | Strategic cybersecurity trends, enterprise investment priorities, talent pipeline insights | |
Cybersecurity Regulation in Flux as Trump Administration Focuses on Evolving Threats | Latham & Watkins | Executive Order 14306 and U.S. policy shift toward AI, supply chain, and post-quantum risks | |
Declassified Report: FBI/Cyber Election Influence Activities | ODNI | Foreign interference and cyber operations targeting U.S. elections; intelligence community assessment | |
Zero Trust Cybersecurity: Procedures and Considerations in Context | Lund, Lee, Wang et al. (arXiv) | Real-world analysis of Zero Trust in schools/libraries; useful for adapting models to low-budget high-risk orgs | |
From Texts to Shields: Convergence of LLMs and Cybersecurity | Tao Li, Ya-Ting Yang et al. (arXiv) | Trust, transparency, and human-in-the-loop applications of LLMs in defensive cybersecurity |
Hampton North
Washington, DC, US
Illumio
Sunnyvale, CA, US
Chief Information Officer (CIO)
Solar Mason
Scranton, PA, US
Intelligence Analyst - Falcon Recon (Remote)
CrowdStrike
Remote
Senior Cyber Investigations Analyst
Corebridge Financial
Los Angeles, CA, US
F5
Seattle, WA, US
MGM Resorts International
Las Vegas Metropolitan Area, US
Skechers
Manhattan Beach, CA, US
Boeing
Hazelwood, MO, US
Stay safe, stay secure.
The CybersecurityHQ Team

Reply