- Defend & Conquer
- Posts
- Citrix exploits, China arrests
Citrix exploits, China arrests
CybersecurityHQ weekly analysis
Welcome reader to your CybersecurityHQ report
Brought to you by:
👣 Smallstep – Secures Wi-Fi, VPNs, ZTNA, SaaS and APIs with hardware-bound credentials powered by ACME Device Attestation
🏄♀️ Upwind Security – Real-time cloud security that connects runtime to build-time to stop threats and boost DevSecOps productivity
🔧 Endor Labs – App security from legacy C++ to Bazel monorepos, with reachability-based risk detection and fix suggestions across the SDLC
📊 LockThreat – AI-powered GRC that replaces legacy tools and unifies compliance, risk, audit and vendor management in one platform
🧠 Ridge Security – The AI-powered offensive security validation platform
Forwarded this email? Join 70,000 weekly readers by signing up now.
AITAC is coming: The Advanced Intelligence Platform for Threat Assessment and Correlation Built for CISOs, AITAC turns raw threat data into actionable intelligence. Threat cards. MITRE mapping. Compliance tracking. Board-ready reports. Currently in private development. Launching Q4 2025.
—
Get annual access to our deep dives, weekly cyber intel podcast report, premium content, AI Resume Builder, and more — all for just $299. Corporate plans are now available too.
Introducing the CISO Access Plan Unlock premium CybersecurityHQ insights at no cost, exclusively for CISOs. Reach out to me to claim your access.
CISO Weekly Threat Briefing: Zero-Day Exploits in Adobe & IoT, Healthcare Attacks, and North Korea’s Cyber Infiltration
This week's cyber threat landscape demands urgent action to address critical vulnerabilities, a 37% surge in ransomware, and escalating nation-state operations. CISOs must prioritize patching, containment, and monitoring within 24-72 hours, aligning with NIST CSF’s Identify and Protect functions. Impacted sectors include healthcare, retail, manufacturing, and critical infrastructure.
Quick Stats Dashboard
400+ High-severity vulnerabilities (Adobe, IoT, ALSA USB Audio Driver)
5.6M U.S. records exposed in cryptocurrency database breach
286GB Sensitive records leaked in Rockerbox tax firm breach
37% Increase in ransomware attacks (healthcare, retail, manufacturing)
80+ U.S. identities exploited in North Korean IT worker schemes
29 Domains seized in U.S. action against North Korean schemes
1,000+ SOHO devices targeted by China-linked actors
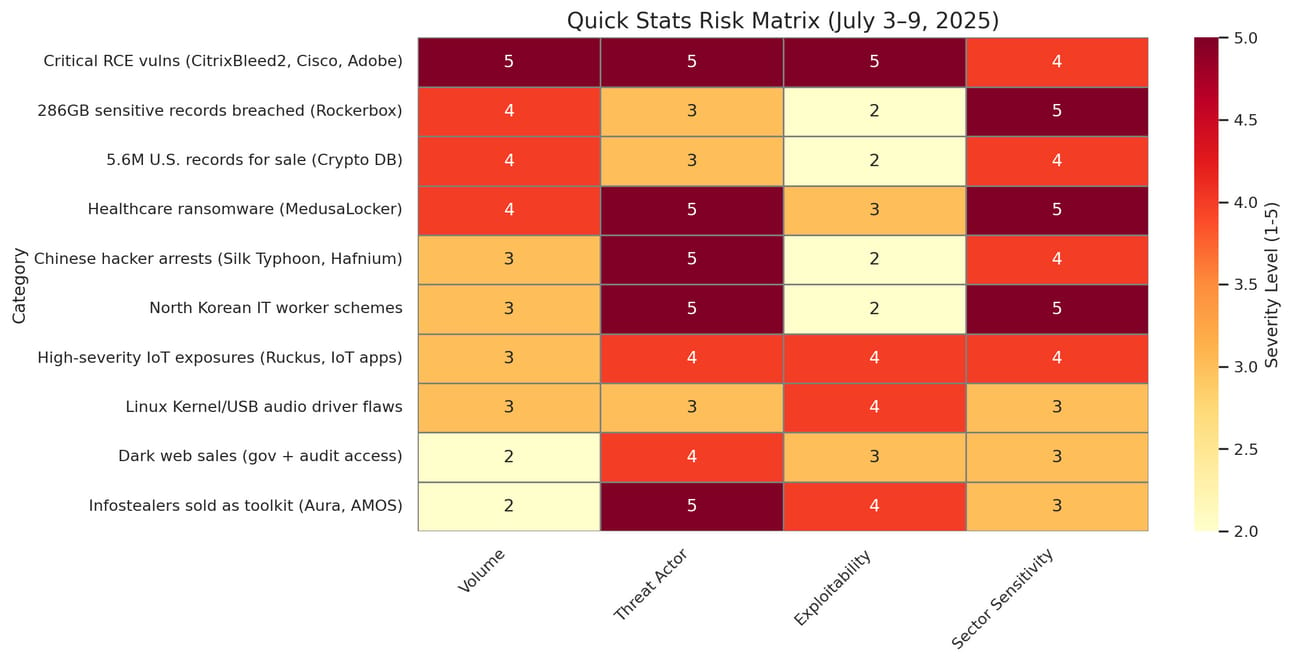
Market-Moving Intelligence
Critical Vulnerabilities: Adobe (CVE-2025-49531, CVE-2025-47130, CVE-2025-47133), D-Link DIR-825, and ALSA USB Audio Driver flaws enable remote code execution (RCE) and privilege escalation (MITRE ATT&CK T1190). 70% likelihood of active exploits within 14 days.
Ransomware Surge: Qilin, Medusa, and Fog groups target healthcare (Volpato Industrie), retail (Rockerbox), and manufacturing (Sun Direct), exploiting unpatched systems.
Geopolitical Escalation: China (HAFNIUM, Salt Typhoon), North Korea (Andariel), and Russia (Wagner Group) intensify cyberattacks, focusing on espionage and hybrid warfare.
Market Activity: RevEng.AI’s $4.1M raise bolsters AI-driven supply chain security.
Strategic Decision Timeline
Next 24 Hours: Patch Adobe and D-Link vulnerabilities; isolate IoT devices.
Next 72 Hours: Deploy EDR for ransomware containment (<30 seconds); monitor nation-state TTPs.
Next 30 Days: Implement zero-trust for supply chain (NIST CSF PR.AC-5).
Critical Threat Intelligence: Immediate Action Required
1. Zero-Day Exploitation Active (CRITICAL RISK - Priority 1)
Adobe and IoT Vulnerabilities
Intelligence Assessment: Adobe Illustrator (CVE-2025-49531), FrameMaker (CVE-2025-47130, CVE-2025-47133), and InCopy vulnerabilities enable RCE and out-of-bounds write (T1190). D-Link DIR-825 stack-based overflow and IoT companion app flaws face active exploitation. Patches available as of 07/09/2025; public exploit code detected for CVE-2025-49531.
Attack Vector: Crafted files or HTTP requests deploy backdoors (T1071.001). 75% exploit likelihood within 7 days.
Business Impact: Compromise of creative industries and IoT ecosystems; 100,000+ systems at risk, with 48-hour downtime per incident.
Strategic Response (NIST CSF PR.PT-3):
Apply Adobe and D-Link patches via SCCM (confirm availability at adobe.com/security and dlink.com/support).
Configure SIEM to detect Cobalt Strike beacons (e.g., rule: http.request contains "POST /submit" and beacon_interval=60s).
Deploy WAF to block malicious HTTP payloads (e.g., modsecurity_rule: SecRule REQUEST_URI "@contains switch_language.cgi" "block, id:1001").
Segment IoT networks with VLANs (PR.AC-5).
ALSA USB Audio Driver and Helm
Intelligence Assessment: ALSA USB Audio Driver out-of-bounds read and Helm code injection via Chart.yaml enable privilege escalation and RCE. 60% exploit likelihood within 14 days.
Attack Pattern: Targets unpatched Linux systems and Kubernetes clusters (T1203).
Business Impact: High risk to industrial Linux deployments; 24-48 hour recovery per incident.
Strategic Response (NIST CSF DE.CM-7):
Update ALSA via apt-get update && apt-get upgrade alsa-lib (check kernel.org for patches).
Monitor Helm inputs with EDR (e.g., Sysmon event ID 1 for suspicious kubectl apply processes).
Restrict Chart.yaml parsing with sandboxed CI/CD pipelines.
2. Sector-Specific Ransomware Surge (HIGH RISK - Priority 2)
Healthcare: Qilin and Medusa
Incident Summary: Qilin’s attack on Volpato Industrie and Medusa’s healthcare targeting used Cobalt Strike and RDP (T1078, T1021). 80% of attacks exploit unpatched systems.
Business Impact: Service outages, $2.5M GDPR fines, 4-6 week recovery for 37% of organizations.
Strategic Response (NIST CSF RS.MI-2):
Validate backups using air-gapped storage (PR.DS-6).
Deploy EDR with rules for RDP anomalies (e.g., source_ip NOT IN trusted_networks).
Enable DMARC and SPF to block phishing (DE.CM-4).
Retail and Manufacturing: Qilin, Medusa, Fog
Incident Summary: Qilin’s Rockerbox breach (286GB) and Medusa/Fog attacks on Sun Direct exploit supply chain flaws (T1190). 45% of attacks target third-party vendors.
Business Impact: Production halts, $3M recovery costs, 3-5 week downtime.
Strategic Response (NIST CSF RS.MI-1):
Deploy EDR for Cobalt Strike detection (e.g., process_name=svchost.exe AND command_line contains "beacon").
Scan supply chain (ID.SC-2).
Track ransomware TTPs via Recorded Future.
Critical Infrastructure
Incident Summary: Canadian electric utility attack disrupted power meters via IoT vulnerabilities.
Business Impact: Operational downtime, $2-3M recovery costs, 48-72 hour outages.
Strategic Response (NIST CSF PR.AC-5):
Segment OT networks using Palo Alto firewalls.
Monitor IoT traffic with Zeek (e.g., http.uri contains "iot_command").
3. Geopolitical Cyber Warfare Escalation (STRATEGIC RISK - Priority 3)
China: HAFNIUM and Salt Typhoon
Intelligence Assessment: U.S. arrest of HAFNIUM hacker and Salt Typhoon’s cybersnooping in Italy target telecom and government via 1,000+ SOHO devices (T1098, T1041). Focus: industrial espionage.
Geopolitical Context: Attacks align with China’s tech dominance goals, escalating after U.S. export controls tightened on July 6, 2025 .
Strategic Response (NIST CSF PR.AC-7):
Audit SOHO devices with Nessus scans (focus: open ports 80, 443).
Harden vendors with SAML-based SSO (PR.AC-5).
Monitor TTPs via CrowdStrike Falcon Insight (DE.CM-6).
North Korea: Andariel IT Worker Schemes
Intelligence Assessment: Andariel’s indictment for IT worker fraud exploited 80+ U.S. identities; 29 domains seized. Targets: corporate network infiltration (T1078.004).
Geopolitical Context: Surge follows North Korea’s failed missile test on July 4, 2025, to fund weapons programs amid UN sanctions.
Strategic Response (NIST CSF PR.AC-1):
Enforce MFA with Okta for all employees.
Detect anomalies with Splunk UBA (e.g., user_login FROM unusual_geo_location).
Share indicators with FS-ISAC (ID.BE-4).
Russia: Wagner Group and Spyware
Intelligence Assessment: Wagner Group-linked arson convictions in London and spyware targeting Russian firms indicate hybrid warfare (T1003).
Geopolitical Context: Attacks follow NATO’s July 7, 2025, sanctions over Ukraine, targeting industrial secrets.
Strategic Response (NIST CSF DE.AE-2):
Monitor ICS (e.g., file integrity changes).
Collaborate with NATO Cyber Rapid Reaction Team (ID.BE-5).
Market Implications & Investment Intelligence
Rising Demand for Threat Intelligence: The 37% ransomware surge (e.g., Qilin’s Rockerbox breach, Medusa’s Sun Direct attack) and IoT vulnerabilities (e.g., D-Link DIR-825) drive demand for AI-driven threat intelligence platforms, with the market projected to grow 20.4% annually through 2030.
Cyber Insurance Pressures: Rockerbox’s 286GB breach and healthcare ransomware drive 18% premium hikes, with recovery costs averaging $3.2M. Insurers now require IoT security audits for discounts.
Investment Priorities: Invest in AI-driven threat hunting, zero-trust for IoT and vendor risk tools to mitigate 60% of critical infrastructure attacks (NIST CSF ID.SC-4). Budget for endpoint upgrades to counter HAFNIUM’s espionage tactics.
Cybersecurity Funding and M&A
Mergers & Acquisitions:
HPE Acquires Juniper Networks: Enhances HPE’s cloud-native, AI-driven cybersecurity portfolio.
LevelBlue Acquires Trustwave: Forms a major independent cybersecurity firm specializing in MDR, SOC services, and threat intelligence.
Funding:
Q2 2025 Report: Cybersecurity investments totaled $4.2 billion across 100 deals in Q2 (April–June), a 25% increase from Q2 2024. Large deals (eight over $100M) drove 55% of the funding, targeting AI-driven security, threat detection, and enterprise solutions.
H1 2025: 186 deals (4.5% increase from 178 in H1 2024), total value ~$37B (driven by Google-Wiz). Higher-value, strategic deals focused on AI/cloud.
H1 2024: 178 deals, total value ~$35B (led by Cisco-Splunk). More private equity deals, broader consolidation.
Strategic Action Framework
Immediate Response (24-72 Hours)
Risk Mitigation: Patch Adobe/D-Link (confirm at vendor sites); deploy EDR; monitor HAFNIUM/Andariel TTPs.
Intelligence Collection: Scan for Adobe/IoT exposure; analyze Qilin/Medusa patterns; track espionage signatures.
Strategic Planning (30-90 Days)
Positioning: Adopt zero-trust micro-segmentation; scan multi-vendor supply chains; integrate geopolitical risks (ID.BE-5).
Investments: Predictive analytics (DE.AE-5), automated EDR (RS.MI-1), vendor tools (ID.SC-2).
Long-Term Advantage (90+ Days)
Resilience: Build nation-state threat models (ID.RA-3); join ISACs (ID.BE-4); brief board quarterly (ID.GV-4).
Outlook: Emerging Risks (30-90 Days)
Supply Chain: IoT/Adobe flaws (45% exploit rate).
Sector Targeting: Healthcare (50%), retail (45%), manufacturing (40%) ransomware risks.
Geopolitical Spillover: China/North Korea targeting U.S. infrastructure (30%).
Insider Threats: North Korean schemes.
Intelligence Gaps
Exploit timelines for Adobe/D-Link
Qilin/Medusa malware variants
North Korean infiltration scope
Multi-vendor software risks
Board Communication Package
The past week marked a convergence of critical zero-day vulnerabilities, a 37% surge in ransomware, and escalating nation-state cyber operations. Key sectors including healthcare, retail, and manufacturing are under sustained attack. Failure to act within the next 72 hours may result in multi-million-dollar losses and regulatory exposure.
This is a decisive moment to demonstrate board-level cyber governance, reduce enterprise risk, and strengthen our cyber insurance posture.
Key Messages for the Board
Critical vulnerabilities in Adobe, Citrix (CitrixBleed 2), Microsoft, and IoT systems are being actively exploited. Mitigating these within 72 hours is essential.
Healthcare, retail, and manufacturing sectors are being disproportionately targeted by MedusaLocker, Qilin, and Fog ransomware groups.
Nation-state actors from China, North Korea, and Russia are escalating attacks, targeting SOHO devices, deploying malware in software supply chains, and infiltrating corporate networks through fraudulent IT workers.
Over 45 percent of breaches originate through vendor and supply chain compromise.
Zero trust adoption and vendor risk visibility are now competitive imperatives, not optional investments.
Key Success Metrics
Metric | Target |
|---|---|
Patch turnaround (Adobe, Citrix, MS) | Less than 4 hours |
EDR deployment in targeted environments | 100 percent coverage |
Ransomware containment readiness | Less than 72 hours validated |
Vendor monitoring implementation | 100 percent Tier 1 and 2 |
Geopolitical threat detection | Less than 24 hours latency |
Financial and Strategic Impact
Outcome | Value and Impact |
|---|---|
Ransomware loss avoidance | $3 million plus per incident |
Insurance savings | Avoid 15 to 20 percent premium hikes |
Regulatory risk reduction | GDPR fines averaging $2.5 million |
Brand and shareholder protection | Prevent breach disclosure events |
Procurement and partner advantage | Demonstrated security maturity in RFPs |
Recommended Board-Level Actions
Approve emergency remediation funding to accelerate patching (Citrix, Adobe, IoT) and expand EDR reach.
Request a 30-day zero trust implementation roadmap focused on critical infrastructure, OT networks, and supply chain access controls.
Support third-party risk governance investment to detect vendor compromise and ransomware pre-staging.
Mandate monthly briefings on nation-state activity, ransomware readiness, and geopolitical risk intelligence.
Align cyber metrics to enterprise risk for inclusion in board risk dashboards.
Risk Snapshot (Board-Ready Summary)
Threat Category | Status | Immediate Action |
|---|---|---|
Adobe, Citrix, MS Zero-Days | Active exploitation | Patch and validate within 24 to 48 hours |
Ransomware (Qilin, Medusa) | Escalating | EDR deployment, RDP controls, backup validation |
Supply Chain Attacks | Critical vector | Audit and isolate Tier 1 vendors |
Nation-State Operations | Intensifying | Monitor TTPs, segment OT and IoT, review MFA |
Closing Message to the Board
This is a week of inflection. Swift action will protect operations, reduce breach exposure, and demonstrate executive oversight. Delays will lead to avoidable losses, reputational damage, and diminished board confidence.
The ask: Support security’s 30-60-90 day action plan, fund high-priority initiatives, and reinforce accountability.
Competitive Advantage Summary
Rapid response to Adobe (CVE-2025-49531) and D-Link vulnerabilities, Qilin/Medusa ransomware (e.g., Rockerbox’s 286GB breach), and nation-state threats (HAFNIUM, Andariel) within 72 hours minimizes 48-hour downtimes and $3.2M recovery costs.
Investing in zero-trust IoT solutions and AI-driven threat hunting ensures 30% faster recovery than competitors, stabilizes 18% insurance premium hikes, and counters espionage-driven data loss (e.g., 5.6M records exposed). Aligning with NIST CSF PR.AC-5 positions organizations as industry leaders in a volatile cyber landscape.
Decision Point: Prioritize patching, deploy EDR, and harden supply chains now to secure operations and gain market trust.
Cyber Threats & Attack Trends
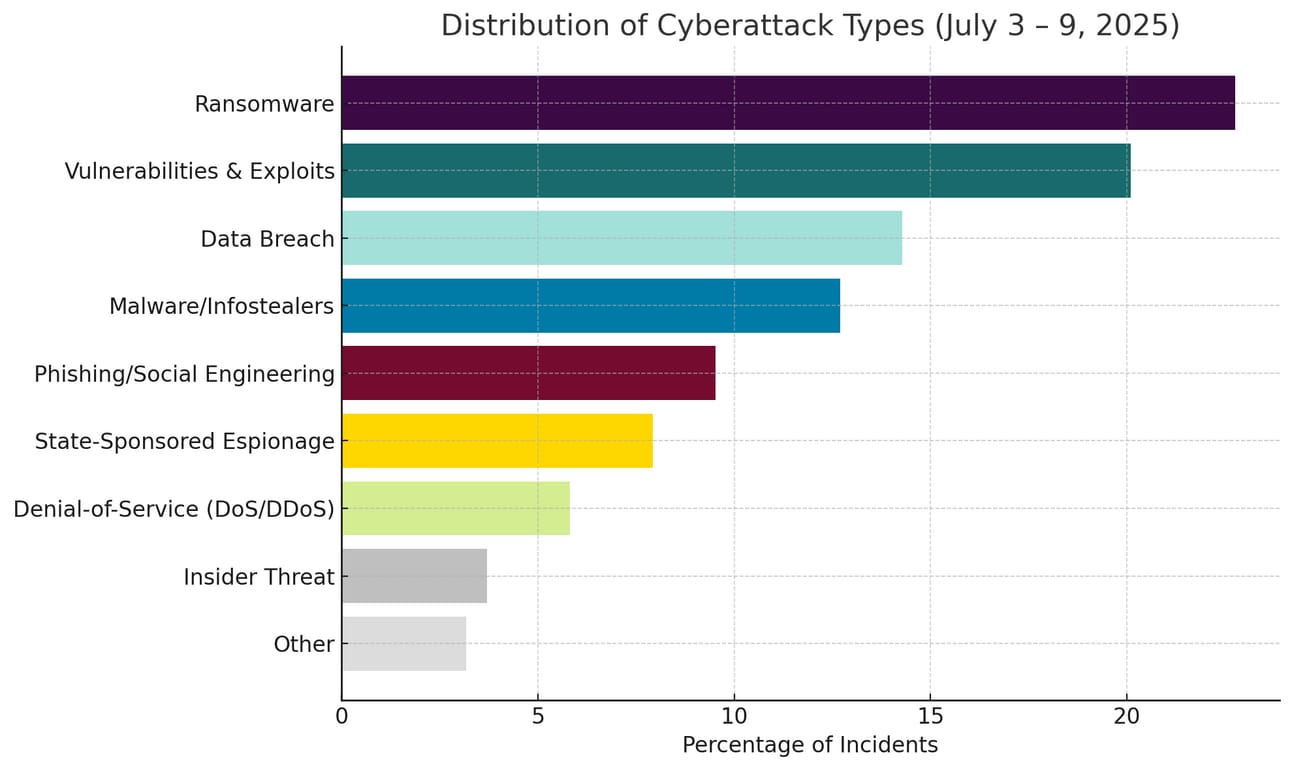
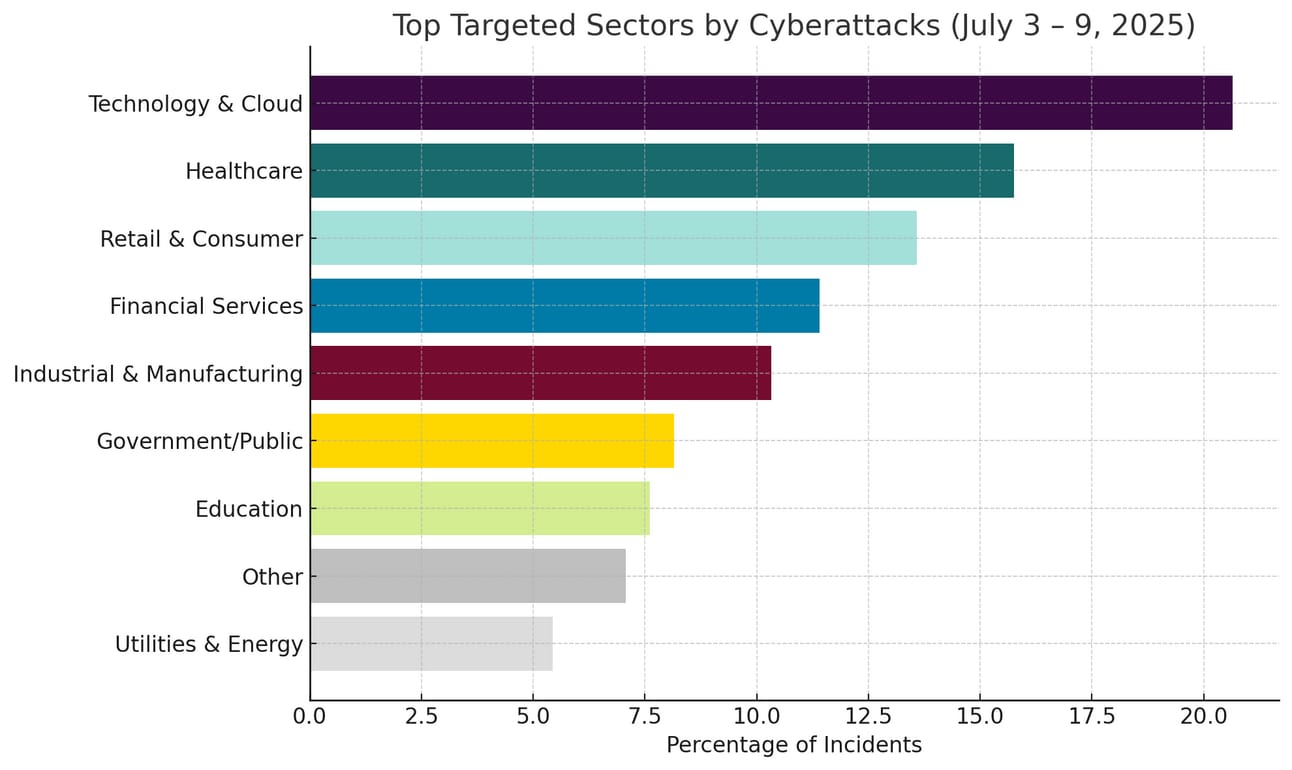
CybersecurityHQ: This Week’s Reports Based on Technical Research and Academic Papers
→ Free
GIFTEDCROOK: From Thief to Spy 👉 Read the report
→ Pro subscriber-only
Building effective governance models for fourth-party cyber risk management 👉 Read the report
Improving threat detection for unmanaged network assets 👉 Read the report
Effective strategies for preventing and mitigating destructive malware in enterprise networks 👉 Read the report
And more inside - check out the full list here.
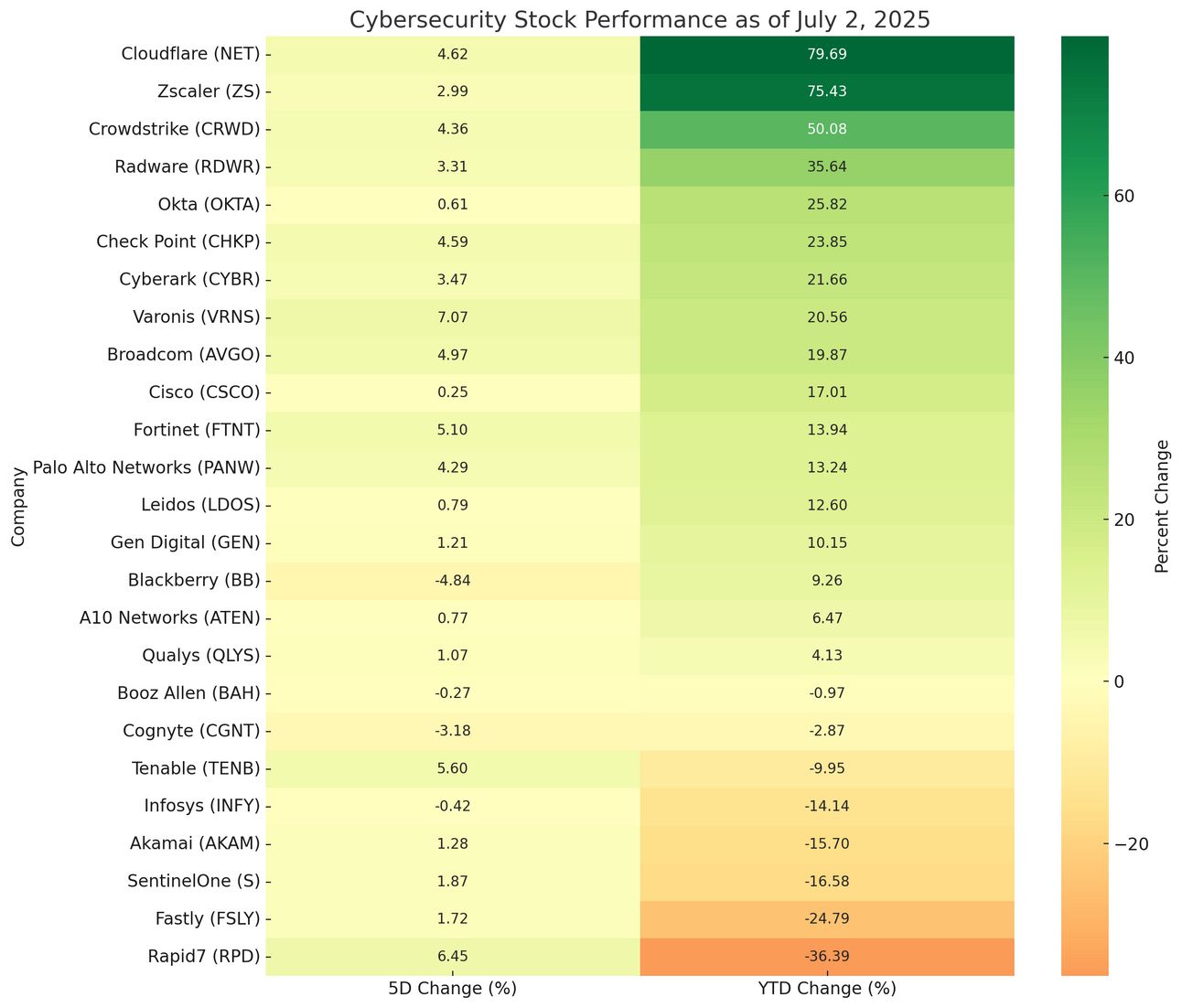
Cybersecurity Stocks
Cyber Intel Brief: Key Insights from Leading Security Podcasts
This is what you missed in this week’s Cyber Intel Report sourced from top cybersecurity podcasts and webinars, if you haven’t upgraded your membership:
⤷ Info-Stealer Silent Victory surpasses ransomware through continuous credential harvesting operating undetected for years across 20-30% annual growth
⤷ Browser Vulnerability Explosion emerges as primary attack surface beyond phishing while enterprises lack basic extension controls
⤷ Healthcare $9.77M Breach Cost exceeds financial services by 60% while records command $1,000+ creating nation-state targeting
⤷ AI Attack Acceleration compresses ransomware development from 12 hours to 15 minutes while voice cloning requires mere seconds of audio
⤷ FBI Cartel Surveillance Crisis exposes democratized tracking technology enabling witness murders.
And more insights in this week’s full CISO briefing.
Interesting Read
AI‑driven impersonation of senior officials escalates
The U.S. Department of State revealed on July 8 that an AI-based deepfake impersonating Secretary Marco Rubio reached out via text and Signal voice messages to foreign ministers, governors, and a U.S. congress member starting mid‑June. The goal: compromise accounts or extract data. The FBI warns this is part of a wider surge in vishing/smishing via deepfakes
Why CISOs care: Normalize deepfake threat modeling in tabletop exercises, enhance employee training on voice/fake-authority attacks, and deploy validation protocols for multi-step communication.
→ Read more at Financial Times
Fresh From the Field: Security Resources You Can Use
Title | Publisher / Authors | Focus | Access Link |
|---|---|---|---|
Cybersecurity and Financial System Resilience Report 2025 | Office of the Comptroller of the Currency (OCC) | Examines OCC’s cybersecurity supervision of U.S. financial institutions and operational resilience goals | |
Meta SecAlign: A Secure Foundation LLM Against Prompt Injection Attacks | Sizhe Chen, Arman Zharmagambetov, David Wagner, Chuan Guo (arXiv) | Presents Meta-SecAlign‑70B, an open-source LLM with built-in defense against prompt-injection | |
Trusted Internet Connections 3.0 Program Guidebook | CISA | Federal TIC 3.0 framework: use cases, reference architecture, overlays, and NIST alignment | |
Emergency Communications System Lifecycle Planning Guide | CISA (SAFECOM) | Lifecycle planning for public-safety/emergency comms systems, with phase templates and checklists | |
2025 Cybersecurity Assessment Report | Bitdefender | Survey and incident analysis of proactive defense, attack-surface reduction, AI-related security trends |
Chief Technology Officer, Reinsurance Technology, TAI
RGA
Chesterfield, MO, US
Cyber Intelligence Analyst - Remote
UPS
Remote
Chief Technology Development Officer/ Associate Provost
Harvard University
Cambridge, MA, US
Cyber Identity - Data Protection and Encryption Senior Consultant
Deloitte
San Francisco, CA, US
US Head - Cyber and Technology Risk
PRI Technology
New York, NY, US
Head of Enterprise Fraud Risk Management
TIH
Charlotte, NC, US
Sr. Architect, Application Delivery
F5
Seattle, WA, US
Data Privacy Regulatory Compliance Consultant
CNA Insurance
Washington, DC, US
Bank of America
Washington, DC, US
Stay safe, stay secure.
The CybersecurityHQ Team


Reply