- Defend & Conquer
- Posts
- CISO market intelligence: Oct 23-29, 2025
CISO market intelligence: Oct 23-29, 2025
CybersecurityHQ weekly analysis
Welcome reader to your CybersecurityHQ report
Brought to you by:
👣 Smallstep – Secures Wi-Fi, VPNs, ZTNA, SaaS and APIs with hardware-bound credentials powered by ACME Device Attestation
📊 LockThreat – AI-powered GRC that replaces legacy tools and unifies compliance, risk, audit and vendor management in one platform
Forwarded this email? Join 70,000 weekly readers by signing up now.
—
Get annual access to our deep dives, weekly cyber intel podcast report, premium content, AI Resume Builder, and more — all for just $299. Corporate plans are now available too.
Introducing the CISO Access Plan Unlock premium CybersecurityHQ insights at no cost, exclusively for CISOs. Reach out to me to claim your access.
Top Targeted Sectors & Attack Trends
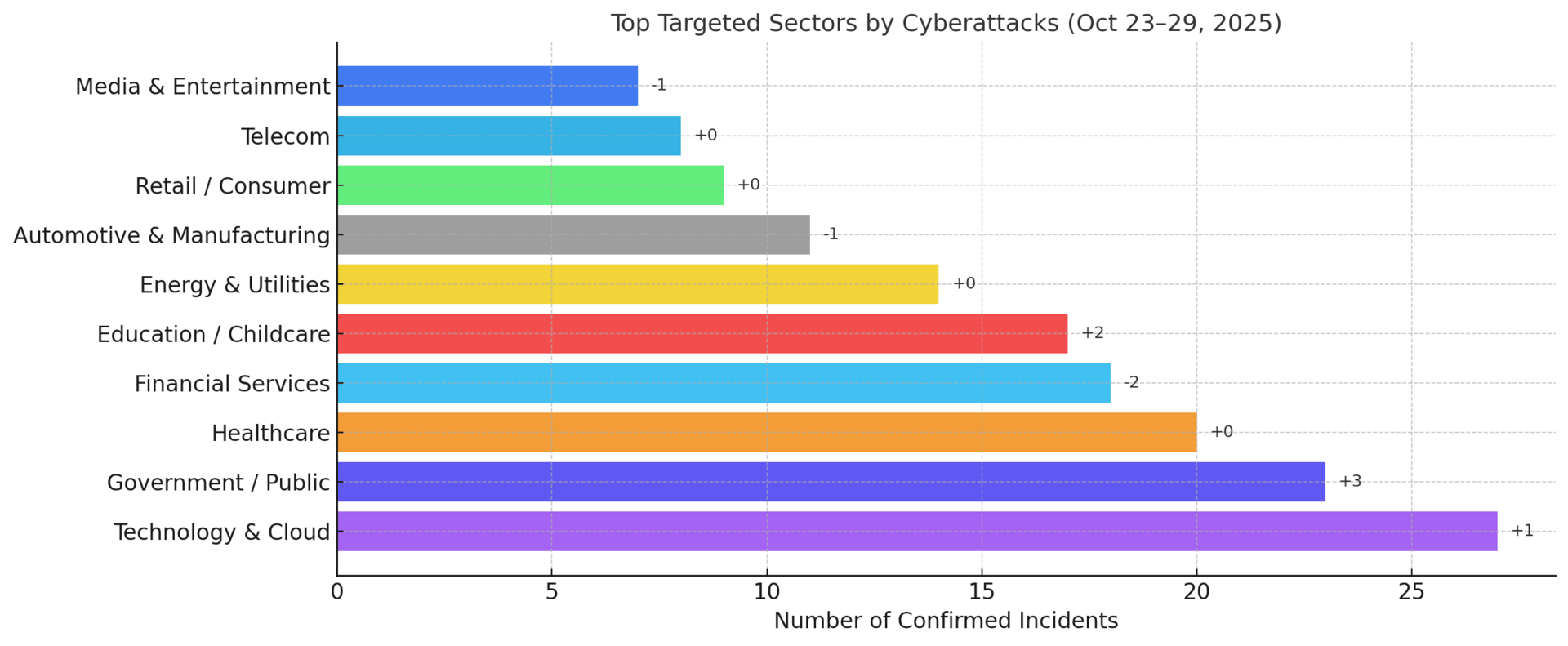
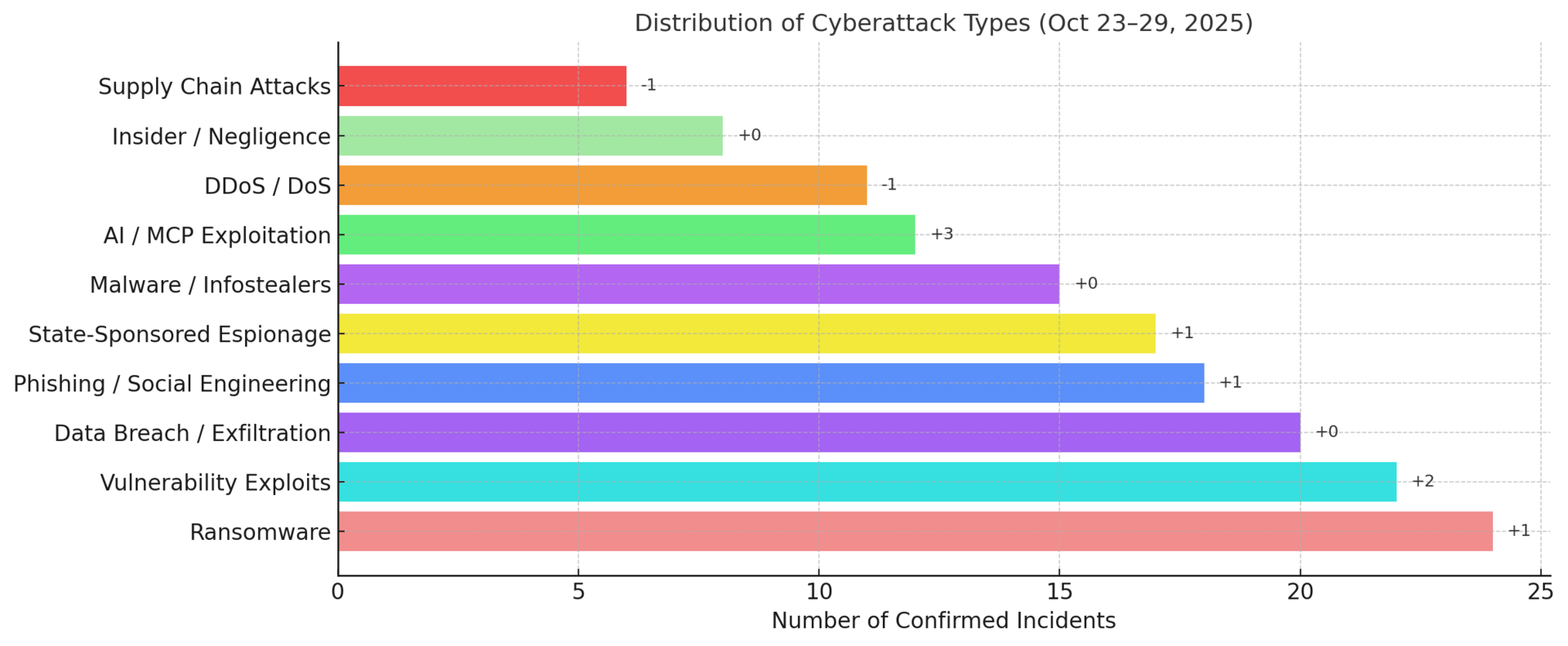
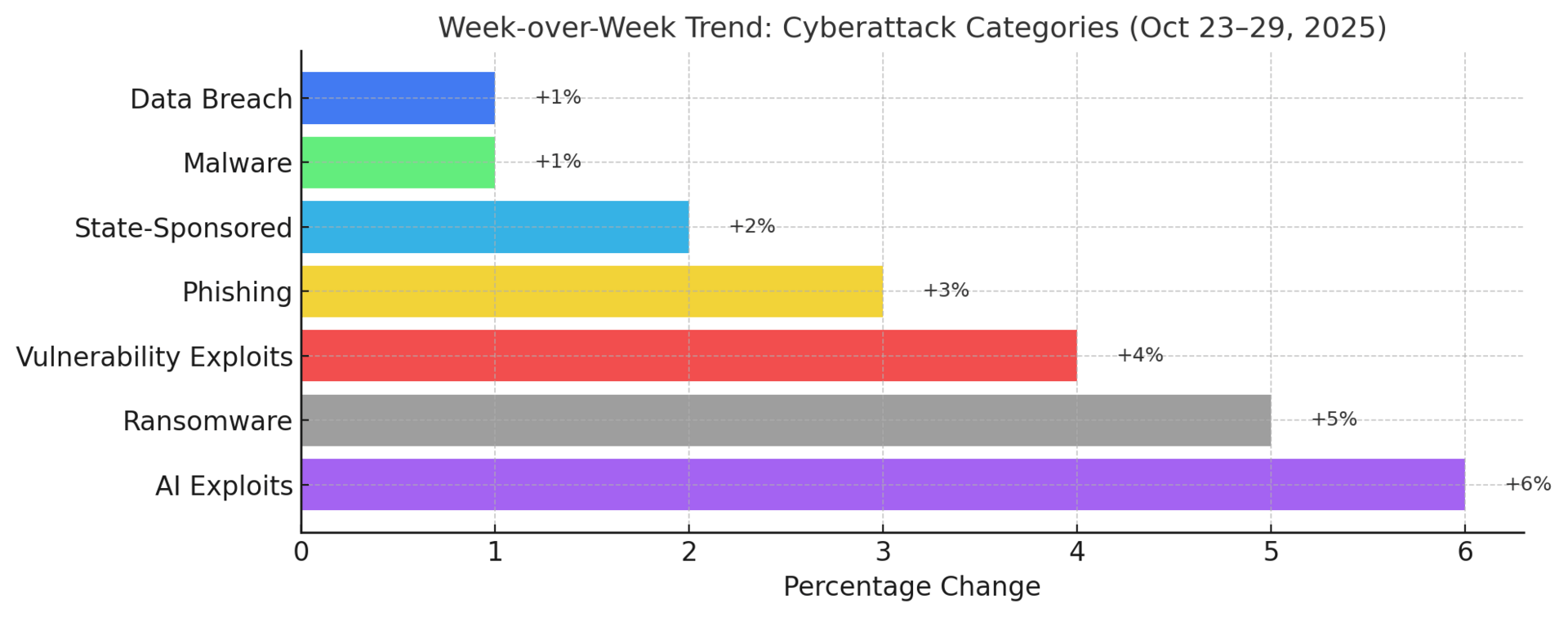
Threat Highlights:
Government/Public: Spike in APT campaigns targeting ministries and telecoms; Russian and North Korean actors exploited F5 and WSUS flaws in coordinated attacks across Europe and Asia.
Healthcare: Steady ransomware activity from Rhysida and Medusa; minor disruptions in U.S. hospital suppliers but no large-scale patient data leaks.
Financial Services: Quiet week publicly; targeted credential-harvesting and BitLocker exploit attempts resurfaced against regional banks.
Technology & Cloud: Remains the most targeted sector — Microsoft, VMware, and Google issued out-of-band patches; AI-driven phishing kits surged 900% YoY.
Industrial/Manufacturing: Moderate increase in botnet exploitation (Mirai, Aisuru) against routers and PLCs; Claroty flagged new ICS misconfigurations.
Energy & Utilities: Reconnaissance uptick linked to Sandworm and Volt Typhoon on critical grid assets; new OT flaws disclosed by ICS-CERT.
Ransomware: LockBit and Qilin dominated attacks across education and local government; ALPHV activity declined slightly after takedown rumors.
Exploits: Active exploitation of WSUS CVE-2025-59287, sudo privilege escalation, and Oracle EBS zero-day; rapid post-patch weaponization observed.
Phishing: Volume stable; credential-stealing kits increasingly use CAPTCHA evasion and fake MFA prompts targeting corporate VPNs.
AI / MCP Exploitation: Up +6% WoW; threat actors deploying generative AI for spear-phish automation, voice-clone scams, and deepfake job recruitment.
CybersecurityHQ: This Week’s Reports Based on Technical Research and Academic Papers
→ Free
When defense became impossible: The 18-minute collapse of corporate security 👉 Read the report
→ Pro subscriber-only
Tactical use of deception and honeypots in volatile threat climates 👉 Read the report
Building analytics systems to detect anomalous high-velocity API usage – a CISO’s guide 👉 Read the report
Evolution of Chinese state-affiliated hacking operations in 2025 👉 Read the report
Adapting to new U.S. DoD cybersecurity rules (effective November 2025) and contract risk 👉 Read the report
And more inside - check out the full list here.
Cybersecurity Stocks

Market Intelligence
The cybersecurity sector drifted slightly lower this week as investors took profits from a strong third-quarter run. The tone has shifted from enthusiasm around AI-driven platforms to caution over valuations, budget timing, and renewed geopolitical risks.
AI remains central to the sector’s narrative, but investors are now distinguishing between vendors that embed intelligence natively into their workflows and those layering AI features onto legacy architectures. Platforms demonstrating measurable automation such as credential risk scoring or autonomous certificate rotation are sustaining stronger margins and customer retention.
Investor focus continues to move toward operating discipline. Companies like Zscaler, CrowdStrike, and CyberArk that balance growth with expanding margins retain institutional favor, while smaller unprofitable vendors face greater scrutiny. The bar for premium valuations has risen as investors prioritize cash flow visibility over ARR velocity.
Recent breaches at Ribbon Communications and F5 Networks reinforced the market’s focus on infrastructure and supply chain risk. Government and public-sector demand remains resilient, benefiting vendors with compliance credentials and proven resilience.
Enterprise budgets are leaning toward renewals and expansions of existing platforms rather than new vendor adoption. Vendors with broad product suites and high dollar-based retention are best positioned to weather macro softness.
Overall, the market is consolidating around a few durable themes:
AI-native automation is outperforming marketing-driven AI.
Margin strength is being rewarded more than topline growth.
Resilience and compliance depth are now investor filters.
Tactical view:
Maintain overweight on Zscaler, CyberArk, and Palo Alto Networks for their automation leverage and profitability visibility. Watch Fortinet and Varonis for rebound potential if sentiment improves. Avoid mid-cap consulting and endpoint vendors until cost discipline stabilizes.
Synthesis of Podcast Insights
This is what you missed in this week’s Cyber Intel Report sourced from top cybersecurity podcasts and webinars, if you haven’t upgraded your membership:
The Revenue Translation Gap that's replacing technically-competent CISOs with business-literate ones—three Fortune 500 security chiefs terminated in Q3 2025 not for breaches but for strategic irrelevance, while boards now demand a specific ROA calculation 80% of security leaders can't perform
The 90/10 Deception Inversion exposing why current security training defends the wrong threat as $1 trillion in scam losses proves cybercrime operates with Fortune 500 organizational sophistication—yet 87% of awareness programs still target technical exploits while attackers mine psychological vulnerabilities
The 96% Speed Barrier separating surviving SOC models from obsolete ones as new detection-response benchmarks (1-minute MTTD, 12-minute remediation) reset board expectations—forcing impossible choices between volume-based metrics that mask failure and velocity-based KPIs that correlate 8x better with breach-cost avoidance
The $8,000/Month Invisibility Tax revealing why major breaches are functionally minor intrusions that organizations can't see—as asset complexity itself becomes the vulnerability and CISOs defend systems nobody uses while attackers exploit the 30% of infrastructure security teams don't know they own
The 66%-vs-37% AI Governance Crisis as organizations expecting significant AI security impact outnumber those with preparedness plans nearly 2:1—while the "Human + Machine" dependency model collapses career ladders that once built security judgment, leaving boards asking which group your leadership belongs to
And more insights in this week’s full CISO briefing.
Interesting Read
Quantum Meets Reality: Tier-4 Data Centers Get “Quantum Zones” and Risk Deepens for CISOs
A new report from ODATA reveals that by 2032, about 5% of Tier-4 data centers will embed “quantum co-processors” — essentially quantum-capable hardware zones — signaling a shift in how enterprise cloud and data-center infrastructure is being architected.
The implications are profound. These quantum zones blur the line between classical cloud workloads and next-gen quantum computing, meaning CISOs need a fresh lens on infrastructure risk now. Quantum readiness is no longer a distant “one day” concern, it’s an architectural issue for today’s high-end hybrid deployments.
For IT and security teams, this means rethinking more than cloud segregation and classical cryptography. It introduces quantum-safe crypto, hybrid workload boundaries, and new supply-chain implications. CISOs must now assess whether their infrastructure providers are moving toward quantum-capable zones and if their encryption and key-management strategies are prepared for “harvest now, decrypt later” threats.
This isn’t a theoretical forecast, Tier-4 centers are already deploying quantum-enabled hardware, bringing quantum risk into the operational horizon for enterprise security leaders.
→ Read more at Security Boulevard
Fresh From the Field: Security Resources You Can Use
Title | Domain | Authors / Vendor | Key Insight | Source |
|---|---|---|---|---|
CISA Alert — Out-of-Band Update for WSUS RCE (CVE-2025-59287) | Government / Vulnerability & Patch Management | Cybersecurity and Infrastructure Security Agency (CISA) | CISA issued an urgent federal alert urging organizations to apply Microsoft’s Oct 23 out-of-band patch for the WSUS remote-code execution vulnerability. It highlights how compressed exploitation timelines now outpace traditional patch cycles. | |
Microsoft — Out-of-Band Update Guidance for WSUS Vulnerability | Vendor / Platform Security | Microsoft Security Response Center | Microsoft confirmed release of the Oct 23 out-of-band update mitigating WSUS RCE and replacing October’s Patch Tuesday build. The report details new servicing guidance and requires immediate deployment and system reboot to ensure mitigation. | |
CISA — Three New Industrial Control Systems (ICS) Advisories | Government / OT & ICS Security | Cybersecurity and Infrastructure Security Agency (CISA) | CISA published three new ICS advisories on Oct 28 2025, underscoring persistent exposure in industrial environments. Advises rapid patching, segmentation, and enhanced monitoring as recurring vulnerabilities appear in PLC and SCADA devices. | |
Unit 42 — WSUS RCE Active Exploitation Brief | Vendor / Threat Research | Palo Alto Networks Unit 42 | Unit 42 confirmed WSUS RCE (CVE-2025-59287) active exploitation within 24 hours of disclosure. Recommends isolating patch infrastructure, monitoring lateral movement, and validating remediation completeness. | |
Trellix — Cyberthreat Report: October 2025 | Vendor / Global Threat Intelligence | Trellix Advanced Research Center | Based on April–September 2025 data, the report details a surge in AI-powered malware, cloud-native exploitation, and targeting of critical infrastructure. Identifies sharp growth in credential abuse and adversary automation. |
Senior Executive Partner - Global CIO/CTO Advisory
Gartner
Remote
Keeper Security
Remote
Vulnerability Assessments Automation Developer
CITI
Irving, TX, US
Associate, Risk/Policy Management
Morgan Stanley
New York, NY, US
Meta
New York, NY, US
Global Data Privacy Counsel; U.S. & Canada Privacy Officer
Arrive
Atlanta, GA, US
Pinterest
San Francisco, CA, US
Partner - Cyber Incident Response, Americas
Control Risks
New York, NY, US
Identity and Access Management Programmer
University of California, Berkeley
Berkeley, CA, US
Stay safe, stay secure.
The CybersecurityHQ Team

Reply